Mechanics Behind Ransomware-as-a-Service
Introduction
Ransomware is an increasingly serious concern, and this problem is getting worse over time. Initially, this malware began to compromise fixed targets such as individuals, but now the focus has changed and became much broader — from individuals to organizations. Hospitals, for instance, have become under attack by cyber attackers that carried out malicious campaigns to extort money.
In a few words, ransomware is a malware type which restricts access to data stored on a computer or system and demands the users to pay a ransom to remove that restriction. With the rise of Ransomware-as-a-Service (RaaS) model, cyber attackers have an easy way to launch a cyber-extortion business with virtually no technical expertise required. RaaS platforms have emerged on the Dark Web, and they are likely one of the primary drivers behind the huge spike in ransomware attacks over the last year.
Nowadays, the main targets for ransomware attacks are the organizations, as many of them end up paying the ransom to cyber attackers to avoid any negative reputational consequences which arise from the failure to protect their sensitive information.
The Most Representative Forms of RaaS
RaaS already put its hallmark in the complex landscape of digital threats by operating with the same principles that govern Cloud services to satisfy business needs for online services. Hence, it is no surprise that cybercriminals went even further and contrived an affiliate ransomware distribution scheme.
This scheme gained major traction in 2015. RaaS began to be distributed via toolkits allowing cybercriminals to distribute ransomware by paying another cybercriminal for access to the code. With this piece of software, anyone can become a cybercriminal, even those who aren't very technologically skilled.
Tox, for instance, is the first occurrence of RaaS detected and discovered since early 2015. The ransomware-construction kit was available online for free in the Dark Web since May 19th, 2015.
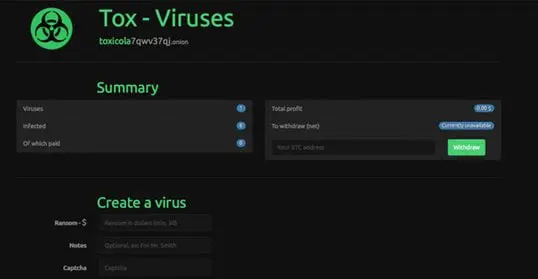
Figure 1: Tox RaaS Creator.
Cybercriminals behind Tox created a virus which, once opened in a Windows OS, encrypts all the files. When this process is completed, it displays a message asking to pay a ransom to a bitcoin address to unlock the files. The malware was available at toxicola7qwv37qj.onion on dark web.
In this information era, many new RaaS kits such as Cerber, Satan, Petya, Mischa, Ransom32, Karman, Philadelphia, and CryptoLocker Service, Ranion, and many others, have entered the market, making ransomware much more accessible to cybercriminals. The increased RaaS competition led to a reduction in price. For example, cybercriminals can now obtain RaaS kits for as low as $39.
Nonetheless, over the years, ransomware attacks have become more sophisticated and continually focused on the weaknesses of the aging IT infrastructure. At healthcare institutions, for instance, these attacks do not only compromise the patient's confidential data but both the health service capacity and people's safety too.
Organizations, and the industry in general needs to modernize and update IT services to protect itself from inevitable attacks.
Modus Operandi of a RaaS
In short, the simple form of a ransomware attack consists of four stages, namely:
- The infection with ransomware.
- Activation of ransomware.
- Request for the ransom, and;
- Payment of the ransom.
Below, Figure 2 presents the differences of ransomware in contrast with RaaS.
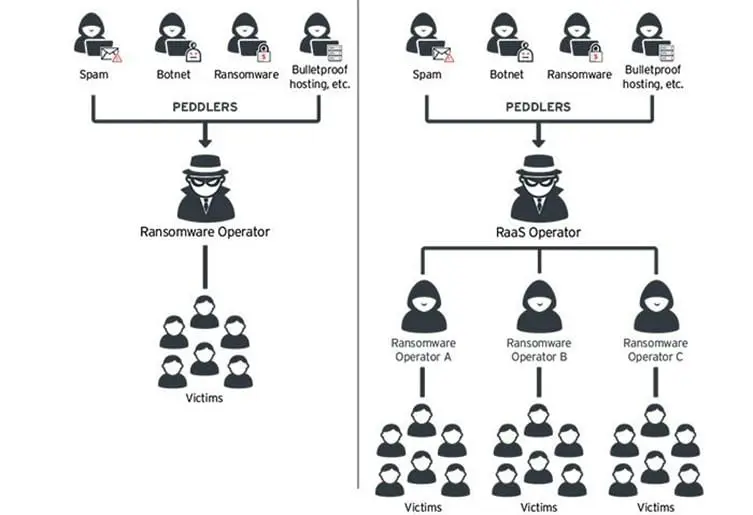
Figure 2: Simple form of ransomware versus RaaS (TrendMicro [8]).
The major distinction between ransomware and RaaS is that the operator gets a cut from each victim's payment, resulting in more potential profit than from the traditional ransomware business model.
How It Works
Typically, RaaS creators host their ransomware code on a web portal, where RaaS affiliates (other cybercriminals) can deploy it from a simple dashboard. Affiliates can configure their new ransomware campaign, namely the time intervals at which the ransom increases and even get an estimate of their potential earnings before signing up and get the "malicious software."
Afterward, purchase affiliates use their own methods as a means of infection. Notice that many ransomware code packages are free to deploy with a profit-sharing model in which the author shares in the affiliates' earnings. This works like a legitimate software affiliate program. When victims pay (e.g., via Bitcoin) to unlock their data, payments are often delivered to the author's account, who then distributes a share to the affiliates. Affiliate shares can range from 60 to 80 percent. Undoubtedly, this makes RaaS a very lucrative business for both authors and affiliates.
Satan dashboard, below, represents one of the best examples of this type of malicious architecture.
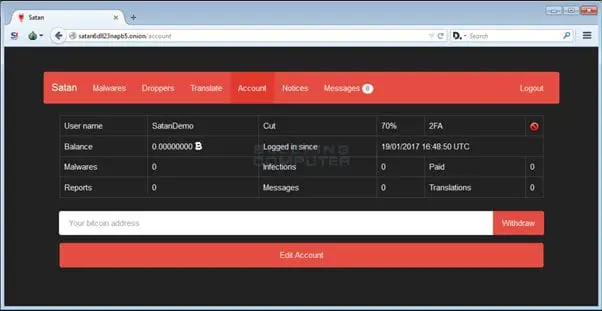
Figure 3: Satan RaaS Dashboard (Bleeping Computer [9]).
Defensive Measures
The best way for companies and individuals to fight this problem is to follow these defensive measures against ransomware in general:
- Make regular backups. This is the most important procedure for organizations that process data. Having backups available allows them to restore the original information without paying for it, and free of damage.
- Be careful and don't enable macros in document attachments received via email. In this sense, Microsoft purposely turned off auto-execution of macros by default many years ago as a security step.
- Pay attention and discard emails with suspicious attachments or extensions.
- Keeping all the system updated. Create a checklist of all systems and software, with their versions, and to plan update them with frequency.
- Protect your organization against RaaS. Start by educating by creating a cybersecurity culture. For example, most ransomware delivered through the Internet is addressed via phishing emails. Training employees to question suspicious messages and unknown attachments can be an essential first line of defense.
- Employ a good combination of antivirus and a digital security scanner.
Final Thoughts
Conventional antivirus software can only operate and protect against threats they know, based on past infections. It's clearly notorious that, cybercriminals can create a new variant of ransomware with each new campaign. In this way, organizations behind antivirus software must identify and analyze the threat beforehand to adapt their protection successfully to block the malware. The bad news is the only way that this happens is if someone gets infected first.
When you follow these recommendations and implement the correct software for digital security, you will have more barriers to keep your digital assets away from the tentacles of cybercriminals.
Sources
[1] https://www.malwarebytes.com/pdf/white-papers/SecondAnnualStateofRansomwareReport-USA.pdf
[2] https://www.vpnmentor.com/blog/history-ransomware-threat-past-present-and-future/
[4] https://securityzap.com/tox-ransomware-creator/
[6] http://www.gb-advisors.com/tech-blog/raas-ransomware-as-a-service/
[7] /ransomware-as-a-service-8-known-raas-threats/#gref









