Cybercrime and the underground market [Updated 2019]
Technology is invading our lives. Every day we perform a multitude of operations using computing devices; we check out bank account balance, we pay parking and we exchange documents with our colleagues and friends. Mobile, social networks and cloud computing are the paradigms that have changed the online user experience; these platforms manage today almost all of the information in the internet, an impressive and priceless amount of data.
The information is money and criminals follow it, the schemes of monetization are various and target every sector. Cybercrime is evolving in complexity and organizational capacity, under many aspects it works exactly as a major enterprise.
Hands-on threat intel training
Cyber-attacks, malware, identity theft, phishing and spam are the emerging threats that menace the users in cyberspace. The attackers commit malicious activity that creates a shadow economy comparable to the one of principal states of the planet.
As usual, the most interesting information on cybercrime activities are provided by the principal security firms that collect data from global intelligence networks able to detect and analyze cyber threats identifying emerging trends in malicious activities. Symantec Security firm publishes annually a very interesting report titled the "Internet Security Threat Report", a complete overview on the principal cyber threats detected by its network during the year. In 2011 Symantec detected and blocked over 5.5 billion malware attacks, an impressive figure with an increase of 81% compared to the previous year, and in many cases the offensives remain undetected for long periods. The situation is worrisome, lack of awareness on principal cyber threat, poor information security in design, users risky behaviors and economic crisis are all factors that concurs to exacerbate the situation.
Cybercrime is assuming an amazing relevance in our lives. What really surprises me are its organizational capability that has nothing to envy to the most efficient industry. It is assuming a typical hierarchical structure in which every actor has a well-defined role and responsibility. From leaders to money mules, cybercrime is practically infiltrating every sector of society. The hierarchy's "executives" oversee operations, define the strategy and the business model to implement, verifying that everything proceed as planned. Core of criminal business is the technology, groups of specialists that are able to deploy sophisticated malware, arrange private botnets, and design fake antivirus software as well as efficient exploit toolkits.
Just like any legitimate organization, the code is reviewed and subject to a strict validation processes. Another interesting aspect is the recruiting process for large-scale operations in which specialized affiliates set up recruitment programs searching for specific technologic profiles to arrange cyber-attacks.
Cyber criminals use to the following to promote their products/services: Internet job boards, hacking message forums, and underground IRC chat channels.
Economic impact of cybercrime
The number of attacks blocked by Symantec is just the tip of the iceberg and cybercrime is surely responsible for the majority of them. The privileged weapons used are the malware, malicious code of increasing complexity that in many cases have eluded security mechanisms, principal vectors of attacks exploited by cybercriminals are web attack kits and socially engineered phishing techniques.
Cybercrime and business
Targeted attacks exploiting zero-day vulnerabilities are the most dangerous, they aren't the most common. The use of exploits of known vulnerabilities for which a slow, and often incorrect patch management process exposes IT infrastructures to concrete risk to be compromised.
The following is some data provided by Symantec in the report related to malicious activity related to cybercrime:
- Web based attacks increased by 36%, with over 4,500 new attacks each day.
- 403 million new variants of malware were created in 2011, a 41% increase of 2010.
- SPAM volumes dropped by 13% in 2011 over rates in 2010.
- 39% of malware attacks via email used a link to a web page.
- Mobile vulnerabilities continued to rise, with 315 discovered in 2011.
Looking at the data, it's easy to foresee a further increase of the phenomena also for 2012.
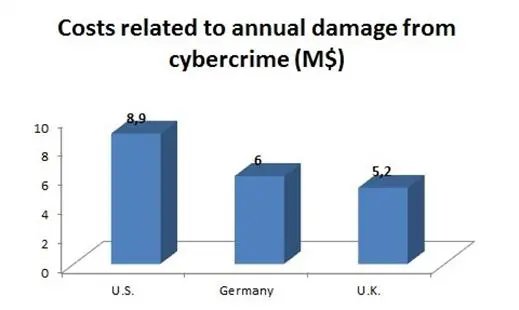
In October 2012, Ponemon Institute Research, Sponsored by HP Enterprise Security, published the report "2012 Cost of Cyber Crime Study: United States" that quantifies the economic impact of cybercrime on the US economy, and the report proposes worrying scenarios. Cybercrime impact has been estimated in reaching $8.9 million in 2012, and average annual cost increased 6 percent in respect to the previous year, an impressive growth that has been driven up by attacks on websites, denial-of-service attacks and malicious insiders.
Companies are daily victims of different type of attacks such as data breaches, system destruction and violation of networks. It has been estimated that there are an average of 1.8 successful attacks each week.
The US has suffered the largest cost cost, followed by Germany with $5.9 and Japan at $5.1. Cybercrimes are very costly for organizations, despite the organizations size. All industries fall victim to a different degree.
Figure 1 - Total cost of cybercrime 2012 - Ponemon Institute
Small organizations pay a higher per capita cost than respected big enterprises. Ponemon Institute estimated in 2012 a cost per seat of $1,324 for small businesses and of $305 for enterprises. The industries with the highest cost for cybercrime are defense, utilities and energy and financial service.
The cyber-attacks which cause major economic losses are denial of service (DOS), malicious insider and web-based attacks. They represent the 58 percent of all cybercrime annual costs per organization, the research demonstrated that the impact of cybercrime is higher if mitigation solutions are applied late.
Cybercrime, a social threat
Governments, intelligence agencies and law enforcement agree on the consideration that cybercrime represents one of the primary threats to the security of collectivity; it has equal and devastating impact on industries and private citizens. The "2012 NORTON CYBERCRIME REPORT" provided interesting elements to evaluate the incidence of cybercrime in the daily users experience online.
The scale of consumer cybercrime is amazing – 1.5 million daily victims that amounts to an annual global cost of $110 billion.
Four out of ten social network users have fallen victim to cybercrime but the data that is more worrisome is that one out of six users report that someone has committed a cyber-attack to their profile, typically it is hacked by someone that pretend to impersonate them. Social network platforms and mobile platforms are considered privileged channels for scams and frauds; a new wave of malware is targeting the powerful platforms and their users.
The highest numbers of cybercrime victims are located in Russia, China and South Africa, countries where malicious activities are very popular.
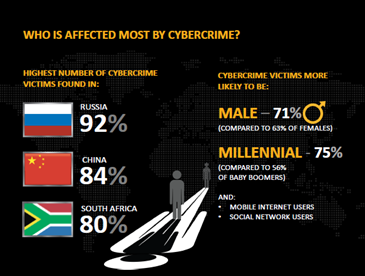
Figure 2 - Geographic location of victims (Symantec)
The data demonstrate the efficiency of cybercrime activities and justify the concerns of security community and governments, criminals are evolving their techniques adapting them to the evolution of IT tools.
Deep in the cybercrime underground
It's impossible to provide a clear picture of the wide worldwide hacker community, a complex universe composed by a wide number of groups that share opinions, tools and any other information on dedicated and self-managed forums. The platforms are various; every technology is good if the final intent is sharing, even better if it is possible to keep away law enforcement and other prying eyes.
These places were are also used for illegal activities such as the sale of malicious code and the providing of hacking services, a black market that is reaching impressive figures.
Many security companies have tried to infiltrate these groups, they represent an incredible source of information and their monitoring could allow to discover the cybercrime trends and to detect new cyber threats and new dangerous customization of well know malware.
Recently, Trend Micro published a fascinating report on the Russian underground, one of the most active cybercriminal communities, proposing interesting considerations on principal products and services available on the black market and their prices.
The study showed data collected during the analysis of online forums and services attended by Russian hackers such as carding-cc.com, antichat.ru, xeka.ru, and carding-cc.com. Online it is possible to acquire all the necessary resources to conduct a cyber-attack or to realize a sophisticated fraud without having particular skills. The list of criminal activities is long, as is the range of products and services offered to the buyers for relative cheap prices. The following is a list of the principal "articles" sold in the underground ranked by popularity and the number of requests:
- Programming services and software sales
- Hacking services
- Dedicated server sales and bulletproof-hosting services
- Spam and flooding services, including call and SMS flooding services
- Download sales
- DDoS services
- Traffic sales
- File encryption services
- Trojan sales
- Exploit writing services and sales
Cyber criminals have discovered the possibility to provide malicious services renting tools, botnet architectures and cloud infrastructures providing computational resources on demand. The innovation is represented by the possibility to offer also an efficient "customer care" to support customers in their initiatives and social networks platform to manage the community of clients and communicate with them rapidly. The business model is consolidated and adopted by various criminal organizations. Security experts dubbed it malware-as-a-service, and on June 2012 experts of the AlienVault security firm discovered a service called Capfire4 that offered cyber-attack tools and.
Figure 3 - Capfire4 - Malware as a service
Trend Micro confirmed that programming services and software sales were the most common services in the underground market. The sale of brute-force tools, DDoS bots and exploit toolkits is feeding the growth of a shadow economy that is increasingly becoming a serious threat for governments.
The information security company Group-IB published a study on the Russian cybercrime market estimating an amount of $2.3 billion in 2011.
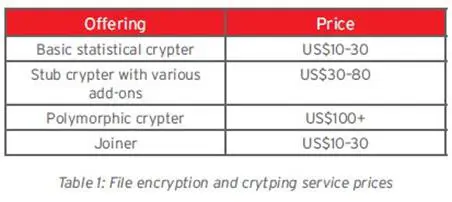
Very popular are file encryption and crypting services for malware creation – essential components to allow a malicious code to avoid detection by defense systems. The most important module for crypting services is the crypter stub used to code/decode a malicious software.
Crypters can be classified as either statistical or polymorphic.
- "A statistical crypter's stub is a separate program to which the encrypted file is tied. When launched, the file is extracted, decoded, and executed."
- "Polymorphic crypters are considered more advanced. They use state-of-the-art algorithms that utilize random variables, data, keys, decoders, and so on. As such, one input source file never produces an output file that is identical to the output of another source file."
In the following table is the proposed price list for crypters. It is possible to note that is very convenient for criminals to acquire them improving the efficiency of their malware, making the detection process very difficult.
Figure 4 - Encryption Services Price List
In many cases it could be useful to acquire the entire malware requesting specific customization to the creators that also provide the environments to spread the malware. One of the most popular case studies is related to the famous Zeus malware offered everywhere in the underground with a moderate cost, which often includes hosting services. Following some posts published on Russian forums:
"I'll sell ZeuS 2.0.8.9 source code. Private sale of source code. Price: US$400–500; bargaining (swapping) is possible."
"Selling ZeuS 2.1.0.1 bin + set up on your hosting for US$200 escrow is accepted."
"I'll sell a Zeus 2.0.8.9 builder + administration controls. I also do builds. Price: US$300. Build price: US$100."
"LOGS-ZeuS logs (2.4Gb) DE FR IT GB, price: US$250."
"Installation of ZeuS in your host: US$35. Installation of ZeuS in my host: US$40."
"Setup of ZeuS: US$100, support for botnet: US$200/month, consulting: US$30."
Always in the Russian underground, Group-IB discovered the sale of new variant of banking trojan called Carberp that will be used in future attacks against financial institutions. Sellers also started to provide special service of individual «web-injects» developments for major US and Canadian banks such as WellsFargo, Citi, JP Morgan Chase, Bank of America, TD, and many others.
Figure 5 - Carberp sale on Russian Forum (Group IB)
The most interesting feature is a new bootkit module, the price of which is 40 000 USD or 10 000 USD on rent per month. It helps to infect an MBR record which means that the hacker will have a long term opportunity to control the victim without antivirus notifications.
Also in this case, malware sellers started to use new scheme of Carberp sales by the opportunity of its rent, which was popular in selling of very qualified written and professional banking malware from a very old famous underground networks called «RATNET» (valenok and htum were one the most famous vendors of the professional private banking spyware for US and Canadian banks).
The sales model known as "malware as a service" is very dangerous because it open the doors to ordinary crime that without particular knowledge could move serious attacks against banking systems. In some cases, to protect their anonymity, they deploy the sales structure in the deep web, like what happened to Citadel. Security blog S21Sec discovered last year a new version of Citadel deployed in the Deep Web and developed to avoid detection and analysis, usually done using sandboxes.
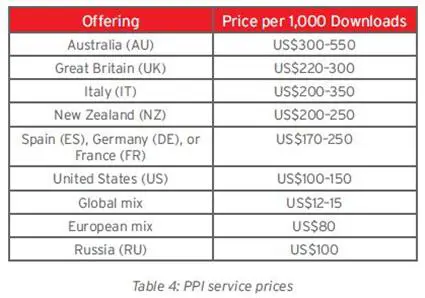
Other items often requested in the underground are the Pay-per-install services such as download services, criminals provide the malicious file to a service provider, or ask it for a customization of most common malicious agents, and the provider manages the distribution aspects for them.
"Download services are usually offered based on the target country. The value of traffic is primarily based on how important its owner is. The bigger the organization it belongs to, the more expensive it is"
Figure 6 - Pay-per-install services price list (TrendMicro)
Are you wondering how it is possible that I have forgotten DDoS attacks and botnets, and often related events that cause major problems for institutions and companies? The answer is simple, I have not forgotten them but I preferred first to introduce activities through which it is possible to identify a direct process of monetization.
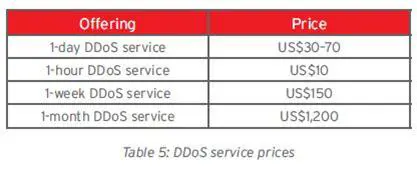
In fact, even botnets are often used to spread malware. Despite the fact that DDoS attack are very dangerous for IT infrastructures, it is simple to acquire tools to conduct this type of attack or to rent a "one-day denial-of-service", which criminals have to pay a cost from $30 to $70.
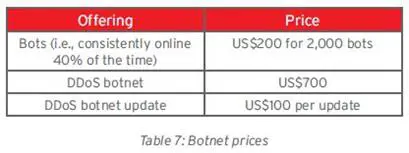
To arrange DDoS attacks, criminal need to use specially crafted bots and botnets. This means that he must obtain access to a huge quantity of machines and installs a daemon on it using his DDoS bot kit. In the following table are the reported costs for DDoS service renting and botnet renting, which is extremely cheap.
Figure 7 - DDoS service prices (Trend Micro)
Figure 8 - Botnet prices (Trend Micro)
Figure 9 - Botnet Renting
The data provided is similar to the ones proposed by other security firms such as Fortinet and Imperva. Fortinet, the worldwide provider of network security applications and a market leader in unified threat management (UTM), has recently published the report "Fortinet 2013 Cybercrime Report" that deepens the phenomenon of cybercrime. The following is the Cybercriminal Pay Rates proposed by Fortinet in the report:
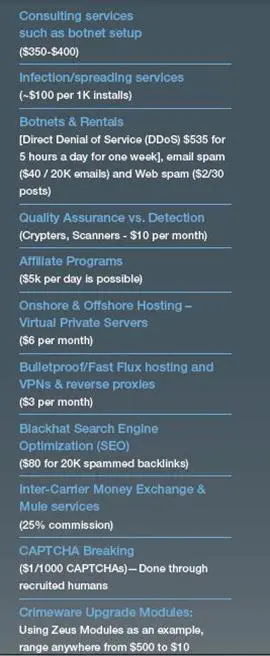
Figure 10 - Malicious Services Price List (Fortinet)
What are the most efficient deliverables in cybercrime?
They are various and they range from hacking services to the production of malicious code customizable according to the clients request.
The following principal services are offered along with their related prices:
- Consulting services such as botnet setup ($350-$400)
- Infection/spreading services (~$100 per 1K installs)
- Botnets & Rentals [Direct Denial of Service (DDoS) $535 for 5 hours a day for one week], email spam ($40 / 20K emails) and Web spam ($2/30 posts)
- Quality Assurance vs. Detection (Crypters, Scanners – $10 per month)
- Affiliate Programs ($5k per day is possible)
- Onshore & Offshore Hosting – Virtual Private Servers ($6 per month),
- Bulletproof/Fast Flux hosting and (VPNs & reverse proxies ($3 per month)
- Blackhat Search Engine Optimization (SEO) ($80 for 20K spammed backlinks)
- Inter-Carrier Money Exchange & Mule services (25% commission)
- CAPTCHA Breaking ($1/1000 CAPTCHAs)—Done through recruited humans
- Crimeware Upgrade Modules: Using Zeus Modules as an example, range anywhere from $500 to $10K
The above deliverables are provided using different modalities such as renting, buying or leasing to respond to the client's needs.
Money Laundering
A profitable industry needs to reinvest illegal profits in legitimate business, a fundamental role in cyber-criminal organizations covered by the "money mules", individuals who are knowingly or unknowingly used to launder a crime syndicates' illegal gains. Money mules are used to anonymously transfer money from entities, typically through anonymous wire transfer services such as Western Union, Liberty Reserve, U Kash and WebMoney. Virtual currency services such as Bitcoin offer a valid instrument for money laundering preventing that law enforcement will be able to intercept the payment made to finance illegal activities.
Usually, each sale transaction is fragmented into smaller batches to elude controls operated by law enforcement. Cyber criminals' organizations are structured like businesses. They develop a detailed business model and monetization strategy "because even an illegal company needs to 'pay the bills' in order to function on a day-to-day basis". Money Management is vital aspect, as organizations have to track the resources used and the earns for their utilization, they do this utilizing commercial business process management tools, financial systems and many other instruments to manage everything from software development to accounts payable.
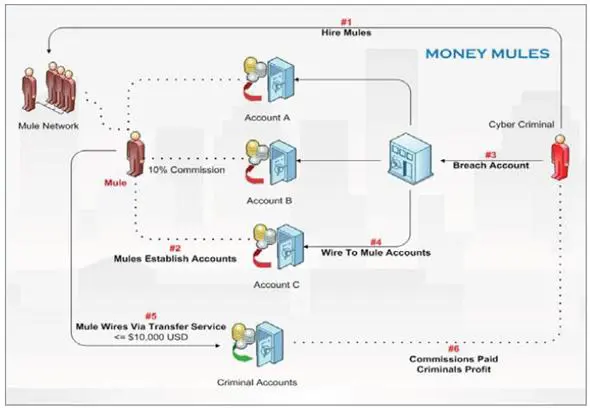
Figure 11 - Money Laundering Schema (Fortine)
Zero-day vulnerabilities market and its trends in cybercrime world
During the last month, I have had the opportunity to collaborate with security experts from the information security company Group-IB, a security firm that is very active in the fight against cybercrime. The company has recently received a grant in the amount of 30m rubles (approximately $966,000) for the development of a global counter-cybercrime system named the CyberCop. The collaboration was for me the opportunity to look at a lot of interesting information on the evolution of the cybercrime phenomena. The company faces lots of penetration testing and vulnerability assessments jobs for the financial and industrial sector, activities made possible with the elaboration of its own statistics to figure that the stable directions of vulnerabilities research from cyber criminality are in:
- 75% - modern WEB-browsers (Internet Explorer, Firefox, Google Chrome and etc.); the most interesting is Safari also, because of that the interest of professional hackers is in theft of rich people, who traditionally use MacBooks and other kind of Apple products. Not all vendors are ready to update their software quickly, that's why criminals use it for spreading malware through vulnerabilities in plugins designed for these browsers. For now, there were not a lot of private vulnerabilities in this sphere, due this reason there are a lots of modifications of exploit-packs with known vulnerabilities (like Stynx exploit-pack and many others). Most efficiency, modern exploit-packs include special modules called «Plugin Detect», which help not to run exploits on non-vulnerable client (http://pastebin.com/raw.php?i=v0nccWXF - one of the POCs). One of the latest trends is in that criminals began to use SaaS services for automatically exploit-pack generation and obfuscation. It helps them to automate their work and to crypt it against anti-viruses more efficiently.
Figure 12 - Stynx exploit-pack
- 15% - modern AV and security software (mostly HIPS) for heuristic bypass. Good examples are the methods of Microsoft UAC bypass; some of them are traded on black market for really big money. Another kind of flaws – vulnerabilities in ring3 or ring0 (drivers) modules of modern AV and HIPS/FW – (often combined with malware for bigger price);
- 10% - vulnerabilities for privilege escalation, most of them are used on Microsoft Windows for placing malware and for bypassing administrative restrictions; another side is to use them on compromised WEB-servers under FreeBSD or Linux, which the hacker has not enough rights to do any question (to edit a page for placing malware, to add new user, to dump database, to read the exact file and etc.)
One of the most interesting vulnerabilities related to AV and security controls bypass is UAC bypass used in famous banking Trojan Carberp by "auto-elevation" for certain processes started from explorer.exe and injection in to explorer.exe. This technique can be also used for Windows 8 DP, CP all 32-bit for admin with default UAC settings, which is standard situation. Once disabled UAC it is also possible to turn AV off or to modify its resources, that's why such vulnerabilities are very important and private methods of them cost a lot of moneys. They are rather rare, because for it you need to do deep research of OS architecture. Often such kinds of methods are combined with so called "bootkits", which infect MBR for silent long-term work as in new modifications of Carberp. The next scenario is to place remote connection modules by patching RDP or placing modified VNC or Team Viewer servers for reverse connections to the victim and organizing a new transfer under its IP address. That's why modern antifraud systems are unable to detect fraud if the hacker uses the standard limits, if the bank does all work from the compromised PC.
Other areas of interest for underground hacking communities are:
- Use of mobile malware for online-banking. Mobile banking will be the sector more impacted according security experts, a new wave of cyber-attacks is expected, financial institutions and their users will be victims of new offensive especially against all that services implemented on mobile platforms. Several month ago Group-IB Forensics Lab detected mobile-banking malware through Google Play by Sberbank request (Russian leading national bank), demonstrating that cybercriminal try also to exploit legitimate channels to spread malicious agents.
- Vulnerabilities in industrial sector. The interest of hackers can be divided into financial fraud in industrial (especially in oil and gas sector) and remote attacks of SCADA/ICS infrastructures. The first one is traditionally organized in cooperation with internal employees of industrial companies or only by them. They can use vulnerabilities in billing software and to modify the values of it, which helps them to make lots of dirty business. Group-IB discovered this trend in petroleum sector, especially in retail network and branches companies; in many cases they need special malware for doing it. Most of the vulnerabilities related to such segment is in frontends of SCADA applications and its WEB-application modules:

Figure 13 - Industrial vulnerabilities discovered by Group-IB
Remote attacks have as primary purposes the cyber espionage as offensive business intelligence and vandalism "just for fun". Lots of SCADA environments can be probed remotely by special signatures of network services. The ways of exploitation in modern industrial sector are often privately spread because they are depended on the OS, for example real-time OSs like QNX are really hard to compromise and mostly they are isolated from the ISP. Hackers sell automatic tools that are able to find services exposed by SCADA systems but also public repositories such as the popular Shodan (http://www.shodanhq.com/) search engine could be used to gather precious information for attacks.
Security firms use similar tools to detect potential targets of the cybercrime, in the next picture is proposed the Group-IB automated systems for SCADA environments detection. It is easily seen that it plots the site of interest on the map where are located potential targets such as industrial infrastructures.
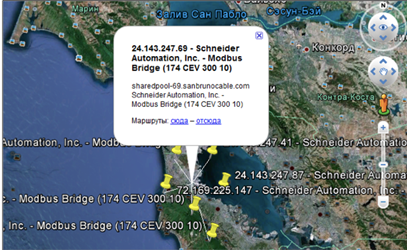
Figure 14 - SCADA detection system (Group-IB)
More than 6000 control systems can be easily found through the WEB, which is really great threat to the industrial sector. The attackers began to use non-standard ways for attacking SCADA environments such as satellite telemetry terminals, video-cameras, alarm-management devices and etc.
The trend for 2013-2016 years will be in that lots of vulnerabilities on software will be used as cyber warfare products on banking and industrial sector. Lots of cybercrime will be organized through alternative and mobile platforms.
Cybercrime, the endless war
The fight to cybercrime is an arduous task an endless clash between the law enforcement and cyber-criminal groups that are growing under organization aspects and that are able to provide products and services more and more advanced. Cybercrime is a worldwide phenomenon that menaces economics and the security of every state. Governments and law enforcements must cooperate to face with cyber threats.
Sharing data on criminals' events is a crucial step. Information must be proposed to common people through an awareness campaign. Private business and governments must collaborate to monitor criminal activities detecting them as soon as possible via the monitoring of internet, especially of underground forums.
The detection of criminal activities could be improved using security intelligence systems such as SIEMs, the definition and the share of security best practices is another aspect that could limit the level of penetration for cybercrime in private business and moderates the cost of cybercrime, let's think for example to the possibility to avoid spear phishing attacks due a proper awareness campaign.
Of course, all these reasons must be supported by the establishment of a legal framework accepted globally that severely punishes cyber criminals everywhere they operate. Unfortunately, we are still far from these conditions that are absolutely necessary to cope with an industry that knows no crisis and that is showing frightening growth.
Pierluigi Paganini
Special Thanks to Andrey Komarov, Head of International Projects Department at Group-IB, and to his team for the precious collaboration