Equation Group APT and TAO NSA: Two Hacking Arsenals Too Similar
The Equation Group
In February 2014, the team of experts from Kaspersky Lab announced the discovery of a hacking group operating since 2001 that managed numerous cyber espionage campaigns targeted against companies in practically every industry by leveraging on sophisticated zero-day malware.
The researchers dubbed the hacking team the Equation Group because of their attitude in the use of encryption algorithms and obfuscation methods, and for the sophisticated methods used in their campaigns.
Hands-on threat intel training
The researchers revealed that hackers behind the Equation Group show significant hacking capabilities combined with sophisticated and complex tactics, techniques, and procedures. The experts have collected a huge quantity of information related to the hacking tools in the arsenal of the Equation Group. These tools have required a considerable effort to their development, a fact that suggests the involvement of a government.
The most disconcerting discovery made by the investigators is related to the alleged link between the Equation Group and the team of coders behind the Stuxnet and Flame malware.
Based on the information related to the numerous cyber espionage campaigns analyzed by the experts at Kaspersky over the years, the community of security experts hypothesized that the National Security Agency (NSA) could be linked to the Equation Group, though Kaspersky never pointed the finger at the US intelligence.
"There are solid links indicating that the Equation Group has interacted with other powerful groups, such as the Stuxnet and Flame operators—generally from a position of superiority," states the report released by Kaspersky during the company's Security Analyst Summit in Cancun, Mexico.
The researchers from Kaspersky explained that the Equation Group is a "threat actor that surpasses anything known in terms of complexity and sophistication of techniques." Its activity was defined by the experts as the most sophisticated cyber espionage campaign ever seen.
The Equation Group also had access to zero-days before they were used by operators behind Stuxnet and Flame campaigns. According to the researchers at Kaspersky Lab, on seven exploits used by the Equation Group in their malware and exploit kit, at least four of them were used as zero-days. For example, the experts mentioned a malicious code dubbed Fanny, which was used by the Equation Group in 2008 when it exploited two zero-days, later introduced into the Stuxnet variants detected in June 2009 and March 2010. This is proof that the hacking team had access to previously unknown flaws before any other group of hackers.
"At least four of these were used as zero-days by the EQUATION group. In addition to these, we observed the use of unknown exploits, possibly zero-day, against Firefox 17, as used in the TOR Browser. An interesting case is the use of CVE-2013-3918, which was originally used by the APTgroup behind the 2009 Aurora attack. The EQUATION Group captured their exploit and repurposed it to target government users in Afghanistan."
The Equation Group infected thousands, "even tens of thousands," of victims worldwide. Researchers from Kaspersky have collected evidence of attacks in 42 countries.
Researchers from Kaspersky have documented nearly 500 infections. Victims were mainly located in Iran, Russia, Pakistan, Afghanistan, India and Syria. The self-destruct mechanism designed for the malicious codes used by the Equation Group fuels suspicions that the cases uncovered by the experts are just a small percentage of the total infections.
The group hit government organizations and private companies belonging to the following categories:
- Governments and diplomatic institutions
- Telecommunication
- Aerospace
- Energy
- Nuclear research
- Oil and gas
- Military
- Nanotechnology
- Islamic activists and scholars
- Mass media
- Transportation
- Financial institutions
- Companies developing cryptographic technologies
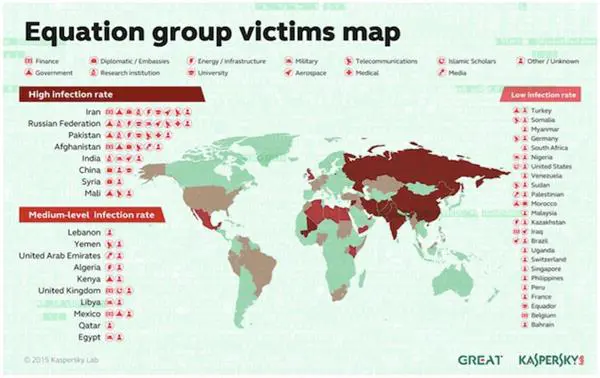
Figure 1 - The Equation Group (Kaspersky Lab)
The Equation Group relies also on physical attacks to compromise systems of its victims. According to the report published by Kaspersky, the group of hackers sent victims a malware-infected CD in the mail and intercepted a Cisco Systems router in the mail to implant trojans directly in the firmware of the device. The attack technique is known as "interdiction" and consists of the interception of shipped goods and replacement with trojanized versions.
"The attacks that use physical media (CD-ROMs) are particularly interesting because they indicate the use of a technique known as 'interdiction', where the attackers intercept shipped goods and replace them with trojanized versions," continues the report.
Inside the Arsenal of the Equation Group
The experts discovered that the Equation Group relies on multiple attack techniques to compromise victims' computers, including:
- Self-replicating (worm) code – Fanny
- Physical media, CD-ROMs
- USB sticks + exploits
- Web-based exploits
The hackers behind the Equation Group used several attack tools and malware, some of which are exclusive to the group. Below the list of malware used exclusively by the Equation Group:
- EQUATIONDRUG – A very complex attack platform used by the group on its victims. It supports a module plugin system, which can be dynamically uploaded and unloaded by the attackers.
- DOUBLEFANTASY – A validator-style Trojan designed to confirm the target is the intended one. If the target is confirmed, they get upgraded to a more sophisticated platform such as EQUATIONDRUG or GRAYFISH.
- EQUESTRE – Same as EQUATIONDRUG.
- TRIPLEFANTASY – Full-featured backdoor sometimes used in tandem with GRAYFISH. Looks like an upgrade of DOUBLEFANTASY, and is possibly a more recent validator-style plugin.
- GRAYFISH – The most sophisticated attack platform from the EQUATION group. It resides completely in the registry, relying on a bootkit to gain execution at OS startup.
- FANNY – A worm created in 2008 and used to gather information about targets in the Middle East and Asia. Some victims appear to have been upgraded first to DoubleFantasy, and then to the EQUATIONDRUG system. Fanny used exploits for two zero-day vulnerabilities which were later discovered with Stuxnet.
- EQUATIONLASER – An early implant from the EQUATION group, used around 2001-2004. Compatible with Windows 95/98, and created sometime between DOUBLEFANTASY and EQUATIONDRUG.
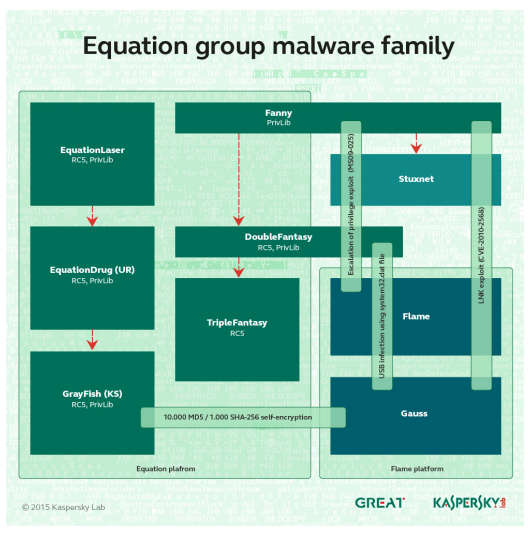
Figure 2 - Equation Group malware family (Kaspersky Lab)
Security expert Claudio Guarnieri, one of the most active malware researchers involved in the analysis of malicious code described in the document leaked by Edward Snowden, is sure that hacking tools used by the Equation Group are the same used by the NSA.
It is the case of a very sophisticated keylogger used by the Equation Group called "Grok", which was also mentioned in one of the documents leaked by Edward Snowden. Grok is considered a keylogging component of the UNITEDRAKE malware, which experts linked to Regin malware.
"The codename GROK appears in several documents published by Der Spiegel, where 'a keylogger' is mentioned. Our analysis indicates EQUATIONGROUP's GROK plugin is indeed a keylogger on steroids that can perform many other functions," reads the report.
"Grok" is referred to for the first time in a post published by The Intercept titled, "How the NSA Plans to Infect 'Millions' of Computers with Malware." The article introduces an NSA-developed keylogger called Grok.
"One implant, codenamed UNITEDRAKE, can be used with a variety of "plug-ins" that enable the agency to gain total control of an infected computer," states The Intercept. "GROK is used to log keystrokes."
Another powerful tool in the arsenal of the Equation Group is GRAYFISH, considered by experts to be the most sophisticated attack platform of the hacking crew. GRAYFISH relies on a bootkit to gain persistence on the victim's machine. It is able to infect almost all versions of Windows, including 8. GRAYFISH also steals files and stores them in its own encrypted Virtual File System (VFS). GRAYFISH was designed to masquerade its presence and make its detection and analysis difficult.
If an error happens during startup, the entire GrayFish platform self-destructs to avoid leaving traces on the host machine. Among the various features implemented by GrayFish, the malware encrypted its payload with a 1,000-iteration hash of the target machine's unique NTFS object ID.
"The first stage GRAYFISH loader computes the SHA-256 hash of the NTFS of system folder (%Windows% or %System%) Object_ID one thousand times. The result is used as an AES decryption key for the next stage. This is somewhat similar to Gauss, which computed the MD5 hash over the name of its target folder 10,000 times and used the result as the decryption key."
By using this technique, the only way for researchers to access the final payload is to analyze the raw disk image for each individual infected machine. The technique is similar to the one observed by the experts for the popular Gauss, which shared strong technical similarities with both Stuxnet and Flame, and for this reason was associated with the NSA.
"We do not know if the people behind Duqu switched to Gauss at that time but we are quite sure they are related: Gauss is related to Flame, Flame is related to Stuxnet, Stuxnet is related to Duqu. Hence, Gauss is related to Duqu," declared the researchers at Kaspersky Lab in 2012.
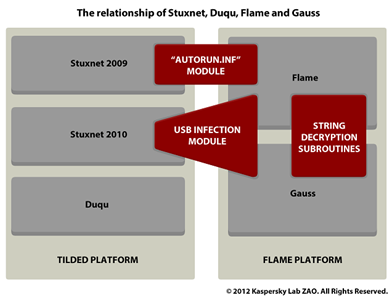
Figure 3 - Flame vs Tilded Platform (Kaspersky Lab 2012)
As mentioned before, the Fanny worm is another hacking tool that captured the attentions of the researchers. It used two zero-day vulnerabilities and a third flaw that were all exploited to hit the Iranian nuclear programs. Fanny exploited the flaw before Stuxnet did. Both tools were used to compromise "air gapped" networks.
Fanny used a unique command and control that set up a hidden storage section on infected USB sticks. When the Fanny malware detected there wasn't an Internet connection, it would acquire system information. When the stick was connected to a machine that has access to the Internet, it sent the information back to the command and control server, which would return instructions on how compromise the air-gapped systems.
"If the attackers wanted to run commands on the air-gapped networks, they could save these commands in the hidden area of the USB stick. When the stick was plugged into the air-gapped computer, Fanny recognized the commands and executed them."
The Fanny worm was used by the Equation Group to map air-gapped networks and to execute commands to those isolated systems.
There are other similarities between the tools used by the NSA's Tailored Access Operations unit and the Equation Group. For example, researchers at Kaspersky recognized the following tools as part of the arsenal of the mysterious hacking team:
- STRAITACID
- STRAITSHOOTER
The names of the two tools have a similarity (spelling "strait") with one of the most powerful malware designed by the NSA TAO, STRAITBIZARRE. STRAITBIZARRE is a multiplatform malware that also works on mobile devices.
Many tools in the TAO catalog that were leaked in 2013 present similar features to the hacking tool Kaspersky identified in the Equation Group, including codenames UNITEDRAKE, STRAITBAZZARE, VALIDATOR and SLICKERVICAR.
According to Wired Magazine, researchers at Kaspersky have found a possible link in the code of a tool used by the Equation Group that could refer the NSA Tao tool code named UNITEDRAKE (United Rake).
"Kaspersky did find 'UR' in EquationDrug, suggesting a possible connection to UNITEDRAKE (United Rake). Kaspersky also found other codenames in the components that aren't in the NSA catalog but share the same naming conventions—they include SKYHOOKCHOW, STEALTHFIGHTER, DRINKPARSLEY, STRAITACID, LUTEUSOBSTOS, STRAITSHOOTER, and DESERTWINTER," states Wired Magazine.
The STRAITBIZARRE malware was designed to implement a common interface for a large variety of software and hardware implants (i.e. COTTONMOUTH, DROPOUTJEEP) used by US intelligence to exfiltrate data from targeted networks. A document leaked by Snowden explains that machines infected by STRAITBIZARRE can be turned into disposable "Shooter" nodes, part of the QUANTUM infrastructure.
According to the report published by Kaspersky, the Equation Group also used physical media and CD-ROMs to compromise systems of its targets.
Researchers from Kaspersky revealed that in 2009 the Equation Group targeted participants at an international scientific conference that was held in Houston. The hackers targeted leading scientists from several countries by sending them a CD-ROM containing a presentation with the best photos from the event. The hackers included in the CD-ROM a powerful nation-state malware that was activating silently in the background.
The CD-ROM was crafted with two zero-day exploits. The main loader was able to drop into the victim machine the Equation Group implant installer codenamed DoubleFantasy.
The DoubleFantasy implant collects information on the target and sends them back to the control server, which serves a sophisticated Trojan platform, like EquationDrug or GrayFish, in response.
A few days after the publication of the report by Kaspersky, Reuters reporter Joseph Menn confirmed in a post that the NSA was using for its operations a malicious agent that was able to compromise hard-drive firmware. The reporter cited two former government employees as the source of the information.
"A former NSA employee told Reuters that Kaspersky's analysis was correct, and that people still in the intelligence agency valued these spying programs as highly as Stuxnet. Another former intelligence operative confirmed that the NSA had developed the prized technique of concealing spyware in hard drives, but said he did not know which spy efforts relied on it."
The researchers at Kaspersky were able to recover two modules that allowed the group to reprogram hard drive firmware of more than a dozen of the popular hard disk drive brands, including Western Digital, Maxtor, Samsung, IBM, Micron, Toshiba, and Seagate. The most disconcerting aspect of the discovery is that the malware was able to survive disk formatting and OS reinstallation.
"It means that we are practically blind, and cannot detect hard drives that have been infected by this malware," said Costin Raiu, Director of the Global Research and Analysis Team at Kaspersky Lab. "It can resurrect itself forever."
The last similarities between the Equation Group and NSA Tao hacking unit is the exploitation of "unknown exploits, possibly zero-day" against Firefox 17, which is the browser used by Tor clients. Why is the Equation Group interested in the de-anonymization of Tor users?
The intent to track users in Tor networks appears out of the scope of criminal gangs, and led investigators to believe that the group operated for a government.
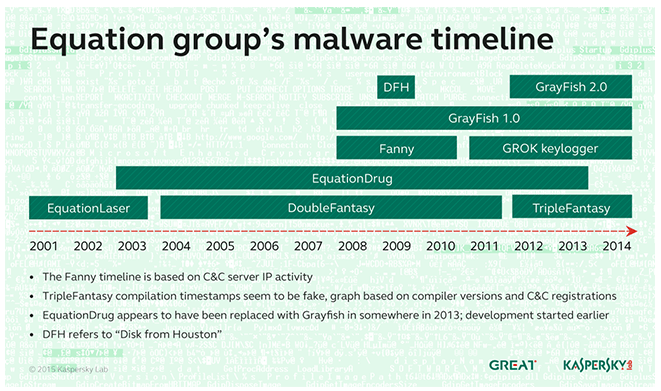
Figure 4 - Equation Group malware timeline (Kaspersky Report)
Conclusion
Researchers at Kaspersky and security experts have no doubt the hacking tools used by the Equation Group required time and money for their development, a circumstance that led them to believe in the involvement of a government with significant cyber capabilities. The evidences collected by the experts suggest that members of the group have a strict relationship with author of Stuxnet and Duqu.
"The discovery of the Equation Group is significant because this omnipotent cyber espionage entity managed to stay under the radar for almost 15 years, if not more," Raiu said. "Their incredible skills and high tech abilities, such as infecting hard drive firmware on a dozen different brands, are unique across all the actors we have seen and second to none. As we discover more and more advanced threat actors, we understand just how little we know. It also makes us reflect about how many other things remain hidden or unknown."
The NSA released the following comment on the report published by Kaspersky Lab:
"We are aware of the recently released report. We are not going to comment publicly on any allegations that the report raises, or discuss any details. On January 17, 2014, the President gave a detailed address about our signals intelligence activities, and he also issued Presidential Policy Directive 28 (PPD-28). As we have affirmed publicly many times, we continue to abide by the commitments made in the President's speech and PPD-28. The US Government calls on our intelligence agencies to protect the United States, its citizens, and its allies from a wide array of serious threats – including terrorist plots from al-Qaeda, ISIL, and others; the proliferation of weapons of mass destruction; foreign aggression against ourselves and our allies; and international criminal organizations."
References
http://securityaffairs.co/wordpress/33637/cyber-crime/the-equation-group-atp.html
http://25zbkz3k00wn2tp5092n6di7b5k.wpengine.netdna-cdn.com/files/2015/02/Equation_group_questions_and_answers.pdf
http://securelist.com/blog/research/68787/a-fanny-equation-i-am-your-father-stuxnet/
https://nex.sx/blog/2015-01-27-everything-we-know-of-nsa-and-five-eyes-malware.html
http://securelist.com/blog/research/68750/equation-the-death-star-of-malware-galaxy/
https://firstlook.org/theintercept/2014/03/12/nsa-plans-infect-millions-computers-malware/
http://www.reuters.com/article/2015/02/16/us-usa-cyberspying-idUSKBN0LK1QV20150216
http://arstechnica.com/security/2015/02/how-omnipotent-hackers-tied-to-the-nsa-hid-for-14-years-and-were-found-at-last/
http://www.wired.com/2015/02/kapersky-discovers-equation-group/
http://securityaffairs.co/wordpress/8037/intelligence/gauss-evidence-of-ongoing-cyber-war-and-cyber-espionage-campaigns.html
http://www.kaspersky.com/about/news/virus/2015/equation-group-the-crown-creator-of-cyber-espionage
http://www.forbes.com/sites/thomasbrewster/2015/02/16/nsa-equation-cyber-tool-treasure-chest/
http://www.forbes.com/sites/thomasbrewster/2015/02/16/nsa-equation-cyber-tool-treasure-chest/










