Defeating Conundrums: Solutions to Net-Force Internet CTF Challenges
About Net-Force Internet Challenges
These challenges require that you provide the correct passwords that are revealed to you after solving them. The challenges are arranged in order of increasing complexity and you can attempt them in any order. Internet challenges belong to a variety of subjects and you would need to search the Internet to gain the knowledge required to solve some of them.

What should you learn next?
Spoiler Alert!!
Please be advised that the following content provides solutions to the intriguing Internet challenges on Net-Force. It would be unavailing to read further without having tried your absolute best at the challenges first.
Solutions to Internet Challenges 1 to 8
Internet Challenge 1, Level 703: "Flash Login"
One of the golden rules of security is to never perform any authentication check completely at the client-side. This is because anything at client-side is susceptible to manipulation by the client or user. The user could simply bypass the authentication check or discover the credentials after some reverse engineering. This first challenge demonstrates the dangers of client-side authentication.
We are provided with a flash login screen that demands a username and password [Figure 1].

Figure 1
In Chrome, we use 'Inspect Element' to locate the relevant SWF file [Figure 2].

Figure 2
We notice that this file is present at the following location:
https://www.net-force.nl/challenge/level703/password.swf
We need to obtain this file, 'password.swf', for further analysis. We use 'wget' to download the file on our machine, 'flasm' to reverse engineer the file, and then locate the corresponding file containing the reversed source code using the Linux 'find' command [Figure 3].

Figure 3
We read the source code in a text editor and notice the login credentials (hassan::saeed) embedded in the code [Figure 4].

Figure 4
We can now use these credentials at the login screen. Additionally, while reading the code, we notice the following URL is being accessed: https://www.net-force.nl/challenge/level703/hassan [Figure 5]

Figure 5
We now have 2 options to solve the challenge: use the discovered credentials on the login page OR directly access the discovered URL and bypass the authentication completely. In both cases, we were provided the password for this challenge [Figure 6].

Figure 6
Password: saeed
Internet Challenge 2, Level 705: "Hmmm, I don't see it…"
This next challenge presents us with an image containing a sequence of strange characters [Figure 7]. A big hint is in the title: 'I don't see it'. The language used in the image is Braille—used by the visually impaired. The sequence of raised dots can be felt and read.

Figure 7
In order to decipher the code, you would have to get familiar with Braille. Alternatively, you can use this online Braille keyboard to type it in, and this translator to obtain the plaintext. After decoding the sequence, you would obtain the plaintext message: "this challenge has been written in braille, what was the first name of its inventor". Hence, the password is the first name of Louis Braille—inventor of the Braille language.
Password: Louis
Internet Challenge 3, Level 701: "Hey, where are you from?"
This challenge needs us to manipulate the HTTP variables before it would show the password. If all 3 HTTP variables are set to the correct values, the password would be revealed by the page. You need to modify the following headers:
-
Forwarded
-
OS
-
Via
We were already using a Unix based OS, so we only needed to modify the other 2 headers [Figure 8].

Figure 8
In order to do this, you can use the Firefox extension 'Modify Headers' that is created specifically for such tasks [Figure 9].
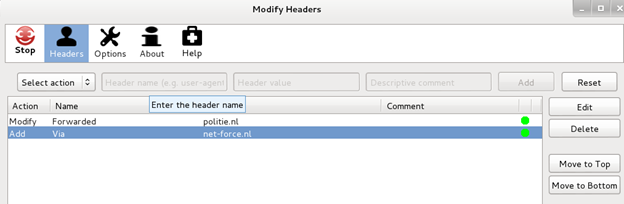
Figure 9
We manipulate the HTTP headers as required by the challenge and obtain the password [Figure 10].

Figure 10
Password: httpheaders
Internet Challenge 4, Level 702: "What am I :-)"
In this challenge, we are provided a file by the name of 'file.txt' and asked to identify the type of file (What am I). This can be easily done using the 'file' utility in Linux that determines the type of file by reading the magic numbers. We determine that this file is in fact a ZIP archive protected by a password [Figure 11].

Figure 11
Since the ZIP archive is password-protected, we need to brute force the password using a tool such as 'fcrackzip'. After brute-forcing the password combinations with 'fcrackzip' for some time, we were able to obtain the password [Figure 12].
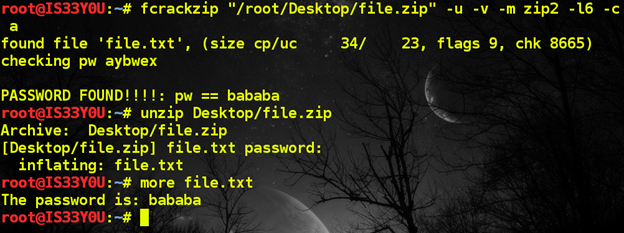
Figure 12
Note: To read more about the functionality of 'fcrackzip', refer to one of our previous papers on steganalysis.
Password: bababa
Internet Challenge 5, Level 704: "Chemical Stuff"
The challenge page describes this challenge as a cryptographic puzzle that requires knowledge of chemistry. We are also told that the Period Table of Elements can be used to solve this cryptogram [Figure 13].

Figure 13
Our first guess is that each of these symbols '22-', '90+', '10+' etc. (separated by a '|') represents a character in plaintext. We need to discover how the plaintext characters were mapped to these symbols. Looking at this periodic table, we see Titanium (Ti) with atomic number '22', Thorium (Th) with atomic number '90', and Neon (Ne) with atomic number '10'. We can get the word 'The' out of this, if the symbol '+' refers to the 1st character in Ti, and the symbol '-' refers to the 2nd characters in 'Th' and 'Ne'. Now, we see a pattern. The number refers to the atomic number in the periodic table while the '+' or '-' points to whether we are to use the 1st character of the atomic symbol or the 2nd. We use this knowledge to decrypt the string. The decrypted plaintext is: "the correct password for this challenge is periodiek". 'Periodiek' is the dutch word for 'periodic'.
Password: periodiek
Internet Challenge 6, Level 706: "Made in Taiwan"
This challenge presents us with a barcode image and asks us to decode it. This can be done easily using a barcode reader or scanner. You can use this online barcode reader to read the barcode GIF image. The decoded barcode data is: 4710212125960 [Figure 14]

Figure 14
Password: 4710212125960
Internet Challenge 7, Level 707: "Walk like an Egyptian"
This next challenge presents us with an ancient Egyptian inscription that we require to translate to Dutch in order to obtain the password. This challenge will be particularly arduous for those of us who don't speak Dutch, since it adds another layer of cryptography for us. The key to solving this challenge lies in knowing that this sentence would most probably say something like: The password for this challenge is: *******. This knowledge comes from having solved several other challenges on the Net-Force website. However in this case, this sentence is in Dutch. Hence, the sentence would say something like: Het wachtwoord voor deze uitdaging is ******.
Decrypting the whole string would require great effort since we need to translate the inscription from ancient Egyptian hieroglyphics to Dutch, and then Dutch to English. Hacking involves smart work and so we focus our attention on first locating the word 'is' in the given inscription and then decoding the word following it—since that is most probably the password.
We will not go into details of how to read ancient Egyptian hieroglyphics since that is beyond our scope. However, the most important thing while reading these Egyptian hieroglyphics is to realize that these symbols don't map to certain characters in our language but have phonetic significance—they represent sounds. By using this image for rough a translation of the inscription, we discover what we were looking for [Figure 15].

Figure 15
Now, we do not need to decode the entire inscription since 'marking' is most probably the password if the inscription is saying something along the lines of: 'the password for this challenge is marking'.
Note: The 'hand' or 'arm' symbol corresponds to a 'd' according to the chart that we are using but the word 'mdrking' does not make sense. Hence, we tried 'marking' instead.
Password: marking
Internet Challenge 8, Level 710: "TurboSnake"
This challenge presents us with a flash game called 'TurboSnake' [Figure 16]. We are required to obtain a score of exactly 40.000 to acquire the password. If you play the game and get a score of '40', the password is not revealed to you since it needs to be exactly '40.000'.

Figure 16
This challenge is built on concept of client-side score-generation vulnerability that many older flash games suffered from. This vulnerability affected games where scores were calculated at client-side after the game was over and then sent to the scoreboards on the servers. Clever players were able to intercept the scores, manipulate them, and send impossibly high game scores to the scoreboards after exploiting this vulnerability. Here, we are going to take advantage of the same weakness, but instead of modifying the value to a very high score, we would focus on setting the score value to exactly '40.000'.
First, we need to locate the SWF file and download it using 'Inspect Element' in Chrome [Figure 17].

Figure 17
We need to reverse this 'challenge.swf' but we need to use something better than 'flasm', otherwise we might struggle with reading a very lengthy bytecode. So, we use this online SWF disassembler to read the source code. A function called 'scoreHandle' immediately interests us, since we are required to modify the score. This function is defined as follows:
[download]
After reading this source code, we know that 'A' corresponds to '0' and 'E' corresponds to '4'. Also, notice that the string obtained from the client-side is first reversed and then appropriate mapping is done.
We need to get '40.000'. If we reverse this it becomes 00004 and, according to the scoreHandle function mapping, '00004' corresponds to 'AAAAE'. Therefore, we try sending in 'AAAAE' as our score. We use BurpSuite proxy to intercept the request, send in this score to the server, and render the response [Figure 18].

Figure 18
Alternatively, you could use an add-on like 'Tamper Data' in Firefox to manipulate the score being sent to the server.
Password: cheatItOut!
End Remarks
After being dormant for some time, the Net-Force community is accepting new members again and is under new management. These Internet challenges at Net-Force were imaginative and captivating. If you are new to solving CTF challenges, these exercises put you on a rapid learning curve with challenges that increase in complexity as you move forward.

What should you learn next?
The solutions above discuss only successful attempts for the sake of brevity. If you enjoyed these, consider attempting more captivating challenges at Net-Force to test or build your skills in security.





