From Turbine to Quantum: Implants in the Arsenal of the NSA
Introduction
The revelations of Edward Snowden totally changed our perception of NSA cyber capabilities. Day by day, the IT security community is reading about secret surveillance programs, exploits, and automated hacking platforms to compromise any kind of technology, infiltrating networks all over the world.
The last collection of leaked documents proved that the National Security Agency has also dealt numerous attacks against the cybercrime ecosystem to pursue its goals.
Hands-on threat intel training
The NSA has been hijacking the botnets managed by cybercrime to conduct secret cyber operations. The news was disclosed first by The Intercept website, which stated that since July 2010 the National Security Agency had built and used a hacking architecture named TURBINE. The platform was designed with the specific goal to conduct automated and sophisticated computer-hacking operations on hundreds of thousands of infected computers used by cyber criminal gangs.
Ryan Gallagher and Glenn Greenwald, the authors of the post "How the NSA Plans to Infect 'Millions' of Computers with Malware" hypothesized that the NSA hacking program TURBINE has infected between 85,000 and 100,000 computers.
Turbine is not the only hacking platform designed by US Intelligence. In October 2013, Snowden disclosed a series of slides on the FOXACID architecture, a collection of servers used to serve malicious exploits (e.g. United Rake, Peddle Cheap, Packet Wrench, and Beach Head).
The NSA, thanks to the collaboration of US telecoms operators, deployed a battery of servers, codenamed Quantum, on the Internet Backbone to be able to impersonate practically every website and inoculate malicious code on victim's systems. The US architecture may operate from Fort Meade HQ, Maryland, and from eavesdropping stations located in Japan and UK, also thanks the support of the British GCHQ.
"To trick targets into visiting a FoxAcid server, the NSA relies on its secret partnerships with US telecoms companies. As part of the Turmoil system, the NSA places secret servers, codenamed Quantum, at key places on the internet backbone. This placement ensures that they can react faster than other websites can. By exploiting that speed difference, these servers can impersonate a visited website to the target before the legitimate website can respond, thereby tricking the target's browser to visit a Foxacid server," reported the post on The Guardian.
FOXACID and TURBINE platforms provide the NSA operator a multiple choice menu for attack options, from which attackers could choose the proper offensive mode. Both architectures are under the control of the Tailored Access Operations (TAO) operators, a secret hacking unit in the NSA agency.
TAO unit's mission is to "aggressively scale" cyber espionage campaigns, and more in general hacking operations, due to the large number of computers infected worldwide the NSA has spent a great effort in the design of automated systems to manage a massive network of implants. Documents leaked by Snowden shows that the NSA describes its techniques as "a more aggressive approach to SIGINT".
"One of the greatest challenges for active SIGINT/attack is scale," explains the top-secret presentation from 2009. "Human 'drivers' limit ability for large-scale exploitation (humans tend to operate within their own environment, not taking into account the bigger picture)." The agency's solution was TURBINE. Developed as part of TAO unit, it is described in the leaked documents as an "intelligent command and control capability" that enables "industrial-scale exploitation."
TURBINE, exactly as FOXACID, allows NSA operators to serve malicious code on a large scale, and to do its job the NSA operators targeted the compromised computers belonging to the numerous botnets available in cyberspace.
"If the target is a high-value one, FoxAcid might run a rare zero-day exploit that it developed or purchased … If the target is technically sophisticated, FoxAcid might decide that there's too much chance for discovery, and keeping the zero-day exploit a secret is more important. If the target is a low-value one, FoxAcid might run an exploit that's less valuable. If the target is low-value and technically sophisticated, FoxAcid might even run an already-known vulnerability," Bruce Schneier wrote in his blog post.
[TURBINE] is designed to "allow the current implant network to scale to large size (millions of implants) by creating a system that does automated control implants by groups instead of individually."
Why hit a botnet?
Large botnets can be composed of millions of infected computers, and security experts believe that the NSA has planned to abuse them to conduct covert operations. Let's think, for example, that a botnet could be exploited to hide the real source of a cyber attack, obscuring the attribution of responsibility for the offensive. Botnets represent the optimal choice for NSA cyber units, as they are an army of infected machines that could be coordinated to conduct cyber attacks against strategic targets. Botnets are ordinarily used by cyber criminals to spread malicious code, run DDoS attacks, mine Bitcoin, and steal sensitive data.
The document on the TURBINE architecture also confirmed the existence of a specific program named QUANTUMBOT. Operative since 2007, it is a dedicated architecture to take control over the C&C servers of existing botnets. In particular, in one of the leaked slides it is reported that TURBINE has compromised "over 140,000 bots co-opted".
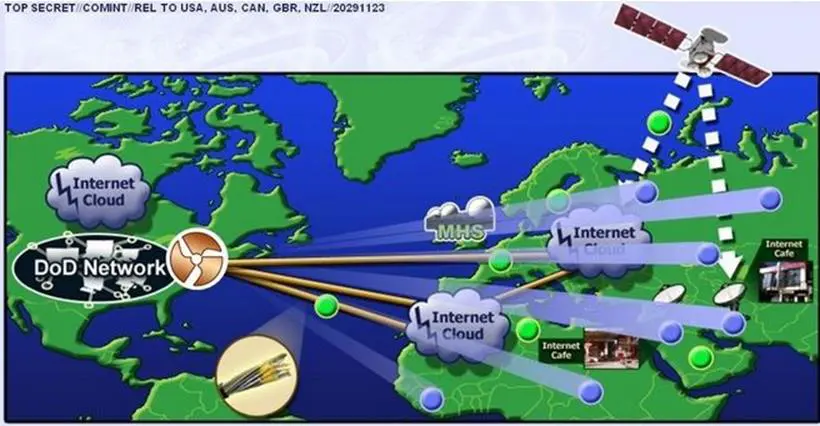
Figure - TURBINE NSA Slide

Figure - Turbine platform description from NSA document
"TURBINE was designed to make deploying malware much easier for the NSA's hackers by reducing their role in overseeing its functions. The system would "relieve the user from needing to know/care about the details," the NSA's Technology Directorate notes in one secret document from 2009. "For example, a user should be able to ask for 'all details about application X' and not need to know how and where the application keeps files, registry entries, user application data, etc.
"In practice, this meant that TURBINE would automate crucial processes that previously had to be performed manually – including the configuration of the implants as well as surveillance collection or "tasking" of data from infected systems. But automating these processes was about much more than a simple technicality. The move represented a major tactical shift within the NSA that was expected to have a profound impact – allowing the agency to push forward into a new frontier of surveillance operations," reports The Intercept.
What is the intent of the NSA? Cybercrime prevention, infiltration of the underground ecosystem ... or worse, the agency planned to serve malware for surveillance purposes or to conduct attacks against foreign targets in undercover. Personally, I incline to the latter hypothesis.
Quantum Suite
Last week, Edward Snowden released a new collection of documents on a powerful suite of exploits to target users all over the worlds. Its name is Quantum Suite. The slides were published online on The Intercept website, and according to journalists the platform was used for large-scale surveillance and not only against terrorists and foreign hackers. The attacks against the company Belgacom were probably one of numerous operations conducted by the NSA and its allies like the British CGHQ.
QUANTUM Suite is a collection of tools and exploits, including both DNS injection, man-in-the-middle attack through digital certificate manipulation, and HTTP injection. The document also refers to the capability of the agency to inject arbitrary code into MySQL connections, allowing the NSA to manipulate online contents of a third-party's database.
The NSA has used its hacking architecture to arrange malware-based spam campaigns with the intent to spread spyware, and also to launch cyberattacks with the purpose of disrupting file downloads or denying access to websites. QUANTUMMUSH was used to conduct targeted spam exploitation, meanwhile QUANTUMCOPPER is the tool dedicated to the corruption of file downloads.
Another curious detail reported in the documents leaked by Snowden was related to the capability of NSA cyber operators to hack both IRC and HTTP-based botnets. The component QUANTUMBOT was in fact used to hijack IRC botnets, and QUANTUMBISCUIT was used for the redirection based on keywork, mainly based on the analysis of cookie values. The slides also refers to the tolls dubbed QUANTUMBOT2, which is a combination of QUANTUMBISCUIT and QUANTUMBOT for the control of web-based managed botnets.
One of the tools that has most captured the media's attention is the QUANTUMHAND exploit family that was used by the National Security Agency to implant malware in Facebook users' machines. The tactic is simple and efficient: the NSA secretly pretended to be a Facebook server to covertly serve malicious code for surveillance purposes.
According to the news published by the journalists Gallagher and Greenwald, in different cases the NSA "masqueraded [itself] as a fake Facebook server, using the social media site as a launching pad to infect a target's computer and exfiltrate files from a hard drive."
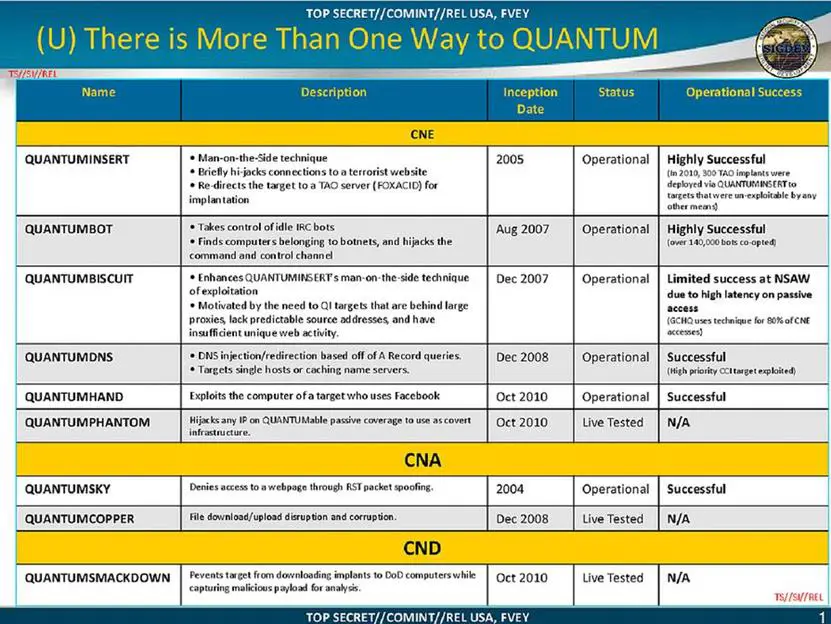
Figure - NSA QUANTUMHAND
The documents leaked by the whistleblower Edward Snowden demonstrate that the NSA has the technology to conduct MITM attacks impersonating Facebook servers to deploy its surveillance "implants" on targets' computers.

Figure - QUANTUMTHEORY on Facebook Attacks
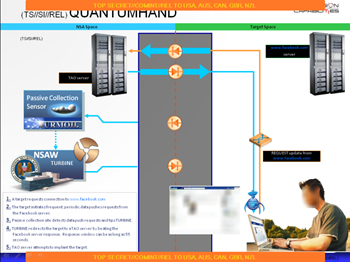
Figure - NSA QUANTUMHAND
The news aroused the indignation of Facebook founder Mark Zuckerberg, who is infuriated and expressed disappointment in a phone call to President Barack Obama:
"I've been so confused and frustrated by the repeated reports of the behavior of the US government ... When our engineers work tirelessly to improve security, we imagine we're protecting you against criminals, not our own government," Zuckerberg wrote in a blog post last week.
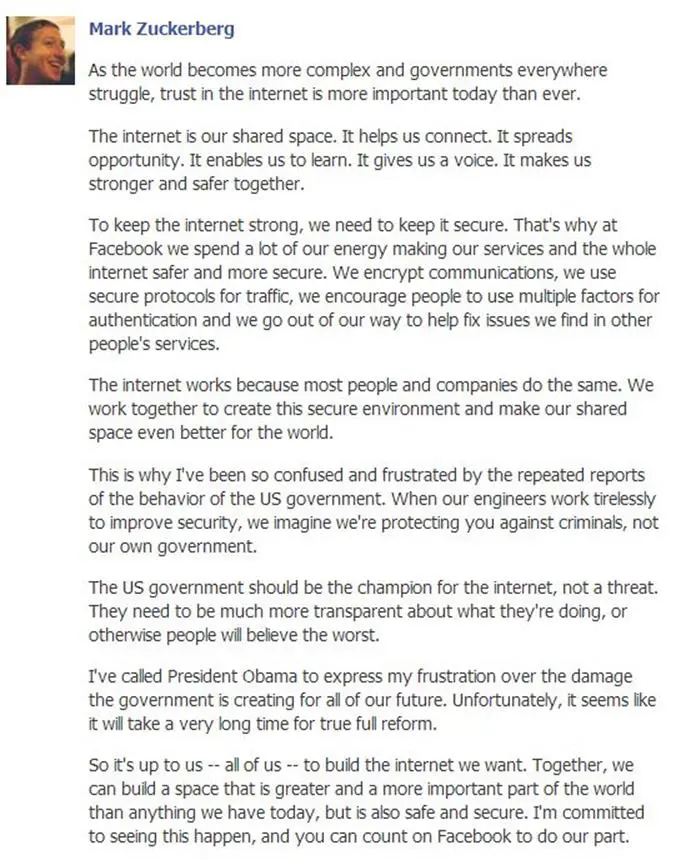
Figure - Zuckerberg post on NSA QUANTUMHAND
The documents, once again, claim that the NSA spies indiscriminately on every Netizen, but the agency refused the accusation and released a public statement attacking the "inaccurate" media reports. It has denied that it was "impersonating U.S. social media or other websites" and it added that it had not "infected millions of computers around the world with malware."
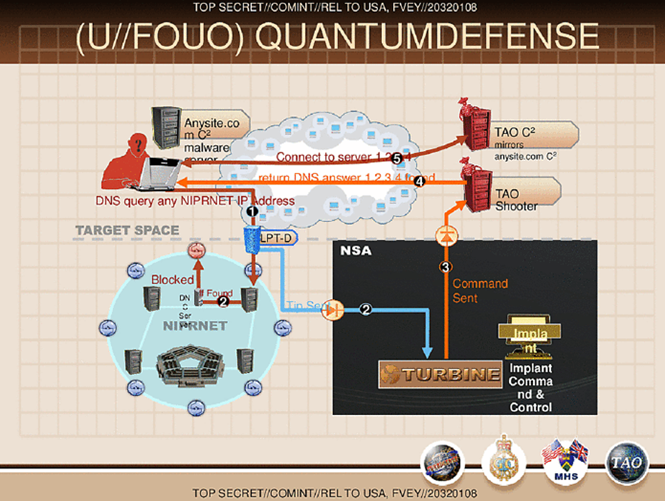
Figure - NSA QUANTUMDEFENSE Architecture
The above slide on QUANTUMDEFENSE shows the capability of the NSA to manipulate DNS requests for NIPRnet IP addresses. The experts of the agency are able to inject bogus DNS replies redirecting the victims to a website controlled by the NSA.
The NIPRNET (Non-classified Internet Protocol Router Network) is the Defense Department's portion of the Internet reachable of the public. The DoD controls the DNS authority record that the attacker is looking up, and could directly send it off. Let's close this overview on the QUANTUM theory analyzing the QUANTUMSMACKDOWN, a tool designed by the Intelligence to block attacks against DoD assets with a packet injection mechanism.
Once identified, the malicious traffic directed against the US infrastructure QUANTUMSMACKDOWN could be immediately triggered to protect the networks.
The NSA declined to answer questions about the effective deployment of implants, pointing to a new presidential policy directive announced by President Obama. "As the president made clear on 17 January," the agency said in a statement, "signals intelligence shall be collected exclusively where there is a foreign intelligence or counterintelligence purpose to support national and departmental missions, and not for any other purposes."
NSA Arsenal - the Implant Collection
The NSA has probably the largest arsenal to compromise any kind of technology, even if targets try to protect them through the adoption of encryption. The NSA has a wide range of implants that can be used to "circumvent privacy-enhancing encryption tools that are used to browse the Internet anonymously or scramble the contents of emails as they are being sent across networks."
Unfortunately, there is no information on the real use of these implants. It is not clear how many computers have been infected with these tools. In the following table, the most popular implants used by NSA to compromise victims' machines are listed.
Infiltration and control of cellphone networks under control
The NSA has numerous arrows in its arsenal. Malicious code distributed with automated hacking platforms is not only for surveillance purposes, the agency also designed specific implants for sabotage. It has been documented that NSA designed implants to compromise routers used by foreign ISP in foreign countries. By infecting routers all around the world, the NSA monitored Internet traffic in stealth mode, tracking users' accesses to the Internet and their browsing sessions and intercepting network communications.
The most popular implants used by the NSA to compromise network routers and to spy on VOIP conversations are respectively HAMMERCHANT and HAMMERSTEIN. The HAMMERSTEIN exploit has been also used to sniff data and inject malicious code over Virtual Private Network. As shown in the following slides extracted by NSA leaked documents, the implant HAMMERCHANT was used to monitor VOIP conversations, including Skype, and it was also able to catch the caller's username.
In case the VOIP conversations are sent using the unencrypted "Real-time Transport Protocol", the implant is able to capture the packet to reassemble and record the audio data.
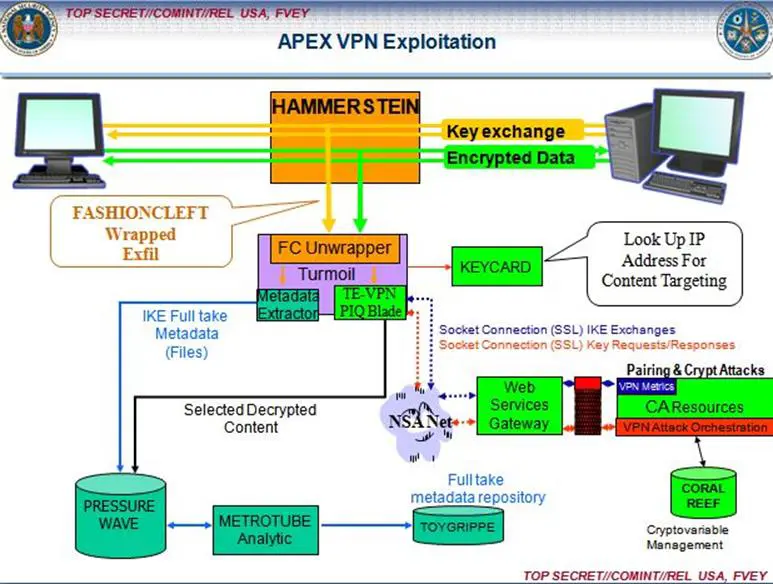
Figure – NSA HAMMERSTEIN implant
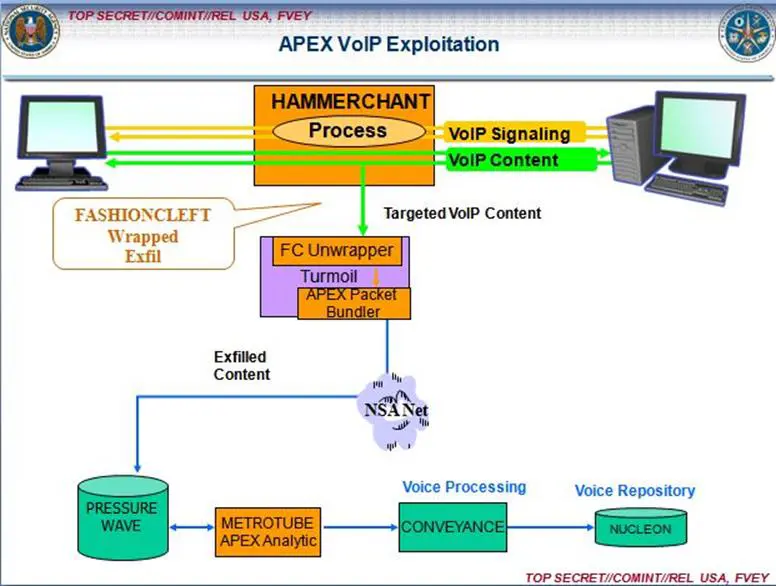
Figure - NSA HAMMERCHANT implant
The information on the surveillance capabilities of the National Security Agency is updated on a daily basis. While I was writing, another shocking piece of news was revealed by a new collection of NSA leaked documents: the agency has the technology to record all the phone calls of an entire country and replay them later.
A senior manager for the program described the technology used in the interception as a "time machine" that is able to analyze also phone calls made in the past. The NSA can collect every phone calls of a target country and use the tools codenamed as MYSTIC and RETRO to search and analyze each conversation. The document revealed that the tools can "retrieve audio of interest that was not tasked at the time of the original call."

Figure - MYSTIC system slide
The NSA agency is able to tap into the entire network from a country. MYSTIC and RETRO tools give them the possibility to analyze phone calls in each time window.
"The National Security Agency has built a surveillance system capable of recording '100 percent' of a foreign country's telephone calls, enabling the agency to rewind and review conversations as long as a month after they take place, according to people with direct knowledge of the effort and documents supplied by former contractor Edward Snowden," reports the article published in the Washington Post.
The voice interception program MYSTIC was started in 2009, meanwhile its RETRO tool reached full capacity against the first target nation in 2011.
"Ubiquitous voice surveillance, even overseas, pulls in a great deal of content from Americans who telephone, visit, and work in the target country … Present and former U.S. officials … acknowledged that large numbers of conversations involving Americans would be gathered from the country where RETRO operates," the Washington Post reports.
Sabotage and mass exploitation
For now we have discussed the capabilities of the NSA to spy on victims through implants, but the National Security Agency also designed a series of tools to conduct mass exploitation to inoculate the malicious code on the targeted systems. The NSA also used the implants to interfere with target operations, for example, preventing that victim's systems access to a specific website. QUANTUMSKY is a malware developed by NSA in 2004 to block the access to the Internet, other malware dubbed QUANTUMCOPPER which was spread in 2008 is able to disrupt target's file downloads. The US intelligence exploited a security flaw in the principal application (e.g. Java Platform, IE, Adobe products) to serve malicious payload onto targeted machines.
A classified document dated 2012 describes the necessity of adopting new exploitation methods, as phishing and in-line XSS were in fact becoming less efficient to circumvent the targets, so the NSA introduced the Quantum platform that mainly adopted Man-in-the-Middle and Man-on-the-Side techniques to interact with the victims' activity.
The man-in-the-middle capability used by the NSA was codenamed SECONDDATE. It is described as the practice "influence real-time communications between client and server" and to "quietly redirect web-browsers" to NSA hacking platform FOXACID.
But SECONDDATE was also able to serve as an attack platform able to distribute malware against computers. According to the 2012 presentation, SECONDDATE has "mass exploitation potential for clients passing through network choke points."

Figure - SECONDDATE exploitation technique
Conclusions
The public image of the NSA is seriously compromised. It's hard to regain the citizens' trust if day after day a new collection of documents reveals the aggressive approach of US Intelligence. Some experts believe that the US must admit the covert operations, but others reply that it would be a suicide for the agency to reveal targets and techniques adopted to hit them.
Chief research officer at the Finnish security firm F-Secure, Mikko Hypponen, has called the revelations "disturbing."
"When they deploy malware on systems," Hypponen says, "they potentially create new vulnerabilities in these systems, making them more vulnerable for attacks by third parties."
The NSA's surveillance programs could inadvertently be undermining the security of the Internet. Let's consider that the implants deployed all over the global network would be "out of control," said Hypponen.
Hypponen's claims are our main concern.
References
https://firstlook.org/theintercept/article/2014/03/12/nsa-plans-infect-millions-computers-malware/
http://securityaffairs.co/wordpress/23034/cyber-crime/turbine-nsa-plundered-botnets-cybercrime.html
http://securityaffairs.co/wordpress/18601/hacking/nsa-foxacid-servers.html
https://firstlook.org/theintercept/2014/03/15/nsas-disingenuous-malware-non-denial-denial/
http://news.cnet.com/8301-1009_3-57620226-83/nsa-system-designed-to-attack-millions-of-computers-report/
https://firstlook.org/theintercept/document/2014/03/12/nsa-gchqs-quantumtheory-hacking-tactics/
http://www.wired.com/opinion/2014/03/quantum/
http://www.f-secure.com/weblog/archives/00002684.html
http://securityaffairs.co/wordpress/23129/hacking/quantumhand-nsa-impersonates-facebook-inject-malware.html
http://www.washingtonpost.com/world/national-security/nsa-surveillance-program-reaches-into-the-past-to-retrieve-replay-phone-calls/2014/03/18/226d2646-ade9-11e3-a49e-76adc9210f19_story.html










