Flame: The Never Ending Story
It is not possible to talk about cyber warfare and cyber weapons without mentioning the famous Stuxnet virus and the series of state-sponsored malware developed in the same period, using a common development platform with different purposes. Stuxnet is considered the first cyber weapon detected, and since then, many tools of cyber espionage have been used by governments to steal sensitive information and intellectual property of foreign government, agencies, and enterprises. The first malware developed with this intent by a government appeared to be Duqu, an agent designed by the same authors of Stuxnet and realized using the same development framework named "Tilded platform".
Last May, the Iranian Computer Emergency Response Team (MAHER) detected a new targeted malware which hit the country. It has been named Flame (also known as Flamer or Skywiper) due the name of its main attack module. In the same hours, CrySyS Lab and Kaspersky Lab published news regarding the new malware that has been detected and has hit mainly Windows systems of the Middle East area, specifically Iran. Coincidence or planned communication strategy?
Hands-on threat intel training
Hands-on threat intel training
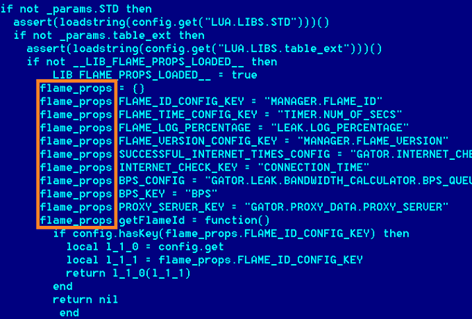
Figure - Flame Source Code
The discovery was made by Iranian scientists during the investigation on the malicious agents Stuxnet and Duqu, and what surprised them was the capability of the malware to dynamically change its behavior, including receiving and installing specific modules designed to address specific targets.
But what really surprised the world wide security community was the capability of Flame to be undetectable by all the principal antivirus software for a long period of time. This very anomalous circumstance induced conjecture of the collaboration of the principal security firms to avoid the malware's detection to advantage its spread. The prompt response of the major security firms and the certainty that the malware is dated at least to 2010, would give cause to think that the companies were aware of the project Flame and have been silent in agreements with Western governments.
Some months before the discovery of Flame, Western countries had decided to suspend the supply of antivirus systems to Iran for penalty, forcing the country to develop its own antivirus. How is it possible that the Iranian Computer Emergency Response Team anticipated the world wide community and was first to discover the agent?
The malware infected mainly Windows platforms running Windows XP, Vista and Windows 7, gathering information from the victims in different modes such as sniffing network traffic, taking screenshots, recording audio conversations and intercepting the keyboard. Once collected, the information was sent by the agent to the command-and-control servers.
Flame is considered a complex malware realized with the primary intent to create a comprehensive cyber espionage tool kit. The following list gives some features of the malware listed in the official announcement of MAHER center:
- Distribution via removable medias
- Distribution through local networks
- Network sniffing, detecting network resources and collecting lists of vulnerable passwords
- Scanning the disk of infected systems, looking for specific extensions and contents
- Creating series of user's screen captures when some specific processes or windows are active
- Using the infected system's attached microphone to record the environment sounds
- Transferring saved data to control servers
- Using more than 10 domains as C&C servers
- Establishment of secure connection with C&C servers through SSH and HTTPS protocols
- Bypassing tens of known antiviruses, anti malware and other security software
- Capable of infecting Windows XP, Vista, and 7 operating systems
- Infecting large scale local networks
The Iranian Government sustains that the malware is a new cyber weapon due to its complexity level and propagation methods observed. It didn't exclude that a mass data loss in Iran was related to the attack of the same malware.
The nature of the systems targeted and the geographic distribution of the malware, the Middle East, combined with the high level of sophistication, according the opinion of many security experts, are clear clues that the malicious software was developed by a foreign state that intents to hit a specific country in that region of the globe. Kaspersky Team defined Flame as a sophisticated attack toolkit which condenses the characteristics of a backdoor, a Trojan, and a worm able to spread itself within a local network and on removable media.
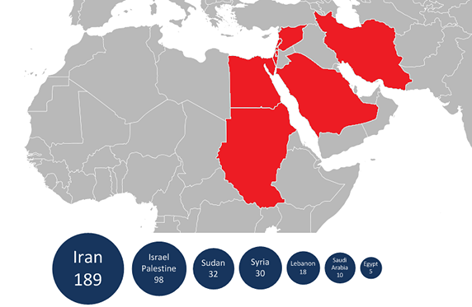
Figure - Geographic Distribution of Flame malware according Kaspersky Lab
The first investigations demonstrated that Flame was active since 2010, exactly the same period of Stuxnet, and according the opinion of the analysts at Kaspersky Labs, both projects were produced by two separate, skilled teams of professionals that in the design phase of the malware have had the opportunity to collaborate.
Despite Kaspersky team sustaining that Flame is an advanced cyber espionage tool, there is a strange particular that raised doubts on the capability of Flame to remain undetected for a so long time: its size is anomalous for a stealth espionage toolkit. The total dimension of the malware is almost 20 MB, a considerable size motivated by the presence of many different libraries and of a LUA virtual machine. This last feature is another distinctive element that represents an innovation and makes me believe that the developers behind the agents are professionals.
The choice of the scripting language is mainly motivated by the following factors:
- Complete portability of the source code and simple integration with C and C++ languages.
- It is a dynamic programming language.
- The LUA virtual machine is extremely compact, less than 200Kb.
LUA is a cross-platform scripting language with "extensible semantics" and its usage is uncommon for malware development. Flame is composed by several modules written using the scripting language and interfacing it with subroutines and libraries compiled from C++.
Who is behind Flame?
Though difficult to say exactly who has developed the malware, for sure it's a state-sponsored project and it has been developed with the specific intent to attack countries in Middle East exactly in same way of Stuxnet.
To better understand Flame, let's analyze the story of the famous Stuxnet, finding the correlations between the two malware.
The worldwide security community suggested the US as the authors of the Stuxnet, which the US government has consistently denied, leading suspicions to the work of Israel intelligence.
According an article published by The New York Times, adapted from journalist David Sanger's forthcoming book, Confront and Conceal: Obama's Secret Wars and Surprising Use of American Power, both the US and Israeli governments developed and deployed Stuxnet.
The planning of the deadly cyber weapon started under the administration of George W. Bush as part of a military operation named "Olympic Games", but the Obama administration has been putting more energy into the offensive program.
The response of the US Government to this article's revelation on the "Olympic Games" secret project has been an internal investigation on the leaks of classified information on the development, instead of an official denial of the claims.
The Kaspersky team demonstrated a strong correlation between Stuxnet and Flame, also highlighting deep differences between the malicious codes.
First of all, Stuxnet is considered the first cyber weapon designed to destroy the Iranian nuclear program, infecting Scada systems inside nuclear plants. Meanwhile, Flame is a sophisticated tool for cyber espionage.
Stuxnet appears to be designed using the famous Tilded platform, but Flame and the products of Tilded framework, such as Duqu, are completely different because they are based on different architectures. Flame never used system drivers, while Stuxnet and Duqu's main method of loading modules for execution is via a kernel driver.
The presence of the US behind the development of Flame is not surprising. Cyber espionage is one of the main activities covered by every cyber strategy, through which it tries to silently steal confidential information, technologies and intellectual property. The ability to infiltrate enemy networks, stealing classified information, represents a major advantage for those who lead the offensive.
Stuxnet was created in the first half of the 2009, when, according to Kaspersky researchers, the Flame platform was already in existence. One of the most sensational discoveries is that a Stuxnet instance dated 2009 used a module built on the Flame platform. This module was specifically developed to operate with Stuxnet malware and was removed in the successive versions. The Flame module found in Stuxnet exploited a 0-day vulnerability enabling an escalation of privileges, presumably exploiting MS09-025.
Kaspersky expert Roel Schouwenberg noted that no Flame components have been used in more advanced versions of Stuxnet:
"Flame was used as some sort of a kick-starter to get the Stuxnet project going," he stated. "As soon as the Stuxnet team had their code ready, they went their way."
In the successive version of Stuxnet, a new module has been found to have substituted it and to empower the propagation of the agent exploiting the vulnerability MS10-046 instead of the "old" autorun.inf.
Starting from 2009, the evolution of the two projects has proceeded independently. This circumstance supports the hypothesis that behind Stuxnet and Flame there were two distinct groups of development named by Kaspersky "Team F" (Flame) and "Team D" (Tilded).
Kaspersky CEO Eugene Kaspersky declared:
"there were two different teams working in collaboration."
Resuming the development team, authors of the malware have started operations since 2007-2008 at the latest. The presence of the component from the Flame platform in Stuxnet demonstrates the collaboration between the groups, but since 2010, the platforms have been developing independently from each other.
The only similitude observed between instances dated after 2010 is that both teams have been exploiting the same vulnerabilities.

Figure - Relationship of Stuxnet, Duqu, Flame and Gauss, according Kaspersky
It's not yet clear why two different groups of experts working for governments have developed two distinct agents with common features. The following are some possible explanations:
- Creators of Stuxnet removed Flame components to avoid being discovered in case of failure of the cyber attack against the Iranian nuclear program.
- The teams are working for different states that have joined the effort to speed-up the creation process of a cyber weapon. Let's recall that many security experts have alerted the international community regarding the risk that Iran could create its nuclear arsenal within a couple of years, making the time factor determinant.
Flame today … and the news on an alleged agent still in the wild
After months of investigation conducted by the Kaspersky team in collaboration with Symantec, ITU-IMPACT and CERT-Bund/BSI, the researcher Kaspersky analyst Dmitry Bestuzhev has cracked the password protecting the Flame command and control server, obtaining access to the malware control panel. The C&C servers discovered were owned by a European company with data centers in another European Union country.
The revelations were sensational as predicted. The forensic analysis of the command & control servers revealed an additional three unidentified pieces of malware under the control of the attackers, but the alarming discovery is related to an alleged agent still in the wild.
According to the last investigation, the first use of Flame, initially thought to have begun in 2010, appeared to be in 2006.
Going deep in the analysis, the group of security analysts get a server image which was an OpenVZ file-system container, an operating system-level virtualization technology based on the Linux kernel and operating system.
OpenVZ allows a physical server to run multiple isolated operating system instances, but it made forensic analysis difficult.
The study demonstrated that the authors of malware have intentionally tried to cover tracks of their operations by providing fake clues to disorient the analysts. For example, the C&C servers present an elementary structure and look and feel to give the impression that it had been prepared by script kiddies, equipped with a simple and anomalous botnet control panel.
A very interesting feature of the botnet is the way the C&C instructs the bots that don't receive the command directly by the console, but attackers uploaded specially crafted tar.gz archives containing scripts that were processed by the server.
The server extracted script from the archive looking for *.news and *.ad files located in specific directories. The priority and target client ID were stored in the filename uploaded to a C&C server with following convention:
<random_number>_<user_type>_<user_id>_<priority>.<file extension>
Going deep in the code analysis, the researchers discovered that C&C servers were able to use a different communication protocol, probably used to "converse" with different clients. The protocols discovered are respectively dedicated to four different types of malware: SP, SPE, FL and IP, where FL stands for Flame, and according to the code analyzed, the remaining clients are similar agents.
The protocols are:
- OldProtocol
- OldProtocolE
- SignupProtocol
- RedProtocol (mentioned but not implemented)
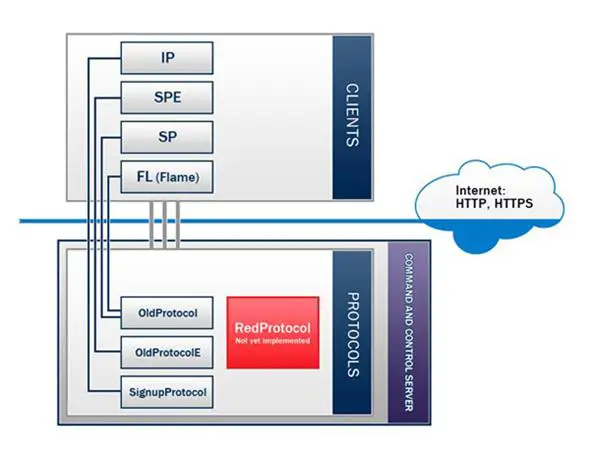
Figure - Clients and Protocols relations found in this C&C server - Kaspersky
Redirecting the Botnet traffic to a "sinkhole" to oversee traffic from infected machines and prevent further distribution of malware and scams, the researchers have distinguished two different streams of data respectively related to Flame and to another, the SPE malware client demonstrating that it is operating in the wild.
Data on the traffic directed to the C&C servers, starting on March 25th, during a week, revealed 5377 unique IP addresses connected to the server located in Europe. 3700 connections were originated from Iran and around 1280 from the Sudan. Less than 100 connections were made from other countries such as United States, Germany and India. A region targeted and number of infections related to specific countries gives indication of a state-sponsored intelligence operation conducted against Iran and Sudan.
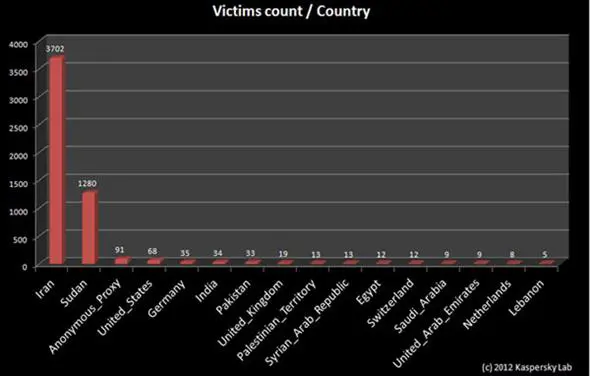
Figure - Client and protocol relations found in this C&C servers - Kaspersky
One of the most valuable traces left by the four developers in the scripts were their nicknames and internal timestamps, the earliest of which is dated December 3, 2006.
Singularly, one of the developers has worked on a majority of the files, demonstrating great experience. Maybe the developer was the team leader, according the report. The study states:
"He coded some very smart patches and implemented complex logics; in addition, he seems to be a master of encryption algorithms. We think [the developer] was most likely a team lead."
Other interesting info discovered from the analysis of the C&C servers are the last modification date that is May 18th and the presence of an automated script used to delete log files and disable the logging function. The researchers have found a shred tool also used by the Duqu team was used to wipe information and also some scripts that downloaded new data and removed old data every 30 minutes.
Ongoing investigation … new sensational revelations on miniFlame
On October 14th Kaspersky Lab has released a new report reporting the results of further investigation conducted on the Command and Control servers and on traffic directed to them. As anticipated the security researchers have detected two different streams of data respectively related to Flame and to another, the SPE malware client demonstrating that it is operating in the wild.
Kaspersky's blog post refers to the SPE agent naming it the "miniFlame", that is the agent uncovered during the investigation and highlighting that it is a smaller version of Flame module, probably because it was developed before.
Don't let the name fool you; "miniFlame" malware is a fully functional espionage module designed for cyber espionage purposes and implemented as an independent module that is able to operate on infected machines, without the main Flame components acting as a backdoor and allowing remote control by the attackers.
Another feature discovered in miniFlame is its ability to operate with Gauss malware, demonstrating a common origin of offensive against the Middle East region.
This singular revelation is related to the use of the C&C server; some of them were used exclusively to control the SPE, others to control both SPE and Flame agents. The experts noted that the diffusion of miniFlame was limited with respect to Gauss and Flame, maybe because it has been used as a surgical attack tool on very specific targets that have been considered strategic by the attackers.
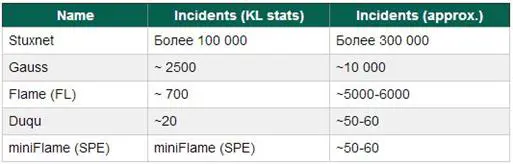
Figure - Malware diffusion data
SPE does not have a clear geographical bias. The researchers found the usage of different modification against different countries such as Lebanon, Iran, Kuwait, Palestine and Qatar. Looking at Sinkhole statistics of miniFlame, it is possible to note that between 28th of May 2012 and September 30th, the servers counted around 14,000 connections in total from about 90 different IPs. Two main locations of victims are Lebanon and Iran.
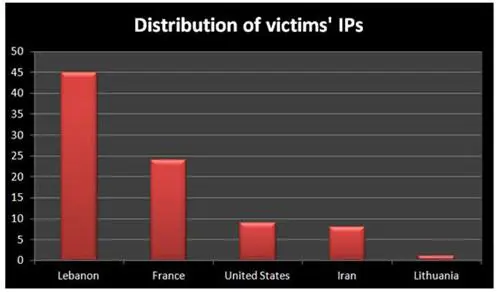
Figure - miniFlame geographic diffusion
The researchers discovered ten commands used for malware running and to instruct the agent on cyber espionage operations.
What's about the other malware not yet identified? Researchers believe that SP could be an older version of miniFlame, while IP agent is still under investigation to try to discover its purpose. The paternity of the massive cyber espionage campaign is also still a mystery. The Kaspersky report on the topic states:
"With Flame, Gauss and miniFlame, we have probably only scratched the surface of the massive cyber-spy operations ongoing in the Middle East. Their true, full purpose remains obscure and the identity of the victims and attackers remain unknown."
Can be Flame considered a cyber weapon?
Flame is not considered at first glance to be a cyber weapon. It doesn't fit into the following definition, despite being a state-sponsored project:
A cyber weapon is "any appliance, device or any set of computer instructions designed to unlawfully damage a computer or telecommunications system having the nature of critical infrastructure, causing huge damage, and to offend the person through cyberspace".
It is a cyber espionage malware, but experts could ignore its modular structure that makes possible the use of its components for offensive purposes, simply loading a module specifically developed to attack critical infrastructures. Kaspersky researcher Schouwenberg said he suspected Flame may be capable of deleting data and attacking industrial control systems. Of course there isn't evidence right now, but it is a feasible scenario.
The expert of Symantec Security firm declared on the argument:
"The modular nature of this malware suggests that a group of developers have created it with the goal of maintaining the project over a long period of time; very likely along with a different set of individuals using the malware. The architecture being employed by W32.Flamer allows the authors to change functionality and behavior within one component without having to rework or even know about the other modules being used by the malware controllers. Changes can be introduced as upgrades to functionality, fixes, or simply to evade security products."
The Kaspersky team proposing the result of its investigation on miniFlame malware used the words "cyber-weapon factory", evidencing that these agent could also act for offensive purposes by simply loading a specific module. The authors of Flame have, according the results of the analysis, created dozens of different agents, and many of them are probably yet to be discovered.
The result of analysis proposed by Kaspersky experts revealed that the projects started earlier than 2010 contrary to when believed, highlighting the great complexity of the encryption used. The information gathered by malware in fact are encrypted on the server and only the attackers can read it.
Concluding, Flame was just a part of a state-sponsored project; it's quite possible that similar projects are still ongoing and what is singular in my opinion is their ability to remain hidden during a long period, a characteristic that makes these agents very dangerous.
Flame represents a milestone in the concept of cyber warfare. The security firms have been able to analyze the detected instances, but the modular structure led them to believe that it is considerable a work in progress with unpredictable evolution.
References
http://www.securelist.com/en/blog/208193522/The_Flame_Questions_and_Answers
http://www.csoonline.com/article/718070/flame-fallout-microsoft-encryption-deadline-looms-tuesday
http://www.securelist.com/en/blog/763/miniFlame_aka_SPE_Elvis_and_his_friends
Hands-on threat intel training
Hands-on threat intel training
Pierluigi Paganini is co-author of the newly-published e-book, The Deep Dark Web, available through Amazon and here.









