Past and Present Iran-linked Cyber-Espionage Operations
Iranian hackers intensify their cyber operations
Security experts and intelligence agencies are observing a significant intensification of the cyber espionage campaigns linked to Iran-based hackers.
A few days ago, security researchers at Palo Alto Networks had uncovered a new cyber espionage campaign linked to Iran that targeted several organizations in the Middle East. Threat actors hit numerous organizations in the energy, government, and technology industries, all the victims are located or have an interest in Saudi Arabia.
The hacking campaign was dubbed Magic Hound, and according to the analysts, it dates back at least mid-2016.
It is interesting to note that hackers behind the Magic Hound campaign used a wide range of custom tools and an open-source, cross-platform remote access tool (RAT) dubbed Pupy.
"According to the developer, PupyRAT is a "multi-platform (Windows, Linux, OSX, Android), multi-function RAT and post-exploitation tool mainly written in Python." CTU™ analysis confirms that PupyRAT can give the threat actor full access to the victim's system." reads the analysis published by SecureWorks.
The hackers' arsenal includes different families of custom tools, including droppers, downloaders, executable loaders, document loaders and IRC bots.
"Unit 42 has discovered a persistent attack campaign operating primarily in the Middle East dating back to at least mid-2016 which we have named Magic Hound. This appears to be an attack campaign focused on espionage. Based upon our visibility it has primarily targeted organizations in the energy, government, and technology sectors that are either in in or business interests in Saudi Arabia." reads the analysis published by PaloAlto Networks.
"Link analysis of infrastructure and tools also revealed a potential relationship between Magic Hound and the adversary group called "Rocket Kitten" (AKA Operation Saffron Rose, Ajax Security Team, Operation Woolen-Goldfish) as well as an older attack campaign called Newscasters."
Experts at SecureWorks are also monitoring the activity of the Iranian threat actor; they linked the attacker to a nation-state group of hackers tracked as COBALT GYPSY that is associated with the Government of Teheran.
The technique used by hackers is not sophisticated; hackers used spear-phishing messages with Word and Excel documents embedding malicious macros. When the victims open the document and enable the macro, a malicious payload is downloaded and executed.
"The downloaded document attempts to run a macro that then runs a PowerShell command. This command downloads two additional PowerShell scripts that install PupyRAT, an open-source remote access trojan (RAT)," reads the analysis published by SecureWorks.
The malicious documents used in the attacks appear to be holiday greeting cards, job offers, and official government documents from the Ministry of Health and the Ministry of Commerce in Saudi Arabia.

Figure 1 - Malicious documents used in the Magic Hound Campaign (SecureWorks)
In January 2017, a cyber espionage group linked to the Iranian Government has been using an unsophisticated strain of malware, dubbed MacDownloader, to steal credentials and other data from Mac computers.
The malicious code was discovered and analyzed by the malware researchers Claudio Guarnieri and Collin Anderson. The security duo discovered that the malicious code was disguised by nation-state hackers as a Flash Player update and a Bitdefender Adware Removal Tool.
The attacks observed by the researchers mostly targeted the defense industrial base sector, but the same threat actors also used the same malware in a targeted attack against a human rights advocate.
The malicious code does not appear to be sophisticated, according to the security duo it was "poorly" developed the end of 2016 and its code was copied from other sources.
The problem is that even if the code is very simple, at the time of writing the analysis, MacDownload was undetected by virus scanning engines on VirusTotal. More than a month later, less than half of the vendors was able to detect the bogus Flash Player and Bitdefender apps as a threat.
Once the MacDownloader infects a device, the malware collects information about the host, including passwords stored in the Keychain.
"MacDownloader seems to be poorly developed and created towards the end of 2016, potentially a first attempt from an amateur developer. In multiple cases, the code used has been copied from elsewhere. The simple activity of downloading the remote file appears to have been sourced from a cheat sheet. The main purpose of MacDownloader seems to be to perform an initial profiling of the infected system and collection of credentials from macOS's Keychain password manager – which mirrors the focus of Windows malware developed by the same actors." reads the analysis published by the security duo.
The experts discovered a first sample of the malware on a fake website of the aerospace firm United Technologies Corporation, that is the same website that was used in the past to spread a Windows malware and the Browser Exploitation Framework (BeEF).
The malware researchers linked the MacDownloader with the activity of an Iranian threat actor known as Charming Kitten (aka Newscaster and NewsBeef).
The Newscaster hacker group made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media.
Iranian Hackers used a network of fake accounts (NEWSCASTER network) on principal social media to spy on US officials and political staff worldwide, this is reported in an analysis done by iSIGHT Partners. The Charming Kitten group is also known for the abuse of Open Source Security Tools, including the BeEF.
The analysis of the malware revealed that the authors have attempted to implement remote update and persistence capabilities, but both features do not work.
"It appears that the application contains an unused attempt to install persistent access to the victim host. One segment provides a poorly-implemented shell script to save a response from the C2 and mark it for persistence by writing an entry in the /etc/rc.common file. In theory, every time the infected computer would start up, the shell script would be launched to download a file from a remote location, check if it changed from the previous iteration, and if so execute that new implant. While we haven't managed to obtain a proper response from the server before it was taken offline, our initial investigation did not find a subsequent implant," states the analysis.
The experts have collected evidence that links the malware to other Iranian threat actors, including the Iran Cyber Security Group and Flying Kitten (aka Rocket Kitten).

Figure 2 - MacDownloader Malware
"Of particular note are wireless networks named Jok3r and mb_1986. Jok3r corresponds with a member of a defacement group, Iran Cyber Security Group, who continues to be fairly active in vandalizing sites. Iran Cyber Security Group also, as with many other defacement groups later identified as involved in state-aligned campaigns, purports to provide commercial security services and penetration testing training," states the report.
"The "mb_1986″ wireless name is more interesting, as it provides a connection to earlier Iranian campaigns, overlapping with the Flying Kitten actor group and subsequent malware activity in summer 2014."
Iranian OilRig APT is back
The OilRig APT is one of the most popular hacker group linked to the Iranian Governments that has been around since at least 2015. The group conducted numerous cyber attacks against government agencies, financial institutions and technology companies in Saudi Arabia, Israel, the United Arab Emirates, Lebanon, Kuwait, Qatar, the United States, and Turkey.
Experts from Palo Alto Networks have been monitoring the activity of the group over the years; hackers conducted numerous spear-phishing attacks using weaponized Microsoft Excel spreadsheets tracked as "Clayslide" and a backdoor called "Helminth."
In January, the experts at ClearSky reported a new string of cyber attacks that targeted several Israeli organizations, including IT vendors, the national postal service, and financial institutions.
The state-sponsored hackers set up a fake Juniper Networks VPN portal and used compromised email accounts from IT vendors to lure victims to it.
The hackers used the email accounts of the IT vendors to send messages containing links to the fake VPN portal to the victims.
"The email was sent from a compromised account of an IT vendor. Similar emails were sent from other IT vendors in the same time period, suggesting the attackers had a foothold within their networks, or at least could get access to specific computers or email accounts." reads the analysis from ClearSky.
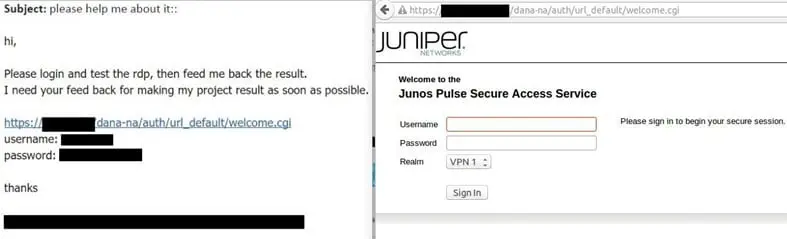
Figure 3 - Bogus VPN Website
When the victims click on the link are redirected to the rogue Juniper website that displays users the instructions to install a legitimate VPN client that packaged with the Helminth malware.
The attackers signed the trojanized VPN client with a valid code-signing certificate issued by Symantec to a US-based software company called AI Squared. The researchers also discovered a second sample of the Helminth malware signed with another certificate.
"Another Helminth sample, 1c23b3f11f933d98febfd5a92eb5c715, was signed with a different AI Squared code signing certificate:
Thumbprint: 92B8C0872BACDC226B9CE4D783D5CCAD61C6158A
Serial number:62 E0 44 E7 37 24 61 2D 79 4B 93 AF 97 46 13 48
This suggests that the attackers had got a hold of an AI Squared signing key, potentially after compromising their network. Alternatively, the attackers might have got Symantec to issue them a certificate under AI Squared's name," states the analysis.
The OilRig group used four domain names apparently belonging to Oxford University (including oxford-symposia[.]com, oxford-careers[.]com, oxford[.]in and oxford-employee[.]com).
In one case, the threat actors set up a fake Oxford conference registration website to instruct visitors to install a tool needed for pre-registration that hides a malicious code signed with an AI Squared certificate.
 <>
<>
Figure 4 - OilRig set up a fake Oxford conference
Back in December 2015, the experts from Symantec published a detailed analysis of the cyber espionage campaign conducted by two Iran-based hacker groups, dubbed Cadelle and Chafer, which used the backdoor.Cadelspy and backdoor.Remexi to spy on Iranian individuals and Middle Eastern organizations.
The IP address 83.142.230.138 reported in the analysis of Symantec belonging to the C&C infrastructure used by the Chafer group is the same used by the OilRig.
"Backdoor.Remexi, one of the malware in use by Chafer, had the following command and control host:
87pqxz159.dockerjsbin[.]com
Interestingly, IP address 83.142.230.138, which serve as a command and control address for an OilRig related sample (3a5fcba80c1fd685c4b5085d9d474118), was pointed to by 87pqxz159.dockerjsbin[.]com as well."
This circumstance suggests that the Chafer and OilRig are the same Iranian entity.
Iranian hackers behind the Magic Hound campaign linked to Shamoon
The dreaded Shamoon malware, aka Disttrack, made the headlines in the last part of 2016.
On December 2016, security experts from Palo Alto Networks and Symantec both monitored a new wave of cyber attack on a single Saudi company.
We met the Shamoon malware for the first time on August 15th, 2012, when the Saudi Arabia's oil company, Saudi Aramco announced that its systems and its internal network were victims of a cyber-attack. According to the company, Shamoon infected more than 30,000 workstations.
The new variant of Shamoon, so-called Shamoon 2, can rewrite the MBR on affected computers with an image of a three-year-old Syrian boy named Alan Kurdi that lay dead on a Turkish beach.
"Why Shamoon has suddenly returned again after four years is unknown. However, with its highly destructive payload, it is clear that the attackers want their targets to sit up and take notice," reported Symantec.
A few weeks later, in January, researchers at Palo Alto Networks discovered a new strain of the Shamoon 2 malware that was targeting virtualization products.
The researchers at IBM's X-Force Incident Response and Intelligence Services (IRIS) have now published a detailed analysis of the attack chain of the Shamoon malware, which is considered a weapon used in the information warfare between Saudi Arabia and Iran.
The IBM's X-Force experts have identified the servers used to deliver the Shamoon 2 variant and were able to break into one of them gathering more information on the threat.
"This research led them to believe that the actor using Shamoon in recent attacks relied heavily on weaponized documents built to leverage PowerShell to establish their initial network foothold and subsequent operations:" IBM reports.
- Attackers send a spear phishing email to employees of the target organization. The email contains a Microsoft Office document as an attachment.
- Opening the attachment from the email invokes PowerShell and enables command line access to the compromised machine.
- Attackers can now communicate with the compromised machine and remotely execute commands on it.
- The attackers use their access to deploy additional tools and malware to other endpoints or escalate privileges on the network.
- Attackers study the network by connecting to additional systems and locating critical servers.
- The attackers deploy the Shamoon malware.
- A coordinated Shamoon outbreak begins, and computer hard drives across the organization are permanently wiped.

Figure 5 - Shamoon 2 attack
The attackers launched a spear-phishing campaign against the potential targets; they used to impersonate a trusted person, for example, the Saudi Arabia's Ministry of Commerce and Investment or the Egyptian software company IT Worx.
The messages come with a Word document marked as a resume, health insurance paperwork, or password policy guidelines, anyway something of interest for the potential victim.
The documents include a malicious macro that is used to start the attack when the victim executes it. The execution of the macro launches two different Powershell scripts.
- The first script downloads and executes another PowerShell script from the 139.59.46.154:3485/eiloShaegae1 via HTTP. The second script creates a memory buffer using the VirtualAlloc library call, fetches shell code from 45.76.128.165:4443/0w0O6 via HTTP, copies it into the buffer, and executes the code using CreateThread. This thread then creates another buffer, fills it with a PowerShell script from 45.76.128.165:4443/0w0O6 via HTTP, and runs that.
- The second script creates a memory buffer using the VirtualAlloc library call, fetches shell code from 45.76.128.165:4443/0w0O6 via HTTP, copies it into the buffer, and executes the code using CreateThread. This thread then creates another buffer, fills it with a PowerShell script from 45.76.128.165:4443/0w0O6 via HTTP, and runs that, too.
"Based on observations associated with the malicious document, we observed subsequent shell sessions probably associated with Metasploit's Meterpreter that enabled deployment of additional tools and malware preceding deployment of three Shamoon-related files: ntertmgr32.exe, ntertmgr64.exe and vdsk911.sys," continues the report.
The researchers identified two web domains used to host malicious executables and launch the attacks.
- Ntg-sa[.]com that spoofs the legit ntg.sa.com domain of Saudi petrochemical support firm Namer Trading Group.
- maps-modon[.]club that spoofs maps.modon.gov.sa, which is associated with the Saudi Industrial Property Authority.
This information is precious for system administrators that could check any connection to these domains and block it.
The experts exploited the infected machine for reconnaissance, gathering information on the target network and stealing sensitive information. Once completed this phase the attackers deploy the Shamoon payload.
Saudi Arabia is warning local organizations about the Shamoon malware; experts believe that the threat actor behind these operations will continue its activity temporarily disappearing and changing tactic.
The experts at IBM X-Force made an interesting discovery, some of the domains used in the Magic Hound campaign were observed in the Shamoon 2 attacks.
According to the experts at Palo Alto Networks an IRC bot used in the Magic Hound campaign is very similar to a piece of malware used by Newscaster, aka Charming Kitten and NewsBeef, the Iranian actor that targeted individuals in the U.S., Israel and other countries using fake social media profiles.
Iranian hackers appear very active in this period, both Charming Kitten and Rocket Kitten actors were mentioned in an analysis of the MacDownloader malware used to exfiltrate data from Mac computers.
Let's close with a rapid look at the cyber-attacks detected by the researchers over the years:
Date Case Description
February 2016 Iranian hackers compromised former IDF chief's computer According to a report published by the Israel's Channel 10, hundreds of Israel's current and former top security officials have been targeted by Iranian hackers.
December 2015
Iranian hackers penetrated computers of a small dam in NY
Iranian hackers penetrated the industrial control system of a dam near New York City in 2013, raising concerns about the security of US critical infrastructure.December 2015
Cadelle and Chafer, Iranian hackers are tracking dissidents and activists
Symantec has uncovered Cadelle and Chafer groups, two Iran-based hacking teams that were tracking dissidents and activists.November 2015
Facebook first discovered spear phishing attacks of Iranian hackers on State Department employees
Facebook was the first company to notice the intrusion of Iranian Hackers in the e-mail accounts of US State Department officials focused on Iran. The attacks appeared politically motivated and aimed to gather data about US-Iranian dual citizens in Iran.November 2015
New insight on the Rocket Kitten Iranian hacking crew
Experts from Check Point firm published a new report on the Rocket Kitten APT that include more insight into the activities of the group.October 2015
Iranian Cleaver hackers exploit LinkedIn for cyber espionage
The Cleaver group managed a well-developed network of fake LinkedIn profiles for cyber espionage purpose.June 2015
Thamar Reservoir – Iranian hackers target entities in the Middle East
Security experts at ClearSky published a report on the cyber espionage campaign dubbed Thamar Reservoir that is targeting entities in the Middle East.December 2014
Iranian Hackers wiped out machines at Sands Corp Casino
Bloomberg revealed that Iranian hackers used Visual Basic malware to wipe out data from corporate systems at Las Vegas Sands CorpDecember 2014
Operation Cleaver – Iranian hackers target industries worldwide
Security firm Cylance revealed that Iranian hackers target airlines, energy, defense companies worldwide as part of the Operation Cleaver campaign.May 2014 Ajax Security Team lead Iran-based hacking groups
FireEye published a report titled "Operation Saffron Rose" to document the activities of the Iranian hacking group named Ajax Security Team
May 2014
Iranian hackers behind most elaborate spying campaign on social media
Iranian Hackers use a network of fake accounts (NEWSCASTER network) on principal social media to spy on US officials and political staff worldwide, this is reported in an analysis done by iSIGHT Partners.
References
http://securityaffairs.co/wordpress/56348/intelligence/magic-hound-campaign.html
http://securityaffairs.co/wordpress/56095/intelligence/macdownloader-iranian-hackers.html
http://securityaffairs.co/wordpress/52027/cyber-crime/oilrig-campaign-iran-hackers.html
http://securityaffairs.co/wordpress/56327/malware/shamoon-attack-chain.html
http://securityaffairs.co/wordpress/44470/hacking/iranian-hackers-against-israel.html
http://securityaffairs.co/wordpress/42964/cyber-crime/iranian-hackers-penetrated-ny-dam.html
http://securityaffairs.co/wordpress/42277/hacking/42277.html
http://securityaffairs.co/wordpress/24923/cyber-crime/ajax-security-team-iran.html
http://securityaffairs.co/wordpress/41528/cyber-crime/middle-east-android-rats.html
http://securityaffairs.co/wordpress/40828/cyber-crime/iranian-cleaver-hackers-linkedin.html
http://securityaffairs.co/wordpress/30734/intelligence/operation-cleaver-iranian-hackers.html
http://securityaffairs.co/wordpress/31039/malware/iranian-hackers-wiped-sands-corp-casino.html
http://securityaffairs.co/wordpress/25355/hacking/iranian-hackers-social-media.html
https://www.secureworks.com/blog/iranian-pupyrat-bites-middle-eastern-organizations
http://securityaffairs.co/wordpress/37512/cyber-crime/thamar-reservoir-campaign.html
/shamoon-reloaded-mysterious-return-dreaded-wiper/
Hands-on threat intel training










