WikiLeaks Vault 7 Data Leak: Another Earthquake in the Intelligence Community
The WikiLeaks organization obtained thousands of files allegedly originating from a high-security network of the U.S. Central Intelligence Agency (CIA).
The huge trove of data, called "Vault 7," sheds light on the hacking capabilities of the U.S. Intelligence Agency and provides details about its spying infrastructure used for the massive surveillance.
"The first full part of the series, "Year Zero," comprises 8,761 documents and files from an isolated, high-security network situated inside the CIA's Center for Cyber Intelligence in Langley, Virginia," reads the announcement issued by WikiLeaks.
"Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, Trojans, weaponized "zero-day" exploits, malware remote control systems and associated documentation."
The archive appears to have been circulated among former US government experts and contractors in an unauthorized manner; one of them likely passed the files to WikiLeaks.
The Vault 7 dump includes confidential information, hacking tools, malicious codes and exploits developed to hack popular products from various IT companies, including Samsung, Apple, Google, and Microsoft.
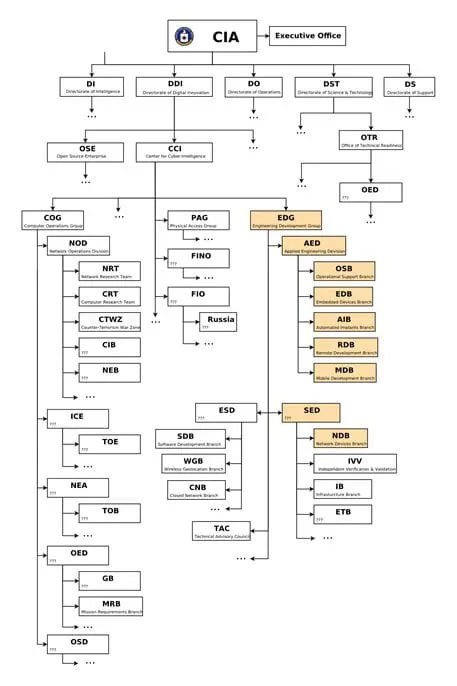
The hacking tools in the arsenal of the CIA have been developed by the CCI's Engineering Development Group (EDG). The developers at EDG are tasked with developing and testing any malicious code, including implants, backdoors, exploits, Trojans and viruses.
The tools allowed cyber spies to target almost any device, including smartphones, desktop computers, and IoT devices (i.e., smart TVs).
According to WikiLeaks, the Central Intelligence Agency has dozens of zero-day exploit codes in its arsenal that can be used to target almost any platform, from Windows and Linux PC to Android and iOS mobile devices.
"CIA malware and hacking tools are built by EDG (Engineering Development Group), a software development group within CCI (Center for Cyber Intelligence), a department belonging to the CIA's DDI (Directorate for Digital Innovation)," continues WikiLeaks.
Just after the release of the CIA archive, WikiLeaks announced that it would not release the tools and the exploits "until a consensus emerges on the technical and political nature of the CIA's program and how such 'weapons' should be analyzed, disarmed and published."
Figure 1 - CIA Organization chart
Several documents in the archive confirm the CIA used hacking tools developed by the British intelligence agencies GCHQ and MI5, the NSA, the FBI, and also by contractors.
A tool dubbed Weeping Angel made the headlines; it is a malicious code developed to transform Samsung Smart TVs into powerful tools for surveillance activities. The tools were developed by the experts at the CIA with the support of their peers at the British MI5.
"The attack against Samsung smart TVs was developed in cooperation with the United Kingdom's MI5/BTSS. After infestation, Weeping Angel places the target TV in a 'Fake-Off' mode so that the owner falsely believes the TV is off when it is on. In 'Fake-Off' mode, the TV operates as a bug, recording conversations in the room and sending them over the Internet to a covert CIA server," continues WikiLeaks.
The documents confirm that the CIA hackers could bypass the encryption implemented by the most popular secure messaging apps such as Signal, WhatsApp, and Telegram.
The attack was possibly targeting mobile devices and not the encryption protocols implemented by the development team of the popular messaging platforms.
CIA Umbrage team, the factory of false flag ops
Just after the release of the WikiLeaks Vault 7 archive, security experts started digging into the precious collection of files.
The files in the dump contain useful information about the Techniques, Tactics and procedures of the US Central Intelligence Agency.
One of the most interesting pieces of information that emerged from the archive is the CIA's ability to fingerprint hacking techniques used by threat actors in the wild, both state and non-state actors.
The CIA has built a specific group of experts, code-named as the Umbrage team, controlled by the Remote Development Branch inside the CIA's Center for Cyber Intelligence.
"The CIA's Remote Devices Branch's UMBRAGE group collects and maintains a substantial library of attack techniques 'stolen' from malware produced in other states, including the Russian Federation.
"With UMBRAGE and related projects, the CIA cannot only increase its total number of attack types but also misdirect attribution by leaving behind the "fingerprints" of the groups from which the attack techniques were stolen," states WikiLeaks.
"UMBRAGE components cover key loggers, password collection, webcam capture, data destruction, persistence, privilege escalation, stealth, anti-virus (PSP) avoidance and survey techniques."
The team maintains a library of techniques borrowed from in-the-wild malware and threat actors for the following reasons:
- The knowledge of attack patterns could help the Agency in forensics investigations to rapidly attribute a cyber-attack to a specific threat actor.
-
The library could be easily included in the CIA's projects to achieve the following goals:
- To reduce the cost and time to develop hacking tools for cyber operations.
- To make the attribution of cyber-attacks harder and cause other threat actors to be blamed for the agency's false flag operations.
Analyzing the WikiLeaks documents about the UMBRAGE group, the experts discovered explicit references to a well-known cyber threat, the Shamoon malware. Information reported in the WikiLeaks dump revealed that the experts at the Umbrage team used the same technique implemented by the Shamoon malware. In this way, it was impossible to distinguish legitimate attacks of the Shamoon attackers from the ones launched by U.S. intelligence.
The Shamoon malware is a malicious code first spotted in 2012 when it destroyed over 30,000 computers at Saudi Aramco.
Since December 2016, security experts have observed a spike in the number of attacks linked to a new variant of the malware, the so-called Shamoon 2.
The first Shamoon variant abused a commercial digitally-signed driver called RawDisk, developed by a company named Eldos.
The experts at the Umbrage group devised a method to bypass the license check for the RawDisk driver and implemented the same disk-wiping technique in an internal hacking tool dubbed Rebound.
Then when malware researchers discovered a Rebound sample in some systems, they identified it as a Shamoon variant instead of the CIA implant.
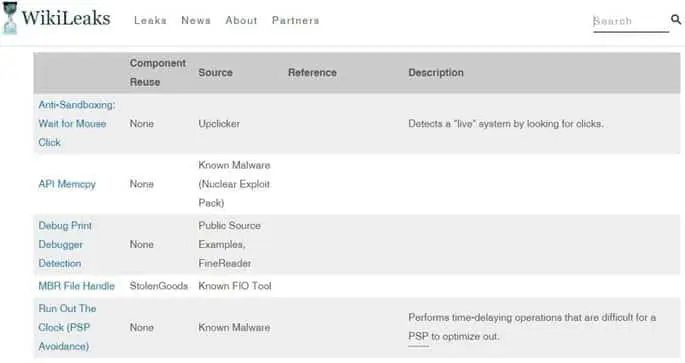
The UMBRAGE team has many other techniques and tools in its arsenal. For example, the experts could reproduce a persistence technique borrowed from the HiKit rootkit.
The CIA hackers can implement the webcam capture feature used by the infamous DarkComet RAT and also sandbox evasion techniques borrowed from the Trojan Upclicker and the Nuclear Exploit Pack.
The arsenal is full of tools; for example, ShoulderSurfer is software used by the CIA to hack Windows Exchange 2010. The tool performs a code injection attack against the Exchange Datastore manager process allowing the CIA hackers to siphon emails and contacts without needing the user's credentials.
Other software in the archive can target Apple users. The QuarkMatter technique, for example, allows attackers to hide spying software persistently on an OS X system by using an EFI driver stored on the EFI system partition.
The documents also include details for a project called HarpyEagle that analyzed Apple's Airport Extreme firmware for private keys and also Time Capsule systems.
Figure 2 - CIA projects included in the Vault 7 dump
The CIA data leak shows the CIA hackers have an extensive list of iOS exploits in their arsenal. Some tools were developed by the CIA itself, others were developed by the GCHQ, and others were sold by private vendors.
The intelligence Agency, of course, also has a lot of tools that can hack Android mobile devices. The documents refer to three implants listed as Bowtie, SuckerPunch, and RoidRage that can be used to spy on Android mobile devices. The release notes for the RoidRage implant show it can be used for different purposes, including the monitoring of all radio functions and stealing SMS messages from the target.
Back to the Umbrage arsenal, its components were inspired by the code leaked in 2015 from the Italian surveillance company Hacking Team.
The CIA experts focused on implementing the implants used by the Hacking Team designed to hack Windows systems.
"If one is interested in using some implementations found in the source code, it should be considered a best practice to extract the desired pieces and thoroughly review and test the extracted pieces," is reported in the leaked files.
Unfortunately, many other intelligence agencies may have used a similar technique to deceive investigators.
WikiLeaks is working with software makers to neutralize CIA hacking tools
WikiLeaks will share information on the hacking tools included in the Vault7 dump with the tech companies whose products are affected even if the White House has warned that there may be legal repercussions for the organization.
WikiLeaks wants to protect the customers of the major companies that use the products of several major companies impacted by the hacking tools in the data leak.
After the data leak, WikiLeaks announced it would not release tools or exploits "until a consensus emerges on the technical and political nature of the CIA's program and how such 'weapons' should be analyzed, disarmed and published."
During a WikiLeaks press conference on March 9, 2017, Julian Assange explained that the organization decided to share information with impacted companies.
"We have decided to work with them, to give them exclusive access to the additional technical details we have so that fixes can be developed and pushed out so that people can be secured," Assange said. "And then, once this material is effectively disarmed by us, we will publish additional details about what has been occurring by removing critical components."
The decision was taken by WikiLeaks and its followers through a poll on Twitter about the possibility of sharing technical details of the hacking tools with the companies in private industry that sell the products targeted by U.S. intelligence.
"Yes, make people safe," while 36 percent of respondents said, "No, they're the problem."
"If a program or a piece of information is classified, it remains classified regardless of whether or not it is released into the public venue or not," said White House press secretary Sean Spicer. "I would suggest that someone consult with [the Department of Justice] regarding the legal repercussions of any individual or entity using any piece of still-classified information, technique, or product that hasn't been declassified."
The CIA did not comment on the authenticity of WikiLeaks' data leak but remarked that US law doesn't allow the Government to spy on its citizens.
While I was writing, tech companies are already working to fix the zero-day flaws in their products and to offer customers tools to detect the presence of anomalies in their applications.
Intel Security has released a tool that allows users to check if the firmware of computers contains unauthorized code.
The Advanced Threat Research team at Intel Security developed a new module for its existing CHIPSEC open-source framework to detect rogue EFI binaries. It can be used to detect malicious code from Windows, Linux, macOS, and even from an EFI shell.
Other companies are doing the same to protect their customers.
Hands-on threat intel training
The CIA's reply to the Vault 7 data leak
The CIA has issued an official statement in response to the WikiLeaks Vault7 Data leak, the US Agency denies conducting large-scale surveillance on its citizens.
According to an unnamed U.S. official quoted by Reuters, a CIA contractor is the most likely source of the data leak.
"Contractors likely breached security and handed over documents describing the Central Intelligence Agency's use of hacking tools to the anti-secrecy group WikiLeaks, U.S. intelligence and law enforcement officials told Reuters on Wednesday," states Reuters.
"Two officials speaking on condition of anonymity said intelligence agencies have been aware since the end of last year of the breach, which led to WikiLeaks releasing thousands of pages of information on its website on Tuesday."
The decision of the CIA to not disclose the data breach exposed the companies that use the devices targeted by its tools to the risk of cyberattacks.
The CIA and the FBI have launched an investigation into the WikiLeaks Vault7 Data leak, even if the Central Intelligence Agency did not confirm the authenticity of the huge trove of files.
The intelligence Agency tried to downplay its responsibility; the CIA pointed out its mission is to "aggressively collect" foreign intelligence from overseas entities. Foreign governments and non-state actors, such as terrorists, are becoming even more dangerous and persistent, so the CIA is also using tools and techniques to protect Americans.
"It is the CIA's job to be innovative, cutting-edge, and the first line of defense in protecting this country from enemies abroad," reads the statement issued by the CIA.
"The American public should be deeply troubled by any WikiLeaks disclosure designed to damage the Intelligence Community's ability to protect America against terrorists and other adversaries. Such disclosures not only jeopardize U.S. personnel and operations but also equip our adversaries with tools and information to do us harm," the agency said.
The tools in the CIA arsenal appear to have been designed for targeted attacks instead of dragnet surveillance. The CIA pointed out that it is not allowed for Intelligence agencies and law enforcement bodies to spy on individuals in the United States. The agency said its activities "are subject to rigorous oversight to ensure that they comply fully with U.S. law and the Constitution."
According to the CIA, all the operations conducted by the US agencies "are subject to rigorous oversight to ensure that they comply fully with U.S. law and the Constitution."
The Vault 7 data leak will seriously impact the CIA surveillance activities; the tool and techniques described in the documents will soon be ineffective.
Which are the reactions of other governments to the WikiLeaks dump?
China expresses concerns at the revelations. The products of many Chinese companies may have been targeted by the CIA hackers.
"China expressed concern on Thursday over revelations in a trove of data released by WikiLeaks purporting to show that the CIA can hack all manner of devices, including those made by Chinese companies," reported Reuters.
"Dozens of firms rushed to contain the damage from possible security weak points following the anti-secrecy organization's revelations, although some said they needed more details of what the U.S. intelligence agency was up to.
"Widely-used routers from Silicon Valley-based Cisco (CSCO.O) were listed as targets, as were those supplied by Chinese vendors Huawei [HWT.UL] and ZTE (000063.SZ) and Taiwan supplier Zyxel for their devices used in China and Pakistan."
Germany's foreign ministry issued a statement saying it is in contact with the U.S. Government to receive more information on the case.
The chief federal prosecutor's office confirmed it would review the WikiLeaks data dump related to the claims that the CIA ran a hacking hub from the U.S. consulate in Frankfurt.
"We will initiate an investigation if we see evidence of concrete criminal acts or specific perpetrators," a spokesman for the federal prosecutor's office told Reuters.
References
https://wikileaks.org/ciav7p1/, WikiLeaks
http://securityaffairs.co/wordpress/56958/intelligence/wikileaks-cia-hacking-tools.html
http://securityaffairs.co/wordpress/56983/intelligence/wikileaks-vault7-cia-umbrage-team.html
https://wikileaks.org/ciav7p1/cms/page_524353.html
http://securityaffairs.co/wordpress/57042/intelligence/wikileaks-vault7-dump-0day.html
http://securityaffairs.co/wordpress/57015/data-breach/cia-replies-wikileaks-vault7.html
http://securityaffairs.co/wordpress/57015/data-breach/cia-replies-wikileaks-vault7.html