ISIL, Terrorism and Technology: A Dangerous Mix
Introduction
I was watching the Homeland series on TV when I received the news of the dramatic events in Paris. The introduction to this latest episode was explaining that modern terrorists have new weapons in their arsenal – keyboards.
Terrorist organizations are increasing their cyber capabilities. They make great use of technology for propaganda, to establish covert communication channels, to gather intelligence on the targets, to hit the computer systems of the adversary, and cause damage.
The Paris attacks have shocked the world. A group of ruthless terrorists belonging to the ISIL killed defenseless people.
The Paris attacks demonstrate that ISIS has a high-level logistical organization. They coordinated such terrorist attacks, avoiding detection by intelligence, despite the level of alert raised by the attack in the Sinai and the tragedy of the Charlie Hebdo.
The war is overwhelmingly coming into our homes and the intelligence experts fear that this is just the beginning. ISIL is showing to the world the importance of the media effect on the targeted population.
Images of the attacks are everywhere on the Internet. The message to the unfaithful West has arrived like a strong punch in the stomach. We all have in mind the images of the numerous massacres managed by the ISIS army, we all have seen the executioners of the ISIL that threatens us brandishing a dagger.
For the first time in the history, a terrorist organization is able to organize such effective propaganda. Media are masterfully handled by the terrorists; they are able to launch against any government PSYOPS that heavily relies on the use of social networks, instant messaging apps, gaming platforms and forums hidden in the darknet.
For the first time, a terrorist group calls itself the state and declares war on other governments; its expansionist policy considers the fifth element of warfare, the cyber space, a strategic territory to conquer.
The fight against the ISIL needs incredible effort in term of intelligence, and monitoring of the Internet is crucial to prevent other terrorist attacks.
In June, the Europol announced the creation of a new team that aims to find key figures in propaganda campaigns managed by the ISIL members, the intent is to identify recruiters of foreign fighters and infiltrate their communication channels. The propaganda machine organized by the ISIL worries the intelligence agencies. It generates something like 100,000 daily tweets, and it is effective in recruiting foreign fighters and online sympathizers to support the terrorist organization.
"Who is it reaching out to young people, in particular, by social media, to get them to come, in the first place? It's very difficult because of the dynamic nature of social media." Rob Wainwright, Europol's director, told to the newspaper the Guardian
The Europol is already working closely with social media companies, to identify accounts that are being used for the propaganda.
Wainwright explained that the new unit aim is to "identify the ringleaders online."
The United Kingdom is one of the most affected countries by the terrorist propaganda, and there was reported several cases of young people leaving their home to join Isis (In Iraq or Syria) – men to fight in battle, women marry Isis terrorists.
Deep in the Dark Web
The dark web is a privileged environment on the Internet for cyber terrorists. Darknets allow them to organize propaganda campaigns and stay hidden. The Dark Web also hosts several black markets where it is quite easy to buy illegal product and services. Weapons and forged documents are goods of great interest to terrorists.
Recently the British law enforcement and intelligence agencies, including the GCHQ and the National Crime Agency (NCA), have created a new unit, the JOC, which will specifically address the cyber-crime.
The JOC will be initially focused on tackling online child sexual exploitation, but experts believe that the recent escalation of events will force the unit to join the forces against the ISIL online.
A number of coordinated attacks like the ones occurred in Paris need a significant effort in communicating among members, which remained hidden from the intelligence agencies despite the authorities rake the web constantly looking any evidence of a possible and imminent terrorist attack.
Authorities are monitoring in every instant the communications, even messages exchanged over the Internet and probably among ISIS members crowding the Deep Web.
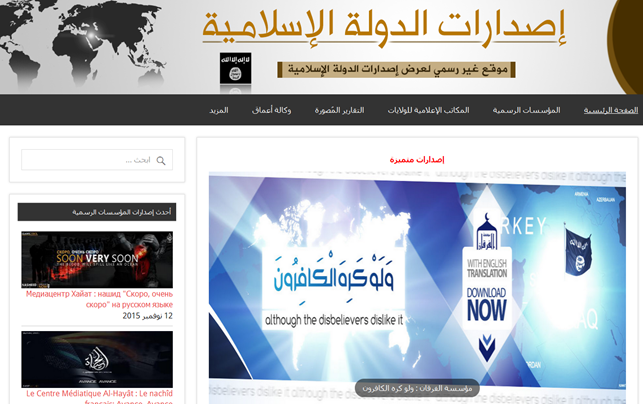
Figure 1 - ISIS Propaganda Hub discovered by Scot Terban (aka @krypt3ia) in the Dark Web
A few hours after the Paris attacks, Daesh (al-dowla al-islaamiyya fii-il-i'raaq wa-ash-shaam, a.k.a. ISIS/ISIL) launched his propaganda on the Dark Web.
A new propaganda center was discovered by the popular researcher Scot Terban (aka @krypt3ia), who reported it to the colleagues at Salted HASH. The researcher had found on the Dark Web a website containing propaganda messages translated in English, Turkish, and Russian. It includes the recent statement issued by Daesh claiming credit for the Paris attacks.
Scot Terban has discovered the propaganda website after he noticed a post that explained the need to create a new hub for propaganda in response to the numerous operations against other websites used by the ISIL that were seized by the law enforcement, or targeted by the Anonymous collective. The terrorists decided to move on the Darknet to make the Daesh more resilient to takeover attempts.
"Terban came across the new Al-Hayat hub while performing jihadi research over the weekend," states Salted HASH. "In a post on the Shamikh forum (a known jihadi bulletin board), someone posted the new address and instructions for reaching it."
The new website includes a collection of propaganda video and images produced by Al-Hayat Media Center, the media division of the Daesh. The Al-Hayat Media Center is used by the sympathizers of the ISIL to spread content glorifying the jihad against the infidel West, including poems for mujahids and songs (Nasheeds).
Terban has mirrored the entire website to analyze it and publish more details in the coming days. The site is a mine of information for the intelligence; it contains data from various sources, including standard bulletin boards used by the ISIS terrorists.
"The site mirrors many of the other standard bulletin boards that the jihadi's have had over the years replete with videos and sections in all languages. Given that this site has popped up today in the Darknet just post the attacks in Paris, one has to assume that an all out media blitz is spinning up by Al-Hayat to capitalize on the situation," Terban wrote.
The new Daesh hub demonstrates that even if the ISIS is aware of the Internet surveillance of western government, it considers the use of technology as strategic.
The problem of communicating and the new technologies
What are the channels exploited by the members of the ISIL to spread their messages from the Middle East to the far Europe and in the US?
The experts have no doubts. Social media platforms, instant messaging apps, forums hidden in the deep web, and also gaming consoles are all targets for exploitation.
Yes, gaming consoles! It has been newly revealed that the ISIS terrorists involved in the Paris attacks may have used the popular Sony PlayStation 4 gaming console as the platform to exchange messages.
During a raid in nearby Brussels, the agents have discovered evidence that terrorists were using at least one PlayStation 4 console. The Belgian federal home affairs minister Jan Jambon explained that the PS4 is used by ISIS members for their communications.
This circumstance highlights that terrorists have a significant mastery of the technology and know the mechanisms of Internet surveillance adopted by the authorities.
Despite the effort of the intelligence agencies in monitoring communications over gaming consoles, the ISIS members were aware of the difficulties to conduct a large-scale surveillance on the PlayStation 4 channels.
"The thing that keeps me awake at night is the guy behind his computer, looking for messages from [the Islamic State]and other hate preachers," Jambon said last Friday, according to Brussels weekly,the Bulletin. "PlayStation 4 is even more difficult to keep track of than WhatsApp."
Figure 2 - Jan Jambon, Belgian Prime Minister
The PlayStation's IP-based voice systems are difficult to monitor and terrorists could send messages to each other within PlayStation games without typing a word.
At the time of this writing there is no certainty, the investigators have no clear idea about a possible use of the Sony Play Station 4, anyway, as explained by the Belgian Minister it could be a serious error underestimate every technological option available to the terrorist organizations.
The possibility that terrorist groups could exploit gaming consoles for internal communications was already analyzed in the past by intelligence agencies. There is the proof that the NSA and the British GCHQ have infiltrated the virtual world of online games considered as an attractive environment for cyber terrorists and hackers.
The Guardian published documents leaked by Snowden on the surveillance program conducted by the intelligence agencies that have operated in virtual worlds and gaming communities to gather intelligence and recruit informants.
Last documents published by the Guardian titled "Exploiting Terrorist Use of Games & Virtual Environments" are dated 2008 and remarked the necessity to monitor online gaming communities describing them as a "target-rich communications network" where intelligence targets could "hide in plain sight".
The documents just provide a warning on the possible abuse of online gaming communities, but don't contain an indication on real case discovered by the intelligence agencies.
The Secret Services have infiltrated the principal online game communities including Second Life to monitor users' habits and snoop their communications, NSA and GCHQ have created human avatars to explore virtual reality and prevent terrorist initiatives.
The principal problems in conducting such kind of activities is that at that time there was no automatic system to monitor such kind of communication, what about today abilities of the Western Intelligence?
Paris attacks must lead us to reflect seriously on the subject, the ISIS has skills and resources and it is not surprising that its members can exploit gaming console as communication channels.
While investigators are analyzing the possible abuse of gaming platform for communications, the researcher Scot Terban observed that the new Daesh hub appeared on the darkweb also suggests ISIL members and sympathizer the use of Telegram, a secret encrypted messaging platform that is largely adopted by the terrorists.
Telegram is "A Secret Chat is a one-on-one chat wherein all messages are encrypted with a key held only by the chat's participants." It is an essential tool for all the individuals that need to protect their communication from prying eyes.
Telegram's Channels used by the terrorists allow them to reach tens of thousands followers instantly.
"As you can see from the picture here they have also included their (semi) new encrypted chat/messaging program of choice (Telegram) which they used in their claim on the Paris attacks. There are several accounts as well as other new ones I have seen popping up on jihadi Twitter accounts as well as Facebook. The rub in this Telegram service is that it is hosted and run out of Russia and so far, the company and he Russian government have not been very forthcoming in attempts to get information from them on the da'esh accounts." states Terban.

Figura 3 - Telegram App used by ISIL
The "Snowden effect"
Riding the emotions of the Paris attacks, several military officials and intelligence experts explained that the revelations made by the popular whistleblower Edward Snowden has provided useful information to the terrorists about surveillance activities run by the intelligence agencies belonging to the Five Eyes.
Clearly, such speculation is completely unfounded and wrong, as explained by the popular journalist Glenn Greenwald in a post on The Intercept.
"One key premise here seems to be that prior to the Snowden reporting, The Terrorists helpfully and stupidly used telephones and unencrypted emails to plot, so Western governments were able to track their plotting and disrupt at least large-scale attacks. That would come as a massive surprise to the victims of the attacks of 2002 in Bali, 2004 in Madrid, 2005 in London, 2008 in Mumbai, and April 2013 at the Boston Marathon. How did the multiple perpetrators of those well-coordinated attacks — all of which were carried out prior to Snowden's June 2013 revelations — hide their communications from detection?" states Greenwald.
The reality is that the Snowden's revelations only confirmed the existence of a complex surveillance machine the existence of which was already known to the terrorists of the ISIL and al Qaeda.
The terrorists were clearly aware of the monitoring of communications operated by numerous governments, they always avoided telephones and the use of the email encryption was already popular before Snowden disclosed the top-secret documents.
The media reported the use of encryption by terrorists for many years prior to the Snowden's case; they reported that members of al Qaeda were using sophisticated encryption to avoid surveillance activities.
"As but one of countless examples, here's a USA Today article from February 2001 — more than 12 years before anyone knew the name "Edward Snowden" — warning that al Qaeda was able to "outfox law enforcement" by hiding its communications behind sophisticated internet encryption" added Greenwald.
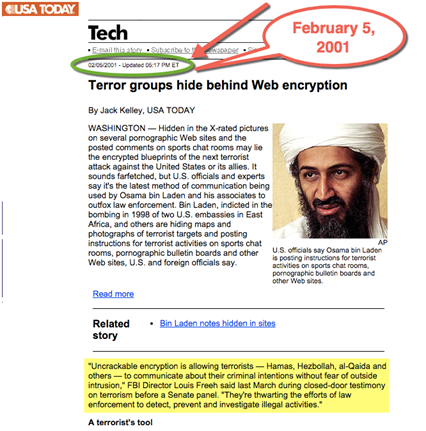
Figure 4 - Media reporting usage of encryption years before Snowden
The intelligence agencies were aware of the use of steganography by groups of terrorists to exchange messages online.
We can add dozens of samples. It is deeply wrong blaming Snowden to have provided useful information to the ISIL, this is a story that someone is trying to manipulate for different purposes.
The ISIL cyber capabilities
A few days ago the popular cyber security expert Mikko Hyppönen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could attack critical infrastructure and cause serious damages. The expert explained that the ISIS is probably the first group of terrorist that has hacking capabilities to manage a major attack against a government infrastructure, and the situation is getting worse because this group is gaining greater awareness of the effectiveness of an offensive launched by the cyberspace.
"The Islamic State is the first extremist group that has a credible offensive cyber capability," said F-Secure Chief Research Officer Hyppönen, speaking last week at the Wall Street Journal's WSJDLive conference in Laguna Beach, Calif. "Clearly, this situation isn't getting better. It's getting worse."
Hyppönen confirmed that a cyber-attack could be arranged with a limited amount of resources, compared to a conventional terrorist attack, and let me add that its preparation is difficult to trace.
Hyppönen added that a cyber-attack could be launched from everywhere. The hackers are moving from Europe to Syria, where they could launch attacks that shut down critical infrastructure in every place of the world.
The terrorists can target SCADA systems used in several western infrastructure, let think of Siemens systems, for example, that control over 50 percent of the world's factory equipment.
"Extremists might be willing to do an attack like that," Hyppönen said.
Last month, the US authorities confirmed that hackers belonging to the Islamic State (ISIL) are trying to hack American electrical power companies.
The news was reported by law enforcement officials during a conference of American energy firms that were discussing Homeland Security. The ISIL has the cyber capabilities to run cyber-attacks against US critical infrastructure and the US intelligence is aware of the risks.
In May 2015, a Pro-ISIL hacking crew dubbed Cyber Caliphate threatened 'Electronic War' on US and Europe.
"ISIL is beginning to perpetrate cyberattacks," explained Caitlin Durkovich, assistant secretary for infrastructure protection at the Department of Homeland Security.
Investigators revealed to CNNMoney that Islamic State have run a series of cyber-attacks that have been unsuccessful. They avoided providing further information on the attacks and neither cited evidence of specific incidents.
The experts described the attacks as not particularly sophisticated; however, they represent a serious threat to the Homeland Security. ISIL hackers use to buy hacking tools in the black markets, there is no evidence that they are developing their own "cyber weapons."
"Strong intent. Thankfully, low capability," said John Riggi, a section chief at the FBI's cyber division. "But the concern is that they'll buy that capability."
Mikko Hyppönen admitted that the threat is very serious. This is an asymmetric war and the enemy can hit us in any moment, in any place, from anywhere. This summer a U.S. drone strike killed the jihadist hacker Junaid Hussain in Syria. The man was actively recruiting ISIS sympathizers and the US intelligence believes that the jihadist hacker is behind a number of cyber-attacks, including the one that hit the Central Command websites and its Twitter accounts.
Anyway Junaid Hussain has been just one of the hackers of the CyberCaliphate, the hacking group considered the cyber army of the ISIS.
In conclusion, it is clear that technology is assuming a crucial importance for the operations of the ISIL and other terrorist organizations. We cannot underestimate the cyber capabilities of the ISIS and its members. Unfortunately, their abilities will continue to grow over the time, and as speculated by part of the intelligence community, there is also the concrete risk that groups of cyber mercenaries could support their operation transferring to the ISIS members a precious knowledge.
References
http://securityaffairs.co/wordpress/41992/intelligence/paris-attacks-playstation-4.html
http://securityaffairs.co/wordpress/42022/intelligence/paris-attacks-darkweb-hub.html
http://securityaffairs.co/wordpress/38006/cyber-crime/europol-against-isis.html
http://securityaffairs.co/wordpress/41438/intelligence/isis-offensive-cyber-capability.html
http://money.cnn.com/2015/10/15/technology/isis-energy-grid/index.html
http://securityaffairs.co/wordpress/41883/cyber-crime/gchq-nca-joc.html
http://www.xpats.com/brussels-weakest-link-europes-fight-against-terrorism











