Lights and shadows on the capabilities of the NSA
Introduction
The documents leaked by Edward Snowden revealed to the world the amazing spying machine built by US intelligence, its capabilities appears virtually infinite, the US agents, in fact, are able to infect targets even if they are not online, they are able to control any communication and can practically interfere with any technology we use daily.
NSA technologies allow the Agency to spy on targets when they are surfing on the web, playing video games or searching for anonymity through TOR network, nothing seem be able to protect individuals from a global surveillance network. Yes, I mentioned a global surveillance network because the NSA isn't the unique government involved in monitoring activities, in many cases, they also collaborated to share data on their population, it is the case, for example, of the alliance of intelligence operations conducted by Australia, Canada, New Zealand, UK and USA.
The NSA had access to fibre-optic cable to wiretap huge quantity of data from intercontinental communication officially to prevent illegal activities and terrorist acts, but many security experts consider the surveillance too invasive and also oriented to the industrial espionage.
Today is requested to intelligence agencies to gather information on industrial competitors to reduce the technological gap between the states, China is accused to have focused its politic on an aggressive cyber conduct to steal intellectual properties from foreign countries.
The former NSA contractor Edward Snowden revealed that the National Security Agency is responsible of industrial espionage, he made the unconfortable declaration during an interview to the public German broadcaster ARD TV.
The whistleblower confirmed that the US Intelligence has conducted numerous campaigns against foreign governments and private companies like the German Siemens. The news doesn't surprice the experts, previous leaked document documents have already described the activities of the NSA to spy on foreign politic representatives and media, probably the most blatant case was the spy story on the Chancellor Angela Merkel's mobile phone.
Which is the link between a private company like Siemens and US Intellogence? Are the cyber espionage campaign conducted only to ensure Homeland Security?
"If there's information at Siemens that's beneficial to US national interests – even if it doesn't have anything to do with national security – then they'll take that information nevertheless," said Snowden.

Figure 1 - Snowden Interview at German TV
Yesterday I made an interview with an important new agency and the journalist asked me which are the three topics that most of all have captured my attention in the Snowden case apart the technologies and exploit described in NSA catalog and I had no hesitation to in the answer, Quantum computing, Gaming surveillance and Tor Network infiltration.
Quantum Computing
The Washington post was the first newspaper to publish news on the effort spent by the NSA to build a quantum computer that could break most types of encryption.
The NSA breaking encryption algorithms, and applications that use them, could practically access to any data on a protected communication channel, nothing could be protected by wiretapping activities of US intelligence.
The intent is to operate the surveillance on a large scale, spy on other foreign governments and also on every business's online activity, even it is done protected by encryption algorithms. Snowden leaked documents that make explicit reference to NSA development for a quantum computer to engage to break encryption codes used to protect sensitive data all over the world.
Figure 2 - Quantum computing
"With such technology, all current forms of public key encryption would be broken, including those used on many secure Web sites as well as the type used to protect state secrets."
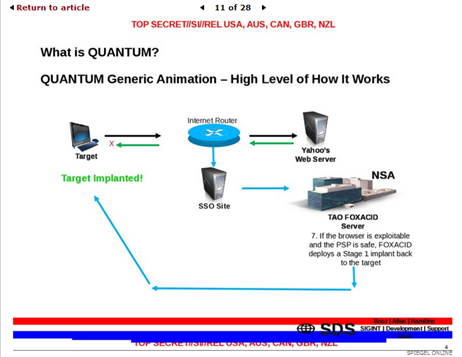
Figure 3 - NSA Leaked Documents on Quantum computer
"The application of quantum technologies to encryption algorithms threatens to dramatically impact the US government's ability to both protect its communications and eavesdrop on the communications of foreign governments," according to an internal document provided by Snowden." reports The Washington Post.
In one of the slides leaked by Snowden, and also published by the Spiegel magazine on line, are described the "Quantum capabilities" according the NSA. The intelligence Agency desires to develop a quantum computer to break encryption adopted by principal web services, including Facebook, Yahoo and Twitter.
What is a quantum computer?
A quantum computer is a computation device that makes direct use of quantum-mechanical phenomena to perform calculation, this confers it an extraordinary computational capability.
"Quantum computers are different from digital computers based on transistors. Whereas digital computers require data to be encoded into binary digits (bits), quantum computation uses quantum properties to represent data and perform operations on these data"
The Washington Post seems to confirm that NSA is working on the design for a quantum computer, but the realization of a final prototype could take years, the newspaper doesn't provide any information on the involvement of private companies for the designing of the supercomputer.
Quantum computers could be used not only in cryptanalysis, but similar capabilities could be extended in other industries medicine.
The NSA development of a quantum computer is partially financed with funds belonging to research program codenamed "Penetrating Hard Targets" for which the Government reserved $79.7 million.
"The geographic scope has narrowed from a global effort to a discrete focus on the European Union and Switzerland," one NSA document states.
There is also the news of another secret project called "Owning the Net," its name is eloquent, the intelligence is working on a system to break encryption algorithms and also in this case it is financing the research for the development of a quantum computer able.

Figure 4 - Penetrating Hard Targets Project


Figure 5 - Owning the Net Programme
After the revelations made by Snowden on US secret programs the US Government is rearranging its internal infrastructures, giving much more importance to cyber security, but the targets of its programs are aware of the NSA'activities and this is pushing NSA to find a new way to open the closed doors, quantum computing could represent its passepartout.
The Gaming surveillance
The document leaked by Snowden demonstrated that NSA is able to use any technology for surveillance, it is natural that the Intelligence has considered the possibility to infiltrate the virtual world of online games. Gaming platform are complex machines always online that offers to the gamers also channels of communication, in many cases they support gaming communicties that also utilize their virtual currency schema.
For these reasons Intelligence agencies consider gaming platforms as an attractive environment for cyber terrorists and hackers, the Guardian published, in partnership with the New York Times and ProPublica, the news that NSA and GCHQ have operated in virtual worlds and gaming communities to conduct intelligence operations and tried to recruit informants. The document leaked by Snowden and published by the Guardian titled "Exploiting Terrorist Use of Games & Virtual Environments" is dated 2008 and reports the possibility that groups of terrorists use gaming platfoms and their services to communicate. The documentation remarks the necessity to monitor online gaming communities describing them as a "target-rich communications network" where intelligence targets could "hide in plain sight".

Figure 6 - Exploiting Terrorist Use of Games & Virtual Environments
The document provides a warning on the possible abuse of online gaming communities, but doesn't contains an indication on real case discovered by the intelligence agencies.
The Games and Virtual Environments (GVE) allow individuals to communicate in private chat (P2P), group chat and also broadcast chat, platform like Second Life offer the possibility to anonymously text to a GSM phone (SMS).
But GVE could be exploited by groups of terrorists also because they offer realistic weapons training, military operations and tactics, the document remark that an abstraction of reality is sufficient for this purpose remarking that some of 9-11 pilots had never flown a real plane, but they had only trained with the MS Flight Simulator.
The Secret Services have infiltrated the principal online game communities, including Second Life to monitor users' habits and intercept their communications, NSA and GCHQ have created human avatars to explore virtual reality and prevent terrorist initiatives.
The CIA, FBI and Defense HUMINT service all have HUMIT operations in Second Life and other GVEs, the intelligence considers gaming an opportunity for its investigations, the games could be used for Computer network exploits, social network analysis, subject tracking and geo-localization of targets.
"Al-Qaida terrorist target selectors and … have been found associated with XboxLive, Second Life, World of Warcraft, and other GVEs [Games and Virtual Environments]," "Other targets include Chinese hackers, an Iranian nuclear scientist, Hizballah, and Hamas members." states the documents.
The principal concern for both agencies is that into the gaming communities could be hidden terrorists making propaganda or that exploit the channel for covert communications.
Figure 7 - Second Life
"Games, the analyst wrote "are an opportunity!". According to the briefing notes, so many different US intelligence agents were conducting operations inside games that a "deconfliction" group was required to ensure they weren't spying on, or interfering with, each other. If properly exploited, games could produce vast amounts of intelligence, according to the the NSA document. They could be used as a window for hacking attacks, to build pictures of people's social networks through "buddylists and interaction", to make approaches by undercover agents, and to obtain target identifiers (such as profile photos), geolocation, and collection of communications. The ability to extract communications from talk channels in games would be necessary, the NSA paper argued, because of the potential for them to be used to communicate anonymously: Second Life was enabling anonymous texts and planning to introduce voice calls, while game notice-board could, it states, be used to share information on the web addresses of terrorism forums." reports The Guardian.
The interest in exploitation of gaming platform is not recent, in the past other special projects promoted by US Intelligence had the goal to hack gaming console all over the world for information gathering on a large scale. The gaming consoles are powerful platforms, capillary spread, which could be exploited to spy on players's environments, the documents leaked by the Guardian reveal a large scale infiltration against the Xbox Live console network that accounts more than 48 million players.
The document leaked don't reveal how NSA and GCHQ spy on gamers' activities and if the agencies have received the support of the gaming industry.
"We are unaware of any surveillance taking place," "If it was, it would have been done without our knowledge or permission." declared a spokesman for Blizzard Entertainment, while Microsoft and the founder of Second Life declined to comment the news.
Gaming environments are perfect for cyber espionage and HUMINT activities, but another aspect that could not be ignored is the possible use of console for cyber-attacks, researchers at ReVuln security firm presented at Black Hat Europe 2013 how to convert local bugs and features in remotely exploitable security vulnerabilities by using the popular EA Origin 3 platform.
Which is the position of the Intelligence agencies?
"All GCHQ's work is carried out in accordance with a strict legal and policy framework which ensures that its activities are authorized, necessary and proportionate, and there is rigorous oversight, including from the secretary of state, the interception and intelligence services commissioners and the Intelligence and Security Committee." said a spokesman for GCHQ not confirming the revelations exactly as the NSA.
Initially, both agencies extracted World of Warcraft metadata trying to link "accounts, characters and guilds" to Islamic extremism and arms dealing efforts.
"According to the minutes of a January 2009 meeting, GCHQ's "network gaming exploitation team" had identified engineers, embassy drivers, scientists and other foreign intelligence operatives to be World of Warcraft players — potential targets for recruitment as agents" reported ProPublica.
The interest in game platforms is also motivated by the possible use of video games for propaganda, the Western intelligence agencies believe that some games may lead to the Islamic doctrine and influence young players fueling hatred against the West.
Snowden has leaked documents that demonstrate gaming platforms are just another option to the US Intelligence and its allies, it must be also considered that the gaming industry is invading also other technologies like mobile and social networking. The exploitation of gaming offers to the NSA the possibility to spy on every environment that runs a game.
Some documents recently spread by The Guardian revealed that the NSA and GCHQ have been developing capabilities to take advantage of security flaws in mobile apps, in particular of the wildly popular games like Angry Birds that transmit users' private information across the internet, according to top secret documents.
"The data pouring onto communication networks from the new generation of iPhone and Android apps ranges from phone model and screen size to personal details such as age, gender and location. Some apps, the documents state, can share users' most sensitive information such as sexual orientation – and one app recorded in the material even sends specific sexual preferences such as whether or not the user may be a swinger.Many smartphone owners will be unaware of the full extent this information is being shared across the internet, and even the most sophisticated would be unlikely to realise that all of it is available for the spy agencies to collect." States The Guardian.
Dozens of classified documents detailed the efforts to piggyback on this commercial data collection for intelligence purposes, once again confirming their strategic importance for the intelligence.
How the NSA tries to compromise Tor anonymity? The Tor Stinks documents
What is the last bastion for anonymity online?
The anonymizing networks you will reply me, Tor network and I2P are the most popular and it is obvious that National Security Agency is spending a great effort to shed light on this dark area of the web.
The demonstration of the effort spent by the NSA is reported in a Top-secret presentation leaked by Edward Snowden that reveals the existence of a project codenamed Tor Stinks leaked. Tor Stinks is a project for the development of techniques to overwhelm Tor Anonymity with manual analysis.
Recently a series of events have completely changed the perception of anonymity over the Tor network, last year groups of researchers demonstrated the possibility to track users also the popular network exploiting a technique dubbed Traffic Correlation attack.
Another serious blow to the anonymity of Tor network was made of the possibility to exploit security flaw within the browser used for the navigation. Law enforcement was able to discover the Tor user's identity exploiting a flaw in the Firefox browser, in the last month Tor network has lost a couple of its most popular entities, Freedom Hosting service and SilkRoad illegal marketplace, both were in fact shut down by the FBI, circumstances that suggested U.S. Authorities have found a way to track criminals (or have simply decided to apply it) even if protected by the Tor anonymity.
In the document leaked by Edward Snowden titled 'Tor Stinks' the NSA admits to being able de-anonymize a small fraction of Tor users manually.
"We will never be able to de-anonymize all Tor users all the time' but 'with manual analysis we can de-anonymize a very small fraction of Tor users'"
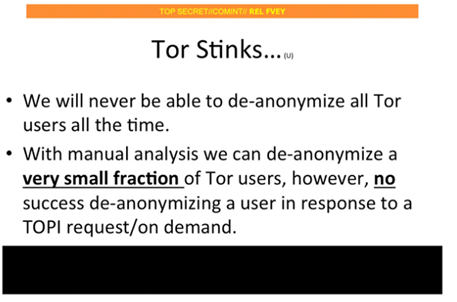
Figure 8 - NSA Tor Stinks slide
The document also reveals that NSA was working to degrade the user experience to dissuade people from using the Tor browser.

Figure 9 – NSA Tor Stinks slide
The NSA strategy relies on the following principles to unhinge Tor anonymity.
- Infiltrate Tor network running its Tor nodes. Both the NSA and GCHQ run Tor nodes to track traffic back to a specific user, the method is based on the circuit reconstruction from the knowledge of the 'entry, relay and exit' nodes between the user and the destination website.

- Exploiting zero-day vulnerability of Firefox browser bundled with Tor, with this technique NSA was able to get the user's IP address. In this way the FBI arrested the owner of Freedom Hosting service provider accused of aiding and abetting child pornography.
- NSA also uses web cookies to track Tor user widely, the technique is effective also for Tor Browser. The cookies are used to analyze the user's experience on the Internet, the intelligence agency owned or controlled a series of website that was able to read last stored cookies from the browser on the victim's machine. With this technique the agency collects user's data, including the IP address. Of course expert users can avoid this type of control in numerous ways, for example, using a dedicated browser for exclusive Tor navigation, using only the official preconfigured Tor bundle or properly managing the cookies stored on their machine. Unfortunately the surveillance methods appeared effective for a huge quantity of individuals. I always suggest using a virtual machine with a live OS for protecting your Tor anonymity, cache and cookies in this way will be lost once the machine is shut down. Documents leaked by Snowden show that the NSA is using online advertisements i.e. Google Ads to make their tracking sites popular on the internet.
It must be specified that despite the great effort of the NSA, it is still not able to compromise the Tor anonymity for the entire network. NSA considers the adoption of Quantum Computing a possible weapon to degrade Tor Access as reported in the following slide.
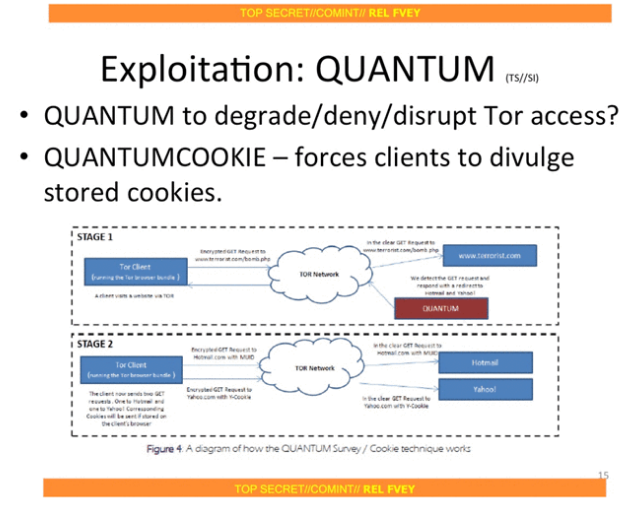
Figure 10 - NSA Slide Tor Stinks
NSA unprepared for "insider attack"
The documents leaked by Snowden revealed that the NSA have developed capabilities to infiltrate every technology in the IT scenario, but ironically the Agency has failed to implement security countermeasures to identify and prevent an attack from insiders. An insider attack is a nightmare for security experts, the attackers in fact have a deep knowledge of IT infrastructures and practices adopted by internal personnel, but there are a series of security measured that could help the identification of suspect behavior.
Analyzing the specific case, Snowden had access to documents located in different geographic areas, transferring them within the internal network, but considering that he has stolen more than 1.7 million confidential files from the NSA archives many questions come to mind.
How is it possible that traffic generated by Snowden was never intercepted raising the suspicions of internal IT administrators?
Snowden has probably made various researches to identify documents of interest, and surely he has needed to provide his credentials to access to secret documents, but in this case how is it possible that so numerous requests were undetected.
The first thought that came to mind is that Snowden has leaked the document over a long period of time, making a small amount of transfer for each request, and it is likely that the whistleblower has used also different identity to access to the documents, for example colleagues' passwords.
The worrying news it that according internal investigation Snowden has leaked the secret NSA' documents using a web crawler software designed to search, index and backup a website.
The New York Times reports Snowden has used a common and inexpensive web crawler to "scrape" the NSA's networks, the media agency received the revelation from the Intelligence officials investigating on the case. Another disturbing revelation regarding the discovery is that Snowden has continued to gather internal documents even after he was briefly challenged by agency officials.
Snowden used a simple web crawler application to scan the network and scrape data out of our systems .
"We do not believe this was an individual sitting at a machine and downloading this much material in sequence," [ The process was ]"quite automated." the official said.
A recent report published by The Federal Government's Track Record provided a scaring picture on cybersecurity for US Government entities, and the circumstance seems to confirm it. Wrong habits, unpatched systems, failure of the fundamentals of cyber security, such as avoiding exposing declassified documents and transcribe password nearly systems used by internal staff, are very common.
The NSA declined to comment the news published by The New York Time, it is a mystery why the presence of a web crawler in the highly classified network of NSA was not detected. Another strange circumstance is the absence of monitoring on the access to internal documents, a similar behavior could be also achieved also by a malware intentionally injected in the internal system, but in this case it would have been impossible to detect its presence with a behavioral analysis.
"Agency officials insist that if Mr. Snowden had been working from N.S.A. headquarters at Fort Meade, Md., which was equipped with monitors designed to detect when a huge volume of data was being accessed and downloaded, he almost certainly would have been caught. But because he worked at an agency outpost that had not yet been upgraded with modern security measures, his copying of what the agency's newly appointed No. 2 officer, Rick Ledgett, recently called "the keys to the kingdom" raised few alarms."
"When inserted with Mr. Snowden's passwords, the web crawler became especially powerful. Investigators determined he probably had also made use of the passwords of some colleagues or supervisors." reports the NYT.
The head of the Defense Intelligence Agency, Lt. Gen. Michael T. Flynn, reported to lawmakers that Mr. Snowden's "disclosures could tip off adversaries to American military tactics and operations", for this reason the US Government is spending a great effort and huge investments to restore a secure situation.
"Everything that he touched, we assume that he took," [including details of how the military tracks terrorists, of enemies' vulnerabilities and of American defenses against improvised explosive devices] "We assume the worst case." said General Flynn
I consider really interesting the comment of Richard Bejtlich, chief security strategist at FireEye, skeptical about the internal supervisory measures.
"Once you are inside the assumption is that you are supposed to be there, like in most organizations," "But that doesn't explain why they weren't more vigilant about excessive activity in the system."
How is it possible that the lonely Snowden had access to secret documents from NSA archives? Why does the NSA engage a so huge quantity of external consultant giving them secret documentation?
It is clear that something was wrong in the chain of custody of those documents, many experts believe that Snowden received the supports of insiders, other believe that the young man user social engineering methods and easy tools to gather information, including colleagues passwords.
How he could leak the documents without any help by colleagues?
New disarming information was reported in an unclassified NSA memorandum disclosed by the NBC News, Snowden allegedly managed to access classified documentation by stealing one of his coworker's passwords. The claim isn't new, in November the Reuters agency already announced the involvement of other coworkers, probably persuaded to give up passwords. It was reported that 20-25 workers who shared their passwords had been identified, questioned, and removed from their assignments, but the NSA has never revealed their identities, while Snowden has always denied the involvement of colleagues.

Figure 11 - NSA memorandum
"Unbeknownst to the civilian, Mr. Snowden was able to capture the password, allowing him even greater access to classified information."states the NSA memorandum.
The unclassified NSA memorandum reports the presence of three actors in the operations, one NSA's civilian employee, an active duty member of the US Military and a contractor, they may have aided Snowden. The NSA's civilian employee has resigned recently, he has admitted that he allowed Snowden to use his digital certificate to access classified information from NSANet, but he was not aware of Mr. Snowden's intentions. The civilian coworker sharing his PKI certificate and allowing Snowden to steal the password has advantaged the whistleblower, as reported in the memorandum he "failed to comply with security obligations,".
The other two actors are currently under investigation and they have been forbidden access to the NSA facilities. Snowden has requested civilian NSA employees and coworkers to enter the password "onto Snowden's computer terminal," it is not clear how he was able to capture it, it is likely he has used a keylogger or simply "shoulder surfed" the secret codes.
Standing to the NSA memo human factor was exploited to carry out the most extended information leakage to an intelligence agency.
The unique certainty is that NSA failed to detect Snowden's "insider attack"
Conclusions
Recently it has been suggested to offer amnesty to prevent Snowden disclose other documents, it's hard to think which are the other technologies still not included in the reports published by the whistleblower.
It is my opinion that the Agency is also working for the development of technologies to compromise Internet of Things and similar effort was spent to hack drones and satellites … probably soon we will read something on that, let's stay tuned!
References
http://www.nytimes.com/2014/02/09/us/snowden-used-low-cost-tool-to-best-nsa.html?_r=0
http://securityaffairs.co/wordpress/21997/intelligence/us-government-entities-cybersecurity.html
http://www.theguardian.com/world/interactive/2013/oct/04/tor-stinks-nsa-presentation-document
http://securityaffairs.co/wordpress/18397/hacking/tor-anonymity-tor-stinks.html
http://www.theguardian.com/world/2014/jan/27/nsa-gchq-smartphone-app-angry-birds-personal-data
http://www.revuln.com/files/ReVuln_EA_Origin_Insecurity.pdf
http://www.theguardian.com/world/the-nsa-files
https://nsa-observer.laquadrature.net/
http://www.nbcnews.com/news/investigations/exclusive-snowden-swiped-password-nsa-coworker-n29006
http://securityaffairs.co/wordpress/20953/intelligence/quantum-computer-nsa.html
http://msnbcmedia.msn.com/i/MSNBC/Sections/NEWS/nsa-snowden.pdf