How hackers use CAPTCHA to evade automated detection
Introduction
CAPTCHA seems to be everywhere we look. These sloppy characters are on blogs, ticket websites, shopping portals — you name it. Those cars you need to spot in a block of images before you can access a website? That’s CAPTCHA too. CAPTCHA was invented to help sites distinguish human users from bots and automated hacking tools. But little did its creators know that cybercriminals would one day be leveraging it to bypass automated detection.
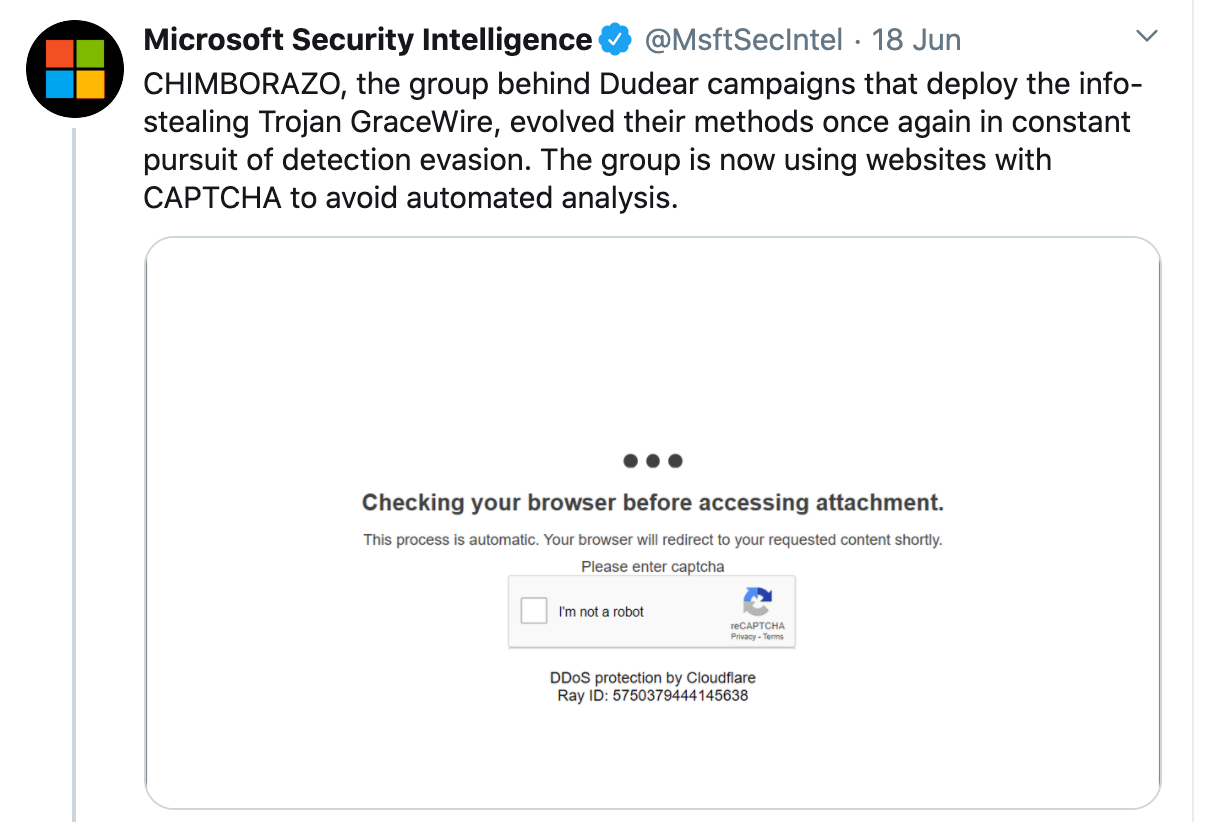
Microsoft recently announced that its Security Intelligence team had identified a malicious Excel campaign involving CAPTCHA. As per the company’s statement, the cybercriminal group CHIMBORAZO is distributing infected Excel documents that redirect users to a Cloudflare DDoS protection page featuring Google reCAPTCHA. Solving the CAPTCHA puzzle then downloads a malicious .xls/.xlsm file, which then infects the victim’s computer with the password-stealing GraceWire Trojan.
Hands-on threat intel training
CAPTCHA Excel malware named Campaign Dudear
Microsoft said that the company has been tracking Chimborazo’s activities since January 2020. The group behind the Dudear campaigns involving info-stealing HTML redirectors are now using advanced methods to evade detection. Requiring users to complete CAPTCHA allows hackers to bypass automated analysis that security programs use to identify and block attacks.
Typically, email virus detectors examine files for exploitable code, drivers, libraries and so on upon the first click. Other programs collect malware samples and execute them in virtual machines for thorough analysis. But requiring a CAPTCHA means the analysis can only be done after the user downloads a malicious file. So the automated analysis gets put on the back burner, increasing the odds of the exploitable code escaping detection and helping adversaries deploy GraceWire.
Microsoft dubbed the ongoing CAPTCHA Excel campaign Dudear, as it’s the part of a bigger phishing campaign aiming to inject the GraceWire payload in users’ systems.
Adversaries distributing Excel files via phishing campaigns and embedded web links
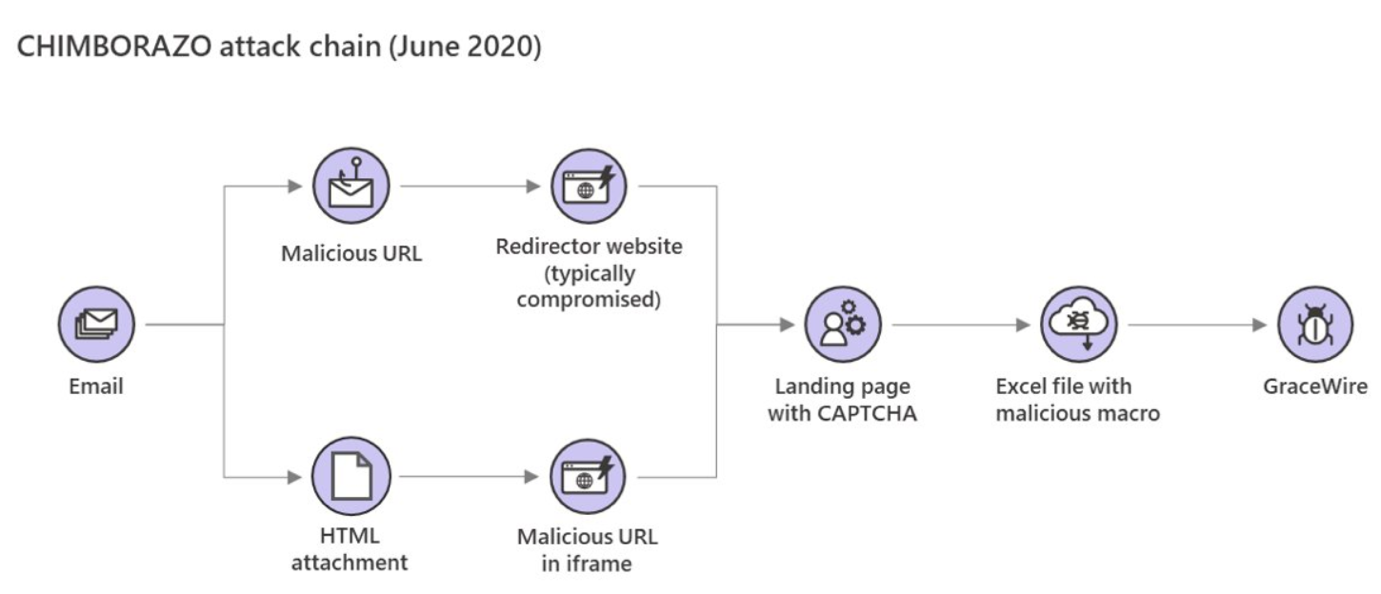
Microsoft also observed the way Chimborazo has been distributing Excel files. The group was initially distributing infected documents through attachments in phishing campaigns. Later, they were spreading it through embedded web links. The group then experimented with phishing messages featuring links that either led to redirector websites (aka compromised legitimate websites) or HTML attachments containing a malicious iframe tag.
In either case, the target is asked to solve CAPTCHA before they can download the document. Once they do, the Excel document releases macros that install the GraceWire Trojan to steal sensitive information such as email and online banking passwords.
Here’s a visual of Chimborazo’s attack chain:
Back in January, the Microsoft Security Intelligence group revealed that Chimborazo leveraged an “IP traceback service” to track the internet protocol addresses of systems that download the malicious CAPTCHA Excel documents, likely also to bypass automated analysis. It was at that time that the company had first seen the hacking group utilize redirector websites.
The CAPTCHA bypass technique isn’t something new
CAPTCHA-based evasion techniques aren’t uncommon. Last year, security researchers at Cofense detected a phishing campaign that relied on CAPTCHA to evade secure email gateways. Researches revealed that adversaries were sending targeting organizations with emails that contained a voip2mail voicemail from a co-worker. If a user clicks the URL to hear the voice message, they’re taken to a webpage where they’re asked to solve a CAPTCHA puzzle.
Upon solving the CAPTCHA, the user is prompted to choose a Microsoft account and login. Once they do, all the information entered is stolen by cybercriminals. Those who implemented this technique were also clever enough to use a different webpage for the Captcha verification test. What this means is that clicking CAPTCHA redirects to a webpage hosting the malware, while the original page (i.e. the page that opened after a user opened the voice message) remains clean.
So when an SEG (secure email gateway) scanned the webpage URL present in the voicemail, it could only scan as far as the first page requesting the CAPTCHA, which didn’t carry any malware. The use of the layered webpage effectively forces the SEG to mark the first page as safe and let the user through.
Conclusion
The Microsoft Security Intelligence team confirmed that products like Microsoft Defender ATP help in detecting the CAPTCHA Excel threat. Still, it would be best if you take caution when downloading any Excel documents that redirect you to a webpage asking for CAPTCHA verification. This also applies to any Microsoft Office files that you enable editing for. Remember, there is no good reason for a legitimate Excel attachment (or any other document) to have CAPTCHA, so be wary of files allowing for downloads this way.
Sources
Hackers force users to solve CAPTCHA, Gridinsoft Blog
The Dark Side of CAPTCHA, Everyone's Least-Favorite Security Tool, MEL Magazine
Microsoft Phishing Page Uses Captcha to Bypass Automated Detection, Bleeping Computer