Diving in the deep web
“Deep Web”, also known as “hidden web”, is a term that evokes the unknown, a mysterious place in the cyber space populated by criminals and hackers that is not accessible for ordinary people, but is it true?
What is the Deep Web, how do you access to its resources and what is possible to find in its networks? In this post, I’ll try to provide an overview on the principal concepts related tothe Deep Web, providing a guide on how to orient within a plethora of hidden services
The Deep Web is a collection on information resources located on the World Wide Web not indexed by search engines, contrary to what one might think, its extension is much higher than that of ordinary web, raw estimationsaccredit it around 500 times larger.
How is it possible? How do search engines work?
Search engines use software called "crawlers" to scan web content, these applications browses the World Wide Web in a methodicaland automated manner and typically create a copy of all the visited pages for later analysis and indexing procedure. The crawlers are not able to scan the entire web but in many cases the fail to retrieve content accessible from the web. The following are the principal categories of Deep Web resources not reached by these software’s:
- Dynamic content: dynamic pages which are returned in response to a submitted query or accessed only through a form, especially if open-domain input elements (such as text fields) are used; such fields are hard to navigate without domain knowledge.
- Unlinked content: pages which are not linked to by other pages, which may prevent web crawling programs from accessing the content. This content is referred to as pages without backlinks (or inlinks).
- Private Web: sites that require registration and login (password-protected resources).
- Contextual Web: pages with content varying for different access contexts (e.g., ranges of client IP addresses or previous navigation sequence).
- Limited access content: sites that limit access to their pages in a technical way (e.g., using the Robots Exclusion Standard, CAPTCHAs, or no-cache Pragma HTTP headers which prohibit search engines from browsing them and creating cached copies).
- Scripted content: pages that are only accessible through links produced by JavaScript as well as content dynamically downloaded from Web servers via Flash or Ajax solutions.
- Non-HTML/text content: textual content encoded in multimedia (image or video) files or specific file formats not handled by search engines.
- Text content using the Gopher protocol and files hosted on FTP that are not indexed by most search engines. Engines such as Google do not index pages outside of HTTP or HTTPS.
The consequence of this data are shocking.During its web experience, a user could access only to a small portion of the overall network, and instead the “Dark” portion is accessed by a limited audience for deeply different purposes, from cybercrime to hacktivism.
Security experts use describe the Deep Web with the metaphor of the “The Web Sea” provided by the founder of BrightPlanet, Mike Bergman, that compared searching on the Internet today to dragging a net across the surface of the ocean: a great deal may be caught in the net, but there is a wealth of information that is deep and therefore missed. Search engines are able to analyze only the surface of the sea without accessing information hidden in its depths. The comparison is apt and evokes the depths, in which due to the absence of light, comparableto the leak of indexing procedures, make navigation very hard.

The principal characteristic of the Deep Web is the anonymity.Its use is mainly motivated by the user’s need to hide their identity online; this exigency is shared by various categories of individuals, not necessary cyber criminals. Of course, total anonymity attracts criminal industries that are migrating various activities in the hidden web.In the recent months, the number of underground markets that sell any kind of odd, from drugs to weapons has grown exponentially.
The Deep Web and the service hidden in its resources are also largely used by governments, in particular by intelligence agencies and militaryto exchange documents secretlyand by journalists to bypass censorship established by dictatorial regimes to suppress internal dissidents.
Anonymizing networks - The Tor network
How are individuals tracked on the web and how is it possible tomake a user anonymous online?
In the Internet every resource is identified by an IP address that could be masqueradedusing anonymizing services or surfing throughanonymizing networks such as I2P and Tor network. The fundamental concepts on which these networks are based arethe layered routing and the adoption of encryption algorithms to protect information during the transmission.
Without doubts, the most popular anonymizing network is Tor, The onion router, a system managedby the US Naval Research Laboratory from 2004 to 2005 to enable online anonymity;successively the project was supported by the Electronic Frontier Foundation.
Using the Tor client software, auser is able to surf in Tor Network, which I strongly suggest to navigate inside the deep web using Tails OS distribution which is bootable OS that doesn't leavetrace on the user’s machine.
https://tails.boum.org/
The popular Tor Bundle is equipped with its own portable Firefox versionfor anonymous navigation.Anyways, it is strongly suggested that usersmake check of installed/in use plugins; in many the commercial version in fact common plugins could expose user’s identity also on anonymizing networks.
Once plunged into the depths of Deep Web, it is easy to get lost, which is why it is essential to keep in mind which are considered the references that can help navigation. Recall that in the Deep Web there aren’t search engines like Google, the navigation is quite different from ordinary web and every research appears more complex due the absence of indexing of the contents.Typically, users proceed in the navigation jumping from list of navigable URL proposed by more or less known sites, collection of Wikis and BBS-like sites have the main purpose to aggregate links, categorizing them in more suitable groups of consulting.
Another difference that users immediately note is the format of web site URLs.Instead of classic extensions (e.g. .com, .gov) the domains in the Deep Web generally end with the .onion suffix, .onion-URLs are used to identify hidden services. Addresses in the .onion pseudo-TLD are 16-character alpha-semi-numeric hashes which are automatically generated based on a public key when the hidden service is configured. These 16-character hashes can be made up of any letter in the alphabet, and decimal digits beginning with 2 and ending with 7, thus representing an 80-bit number in base32.
jhiwjjlqpyawmpjx.onion
This .onion-URL isn’t used only to refer the hidden service, it also offers service authentication. Only one specific hidden service is associated to this identifier and no one can forge or spoof it because an 80 bit number actually is a part of the hash of the public key of the hidden service and the public key is strongly related to its private key.Now that reader has understood what the meaning for this strange sequence of characters representative of onion addressed, let provide few interesting info that could allow him to move first step in the obscurity of the Deep Web.
The Wikies
Wikies are most precious resources in the Deep Web, especially for those individuals that have no fixed references for their researches, they are collections of URLs related to various topics arranged in categories to improve the consultation.Most popular, but not the only one is the Hidden Wiki, it is a mine of information and links to allow wide researched in the Deep Web.
http://kpvz7ki2v5agwt35.onion/wiki/index.php/Main_Page
The wiki offer an impressive quantity of URLs related to raw contents and discussion pages.The web site appears very friendly to visitors that once located the section of interest, representative of a specific thematic area, could browse to the links listed.
Users could easily find content related to hacking, hacktivism, market places, commercial services and forums and a specific session forservices arranged for geographic areas.
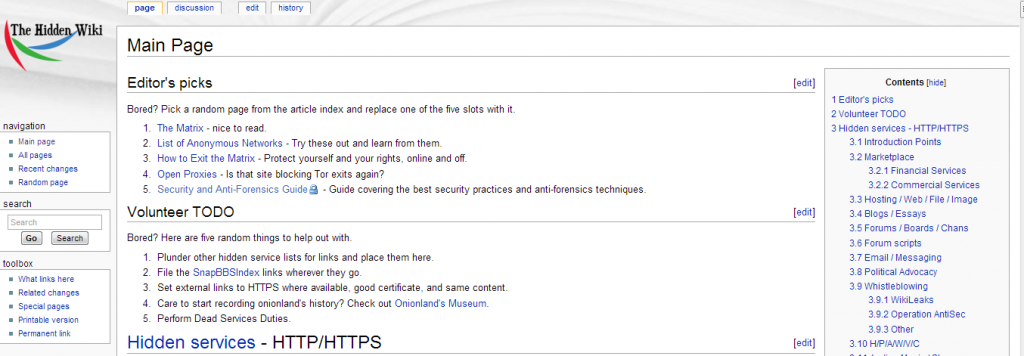
Figure 1 - Hidden Wiki
TorDir is another precious collection of onion links arranged in various categories such as Business, Hacking and Related and Social. Also, this site is very easy to consult; users can share links registering and adding new ones, the website also proposes a search engine to help users to find resources in the TorNetwork.
http://dppmfxaacucguzpc.onion/
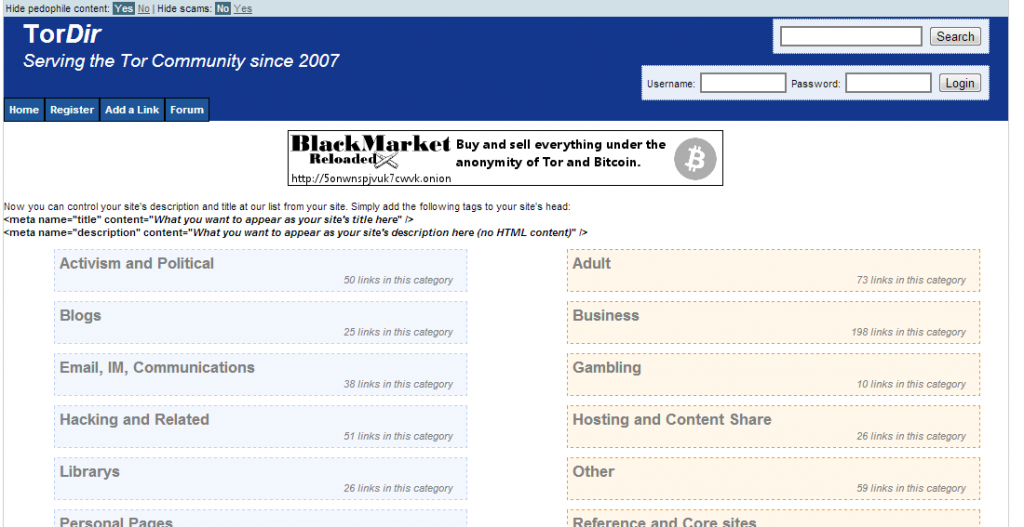
Figure 2 - TorDir
Another precious resource is“TorLinks | .onion Link List”, an interesting collection of links organized in categories for a very simple consultation.
http://torlinkbgs6aabns.onion/
Search engines
The wiki’s aren’t the unique guides for “Dark” web surfers and inexpert users, many sites offers primitive search engines that allow users to retrieve the URLs related to content to search. One of the most interesting Onion domain list is tor hidden service search Ahmia.fi available onworld wide web at the following address:
https://ahmia.fi/
Figure 3 - Ahmia.fi search engine
Other popular search engines are:
The dark business
Since we now have seen general purposes wikis and search engines, we must recognize that theDeep Web is also full of directories dedicated to specific arguments.I know that readers love to read about crime and the dark side of hidden web, so let me give you same example of web sites related to illegal activities.
The anonymity ensured by Tor Network represents an attractive spot for the crime industry, it create the ideal conditionsfor secure business makingvery difficult to trace sellers and buyers, whatever goods they exchange.
In the deep web, it is practically possible to acquire any kind of illegal product and service, from drugs to weapons, recently great success has been obtained by web sites that propose hacking tools and services and exploits. The prices are very variable, from few hundred dollars to thousand’s of dollars for zero day exploits or complex malware. Despite the huge offers, people commonly think that Deep Web is criminal markets where the most requested odds are drugs, in effect the precious product is much requested and many web sites were recently born to allow its sale.The operators of these black markets provide to their customers a series of servicesto anonymously sell and acquire illegal products, encouraging the use of virtual currency schema such as Bitcoin that allow instantaneous and not traceabletransactions on which gain commissions.
The most popular dark market is Silk Road, an online marketplace where the majority of products are derived from illegal activities, an autonomous system that advantage the exercise of criminal activities while ensuring the anonymity of transactions and the inability to track down the criminals.
https://silkroadvb5piz3r.onion

Figure 4 - Silk Road
Last year,Carnegie Mellon computer security professor Nicolas Christin published a research on Silk Road and its business model; it seems that the market is able to realize $22 Million in annual sales only related to the drug market. Total revenue made by the sellers has been estimated around USD 1.9 million per month demonstrating how profitable the monetization schema is.The study estimated that operators receive about USD 143,000 per month in commissions.

Figure 5 - Silk Road - Average daily operator commissions
The researchers examined over 24,400 separate items sold on Silk Road noting that it mainly used as drugs market as observable in the following table reporting a list of Top 20 categories of available items.

Figure 6 - Silk Road Top 20 categories of products
In the Deep Web there is a great number of black markets specialized in sale of specific products, in the following table a short list of most famous ones:
Figure 7–GermanWeed
The Deep Web is also very popular in the hacker underground community, many hackers use it regularly to exchange information, opinions and tools with others passionate in the matter.Recently, some forums in the hidden web have also been used to commercialize exploit tools or hacking services (e.g. DDoS attack, botnetrenting).
One of the most famous malwares, based on the Zeus malicious code,is Citadel trojan that is also available in the deep web; security experts have in fact found an excellent customer relationship management (CRM) model implemented by its creators. The authors of malicious code have structured an efficient service for the sale (around $2,500) of the malware and the providing of improvements and customizations for specific needs (e.g. customization to target specific banks or financial institutions or to setup of a cyber-espionage tool) for the trojan through social network platforms that get in touch clients with the creators of the virus.To ensure their anonymity, authors of Citadel implemented a malware-as-service selling model based on a hidden service in theDeep Web.
The phenomenon is not isolated – cybercrime is exploring the possibility of migrating its activities in the Deep Web; the security community is assisting to the consolidation of the black markets that sell various products from drugs to exploits for zero-day vulnerabilities.
Digging in the Tor network, it is possible to found a huge number of hidden services that offer forums and document exchange platforms specifically developed for hackers.
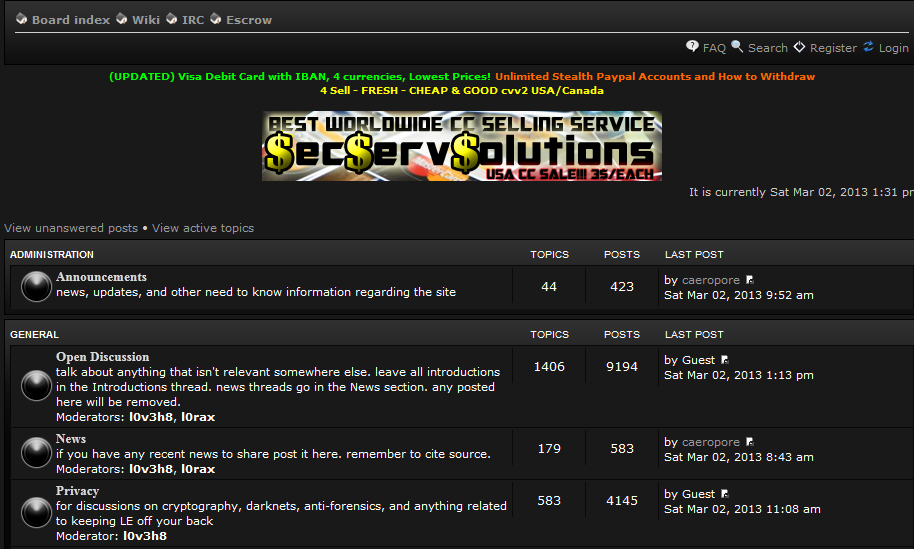
Figure 8 - HackBB Hacking portal
Deep Web … is much more
For obvious reasons, I have introduced the concept of Deep Web and the most attractive topics related, as said in the first part of article, the concept Deep Web evokes in our minds a dark place populated by hackers and cyber criminals.This is true but we cannot ignore that hidden web is also used for many other purposes by different actors such as intelligence agencies, hacktivists and whistleblowers.
Intelligence agencies uses hidden services to provide communication platforms for agents operating in foreign countries that need to elude internet monitoring meanwhile hacktivists use hidden web mainly for propaganda purposes; various are in fact social networks used by community of hackers to organize protest actions.
The deep web is also used by intelligence analysts to study the political situation of foreign countries thanks to the use of powerful analysis tools such as Tor Metrics, a project that aggregates all kinds of interesting data about the Tor network and visualizes them in graphs and reports.
For example, analyzing the number of access to the Tor Network over the time it has been possible to discover how The Ethiopian Telecommunication Corporation, unique telecommunication service provider of the country, has deployed for testing purpose a Deep Packet Inspection (DPI) of all Internet traffic.
Using the metrics, it was possible to identify the introduction of the filtering system as displayed in the following graphs. The deployment of monitoring system is usually associated by repressive politics of central governments that are interest of persecutionof opponents.
Governments are dedicating great attention to the Deep Web and to the opportunity given by its environments to the growth and diffusion of cyber threats, military cyber units are infiltrating it and are using it for both defensive and offensive purposes(in a previousarticle, I wrote about this issue)
“The Deep Web is governments project to operate anonymously, of course this aspect has been also exploited by cyber criminals, hacktivists and normal people that desire to defend their privacy, for this reason institutions and agencies of every countries have promoted project to develop new monitoring systems and at same time they have started a misinformation campaign against the this parallel and hidden world.”
Consider that use of anonymizing networks is not encouraged by governments all over the world, for obvious reasons, because they cannot monitor user’s activities and because they fear the offensives of foreign groups of hackers from the Deep Web.
I always suggest to notbelieve that those whosustain that Deep Web are the reign of the evil because they are trying simply to defend their secrets keeping you away from that place.










