Unprotected MongoDB Installations: Child's Play for Hackers
Hacker held open MongoDB databases for ransom
In the last weeks, security experts observed a significant increase in ransom attacks against unprotected MongoDB databases.
Victor Gevers, the Co-founder of the GDI Foundation, was the first expert that noticed the attacks and warned of poor security for MongoDB deployments in the wild.
Hands-on threat intel training
In a first time, the security researcher discovered 196 instances of MongoDB that were wiped by cyber criminals that were held for ransom.
The expert also noticed that a hacker who goes by online moniker Harak1r1 was behind the ransom attacks. The cyber-criminal was demanding 0.2 BTC, roughly $200 at the time of the attacks, to restore the installation. To verify the ownership of the installation, Harak1r1 requests system administrators to provide their email.
For hackers and security experts is quite simple to identify open MongoDB installations by using custom scripts or search engines like Shodan and Censys.
On December 27, Gevers discovered a MongoDB server that was left open without authentication through the Internet.
"Unlike other instances, he discovered in the past; this one was different. When he accessed the open server, instead of looking at the database's content, a collection of tables, Gevers found only one table, named "WARNING."" reads a blog post published on bleepingcomputer.com.
The attacker accessed the open MongoDB database, exported its content, and replaced all data with a table containing the following code:
{ "_id" : ObjectId("5859a0370b8e49f123fcc7da"), "mail" : "harak1r1@sigaint.org", "note" : "SEND 0.2 BTC TO THIS ADDRESS 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq AND CONTACT THIS EMAIL WITH YOUR IP OF YOUR SERVER TO RECOVER YOUR DATABASE !" }
"I was able to confirm [this] because the log files show clearly that the date [at which] it was exported first and then the new database with tablename WARNING was created," Gevers told BleepingComputer. "Every action in the database servers was being logged."
The security researcher notified victims their database were hacked:
"Criminals often target open databases to deploy their activities like data theft/ransom. However, we also have seen cases were open servers like these are used for hosting malware (like ransomware), botnets and for hiding files in the GridFS," he wrote in the notification letter sent to the victims.

Figure 1 - Hacked MongoDB Installation
Gevers searched on Google for the email address used by the hacker and the Bitcoin address used for the payments. The analysis of the Bitcoin address allowed him to verify how many other users were victims of the same attacker. At the time of this writing, the analysis of the Bitcoin wallet used by Harak1r1 revealed that at least 22 victims appeared to have paid.
In the following weeks, the number of hacked MongoDB databases rapidly increased.
According to the Australian Communications and Media Authority Antipodes, the number of systems compromised by hackers more than double to 27,000 in just a day.
The analysis of the Bitcoin wallet used by Harak1r1 revealed that at least 22 victims appeared to have paid.
The security researcher Niall Merrigan explained that the number of attacks has soared from 12,000 earlier to 27,633 in just 12 hours. The expert believes the ransom attacks were powered by at least 15 different actors. One of the attackers goes online with the moniker 'kraken0,' and he has compromised 15,482 MongoDB databases, demanding victims the payment of 1 bitcoin ($US921).
Merrigan explained that hackers follow a specific strategy, they use Shodan to scan for open MongoDB databases, then connect them using anonymous access to list all available databases.
Crooks may or may not download the database before wiping the archive; they use to leave just a single file that informs victims of the attack and instruct them on how to pay the ransom.
According to the researcher Adrian Sanabria (@sawaba), Shodan only reports a varying fraction of the overall number of MongoDB in the wild open to the Internet, for this reason, Gevers also analyzed another search engine called ZoomEye who reported 99,491 candidates.
Merrigam and Gevers collected information about compromised MongoDB installations and related actors in the following document:
https://docs.google.com/spreadsheets/d/1QonE9oeMOQHVh8heFIyeqrjfKEViL0poLnY8mAakKhM/edit#gid=0
"It's like the kidnappers keep delivering the ransom notes, but you don't know who has the actual original data," Merrigan said. "That's why we're tracking the notes, so that if we see the [databases] are being exfiltrated by the thieves, we can know the guys who should actually get paid if they want to get their data back."
A few days later the Australian Communications and Media Authority Antipodes, that is monitoring exposed MongoDB installations since July 2015 using intelligence provided by the ShadowServer nonprofit, reported about 400 exposed MongoDB databases a day to 90 percent of Australia's network providers via the Australian Internet Security Initiative (AISI).
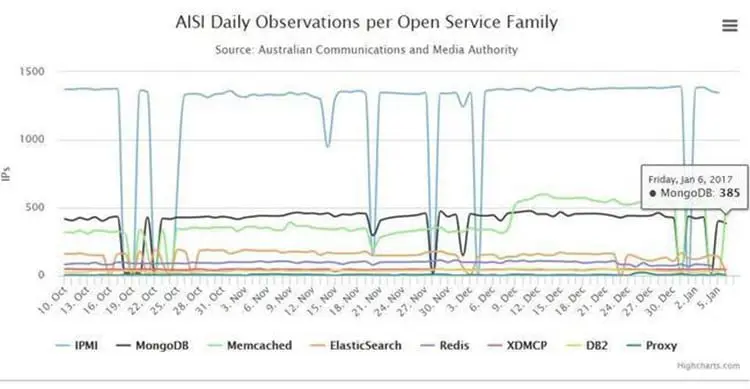
Figure 2 - AISI statistics on Exposed MongoDB published by ElReg
It is interesting to note that the same hackers behind the MongoDB installs have started targeting Elasticsearch clusters that are unprotected and accessible from the internet.
Elasticsearch is a Java-based search engine based on the free and open-source information retrieval software library Lucene. It is developed in Java and is released as open source; it is used by many organizations worldwide.
Crooks are targeting Elasticsearch cluster with ransom attacks in the same way they have made with MongoDB.The news was confirmed on the official support forums this week, a user who was running a test deployment accessible from the internet reported hackers removed all the indices and added a new index "warning" was created there.
The user has found the following text from the raw index data:
"SEND 0.2 BTC TO THIS WALLET: 1DAsGY4Kt1a4LCTPMH5vm5PqX32eZmot4r IF YOU WANT RECOVER YOUR DATABASE! SEND TO THIS EMAIL YOUR SERVER IP AFTER SENDING THE BITCOINS…"
Something quite similar to the recent ransom attacks against MongoDB.
"Late last week, a malicious attack was initiated, in which data from thousands of open source databases was copied, deleted and held for ransom. Although no malware, or "ransomware" was used in these attacks, and they are not related to product vulnerabilities, they nonetheless represent serious security incidents involving a data loss, or even a data breach." reads the description of the discussion in the official forum. "The good news is that data loss from similar attacks is easily preventable with proper configuration."
According to the security researcher Niall Merrigan, more than 600 Elasticsearch clusters have been targeted by the hackers.
Unfortunately, the number of Internet-accessible Elasticsearch installs are much greater, roughly 35,000. The experts believe that the number of wiped Elasticsearch installs would rapidly increase, as it has happened for the MongoDB databases.
MongoDB attacks - Looking back
In December 2015, the popular expert and Shodan creator John Matherly found over 650 terabytes of MongoDB data exposed on the Internet by vulnerable databases.
Matherly warned the IT industry of the presence of vulnerable MongoDB online in July 2015, when he revealed that many MongoDB administrators exposed something like 595.2 terabytes of data by adopting poor configurations, or un-patched versions of the MongoDB.
He found nearly 30,000 unauthenticated MongoDB instances; then he decided to monitor the situation over the time.
Matherly observed the majority of vulnerable databases are hosted on cloud computing platforms run by Amazon.com, Alibaba Group, and DigitalOcean.
Unfortunately, many other vulnerable databases are exposed on the Internet including Redis, CouchDB, Cassandra and Riak as confirmed by Matherly.
Other clamorous cases of open MongoDB exposed on the Internet were found by the researcher Chris Vickery. In December 2015 Vickery discovered 191 million records belonging to US voters online.
The records include voters' full names, unique voter IDs, unique voter IDs, date of births and phone numbers.
Vickery has also found his own information in the database containing 300GB of voters' data.
"My immediate reaction was disbelief," Vickery said. "I needed to know if this was real, so I quickly located the Texas records and ran a search for my own name. I was outraged at the result. Sitting right in front of my eyes, in a strange, random database I had found on the Internet, were details that could lead anyone straight to me. How could someone with 191 million such records be so careless?"
In April 2016 Vickery discovered another 132 GB MongoDB database open on Amazon's AWS and containing 93.4 million Mexican voter records
The archive went online for at least eight days after Vickery discovered it, but the bad news is that the database was set for a public access since September 2015.
"There was no password or authentication of any sort required. It was configured purely for public access. Why? I have no clue." states the post published by Chris Vickery.
"After reporting the situation to the US State Department, DHS, the Mexican Embassy in Washington, the Mexican Instituto Nacional Electoral (INE), and Amazon, the database was finally taken offline April 22nd, 2016."
Giving a close look at the records in the archive, the expert discovered it contains all of the information that Mexican citizens need for their government-issued photo IDs that allow them to vote.
The records include the voter's name, home address, birthdate, national identification numbers, and other info.
The Mexican Elections Commissioner confirmed the authenticity of the information included in the archive.
Once of the most recent case of MongoDB left open online is dated back March 2016, when Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
The researcher confirmed that the database behind the Kinoptic iOS app remained online, although the application was removed from the official Apple Store. The disconcerting aspect of the story is that the developers of the Kinoptic iOS app abandoned their service, leaving the data exposed on the Internet, it was a gift for crooks that could use them to target the unaware users.
The database was available without authentication and includes usernames, email addresses, and hashed passwords, along with other details stored in profiles managed by the Kinoptic iOS app.
Vickery tried to report the issue to both Kinoptic developers and Apple. The Kinoptic team has never replied to the expert.
How to protect your MongoDB installation against ransom attacks?
According to the suggestions provided by the Gevers, it is necessary to block access to port 27017 or limit access to the server by binding local IPs to protect the MongoDB installations.
MongoDB admins could also restart the database with the "–auth" option after they've assigned users access.
Below other tips useful for MongoDB admins:
- Check the MongDB accounts to see if no one added a secret (admin) user.
- Check the GridFS to see if someone stored any files there.
- Check the logfiles to see who accessed the MongoDB (show log global command).
Let me close this post with the Security Checklist published by MongoDB at the following URL:
- Enable Access Control and Enforce Authentication
- Configure Role-Based Access Control
- Encrypt Communication
- Encrypt and Protect Data
- Limit Network Exposure
- Audit System Activity
- Run MongoDB with a Dedicated User
- Run MongoDB with Secure Configuration Options
- Request a Security Technical Implementation Guide (where applicable)
- Consider Security Standards Compliance
References
http://securityaffairs.co/wordpress/55018/cyber-crime/mongodb-hacked.html
http://securityaffairs.co/wordpress/55197/hacking/mongodb-attacks.html
http://securityaffairs.co/wordpress/45413/digital-id/kinoptic-ios-app-db-online.html
http://securityaffairs.co/wordpress/55327/hacking/elasticsearch.html
http://securityaffairs.co/wordpress/42897/hacking/mongodb-vulnerable-databases.html
http://securityaffairs.co/wordpress/46588/breaking-news/mexican-voter-records.html
http://www.theregister.co.uk/2017/01/11/mongodb_ransomware_followup/










