TeamSpy, Miniduke, Red October, and Flame: Analyzing Principal Cyber Espionage Campaigns
Even a layman would notice that cyberspace is in full storm; different entities are increasing malicious activities pursuing various purposes, and cyber espionage is considered one of the principal motivations behind majority of the attacks.
Cyber espionage is not a practices limited to governments. Private business, cyber criminals and hacktivists are also intensifying the use of cyber tools to gather sensitive information.
This article focuses the analysis on those campaigns that could be linked to the activities of state-sponsored hackers that involve a state commitment due the nature and value of information collected.
Let's make first a fundamental clarification: governments are exploring the possibility to use cyber-tools for espionage for a long time. Numerous cases report activities started many years ago that compromised high profile entities stealing secret and sensitive information.
We are facing a global game; no-one is excluded, although countries such as China, Russia, US and Israel are considered the most advanced in cyber espionage.
The governments of these countries have understood at least a decade ago how strategic is the use of cyber tools to gain information on the policies and technologies that their opposition has developed. For years, areas such as military and heavy industry are subject to intelligence activities and it's impossible to estimate the damage over time caused by this form of espionage.
In this post, I analyze in detail the events that have occurred in recent months trying to understand the motivation behind the cyber operations, how they have been conducted, and against whom.
Finally, I will discuss the recent cyber espionage campaigns discovered by researchers at Hungary-based CrySyS Lab --a decade-long activity that targeted high-level political and industrial entities in Eastern Europe.
The attackers, dubbed by security researchers TeamSpy, used a digital signed version of the popular remote control software TeamViewer specially crafted with a malware to steal secret documents and encryption keys from victims.
In many cases attackers digitally signed malicious code to improve the reputation of malware and avoid detection techniques. This method is consolidated in many operations, most of them having a state-sponsored origin.
Once installed, the compromised program provides attackers with a backdoor to control victims.
Who are the targets of cyber espionage campaign?
The hackers hit a large variety of high-level subjects including a Russian-based Embassy for an undisclosed country belonging to NATO and the European Union, multiple research and educational organizations in France and Belgium, and an electronics company located in Iran and an industrial manufacturer located in Russia.
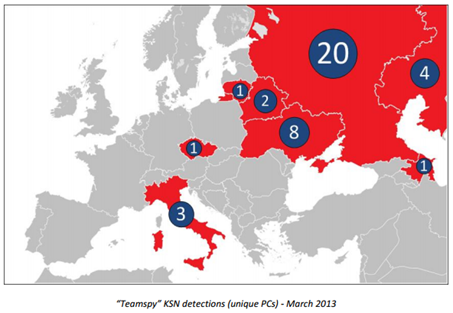
Figure 1 - TeamSpy Victims
Despite the cyber espionage that has been discovered recently, following a revelation of Hungary's National Security Authority on an attack against an unnamed "Hungarian high-profile governmental victim," the researchers dated the beginning of the cyber espionage operations to as much as a decade ago.
Ten years of espionage is an eternity. In cases like this one, a majority of victims ignore they have been compromised, and the long period of time may have allowed the attacking to hide any evidence of their work. Financial data, strategic policies, military operations and intellectual property may be exposed with unpredictable consequences.
Security analysts at Kaspersky Lab confirmed a long-term spying operation; the attackers operated varying their methods in time to avoid detection. We are facing an organization that adapted the techniques of attacks to the specific targets, adopting from time to time innovative attack techniques remaining hidden for many years.
These attackers used various malware and exploit kits infecting victims with "watering hole" attacks. In this way the TeamSpy compromised websites frequented by the intended victims. In many cases the malicious code used to infect victims was spread by Eleonore exploit kit.
The Kaspersky security experts wrote in the report:
"For at least several years, a mysterious threat actor infiltrated and tracked, performed surveillance and stole data from governmental organizations, some private companies and human rights activists throughout the Commonwealth of Independent States (CIS) and Eastern European nations. Some parts of this operation extended into Western nations and the Middle East as well, with victims in sectors such as energy and heavy industry manufacturing. The attackers performed their intelligence gathering and surveillance partly using TeamViewer (http://www.teamviewer.com/en/index.aspx), a legitimate support software package commonly used for remote administration. In addition, they deployed custom written intelligence gathering components and lateral movement utilities."
Colleagues at CrySyS Lab confirmed that the campaign could be started a decade ago:
"Most likely the same attackers are behind the attacks that span for the last 10 years, as there are clear connections between samples used in different years and campaigns," "Interestingly, the attacks began to gain new momentum in the second half of 2012.""The attackers surely aim for important targets. This conclusion comes from a number of different facts, including victim IPs, known activities on some targets, traceroute for probably high-profile targets, file names used in information stealing activities, strange paramilitary language of some structures, etc."
The surprises do not end here. Security researchers found that techniques adopted by TeamSpy are quite similar to methods implemented by the authors of an online banking fraud ring known as Sheldon. Meanwhile researchers at Kaspersky Lab found similarities to the Red October cyber espionage campaign.
The Red October campaign was discovered by Kaspersky Lab team at the end of 2012.Exactly as the TeamSpy operation, it was organized to acquire sensitive information from diplomatic, governmental and scientific research organizations all over the world – mostly from countries in Eastern Europe, the former USSR members and countries in Central Asia. The campaign hit hundreds of machines belonging to following categories:
- Government
- Diplomatic / embassies
- Research institutions
- Trade and commerce
- Nuclear / energy research
- Oil and gas companies
- Aerospace
- Military
Various elements made Red October a memorable campaign; hackers used various sophisticated malware that evaded detection at least for 5 years while continuing to stealing hundreds of Terabytes by now. Researchers discovered that attackers exploited at least three different known vulnerabilities during the attacks.
- CVE-2009-3129 (MS Excel) [attacks dated 2010 and 21011]
- CVE-2010-3333 (MS Word) [attacks conducted in the summer of 2012]
- CVE-2012-0158 (MS Word) [attacks conducted in the summer of 2012]
Different from other cyber espionage campaigns, Red October has targeted various devices such as enterprise network equipment and mobile devices (Windows Mobile, iPhone, Nokia), this is considered a dangerous and fundamental improvement. The Kaspersky Lab blog post states:
"The campaign, identified as "Rocra", short for "Red October", is currently still active with data being sent to multiple command-and-control servers, through a configuration which rivals in complexity the infrastructure of the Flame malware. Registration data used for the purchase of C&C domain names and PE timestamps from collected executables suggest that these attacks date as far back as May 2007."
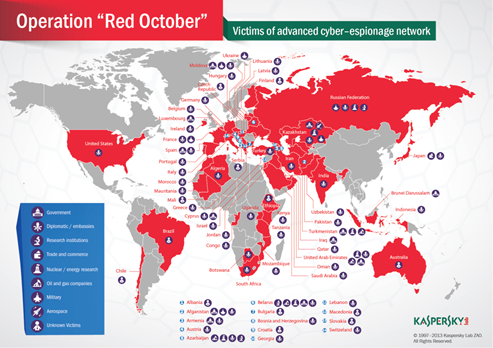
Figure 2 - Red October campaign
From the analysis of the control structure, security analysts discovered more than 60 domain names and several servers' hosts located in many countries, but mainly Germany and Russia. A particularity of the C&C architecture is that the network is arranged to hide the mothership-server true proxy functionality of every node in the malicious structure. According investigation attackers have Russian origins meanwhile used exploits appear to have been created by Chinese hackers.
Jeffrey Carr, founder and CEO of Taia Global, Inc., posted on his blog an interesting analysis that links the cyber espionage to RBN, a powerful cybercriminal organization that shut down their operations in 2007 and that was also linked in the past to government representatives.
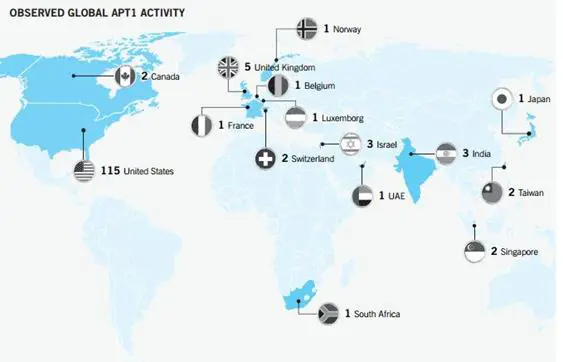
If RedOctober and TeamSpy campaigns still are without official responsibilty, the situation is different for the cyber espionage campaign dubbed APT1 and discovered by Mandiant – the security firm that tracked the operation back to China. The term APT1 is referred to one of the numerous cyber espionage campaigns that stole the major quantity of information all over the world that has interested different sectors from IT to Energy sector.
Security experts at Mandiant collected evidence that link APT1 to China's 2nd Bureau of the People's Liberation Army (PLA) General Staff Department's (GSD) 3rd Department (Military Cover Designator 61398) but what is really impressive is that the operations have been started in 2006 targeting 141 victims across multiple industries.
Figure 3 - APT1 Cyber espionage campaign (Mandiant)
Attackers have taken over the APT1 malware families, and have revealed by the report APT1′s modus operandi (tools, tactics, procedures) including a compilation of videos showing actual APT1 activity.
APT1 is responsible for the theft of hundreds of terabytes of data from victim organizations and has demonstrated the capability and intent to steal from dozens of organizations simultaneously.
Without wandering too far, at the beginning of 2013 it has been discovered that yet another operation of cyber espionage –dubbed Miniduke due the name of malware used to infect victims that hit private businesses and intelligence agencies all over the world.
Once again, the silent cyber threats attacked the above institutions to steal sensitive information and intellectual property causing damage, Kaspersky Lab and Hungary's Laboratory of Cryptography and System Security (CrySyS) discovered that unknown hackers targeted dozens of computers at government agencies across Europe in a series of cyber-attacks that exploited a recent security flaw in Adobe software. Miniduke victims were located in the following 23 countries:
Belgium, Brazil, Bulgaria, Czech Republic, Georgia, Germany, Hungary, Ireland, Israel, Japan, Latvia, Lebanon, Lithuania, Montenegro, Portugal, Romania, Russian Federation, Slovenia, Spain, Turkey, Ukraine, United Kingdom and United States.
Security experts suspect that the malicious code was designed with primary intent of gathering sensitive information. The level of sophistication of the attacks and the nature of the targets chosen lead security experts to think that incidents are state-sponsored attacks, but no hypothesis has been formulated on the nationality of the attackers.
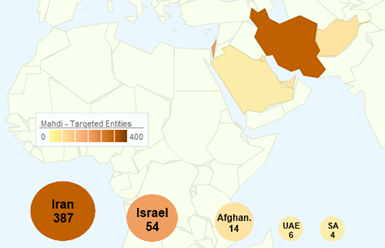
Since we have spoken of cyber espionage campaigns that mainly interested European Region, in July 2012 Kaspersky Lab experts and its partner Seculert revealed an ongoing campaign dubbed "Madi", a large scale infiltration of computer systems in the Middle East area. The hackers targeted individuals across several states of the area such as Iran, Afghanistan and also Israel.
Security researchers isolated different instances of the malware and identifying Command & Control (C&C) servers, estimating that more than 800 victims located in Middle East area and other select countries across the globe.
Figure 4 - Mahdi cyber espionage campaign (Kaspersky)
The operation seems to have started in the second half of 2011. Nicolas Brulez from Kaspersky Lab declared:
"While the malware and infrastructure is very basic compared to other similar projects, the Madi attackers have been able to conduct a sustained surveillance operation against high-profile victims,""Perhaps the amateurish and rudimentary approach helped the operation fly under the radar and evade detection."
Madi campaign exploited well known techniques to deliver the malicious payloads; the huge quantity of data collected reveals the real targets of the operation in Middle East, such as government agencies, critical infrastructure engineering firms, and financial houses. The Madi malware enables remote attackers to steal sensitive files from infected Windows computers, monitor all the activities of infected machines, first investigations suggest that multiple gigabytes of data have been stolen.
I left for last two major cyber espionage kit discovered in recent years –Duqu and Flame. Duqu is a malware discovered on September 2011 by researchers of CrySyS Lab that got its name from the prefix "~DQ" it gives to the names of files it creates.
Duqu is an agent used to gather information on industrial control systems without having destructive purpose. What surprised the security community is its relationship to the popular cyber weapon Stuxnet and its modular structure. Modularity of structure makes Duqu a very powerful tool that could adapt its behavior simply loading a specific payload. Despite the fact it hasn't used to attack systems, security experts don't exclude this possibility due the design of specific modules. Duqu is also able to steal digital certificates to be used in successive attacks to sign malicious code increasing its reputation and eluding detection systems.
Exactly as its predecessor Stuxnet, Duqu exploited zero-day vulnerability on windows system, the first-known installer analyzed by CrySyS Lab used a Microsoft Word (.doc) that exploits the Win32k TrueType font parsing engine and allows execution. Kaspersky's team analyzing the malware gathered evidence that shows that behind the Stuxnet and Duqu, there is the same development team that has used a common platform to build the malware. But what is really interesting and new is that the researchers are convinced that the same framework has been also used to design other malware. Costin Raiu, Director of Kaspersky Lab's Global Research, said
"It's like a Lego set. You can assemble the components into anything: a robot or a house or a tank,"
Researchers with Kaspersky have named the platform "Tilded" because many of the files in Duqu and Stuxnet have names beginning with the tilde symbol "~" and the letter "d."
I conclude this view on principal cyber espionage campaign with Flame malware detected in May 2012by the Iranian Computer Emergency Response Team (MAHER), CrySyS Lab and Kaspersky Lab.
Once again the malicious code hit Windows systems of the Middle East area, specifically Iran, circumstances that don't leave doubts on its state-sponsored origin. The discovery was made by Iranian scientists during the investigation on the malicious agents Stuxnet and Duqu, and what surprised them was the capability of the malware to dynamically change its behavior, including receiving and installing specific modules designed to address specific targets.
The malware is dated at least to 2010 and it is considered a complex agent designed with the primary intent to create a comprehensive cyber espionage tool kit. The Kaspersky team demonstrated a strong correlation between Stuxnet and Flame, also highlighting deep differences between the malicious codes, Kaspersky expert Roel Schouwenberg noted that no Flame components have been used in more advanced versions of Stuxnet:
"Flame was used as some sort of a kick-starter to get the Stuxnet project going," he stated. "As soon as the Stuxnet team had their code ready, they went their way."
Starting from 2009, the evolution of the two projects has proceeded independently. This circumstance supports the hypothesis that behind Stuxnet and Flame there were two distinct groups of development named by Kaspersky "Team F" (Flame) and "Team D" (Tilded). Kaspersky CEO Eugene Kaspersky declared:
"there were two different teams working in collaboration."
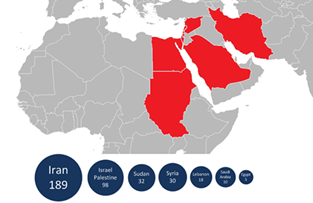
Figure 5 - Geographic Distribution of Flame malware according Kaspersky Lab
Finally, see this view on principal cyber espionage campaigns detected in the last years.Let's try to analyze various factors that emerge in an initial analysis.
Principal considerations:
-
Cyber espionage phenomena have exploded in the last months. The operations detected appear related to governments' activities or anyway conducted by group of state-sponsored hackers. In every case, the high profile of victims, the geographic distribution of the infection, and nature of the information gathered suggest a strong commitment of governments.
-
The level of complexity of malicious code developed to hit specific targets is high. In cases such as Duqu/Stuxnet and the APT1 campaigns, the attackers have conducted continuous research over time to adapt their offensive, defining new strategies and exploiting an increasing number of vulnerabilities. This consideration corroborates the hypothesis that behind the attacks, there are groups of high skilled specialists supported and financed by governments that prepared with meticulous care every operation.
-
The majority of operations is dated many years ago, this means that actors behind the operations have had time to collect high quantity of information with direct impact on economic, politics and industrial aspects of the victims. All the presented cases are characterized by a multiple attacks against various sectors of the country hit, with one unique exception represented by Duqu, that despite could be also used for pure cyber espionage activity has been spread with primary purpose to gather info of targets of cyber-attacks.
-
The duration of the operations highlight the inadequacy of defense systems. The cyber threats, in fact, have remained hidden for long period. In the current cyber scenario, a multi layered approach is absolutely needed to build alert networks to detect cyber espionage campaigns in time. Some companies such as Mandiant have tried to define a set of indicators that could trigger an alarm related to ongoing cyber espionage activities. Probably while I'm writing many other campaigns are ongoing, many experts believe that the attacks discovered are just the tip of the iceberg.
-
Another curious detail that often not perceived is that all these cyber threats were not discovered by government entities, except for Flame case, nevertheless governmental agencies around the world have been attacked successfully. This consideration makes me think that governments and their infrastructures are still too much vulnerable to cyber threats and totally unprepared to mitigate their effects.
Are states all over the world really ready to play a cyber-dispute on global scale?
Are countries conscious that being unprepared to the cyber threats could change the course of their history?
As some claim, do we really need to take a step back before to reach a point of no return?
I wonder how many political decisions have already been influenced by knowledge of the information stolen during these campaigns. While cyber espionage has probably already written the contemporary history, do we want it to change our future?
References
http://www.crysys.hu/teamspy/teamspy.pdf
http://dougvitale.wordpress.com/2012/11/08/hardcore-malware-stuxnet-duqu-and-flame/
https://www.securelist.com/en/downloads/vlpdfs/theteamspystory_final_t2.pdf
http://jeffreycarr.blogspot.it/2013/01/rbn-connection-to-kasperskys-red.html
http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf
https://www.securelist.com/en/downloads/vlpdfs/themysteryofthepdf0-dayassemblermicrobackdoor.pdf
http://www.crysys.hu/publications/files/bencsathPBF11duqu.pdf
http://www.enisa.europa.eu/media/news-items/duqu-analysis/view
Hands-on threat intel training