RansomWar(e)
There is a notable upsurge in the number of ransomware attacks in the past couple of months, and undoubtedly the emergence of the CryptoLocker ransomware is among the most significant contributory factors to this trend. Yet a calamity never comes alone, and presumably for every new threat there is a plausible explanation. In order to find out why this particular group of malware is so popular, we need to dismantle first some of the constituent parts, screws, and bolts that hold together the shell of this digital pest, and look under the hood, scrutinize common tactics, and eventually draw precise conclusions.
In this article, the reader will have the opportunity to catch a glimpse at the notorious Law Enforcement ransomware that was a worldwide menace in 2012 and 2013. The main subject, however, is the CryptoLocker—a type of ransomware that has come into existence in September 2012— the way it has affected many users in full blast shortly after its appearance, its descendants, and reasons why and how it has quickly become such a popular choice for cyber criminals.
Law Enforcement Ransomware /a.k.a. FBI Ransomware or Police Ransomware/
Law Enforcement ransomware is a powerful alloy between the Citadel Trojan, an offset of the Zeus banking Trojan, and the Reveton drive-by Trojan. For the mass public, this ransomware bundle is famous for the fact that it abuses the FBI's name and logo, and refers to its InfraGard and IC3 programs. The malware "delivery" process is via drive-by download attacks from compromised websites rather than the traditional phishing attacks and bad email attachments.
The Citadel malware toolkit has the ability to record users with their own web cam and leverage IP address localization to devise an artful warning message that will really intimidate victims and make them pay up the ransom in no time.
Diagram 1
FBI Ransomware Message

What follows in terms of effects and crackers is familiar—the screen freezes, a violation warning of U.S. federal laws appears complemented by an accusation that victim's IP address was recognized as one visiting child pornography and other illegal content. Of course all these mortal sins are to be 'indulged' at the expense of $300, right here right now. Curiously, this ransomware is like a smart bomb that plays a psychological game because it actually "senses" and attacks visitors of adult or sharing websites, and they already feel somewhat guilty.
Not only that, but once the "fine" is paid, the Citadel malware "[continues] to operate on the compromised computer and could be used to commit online banking and credit card fraud."
No wonder that the FBI received a staggering total of 289,874 complaints for 2012 alone with respect to the aforementioned malicious software.
You can find useful information on how to handle the threat here.
The Browlock ransomware
A type of browser ransomware — a variant of the Law Enforcement one — that spreads through malvertising where the victim is redirected through an ad from one website to another. The final destination is a corrupt Browlock website that 1) generates a law enforcement image corresponding to the victim's country of origin; 2) demands a payment of a fine for copyright or child pornography violations; 3) prevents users from closing the tab;
it is the simplest ransomware known.

CryptoLocker Ransomware
Distribution & Infection
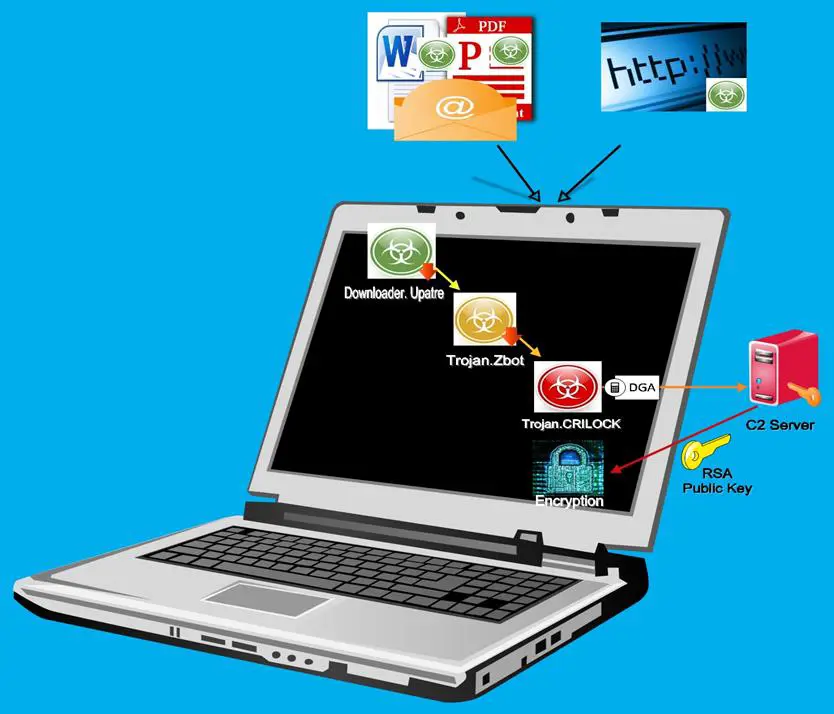
The CryptoLocker, a Windows-only threat, was first noticed in the beginning of September, and these early versions were distributed via social engineering and spam emails that try to entice business professionals into opening an attached Zip file. These Zip archive docs, approximately 20KB in size and with filename having between 13 and 17 charters, contain a tiny executable file dressed up as an invoice, for instance, depending on the email theme. Distribution via websites compromised with the help of malicious exploit kits is now possible as well, but it is rare as compared to the spamming method.
In reality, this executable is Downloader.Upatre, a malware that will download Gameover Zeus trojan (a.k.a. Trojan.Zbot), which in turn will download Trojan.CryptoLocker (See Diagram 2). Once inside the compromised system, CryptoLocker establishes a connection thread with a command-and-control server (C&C). The malware may utilize Domain Generation Algorithm (DGA), which can generate 1,000 domains daily and hold onto the first available line, to seek a live C2 server if the hardcoded connection initially stumbled across an impediment. Only servers possessing a right RSA private key can decrypt the message sent, thus successfully communicate with the infected system. After a contact is made, CryptoLocker will download a public key that will be used to seek out a wide array of file extensions residing on the victim's PC (See Targeted Data section) and launch an encryption process.
Diagram 2
Distribution and Initial Infiltration Step-by-Step
Encryption
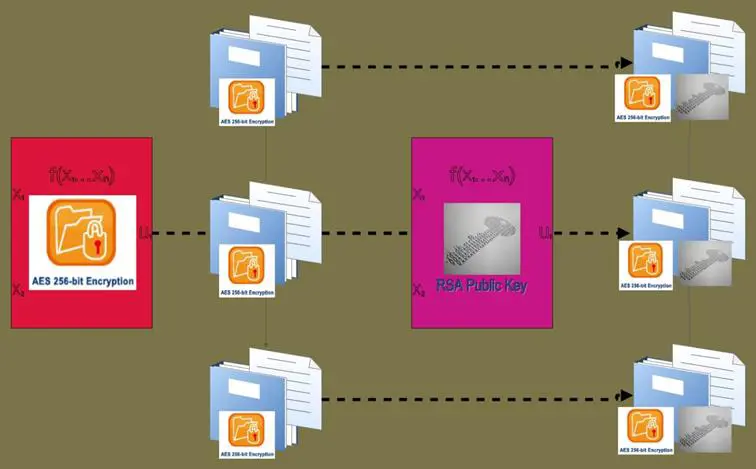
Microsoft's cryptography that uses asymmetric encryption is adopted by CryptoLocker. Every single file of interest on the victim's machine is first encrypted with a unique AES key, and then these files are double-encrypted with the RSA public key sent by the C2 server (See Diagram 3).
Encrypted key and file contents are then saved on the disc, replacing the originals. Recovery is possible only by obtaining the RSA private key, which is in the exclusive possession of the cyber criminals. Rendered unreadable, users would most likely lose every bit of their data if they do not obtain the private key, in other words, do not pay the ransom.
Diagram 3
CryptoLocker's Double Encryption
Expectedly, CryptoLock reveals its presence only after the whole encryption process is set and done. Then the victim is presented with a splash screen that demands a $300 ransom (0.3 Bitcoin as of this publication) payable within a given time frame, usually 72-100 hours.
Diagram 4
Cash for Decryption Key

With regard to missed deadlines, the criminals behind CryptoLocker decided to introduce in the early November a "Late payment" option accessible via TOR, giving mercifully victims a chance to deliver the ransom after the deadline. Of course, that option comes at a price (an arm and a leg almost), 2BTC.
Targeted Data
Encrypted by CryptoLocker are the following patterns of filenames:
????????.jpe, ????????.jpg, *.3fr, *.accdb, *.ai, *.arw, *.bay, *.cdr, *.cer, *.cr2, *.crt, *.crw, *.dbf, *.dcr, *.der, *.dng, *.doc, *.docm, *.docx, *.dwg, *.dxf, *.dxg, *.eps, *.erf, *.indd, *.kdc, *.mdb, *.mdf, *.mef, *.mrw, *.nef, *.nrw, *.odb, *.odc, *.odm, *.odp, *.ods, *.odt, *.orf, *.p7b, *.p7c, *.p12, *.pdd, *.pef, *.pem, *.pfx, *.ppt, *.pptm, *.pptx, *.psd, *.pst, *.ptx, *.r3d, *.raf, *.raw, *.rtf, *.rw2, *.rwl, *.sr2, *.srf, *.srw, *.wb2, *.wpd, *.wps, *.x3f, *.xlk, *.xls, *.xlsb, *.xlsm, *.xlsx, img_*.jpg
CryptoLocker may even encrypt files on any connected drives—mapped network shares and folders located on Cloud services.
Can Anti-virus Software Help?
A good anti-virus system in place may neutralize the CryptoLocker, but it cannot unscramble files that have already been encrypted. As ridiculous as it may sound, a good anti-virus program might prevent you from paying the ransom, if you want to go this way actually, because it may remove the CryptoLocker. Fascinatingly, the criminal mind that designed the malware anticipated such a "predicament" for the victim, and the wallpaper on the infected computer is changed so as to allow users a new download and reinstall of CryptoLocker.
Current Payment Options
While in early versions of CryptoLocker there were numerous payment alternatives, now the option is only between Bitcoin and MoneyPark.
Victims
Security specialists report that English-speaking countries are most affected by CryptoLocker, with the United States being a preferred target. According to Dell's researchers, in the first 100 days of the life of CryptoLocker, the malware managed to contaminate between 200,000 and 250,000 PCs. However, "a minimum of 0.4%, and very likely many times that" of the victims agreed to pay the ransom demand.
Perhaps the most famous case up to date of a victim that has paid is the one of the police department of Swansea, Massachusetts. Despite the successful recovery of data in this case, the security firm Trend Micro has warned that yielding to blackmail requests only encourages malicious actors to further propagate CryptoLocker and create even more robust new versions of ransomware.
Prevention & Disinfection
The best practices are almost identical with those one faces defending against phishing techniques complemented with other tips in similar IT security areas. For more you could click here.
Diagram 5
CryptoLocker and Friends
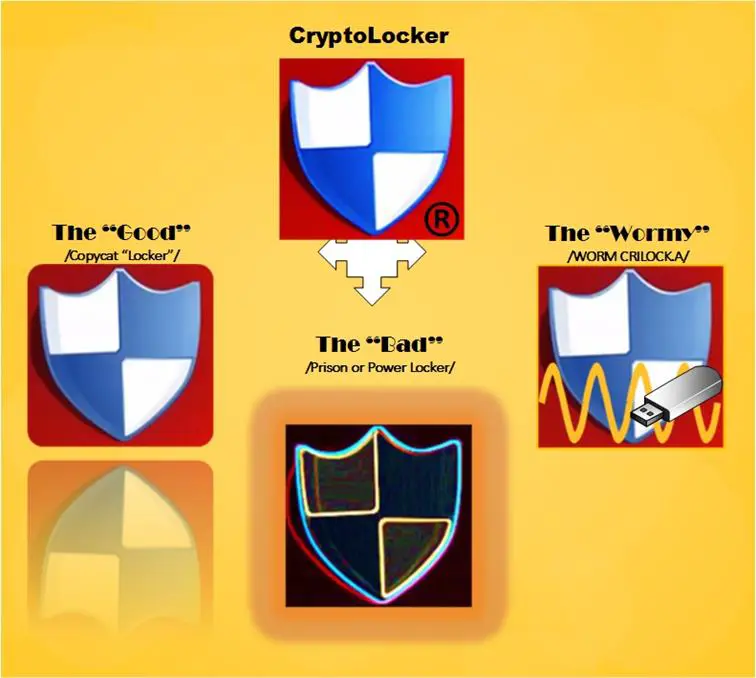

Copycat "Locker"
Locker, a copycat of CryptoLocker, has some interesting specifications:
- It omits systems on which there are tools used for security research and analysis.
- It spreads via drive-by downloads on compromised websites or through executables that look on the outside as MP3 files.
- "Each 'decryptor' has a list of hardcoded IP addresses that helps each sample to operate without any C&A at all, in order to hide the owner and to have no roots at all, besides e-commerce details."
-Locker utilizes AES-CTR for the content encryption of victims' files. Researchers, however, considered creating a skeleton key for unlocking scrambled files as a possible mission due to programming defects.
-With the previous point taken into account, many specialists rank Locker inferior in comparison to CryptoLocker.

WORM CRILOCK.A
Typical CryptoLocker cannot travel on its own and does not self-replicate.
Nevertheless, a new strain of this ransomware, WORM CRILOCK.A, has been recently found, which, much like a USB-spreading worm (it does not need the UPATRE downloader), replicates and propagates on its own initiative by initially penetrating the first host under the guise of an activator for Microsoft Office or Adobe Photoshop seeded on Peer-to-Peer (P2P) sharing sites. Aside from its unusual dissemination technique, it is remarkable for the fact that it does not use DGA algorithm, and thus, as distinct from the classic CryptoLocker, the worm mode relies on fixed control-server domains, a circumstance that allows anti-virus software easier detection and blocking.

PrisonLocker (PowerLocker)
A new ransomware one level up from the CryptoLocker is looming, according to a report by the security research group Malware Must Die (MMD). MMD has spotted a message on a hacking forum in November for the new-born PrisonLocker (also goes by the name PowerLocker). Directly from the source, here are some of the most prominent characteristics of this new malware:
The first level of encryption is changed to BlowFish algorithm that generates a unique key for each file. "That BlowFish key is then encrypted with an RSA key specific to the PC, then the RSA block is stored with the file to be decrypted later."
Missing in the typical CryptoLocker, a locker module is another insidious innovation that disables OS system, processes like cmd.exe and taskmgr.exe (Ctl+Alt+Del is impossible), victims' escape keys,. The new locker module implants a new desktop, usually impervious to removal from the user's perspective, which "checks to make sure user is in the right desktop every few miliseconds, and if the user is another desktop it is immediately switched back." And if the user is able somehow to overcome the locker screen, his files will still remain unbreakably encrypted.
PrisonLocker "uses 5+ anti VM and debugger methods to deter analysis."
On top of everything, the PrisonLocker will come cheap — $100, a price that will certainly make it affordable to many cyber criminals and thrill-seekers.
The Demise of the BlackHole Malware Kit or Why Ransomeware Have Become so Pervasive
BlackHole is a cyber crimeware kit — a software package sold on underground online markets that combines several modules needed to administer all functions of a specific type of malware. Furthermore, it exploits automatically vulnerabilities in loose browsers, Java and Adobe software.
These toolkits thrive "because they are so easy to configure and deploy," as one security researcher pointed out. Because malware kits come as a whole package of services ranging from help pages to timely updates and technical support, more and more amateurs can enter the world of cyber crime.
Certainly, because of its unmatched characteristics, frequent update, and relatively low cost, BlackHole made furor not long after its debut on the online forums for hackers in 2010. Nevertheless, every good thing, from a criminal point of view, has its end, and the end of this exploit kit apparently coincided with the arrest of its Russian creator in the early October.
Ever since then, cyber crooks have been looking feverishly for a replacement. A toolkit named Magnitude looks like a probably successor, but it is more like probing than a real baton passing.
However, Jeff Williams, the director of security strategy for Dell SecureWorks Counter Threat Unit, shares that they have seen "various exploits move from BlackHole to other kits, like Reveton ransomware."
What is really curious is the post-BlackHole takedown trend in the behaviour of cyber criminals, namely, switching from spams that deliver malicious links to more sophisticated social engineered emails that bring along infected attachments (See Diagram 6). Alex Watson analyzes the situation this way: "They've [(the cybercriminals)] had to put more work into the social engineering and having sophisticated-looking emails to get users to click. A second thing we've noticed is an increased aggressiveness with malware installations on computers that are compromised."
For example, before the arrest of the person who supported BlackHole, many cybercriminals made a living by sending out links through the infamous spam botnet Cutwail, leading innocent people to websites that host BlackHole. A downloader is injected there, which in turn would bring in more members of the malware family such as Zeus or Zero Access. These, on the other hand, steal credit card data and banking credentials or make other disastrous mischief.
Diagram 6
Events That Promote the Widespread Adoption of Ransomware in the Last Quarter of 2013
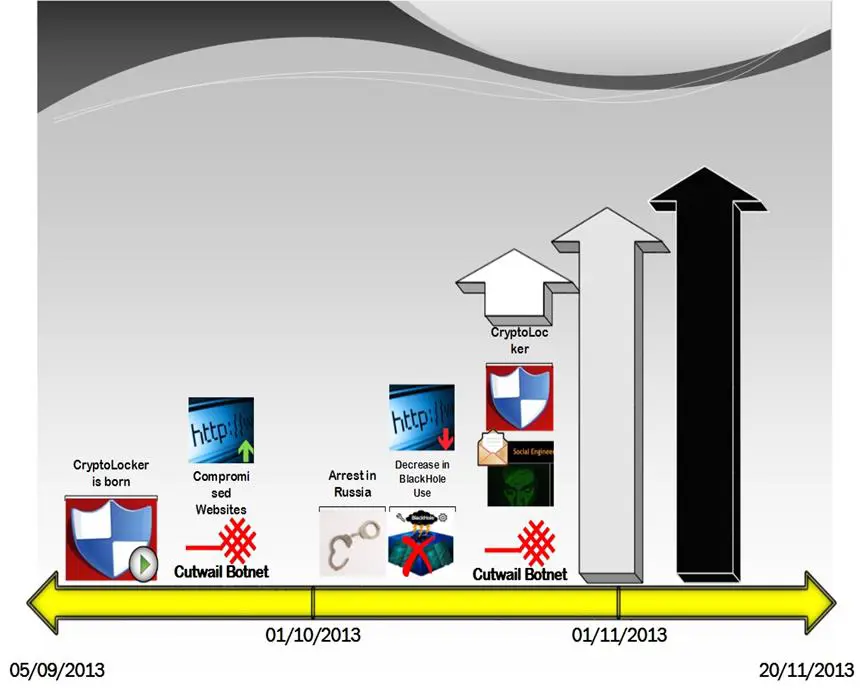
Well, that profitable maneuver was not possible after the end of the BlackHole story, was it? And the spammers cannot cease jamming people's email spam boxes all of a sudden just because their favorite toy is broken. That might mean the end of their business. So we have become witnesses of a behaviour-changing occurrence that shapes a new trend in the cybercrime circles, and now Cutwail is sending out considerably more spamming with embedded dangerous attachments. Logically, CryptoLocker (UPATRE), among other types of ransomware, is one of the weapons selected to make up for the loss of revenue following the arrest.
Some of that dynamic proved to be enough to instigate the criminal minds to invest more resources and time particularly in CryptoLocker and its derivatives. The key reason is the fact that ransomware, inter alia, "gives an attacker an immediate shot at collecting a payout." And according to many observers, CryptoLocker has been very successful so far, especially with regard to ill-prepared smaller companies.
Conclusive Thought
If we decide to go rewind the tape by a couple of years, we would notice that FakeAVs were the predecessor of ransomware. Compared to FakeAV, ransomware impinges more severely upon users' control over their PC. While the former deludes that there is a virus and you need an antidote, the latter, in fact, is a virus that holds your data hostage until you pay up.
Clearly, there is a difference in the directness of how these two "scareware" schemes operate, and the evolution of information security, among other things, imposes the decline of the FakeAV business and the growth of the ransomware swindle. Whether the ransomware will persist is a question within the abilities of fortune-tellers, but given the tendencies in the world of cyber security, it seems very likely so in the measurable future…besides, you probably know the proverb: "One never truly feels the breeze until it blows him away."
Reference List
Blue, V. (2013). CryptoLocker's crimewave: A trail of millions in laundered Bitcoin. Retrieved on 19/01/2014 from http://www.zdnet.com/cryptolockers-crimewave-a-trail-of-millions-in-laundered-bitcoin-7000024579/
Cluley, G. (2013). CryptoLocker: What is it? And how do you protect against it? Retrieved on 19/01/2014 from http://grahamcluley.com/2013/11/cryptolocker-protect/
Cluley, G. (2014).Worryingly, CryptoLocker ransomware turns from a Trojan… into a worm. Retrieved on 19/01/2014 from http://grahamcluley.com/2014/01/cryptolocker-ransomware-worm/
Cooney, M. (2012). US warns users of new Citadel ransomware hit. Retrieved on 19/01/2014 from http://www.networkworld.com/news/2012/053112-citadel-259739.html
Doyle, S. (2013). How to remove the FBI virus (FBI Moneypak Ransomware) – Fake FBI Malware Removal Options. Retrieved on 19/01/2014 from http://botcrawl.com/how-to-remove-the-fbi-moneypak-ransomware-virus-fake-fbi-malware-removal/
Frink, L. (2013). The Three Types of Malware that Scare, Threaten, and Abuse. Retrieved on 19/01/2014 from http://blog.hotspotshield.com/2013/09/09/what-are-scareware-ransonware/
Gorman, G. (2013). Massive Malvertising Campaign Leads to Browser-Locking Ransomware. Retrieved on 19/01/2014 from http://www.symantec.com/connect/blogs/massive-malvertising-campaign-leads-browser-locking-ransomware
http://www.infosecurity-magazine.com (2014). PrisonLocker – a Step Up From Cryptolocker. Retrieved on 19/01/2014 from http://www.infosecurity-magazine.com/view/36344/prisonlocker-a-step-up-from-cryptolocker/
http://www.spamfighter.com (2013). Browlock Ransomware Uses Malvertising to Direct Internauts to Malicious Site. Retrieved on 19/01/2014 from http://www.spamfighter.com/News-18733-Browlock-Ransomware-Uses-Malvertising-to-Direct-Internauts-to-Malicious-Site.htm
Jarvis, K. (2013). CryptoLocker Ransomware. Retrieved on 19/01/2014 from http://www.secureworks.com/cyber-threat-intelligence/threats/cryptolocker-ransomware/
Jeffers, D. (2013). Crime pays very well: Cryptolocker grosses up to $30 million in ransom. Retrieved on 19/01/2014 from http://www.pcworld.com/article/2082204/crime-pays-very-well-cryptolocker-grosses-up-to-30-million-in-ransom.html
Kelion, L. (2013). Cryptolocker ransomware has 'infected about 250,000 PCs'. Retrieved on 19/01/2014 from http://www.bbc.co.uk/news/technology-25506020
Kitten, T. (2013). Trojans Tied to New Ransomware Attacks. Retrieved on 19/01/2014 from http://www.bankinfosecurity.com/citadel-again-tied-to-ransomware-attacks-a-6064/op-1
Kovacs, E. (2013). Experts Find Link Between BlackHole Author's Arrest and Emergence of CryptoLocker. Retrieved on 19/01/2014 from http://news.softpedia.com/news/Experts-Find-Link-Between-BlackHole-Author-s-Arrest-and-Emergence-of-CryptoLocker-398700.shtml
Leyden, J. (2013). Cryptolocker copycat ransomware emerges – but an antidote is possible. Retrieved on 19/01/2014 from http://www.theregister.co.uk/2013/12/13/locker_ransomware/
Leyden, J. (2014). CryptoLocker creeps lure victims with fake Adobe, Microsoft activation codes. Retrieved on 19/01/2014 from http://www.theregister.co.uk/2014/01/02/cryptolocker_worm/
Malware Must Die (2014). Threat Intelligence - New Locker: Prison Locker (aka: Power Locker ..or whatever those bad actor call it). Retrieved on 19/01/2014 from
http://malwaremustdie.blogspot.in/2014/01/threat-intelligence-new-locker-prison.html
Manly, M. (2013). CryptoLocker Emergence Connected to Blackhole Exploit Kit Arrest.
Retrieved on 19/01/2014 from http://blog.trendmicro.com/trendlabs-security-intelligence/cryptolocker-emergence-connected-to-blackhole-exploit-kit-arrest/
Mimoso, M. (2013). Cutwail Botnet Feeling Effects of Blackhole Takedown. Retrieved on 19/01/2014 from http://threatpost.com/cutwail-botnet-feeling-effects-of-blackhole-takedown/103228
Mimoso, M. (2014). Viable Blackhole Successor Could Take Years to Emerge. Retrieved on 19/01/2014 from http://threatpost.com/viable-blackhole-successor-could-take-years-to-emerge/103492
O'Neill, R. (2013). Cryptolocker: Menace of 2013. http://www.zdnet.com/cryptolocker-menace-of-2013-7000024299/
Schwartz, M. (2012). Ransomware Pays: FBI Updates Reveton Malware Warning. Retrieved on 19/01/2014 from http://botcrawl.com/how-to-remove-the-fbi-moneypak-ransomware-virus-fake-fbi-malware-removal/
Simpson, S. (2013). Paunch Arrested: The State of BlackHole Exploit Kit.
Retrieved on 19/01/2014 from http://www.verizonenterprise.com/security/blog/index.xml?postid=4794
Symantec (2013). Cryptolocker Q&A: Menace of the Year. Retrieved on 19/01/2014 from http://www.symantec.com/connect/blogs/cryptolocker-qa-menace-year
Trend Micro (2013). Ransomware Raises the Stakes With CryptoLocker. Retrieved on 19/01/2014 from http://about-threats.trendmicro.com/relatedthreats.aspx?language=au&name=Ransomware%20Raises%20the%20Stakes%20With%20CryptoLocker
Wagenseil, P. (2014). Cryptolocker Ransomware Evolves to Spread on Its Own. Retrieved on 19/01/2014 from http://news.yahoo.com/cryptolocker-ransomware-evolves-spread-own-223413814.html
Walker, D. (2013). Criminals move quickly to other exploit kits after arrest of BlackHole author. Retrieved on 19/01/2014 from http://www.scmagazine.com/criminals-move-quickly-to-other-exploit-kits-after-arrest-of-blackhole-author/article/315629/
Walker, D. (2014). New ransomware, more insidious than CryptoLocker, to go on market. Retrieved on 19/01/2014 from http://www.scmagazine.com/new-ransomware-more-insidious-than-cryptolocker-to-go-on-market/article/328307/
Wismer, D (2013). Hand-To-Hand Combat With The Insidious 'FBI MoneyPak Ransomware Virus'. Retrieved on 19/01/2014 from http://www.forbes.com/sites/davidwismer/2013/02/06/hand-to-hand-combat-with-the-insidious-fbi-moneypak-ransomware-virus/
Diagrams
Diagram 2 is based on the "CryptoLocker Infection Chain" graph provided by Trend Micro in Ransomware Raises the Stakes With CryptoLocker. Retrieved on 19/01/2014 from http://about-threats.trendmicro.com/relatedthreats.aspx?language=au&name=Ransomware%20Raises%20the%20Stakes%20With%20CryptoLocker ; and based on the Figure 2. "Cryptolocker spam email example" provided by
Symantec in Cryptolocker Q&A: Menace of the Year. Retrieved on 19/01/2014 from http://www.symantec.com/connect/blogs/cryptolocker-qa-menace-year
Diagram 3 is based on Diagram 2 is based on graph in the "How does the encryption work" section provided by Trend Micro in Ransomware Raises the Stakes With CryptoLocker. Retrieved on 19/01/2014 from http://about-threats.trendmicro.com/relatedthreats.aspx?language=au&name=Ransomware%20Raises%20the%20Stakes%20With%20CryptoLocker
Diagram 6 is based on information from Figure 13 in CryptoLocker Ransomware (2013) by Keith Jarvis. Retrieved on 19/01/2014 from http://www.secureworks.com/cyber-threat-intelligence/threats/cryptolocker-ransomware/










