The Threatening Evolution of Exploit Kits
Exploit Kits, even more sophisticated and profitable
Exploit kits are rapidly evolving, threat actors improve them on a daily basis by adding the code for the exploitation of the most recent vulnerabilities. In October 2015, expert
s from the Cisco Talos Group published the results of in-depth research on the threat actors behind the Angler Exploit Kit revealing the profitable business behind such kind of threat.
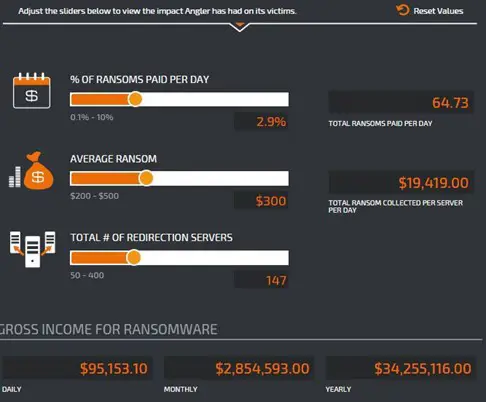
The researchers from Talos gained an inside view of one of the health monitoring servers utilized by an Angler Exploit Kit instance active throughout the month of July 2015. The server analyzed by the experts was monitoring 147 proxy servers, allegedly generating approximately $3 million in revenue over the span of that single month of July.
Additionally, researchers from the Talos team have determined that this single Angler instance was responsible for half of all Angler activity that they observed and is likely generating more than $30 million annually. This revenue was mainly generated through the distribution of Ransomware (CryptoWall 3.0 and TeslaCrypt 2.0), more than 60% of compromised devices were infected by this family of threats.
Additionally, Angler was also found to be serving the Bedep Trojan Downloader, Ad-Fraud (or Click-Fraud) Trojans, as well as various other keyloggers and varying types of Trojans.
A breakdown of the exploits delivered by the Angler instance examined by Talos on July 2015 allowed the experts to discover that 74% exploited, Adobe Flash flaws, 24% the CVE-2014-6332 vulnerability in the Internet Explorer and only 2% leveraged on the Microsoft Silverlight flaw.
Below the statistics emerged from the Talos's study that confirm the strategic role of the exploit kits in the criminal ecosystem:
- 90,000 Targeted Victims Per Day
- 9,000 Exploits Served Per Day
- 3,600 (40%) Systems Successfully Compromised
- 2,232 (62%) Angler Infections Delivered Ransomware
- 2.9% (Based on USCert via Symantec) Ransoms Paid Daily
- $300 Average Ransom Demanded
- 147 Total Redirection Servers
- 64.73 Ransoms Paid Daily
- $19,419.00 Daily Ransom Revenue Per Server
- $95,153.10 Gross Daily Ransom Revenue
- $2,854,593.00 Gross Monthly Ransom Revenue
- $34,225,116.00 Gross Annual Ransom Revenue
Figure 1 - CISCO TALOS Study on Angler exploit kit revenues
Although Angler has dominated the exploit kit market for a long period, other kits obtained a similar notoriety in the criminal underground. The Nuclear exploit kit, arguably, is the second most prevalent exploit kit found in the wild. In October 2015, it was observed utilizing payload delivery mechanisms that are much more efficient and more sophisticated in nature than ever seen before.
One of the most important improvements made by the author of the Nuclear EK is that the payloads delivered by the exploit kit are dynamic in nature. While payloads were often rotated during normal Nuclear EK operation, it has been discovered that the payloads delivered by a number of analyzed hosts serving the Nuclear EK have been exceptionally volatile in nature.
Signature-based solutions detect malware based on hashes; known files, whether legitimate or nefarious in nature can be identified by their hash value (or signature). This value remains static for each file whose hash is computed utilizing the same algorithm that contains the same content.
However, signature-based solutions could be easily bypassed by modifying the payload and adding, removing, or flipping a few bytes. These operations will completely change the hash of any file allowing to evade signature-based solutions.
Experts observed that each payload file appears to have the same size, the actual binary make-up of the payload files is created on-the-fly.
Each unique potential victim is not only just delivered a payload with an entirely different hash, but also delivers a payload whose internal make-up (i.e. variable and function names leveraged by the payload) is entirely unique on a per-host basis (or rather, per-IP address basis).
The most recent versions of the Nuclear EK utilize effective techniques to evade detection, and even when it fails to exploit a target system, its anti-analysis techniques served to prevent malware analysts from re-creating and following/analyzing the infection chain employed by Nuclear.
Newer, or rather, more recent, instances of the Nuclear EK implement IP address logging capabilities; Nuclear will never deliver the same payload to an individual IP address. It has been configured to deliver malicious payloads on a per-target basis, effectively evading signature-based Anti-Virus (AV) solutions, as well as most behavioral/heuristic AV solutions.
Angler EK delivered exploits capable of evading the Microsoft EMET security Tool.
Exploit kits are becoming even more sophisticated; new evasion techniques allow them to bypass security software and avoid detection. This is the case, for example, of the Angler EK, security experts from FireEye have recently observed attacks leveraging on the popular exploit kit delivering malicious code capable of evading the Microsoft EMET Security Tool.
The Microsoft's Enhanced Mitigation Experience Toolkit (EMET) is a free security tool designed by Microsoft to implement a supplemental security layer of defense against the exploitation of vulnerabilities affecting applications running on Windows Systems.
The ability to bypass the EMET is not new, security researchers in the last months have devised methods do the same, and now, according to FireEye a current version of the infamous Angler Exploit Kit can deliver Flash Player and Microsoft Silverlight exploits evading the security tool.
The exploits observed by FireEye leverage the routines built into the Flash Player plugin componentFlash.ocx and the Silverlight component Coreclr.dll to invoke the VirtualProtect and VirtualAlloc memory management functions. In this way, the exploits can bypass both data execution prevention (DEP) mitigation the return address validation-based heuristics before executing shellcode.
"The ability of Angler EK to evade EMET mitigations and successfully exploit Flash and Silverlight is fairly sophisticated in our opinion. These exploits do not utilize the usual return oriented programming to evade DEP. Data Execution Prevention (DEP) is a mitigation developed to prevent the execution of code in certain parts of memory." states the analysis published by FireEye. "The Angler EK uses exploits that do not utilize common return oriented programming (ROP) techniques to evade DEP. Instead, they use Flash.ocx and Coreclr.dll's inbuilt routines to call VirtualProtect and VirtualAlloc, respectively, with PAGE_EXECUTE_READWRITE, thus evading DEP and evading return address validation-based heuristics."
"The Flash exploit uses Flash.ocx's routines to call VirtualProtect for DEP evasion before shellcode is executed"
"Since return address validation heuristics are evaded by utilizing these inbuilt functions from within ActionScript and Silverlight Engine, ROP checks by EMET's DEP capability are not effective," FireEye researchers explained.
The researchers discovered that the Flash and Silverlight exploits used by a current version of the Angler Exploit Kit can also bypass the Address Table Filtering (EAF) and EAF+ mitigations implemented by the EMET to avoid attackers to understand in which portion of memory the code are loaded.
In the attacks observed by FireEye, crooks used this variant of the Angler Exploit Kit to bypass the EMET and deliver the TeslaCrypt ransomware. The attack works against Windows 7 running EMET 5.5; that is the latest version of the Microsoft security tool.
Figure 2 - Angler EK bypass Microsoft EMET (FireEye)
FireEye confirmed that exploit kits are becoming even more sophisticated over the years, they are frequently improved to include code for the exploitation of zero-day flaws and to implement effective evasion techniques.
The experts suggest the adoption of a robust vulnerability management program to prevent attacks leveraging on such kind of threat. Keep your software up to date and adopt a proper security posture in your organization.
"Although there are no quick solutions for the DEP, EAF, and EAF+ evasion techniques, organizations can mitigate this threat through a robust vulnerability management program for end user systems, which includes the installation of security updates for third party software." closes FireEye.
Not only Angler EK
Earlier this year, security experts at Heimdal Security observed a spike in cyber attacks leveraging the popular Neutrino and RIG exploit kit. Threat actors in the wild used both exploit kits to target users that haven't patched their Adobe Flash software.
"It seems that cyber criminals are well rested and have also gotten back to the "office," because out team has spotted a substantial increase in exploit kit activity for Neutrino, RIG, and Angler." states a blog post published by the Heimdal Security firm.
On August 2015, according to the Zscaler security firm, cybercriminals hacked more than 2,600 WordPress websites and deployed malicious iframes on 4,200 distinct pages. The criminals exploited vulnerable versions of WordPress 4.2, and prior, to plant the iframes which were used to redirect users to domains hosting the Neutrino exploit kit.
The Neutrino landing page was designed to exploit Flash Player vulnerabilities to serve the last variant of the popular ransomware CryptoWall 3.0. Also, in this case, the variant of the Neutrino exploit kit leveraged in the attack includes the Flash Player exploits leaked in the Hacking Team breach.
The attackers exploited the remote code execution flaw in Adobe Flash to serve ransomware.
According to the researchers at Trustwave, in the same period, the researchers at Trustwave revealed that the developer behind the RIG exploit kit released a 3.0 version of the RIG exploit kit which included some significant improvements to avoid the analysis of the source code.
Neutrino EK was used to deliver several families of malware, including Cryptolocker 2 and some variants of the Kovter malware family exploiting the Flash (CVE-2015-7645).
"This new campaign also comes with added surreptitious tricks: Google Blackhat SEO poisoning and an immediate focus on using Flash Player vulnerabilities as a distribution vector." continues the Heimdal Security firm.
The campaign relying on the RIG exploit kit spreads through drive-by attacks by using Google Blackhat SEO poisoning. The RIG 3.0 is improved by including the code for the exploitation of known vulnerabilities in popular third-party applications like Adobe Flash, Adobe Reader, Adobe Acrobat and Silverlight to infect outdated Windows machines.
"From our data, derived from having access to RIG exploit kit version 3 panels, we have observed that this payload achieves an infection success rate of 56% on Windows 7 PCs with Internet Explorer 9. The security issues lie particularly with Adobe Flash Player and, respectively, with vulnerabilities to RIG exploit kit version 3 panels, we have observed that this payload achieves an infection success rate of 56% on Windows 7 PCs with Internet Explorer 9. The security issues lie particularly with Adobe Flash Player and, respectively, with vulnerabilities CVE-2015-5119(CVSS Score: 10) and CVE-2015-5122 (CVSS Score: 10), which are wreaking havoc among Windows-based PCs." continues Heimdal Security.
As anticipated the popularity of the Neutrino EK is increasing in the criminal underground, threat actors are using it to deliver ransomware.
Crooks behind the CryptXXX ransomware have recently launched a new campaign leveraging on the Neutrino Exploit Kit instead the Angler Exploit Kit. It is considered by security experts a significant change in the attack chain that was discovered by the SANS Internet Storm Center.
The experts identified the ransomware-based attacks as the pseudo-Darkleech campaign.
"By Monday 2016-06-06, the pseudo-Darkleech campaign began using Neutrino exploit kit (EK) to send CryptXXX ransomware. Until then, I'd only seen Angler EK distribute CryptXXX. However, this is not the first time we've seen campaigns associated with ransomware switch between Angler EK and Neutrino EK." wrote Brad Duncan. "It was documented as early as August 2015. This can be confusing, especially if you're expecting Angler EK. Campaigns can (and occasionally do) switch EKs."
The changes in the attack method were observed concurrently to a resurgence of the CryptXXX ransomware that observed in the wild with improved features, including a new encryption algorithm and a new StillerX credential-stealing module.
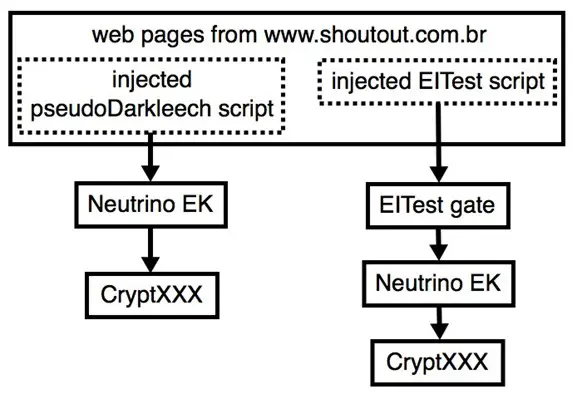
Figure 3 - Neutrino EK Campaigns (SANS)
The attacks leveraging the Neutrino EK observed by the experts target the Java runtime environment, recently the exploit kit was integrated with the code for the exploitation of the CVE-2016-4117 vulnerability in the Adobe Flash software.
"Last month, Neutrino EK was documented using Flash exploits based on CVE-2016-4117 effective against Adobe Flash Player up to version 21.0.0.213," said Duncan.
The attacks have become more and more aggressive, in some cases compromised websites were hosting servers for various campaigns, including the pseudo-Darkleech campaign and the EITest campaign operated to serve the CryptXXX ransomware.
"In both cases, Neutrino EK delivered CryptXXX ransomware as a DLL file. As usual with CryptXXX infections, we sawC:WindowsSystem32rundll32.exe copied to the same folder as the CryptXXX DLL file. In this case, it was re-namedexplorer.exe." reported the analysis published by the SANS Center.
The two CryptXXX DLL files from these infections are:
- 2016-06-07-EITest-Neutrino-EK-payload-CryptXXX.dll (419 kB) – VirusTotal link
- SHA256: d322e664f5c95afbbc1bff3f879228b40b8edd8e908b95a49f2eb87b9038c70b
- 2016-06-07-pseudoDarkleech-Neutrino-EK-payload-CryptXXX.dll (440 kB) – VirusTotal link
- SHA256: 75a927e636c788b7e54893161a643c258fecbbf47d6e7308d3439091aa3ce534
"I was able to generate traffic for each campaign, but I had to use two separate visits, because the pseudo-Darkleech script prevented the EITest script from generating any EK traffic," Duncan added.
Exploit kit landscape is rapidly changing
The exploit kit landscape is in continuous evolution, although it was monopolized by the Angler and Nuclear exploit kits for several years, criminal organizations also look with great interest to less popular EKs.
Recently malware researchers observed a spike in the malicious traffic related to Neutrino and RIG EKs Meanwhile the overall traffic related to other EKs show a drastic fall, around 96% since early April.
What is happening?
The Necurs botnet, one of the world's largest malicious architecture used to spread the dreaded threats like Dridex and Locky appears to have vanished since June 1.
The Angler and Nuclear exploit kits seem to be disappearing too, likely due to the operations conducted by the law enforcement in the malware industry.
The Nuclear EK, the oldest EK in the wild, was observed for the last time at the end of April, and it is still unclear the reason behind the suspension of its activities.
In April 2015, the experts from Check Point published an interesting report on the economic aspects of the Nuclear EK and the infrastructure used by its operators.
According to security experts at Check Point, the creators of the Nuclear EK, a group of Russian developers led by an individual in Krasnodar, are gaining nearly 100K USD each month.
What about the Nuclear EK?
According to the experts from Symantec, there is no evidence of the Nuclear's activity since the first week of May.
"Angler's disappearance has also prompted a falloff in activity in CryptXXX ransomware (Trojan.Cryptolocker.AN). Angler was one of the main delivery channels for CryptXXX." reported the analysis published by Symantec. "Angler is not the only exploit kit to recently depart the scene. The well-known Nuclear exploit kit became inactive from the beginning of May. Since this occurred one month earlier, it is unclear if there is any connection with more recent developments."
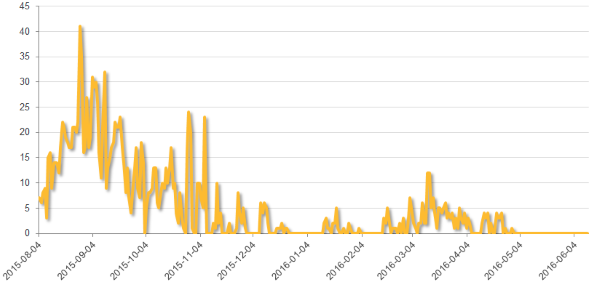
Figure 4 Exploit Kit Activity (Symantec Report)
What's interesting to note, however, is that a graph published by Proofpoint late last week suggests that Nuclear was still active during the second half of May.
The Angler's disappearance might be caused by law enforcement activities, including the recent 50 arrests in Russia that were linked to the operations of the Lurk malware.
We read about Angler since June; most recent news is related to the inclusion of the recent Flash zero-days and improvement of evasion techniques.
According to the experts from Proofpoint, the disappearance of Angler and Nuclear EKs pushed the adoption of the Neutrino and RIG exploit kits.
"Interestingly, the shift to Neutrino was well underway by the time it was first reported, with Angler traffic dropping off dramatically as early as mid-May, and Nuclear EK affected as well. Angler and Nuclear EK activity has dropped to almost nothing as threat actors moved to instances of the Neutrino exploit kit. Shifting from one exploit kit to another is nothing new, and threat actors may even use more than one regularly. However, with the exception of a brief break in January [8], Angler has dominated the EK market for some time, as we explained in the Threat Summary for January-March," states the report published by ProofPoint.
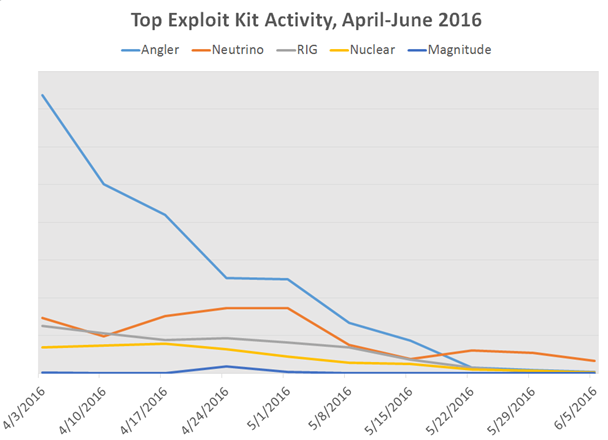
Figure 5 - Top Exploit Kit Activity, April - June 2016 (Proofpoint)
"By our estimates, Neutrino dropping CryptXXX account for as much as 75% of observed exploit kit traffic, and another 10% combined from Neutrino and Magnitude dropping Cerber ransomware. Most of the remaining 15% of EK traffic is RIG dropping a variety of payloads (banking Trojan, info stealers, loaders) on lower-value malvertising traffic, with various smaller EKs such as Sundown, Kaixin, Hunter and others making up the last 1% of total observed EK traffic," continues Proofpoint.
Experts from Kaspersky Lab confirmed the above trends are highlighting that criminal groups switched to Neutrino and RIG exploit kits.
What will happen in the future?
It is impossible to predict the evolution of the Exploit Kit Landscape, multiple factors influence the trends, but the unique certainly is that crooks will continue undeterred their illegal activities.
At the time I was writing a popular anime site in Mexico and South America, Jkanime has been infected with malware redirecting visitors to a Neutrino Exploit Kit landing page. More than 33 million monthly visitors were potentially exposed to the malware-based attack. At the same time, researchers from multiple security firms report seeing a sharp increase in malicious traffic from the Necurs botnet, after the drop-off observed in early June.
Be careful, the malware changes, but it is difficult to eradicate.
References
http://securityaffairs.co/wordpress/41177/cyber-crime/sophistication-exploit-kits.html
http://securityaffairs.co/wordpress/40797/cyber-crime/angler-exploit-kit-report.html
http://securityaffairs.co/wordpress/48225/malware/cryptxxx-neutrino-ek.html
http://www.talosintel.com/angler-exposed/
https://www.fireeye.com/blog/threat-research/2016/06/angler_exploit_kite.html
http://securityaffairs.co/wordpress/43482/cyber-crime/neutrino-rig-exploit-kit.html
http://securityaffairs.co/wordpress/48128/malware/angler-ek-bypasses-emet.html
https://isc.sans.edu/forums/diary/Neutrino+EK+and+CryptXXX/21141/
http://securityaffairs.co/wordpress/47598/malware/magnitude-ek-cve-2016-4117.html
http://malware.dontneedcoffee.com/2016/06/is-it-end-of-angler.html
http://securityaffairs.co/wordpress/43482/cyber-crime/neutrino-rig-exploit-kit.html
Hands-on threat intel training
https://threatpost.com/popular-anime-site-infected-redirecting-to-exploit-kit-ransomware/118890/