Unit 61398: Chinese Cyber-Espionage and the Advanced Persistent Threat
In the world of computer security, the concept of an "Advanced Persistant Threat" has garnered a great deal of publicity recently. Commonly referred to by the abbreviation "APT," the term denotes a specific type of information security risk with a much greater magnitude than the average "skr1pt kiddie." The fundamental elements of an APT typically involve groups of highly adept IT professionals with the funding and resources required to maintain a constant onslaught of cyber-attacks against their target organizations. The term is often employed in reference to the cyber-warfare capabilities of nation-states, however, it's scope is not limited to foreign governments.
The internet security firm Command Five defines an APT in the following manner:
Hands-on threat intel training
The term APT is commonly used in reference to the cyber threat posed by foreign intelligence services, or hackers working on behalf of such entities, but is not limited just to this and can equally be applied to other threat actors such as organized crime syndicates and those involved in traditional espionage.
While the term APT is broad in this sense, it is widely accepted that the most formidable APTs are based in the intelligence services of foreign governments. Examples include the growing cyber-espionage divisions of countries such as Iran, Russia, and the People's Republic of China.
The majority of experts in the field of cyber-security consider China to be our most active and capable adversary. The policy community has become increasingly cognizant of this fact as well. In October of 2011, U.S. Representative Mike Rogers stated:
China's economic espionage has reached an intolerable level and I believe that the United States and our allies in Europe and Asia have an obligation to confront Beijing and demand that they put a stop to this piracy. Beijing is waging a massive trade war on us all, and we should band together to pressure them to stop. Combined, the United States and our allies in Europe and Asia have significant diplomatic and economic leverage over China, and we should use this to our advantage to put an end to this scourge.
For the last decade, the Chinese have systematically targeted and exfiltrated sensitive information from the US government, as well as private sector entities. The following figure is a timeline of cyber-espionage attacks originating from China covering the years 2006-2012, delineated by industry sector.
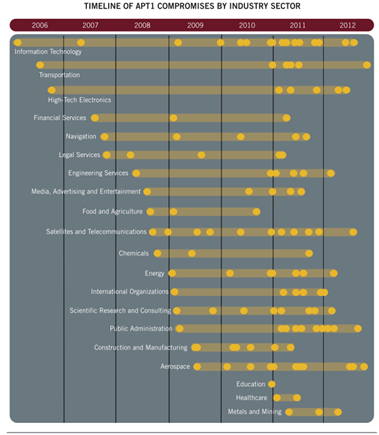
Some well known examples of Chinese cyber-espionage events are Titan Rain and the GhostNet network, which compromised computer systems in Tibet, Taiwan and several other countries. An article from the New York Times describes GhostNet as:
A broader operation that, in less than two years, has infiltrated at least 1,295 computers in 103 countries, including many belonging to embassies, foreign ministries and other government offices, as well as the Dalai Lama's Tibetan exile centers in India, Brussels, London and New York.
Titan Rain was the name given to another incursion, presumably initiated by the Chinese for purposes of cyber-espionage. This event is well known within the cyber-security community. In an article from Time Magazine, Nathan Thornberg describes the incident.
Hackers breaking into official U.S. networks are not just using Chinese systems as a launch pad, but are based in China, sources tell TIME. Their story: Sometime on November 1st, 2004, hackers sat down at computers in southern China and set off once again on their daily hunt for U.S. secrets. Since 2003 the group had been conducting wide-ranging assaults on U.S. government targets to steal sensitive information, part of a massive cyber-espionage ring that U.S. investigators have codenamed Titan Rain.
Initially, the attackers involved in Titan Rain used a scanning program to find vulnerabilities in US computers, specifically targeting military networks. Thornberg goes on to describe the impact of the attacks.
They hit hundreds of computers that night and morning alone, and a brief list of scanned systems gives an indication of the breadth of the attacks. At 10:23 p.m. pacific standard time (PST), they found vulnerabilities at the U.S. Army Information Systems Engineering Command at Fort Huachuca, Arizona.
At 1:19 am PST, they found the same hole in computers at the military's Defense Information Systems Agency in Arlington, Virginia. At 3:25 am, they hit the Naval Ocean Systems Center, a defense department installation in San Diego, California. At 4:46 am PST, they struck the United States Army Space and Strategic Defense installation in Huntsville, Alabama.
As with prior attacks, the targeted networks were unclassified systems; the military's classified networks are not connected directly to the Internet. But even unclassified systems store sensitive information and provide logistics support throughout the armed forces. Government analysts say the attacks are ongoing, and increasing in frequency. But whether the Titan Rain hackers are gathering industrial information or simply testing their ability to infiltrate a rival nation's military systems, the U.S. government is taking the threat very seriously.
Undoubtedly, the Chinese have already successfully acquired significant amounts of classified data from US networks. An example of this is the J-20 stealth fighter produced by the Chinese, which exhibits many features of American aircrafts.
One question that may go unanswered for a long time concerns the degree to which cyber-espionage has aided the development of the J-20. U.S. defense industry cyber-security experts have cited 2006–close to the date when the J-20 program would have started–as the point at which they became aware of what was later named the advanced persistent threat (APT), a campaign of cyber-intrusion aimed primarily at military and defense industries and characterized by sophisticated infiltration and exfiltration techniques.
As dependency on web-based services constantly increases, the influx of cyber-attacks originating from China are a huge concern for those seeking to deter and mitigate such illicit activity. The security firm Mandiant recently made headlines with perhaps the most inclusive investigation of China's cyber-espionage capabilities to date. Their sixty page report entitled "APT1 - Exposing One of China's Cyber Espionage Units" relates the specific details surrounding the clandestine cyber-espionage division of the People's Liberation Army (PLA), referred to internally as Unit 61398.
The number 61398 is the division's Military Unit Cover Designator (MUCD). These five digit identifiers are given to the various sub-divisions of the PLA. The following figure visually depicts the organizational hierarchy of the PLA within the Chinese Communist Party.
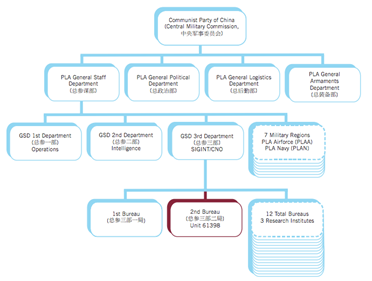
As detailed in the diagram above, Unit 61398 is embedded deeply within the PLA's signals intelligence division, which could be considered China's equivalent to the American NSA. The moniker APT1 is used interchangeably by Mandiant in reference to Unit 61398. The Mandiant Report states:
Evidence indicates that APT1 has been stealing hundreds of terabytes of data from at least 141 organizations across a diverse set of industries beginning as early as 2006. Remarkably, we have witnessed APT1 target dozens of organizations simultaneously. Once the group establishes access to a victim's network, they continue to access it periodically over several months or years to steal large volumes of valuable intellectual property, including technology blueprints, proprietary manufacturing processes, test results, business plans, pricing documents, partnership agreements, emails and contact lists from victim organizations' leadership.
The following figure represents the threat cycle of APT1, but could just as easily be applied to any advanced persistent threat.
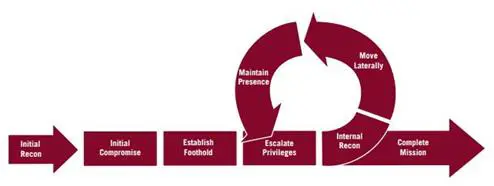
The key findings of Mandiant's report are listed as follows:
-
APT1 is believed to be the 2nd Bureau of the People's Liberation army General staff Department's 3rd Department which is most commonly knownas unit 61398
-
The nature of Unit 61398's work is considered by China to be a state secret; however, we believe it engages in harmful "Computer Network Operations."
-
Unit 61398 is partially situated on Datong Road in Gaoqiaozhen, which is located in the Pudong.
-
Unit 61398 is staffed by hundreds, and perhaps thousands of people based on the size of Unit 61398's physical infrastructure.
-
China Telecom provided special fiber optic communications infrastructure for the unit in the name of national defense.
-
Unit 61398 requires its personnel to be trained in computer security and computer network operations and also requires its personnel to be proficient in the English language.
-
Mandiant has traced APT1's activity to four large networks in Shanghai, two of which serve the Pudong New Area where Unit 61398 is based.
-
APT1 has systematically stolen hundreds of terabytes of data from at least 141 organizations, and has demonstrated the capability and intent to steal from dozens of organizations simultaneously.
-
Since 2006, Mandiant has observed APT1 compromise 141 companies spanning 20 major industries.
-
APT1 has a well-defined attack methodology, honed over years and designed to steal large volumes of valuable intellectual property.
-
Once APT1 has established access, they periodically revisit the victim's network over several months or years and steal broad categories of intellectual property, including technology blueprints, proprietary manufacturing processes, test results, business plans, pricing documents, partnership agreements, and emails and contact lists from victim organizations' leadership.
-
APT1 uses some tools and techniques that we have not yet observed being used by other groups including two utilities designed to steal email — GETMAIL and MAPIGET.
-
APT1 maintained access to victim networks for an average of 356 days. The longest time period APT1 maintained access to a victim's network was 1,764 days, or four years and ten months.
-
Among other large-scale thefts of intellectual property, Mandiant has observed APT1 stealing 6.5 terabytes of compressed data from a single organization over a ten-month time period.
-
In the first month of 2011, APT1 successfully compromised at least 17 new victims operating in 10 different industries.
-
Mandiant believes that the extensive activity they have directly observed represents only a small fraction of the cyber espionage that APT1 has conducted. Therefore, Mandiant is establishing the lower bounds of APT1 activities in this report. This is based on 91 of the 141 victim organizations.
-
Of the 141 APT1 victims, 87% of them are headquartered in countries where English is the native language.
-
The industries APT1 targets match industries that China has identified as strategic to their growth, including four of the seven strategic emerging industries that China identified in its 12th Five Year Plan.
-
APT1 controls thousands of systems in support of their computer intrusion activities.
-
In the last two years Mandiant has observed APT1 establishing a minimum of 937 Command and Control (C2) servers hosted on 849 distinct IP addresses in 13 countries. The majority of these 849 unique IP addresses were registered to organizations in China, followed by the U.S.
-
In the last three years Mandiant observed APT1 use fully qualified domain names (FQDNs) resolving to 988 unique IP addresses.
-
Over a two-year period (January 2011 to January 2013) Mandiant confirmed 1,905 instances of APT1 actors logging into their attack infrastructure from 832 different IP addresses with Remote Desktop, a tool that provides a remote user with an interactive graphical interface to a system.
-
In the last several years Mandiant confirmed 2,551 FQDNs attributed to APT1.
-
In over 97% of the 1,905 times Mandiant observed APT1 intruders connecting to their attack infrastructure, APT1 used IP addresses registered in Shanghai and systems set to use the simplified Chinese language.
-
In 1,849 of the 1,905 (97%) of the Remote Desktop sessions APT1 conducted under our observation, the APT1 operator's keyboard layout setting was "Chinese (Simplified) — US Keyboard." Microsoft's Remote Desktop client configures this setting automatically based on the selected language on the client system. Therefore, the APT1 attackers likely have their Microsoft operating system configured to display Simplified Chinese fonts.
-
817 of the 832 (98%) IP addresses logging into APT1 controlled systems using Remote Desktop resolved back to China.
-
Mandiant observed 767 separate instances in which APT1 intruders used the "HUC Packet Transmit Tool" or HTRAN to communicate between 614 distinct routable IP addresses and their victims' systems using their attack infrastructure. Of the 614 distinct IP addresses used for HTRAN communications:
-
614 of 614 (100%) were registered in China.
-
613 (99.8%) were registered to one of four Shanghai net blocks.
-
-
Mandiant conservatively estimates that APT1's current attack infrastructure includes over 1,000 servers.
-
Given the volume, duration and type of attack activity Mandiant has observed, APT1 operators would need to be directly supported by linguists, open source researchers, malware authors, industry experts who translate task requests from requestors to the operators, and people who then transmit stolen information to the requestors.
-
APT1 would also need a sizable IT staff dedicated to acquiring and maintaining computer equipment, people who handle finances, facility management, and logistics (e.g., shipping).
Mandiant went to great lengths to provide specific details of Unit 61398's operational structure. They even named names, so to speak, in order to support their claims. Three individual members of the cyber-espionage division were highlighted in the report:
-
The first persona, "UglyGorilla," has been active in computer network operations since October 2004. His activities include registering domains attributed to APT1 and authoring malware used in APT1 campaigns. "UglyGorilla" publicly expressed his interest in China's "cyber troops" in January 2004.
-
The second persona,"DOTA," has registered dozens of email accounts used to conduct social engineering and spear phishing attacks in support of APT1 campaigns. "DOTA" used a Shanghai phone number while registering these accounts.
-
The third persona, "SuperHard," is the creator or a significant contributor to the AURIGA and BANGAT malware families which we have observed APT1 and other APT groups use. "SuperHard" discloses his location to be the Pudong New Area of Shanghai.
Ultimately, the Mandiant report draws the following conclusion:
The sheer scale and duration of sustained attacks against such a wide set of industries from a singularly identified group based in China leaves little doubt about the organization behind APT1. We believe the totality of the evidence we provide in this document bolsters the claim that APT1 is Unit 61398. However, we admit there is one other unlikely possibility:
A secret, resourced organization full of mainland Chinese speakers with direct access to Shanghai-based telecommunications infrastructure is engaged in a multi-year, enterprise scale computer espionage campaign right outside of Unit 61398's gates, performing tasks similar to Unit 61398's known mission.
To support mitigation efforts Mandiant details a number of IT solutions in defense of APT1's operations. Specifically, Mandiant providesthe following:
-
Digital delivery of over 3,000 APT1 indicators, such as domain names, IP addresses, and MD5 hashes of malware.
-
Sample Indicators of Compromise (IOCs) and detailed descriptions of over 40 families of malware in APT1's arsenal of digital weapons.
-
Thirteen (13) X.509 encryption certificates used by APT1.
-
A compilation of videos showing actual attacker sessions and their intrusion activities.
As evidenced by Mandiant's efforts, cyber-attacks originating in China are an obvious cause for concern to the US government and private sector entities alike. It is widely accepted that, were an actual cyber-war ever to erupt between nation-state actors, the two most likely candidates would be China and the USA. In "Blown to Bits," Christopher Bronk describes this situation hypothetically, illustrating a potential scenario in the year 2020.
For the purposes of the scenario, I posit a conflict where China stands as the aggressor, although it is not hard to see a possible future in which China might see certain US moves as provocative and even threatening. Consider a possible future where the United States refuses to service its debt to the PRC based on human rights matters or as sour grapes over the Finlandization of Taiwan.
Ponder, too, a world of the next decade where the US–India relationship continues to deepen, and the two countries warming relations and pooled sea power in the Indian Ocean leave China concerned about its access to petroleum sources and other raw materials in the Persian Gulf and Africa. Also suspend a bit of disbelief and think about a reunited Korea without US troops and a Japan increasingly driven to counterbalance China's rise with substantially increased investment in its military.
Of course conflicts go from cool to hot at flash points, so for the purposes of this one, let us suppose that China, now firmly asserting itself over Taiwan as a quasi-autonomous region, faces the problems of city regions such as Shanghai, Guangzhou, and Hong Kong wishing for greater autonomy. The city-state of Singapore comes into focus as China's new other,a sovereign entity Beijing wishes to bring inside the fold as it has Hong Kong, Macau, and Taipei.
In a mostly digital rather than kinetic conflict, how might the PRC isolate the country sitting astride perhaps the globe's most important maritime choke point? So let us imagine a late summer of 2020 in which the People's Republic of China has chosen to employ military force, largely in the cyber domain, to collapse Singapore and exert its influence monolithically over the Straits of Malacca.
This is not the decision of a blindly angry dragon but rather the pragmatic move of a state needing to assert itself against a declining hegemon (the United States), a rising power (India), and an old foe (Japan) in adjusting the balance of power in East Asia.
Bronk suggests a situation in which China combines information warfare with kinetic attacks, using cyber-espionage for monitoring, and DDoS attacks to slow the pace of an active response from its adversaries. These types of combined attacks are far more realistic than a war fought solely in cyberspace.
The opening hours of China's virtual war with the United States and its allies over Singapore would confirm many of the worst suspicions of that crowd. Chinese forces were quite clearly working inside the decision loop of the allied forces. Preliminary moves by the PLA in the information space indicated that it could do much damage to enemy communication and computing resources, but a series of hints would reveal that China also likely had compromised, at least to a degree, the encryption mechanisms used to secure US and allied military and diplomatic communications.
At times, Beijing most probably held the capacity to have a fairly complete information picture even of very high-level, classified systems, although the reverse was also likely true. From the outset of the conflict, PLA cyber-warfare efforts were disruptive activities, highly visible to allied political and military leaders. They preceded formal hostilities, which would be marked by the sinking of a Singaporean guided missile frigate in the South China Sea on 5 September. The cyber attack had a rolling start, rather than being a bolt from the blue. When the PRC did finally choose to make use of kinetic options, the cyber-war was already well underway.
For the American and Japanese leadership, in particular, there was enormous trouble in employing even rudimentary information technologies effectively during the first days of the war. Personal computers, radio networks, satellite receivers, control systems, and battlefield communication hardware failed, often making it impossible for allied commanders to share intelligence and conduct joint planning. Only a few dedicated, high-end, satellite-based communication channels were able to connect American field commanders in Japan and Hawaii with the Pentagon.
But even these links were vulnerable, with the PLAAF's anti-satellite missile attacks on 6 September producing enormous damage to US telecom satellite coverage over the Pacific. Although Guam was the sole location of an electromagnetic strike by the Chinese, and an effective one at that, the PRC was reluctant to repeatedly use strategic missiles to short out the information grid of its enemies in the same way for fear of provoking a nuclear response from the Americans.
Rather than fry the allies' systems with electromagnetic pulse (EMP) weapons, the Chinese launched attacks via the global fiber network. Often the weapon of choice was sophisticated botnets, in which legions of zombie computers and mobile devices were employed to 'gang up' on unclassified government and private systems and bring them to a screeching halt in crushing denial-of-service attacks.
Ultimately, Bronk contends that a cyber-war over Singapore would be a wake-up call to the USA and its allies, but would not lead to nuclear conflict or a significant kinetic war between the two states. His argument seems geared towards China testing the waters, so to speak, in regard to a full-blown war, which would be heavily supplemented by cyber-espionage and the disruption of networks.
China's initial foray into cyber-war was not at all what many experts in the field had prognosticated for years. No electronic Pearl Harbor or Waterloo had occurred, and other than a few flickers here and there, the US power grid held up surprisingly well. It appears the Chinese Central Military Commission had made a calculated decision to leave much of the infrastructure up and running in the nations it had decided to wage war upon, although there is a strong counterargument that the PRC's cyber forces were largely checked in knocking out infrastructure by more than 20 years of concerted effort in building more secure systems.
Whatever the case, China's electronic forces were able to massively disrupt vital communications around the world during the opening days of the conflict. What is more, they were able to exert a persistent influence in this arena, continuing to bring down systems thought to have received a clean bill of health. The conflict of 2020 ended with puzzling results. After inflicting considerable damage upon one another, the protagonists simply ramped back from intensive cyber operations to station keeping. Singapore retained its independence, and a naval standoff between US and Chinese carrier forces never met with conclusive end. Submarines were sunk and cruise missiles dispatched, but no bombs fell on Honolulu or Hong Kong. General war was avoided, principally thanks to a high degree of risk aversion on both sides.
After approximately 55 days, the Sino-Asian conflict ended without treaty, agreement, or even much in the way of international communication.
Bronk's scenario seems entirely plausible, given the tendency of US policy-makers to ignore early warnings, and inadequately address issues of cyber-security. As Moore's law indicates, the nature of technological growth is an exponential curve. This premise supports the idea that in order to properly defend American infrastructure, intelligence, and intellectual property, investments in our own cyber-defenses must be continually increased. Additionally, research efforts akin to Mandiant's ground-breaking report must be further employed in an effort to secure America's presence in the digital domain.
Hands-on threat intel training
References
- Command Five Pty Ltd."Advanced Persistent Threats:A Decade in Review." June 2011.Available at http://www.commandfive.com/papers/C5_APT_ADecadeInReview.pdf
- Rogers, Mike."Statement to the U.S. House, Permanent Select Committee on Intelligence, Open Hearing: Cyber Threats and Ongoing Efforts to Protect the Nation."October 2011.Available at http://intelligence.house.gov/sites/intelligence.house.gov/files/documents/100411CyberHearingRogers.pdf, accessed February 6, 2013.
- Markoff, John."Vast Spy System Loots Computers in 103 Countries." 2009. Available at http://www.nytimes.com/2009/03/29/technology/29spy.html
- Thornburgh, Nathan."Inside the Chinese Hack Attack." August 2005. Available at http://www.time.com/time/nation/article/0,8599,1098371,00.html
- Ibid
- Knecht, Roger. "China Clones US Stealth Fighters." 2011. http://www.rogerknecht.com/2011/01/12/china-clones-us-stealth-fighters/
- Mandiant, "APT1: Exposing One of China's Cyber Espionage Units." 2013. Available at http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf









