Crimea – The Russian Cyber Strategy to Hit Ukraine
Introduction
The year 2014 started with a diplomatic crisis in Crimes and Ukraine. The tension rose just after the 2014 Ukrainian revolution, in which the government of President Viktor Yanukovych was ousted after a popular revolt in Kiev. In the region there are groups contrary to the protest that desire the integration of Crimea with Russia, and these groups are opposed to others consisting of Crimean Tatars and ethnic Ukrainians which supported the revolution. The deposed president Yanukovych during the days of revolution covertly requested the intervention of the Russian military to stabilize the internal situation of Ukraine.
Hands-on threat intel training
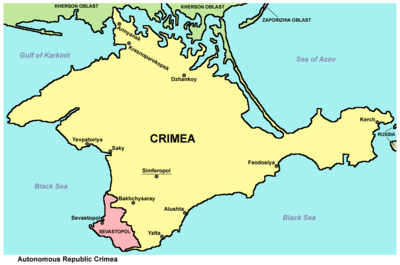
Figure 1 - Map of Crimea
On February 26th, the Russian government moved nearly 150,000 units along the Ukrainian border, officially for a military exercise. In the next days, pro-Russian armed soldiers without insignia seized numerous buildings in Crimea, including the parliament building, two airports, and structures belonging the Ukraine principal telecommunication provider, interrupting services with the rest of Ukraine.

Figure 2 - Russian soldiers seized an airport in Crimea
The Ukrainian government accused Russia of interference in Ukraine's internal affairs and invasion of the country, but Moscow denied these accusations. The Russian militia involved in the Peninsula of Crimea was also reinforced with other resources, including a couple of vessels of the Russian Black Sea Fleet, which violated Ukrainian waters.
After the events precipitated on March 1, the Russian parliament approved President Vladimir Putin's order to use military force in Ukraine.
The Russian Cyber Strategy
The tension between Russia and Crimea has a corresponding conflict in cyber space. Numerous attacks were registering on both sides during the revolution in Kiev, and the cyber offensives have had an escalation after the approval of the Russian parliament for military use in Crimea. The decision of the Russian government has triggered a series of events in cyber space as state-sponsored cyber units, groups of hacktivists, and cyber criminals started their campaigns against the enemies.
Ukraine's mobile phone infrastructure is under attack, according to the declaration of Valentyn Nalivaichenk, the head of Ukraine's SBU security service during a press conference. The official stated that the country is suffering a serious attack in the last few days. The attack against Ukraine's mobile phone infrastructure originated in Crimea and is interfering with the phones of members of the parliament.
"I confirm that an IP-telephonic attack is under way on mobile phones of members of Ukrainian parliament for the second day in a row," declared Valentyn Nalivaichenko, according the Reuters agency.
Ukraine's telecommunications system has come under attack. The attackers used equipment installed within Ukrtelecom networks in the Crimea region under the control of Russian forces. This circumstance has raised tension between the two countries, and although the majority of the Crimean population is pro-Russian, the sabotage is interpreted by the government of Kiev as an intolerable act of war. The equipment is blocking the phones of Nalivaichenko and his deputies.
"At the entrance to (telecoms firm) Ukrtelecom in Crimea, illegally and in violation of all commercial contracts, was installed equipment that blocks my phone as well as the phones of other deputies, regardless of their political affiliation … The security services are now seeking to restore at least the security of communications," according to the security chief. "All state information security systems were unprepared for such a brazen violation of the law," Nalivaichenko said.
The attack is not isolated. Internet connections within the peninsula of Crimea have been severely hampered. Not yet identified militias have seized the offices of telecommunications service provider Ukrtelecom, cutting phone and Internet cables. Militias also set up roadblocks to isolate Crimea from the rest of the Ukraine. Both military operations appear as part of a strategy to isolate the region in case of attack.
Security experts believe that the mission for the Russian military is to isolate the region, and probably for this reason Russian naval vessels were placed in the port at Sevastopol: the units are carrying jamming equipment to block radio communications. Ukrainian naval communications stations around the area of Sevastopol and power lines have been already sabotaged. The Crimean peninsula is suffering numerous denial of service attacks , and Ukrainian telecom provider Ukrtelecom JSC reported that "unknown individuals seized several Crimean communications facilities" last week and that communications between the peninsula and the rest of Ukraine have been degraded as a result of "unknown actions [that] physically damaged fiber optic trunk cable[s]." Other disconcerting news reports that all communication services in Crime have been shut off, including Internet and mobile.
The attacks have taken place also on the Web, as numerous website were already attacked. Two government websites in Crimea were shut down, but it is not clear if they were brought down by foreign hackers or by the same officials of local government.
Other media sources report that the Crimean Peninsula's landline, Internet, and mobile services have been almost entirely shut off. Military experts have no doubt that this is the prelude to a kinetic operation. In particular, Russia adopted the same strategy in 2008 when it isolated Georgia by taking control of government websites and interfering with Internet activities in the country that was without its own Internet exchange point (IXP) and was reliant on foreign governments, including Russia, for nearly 70% of its Internet exchange capacity.
The Ukraine seems to have just one Internet exchange point located in Crimea, so it's quite easy for Russian cyber units to isolate the region.
"Ukraine has a strong and diverse Internet frontier … The roads and railways of Ukraine are densely threaded with tens of thousands of miles of fiberoptic cable, connecting their neighbors to the south and east (including Russia) with European Internet markets. The country has a well-developed set of at least eight regional Internet exchanges, as well as direct connections over diverse physical paths to the major Western European exchanges. At this level of maturity, our model predicts that the chances of a successful single-event Internet shutdown are extremely low," revealed a recent analysis by intelligence company Renesys, which monitors Internet service around the world.
Two Crimean government web portals also went offline, but the cause is still unclear. The attacks also hit Russian entities. The most famous victim is the Russian news agency, Russia Today. Its website was defaced by unknown hackers.
In an information warfare context, the principal targets are critical infrastructures of a country. We must consider that the Russian government dedicates huge investments to improve cyber capabilities and it is possible that in case of an imminent kinetic attack, the government of Moscow will use also cyber weapons to destabilize defensive structures in the area.
Uroburos and the Snake Platform
Recently, researchers at German G Data published an interesting analysis for Uroborun rootkit alleged to be a component of Russian cyber weapons program. Uroburos is considered an advanced rootkit that is active since as far back as 2011. It is used to infect networks belonging to high-level targets, stealing data after setting up rogue P2P networks. It targets both 32-bit and 64-bit Microsoft Windows systems.
German security firm G Data has conducted an interesting study on the malware trying to discover its authors, and its conclusion is that Uroburos is certainly of Russian origin.
What is Uroburos?
"Uroburos is a rootkit, composed of two files, a driver and an encrypted virtual file system. The rootkit is able to take control of an infected machine, execute arbitrary commands and hide system activities. It can steal information (most notably: files) and it is also able to capture network traffic. Its modular structure allows extending it with new features easily, which makes it not only highly sophisticated but also highly flexible and dangerous. Uroburos' driver part is extremely complex and is designed to be very discrete and very difficult to identif," reported G Data analysis.
The Uroborus rootkit presents all the characteristics of a sophisticated design proper for a state-sponsored campaign. It has an unusual complexity, and the modular structure of the malware was certainly designed in Russia, based on the references left by authors in its source code.
Figure 3 - Uroborus malware
The peculiarity of the malware is that it checks for the presence of the USB stick-loving Agent.btz ('Buckshot Yankee') on the victims' computer, a worm that successfully infected US military networks in 2008. If Uroburos finds Agent.btzworm, it does not activate.
"The malicious software, or malware, caught a ride on an everyday thumb drive that allowed it to enter the secret system and begin looking for documents to steal. Then it spread by copying itself onto other thumb drives. Pentagon officials consider the incident, discovered in October 2008, to be the most serious breach of the U.S. military's classified computer systems."
According experts at G Data, Uroburos is a considerable a framework resulting from Intelligence activity. It has surely required a huge investment, and it is likely that malware developers involved in the project are still working on it.
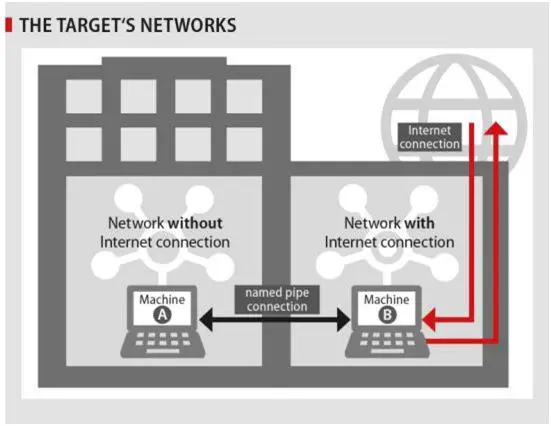
"By commanding one infected machine that has Internet connection, the malware is able to infect further machines within the network, even the ones without Internet connection. It can spy on each and every infected machine and manages to send the exfiltrated information back to the attackers, by relaying this exfiltrated data through infected machines to one machine with an Internet connection."
The Uroburos rootkit was designed to infect networks of huge organizations, even if they have air gapped sub networks. Similar agents are privileged weapons to hit a critical infrastructure in case of attack. The Russian government is known to have invested a lot in the development of cyber weapons and to improve cyber capabilities of its militias.
Just a few day after the disclosure of the Uroburos rootkit, BAE Systems Applied Intelligence firm disclosed a Russian cyber espionage campaign codenamed as SNAKE that remained undetected for a long time, at least eight years.
The attackers behind operation SNAKE penetrated highly secured Windows systems all around the world, but the most interesting revelation is that the Uroburos rootkit recently discovered was just one component of the overall SNAKE campaign.
"The cyber-espionage operation behind the Snake rootkit is well established, a sample compiled in January 2006 indicates that the activity would have begun in at least 2005. It is also sophisticated, using complex techniques for evading host defences and providing the attackers covert communication channels. Toolmarks left behind by the authors 'vlad' & 'gilg', leave tantalizing clues as to the personas behind this," states the report.
The disclosure of the SNAKE campaign confirms the hypothesis made by researchers in G Data. The security community was facing with a large scale campaign organized by Russian entities, and the complexity of the agent suggests the involvement of the Russian government.
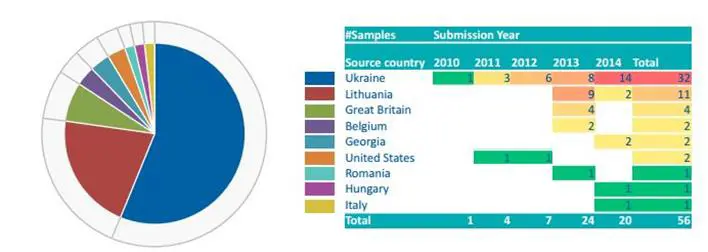
Within the SNAKE campaign the attackers used numerous various pieces of malware. Western intelligence officers have found another spyware, dubbed Turla, used to infect government networks all over the world. The following image demonstrates that Ukrainian entities are most impacted by the diffusion of the malware.
Figure 4 - Malware sample detected (BAE Systems Applied Intelligence)
Researchers linked the malware Turla to the popular cyber espionage campaign Red October, discovered by Kaspersky more than one year ago.
"It is sophisticated malware that's linked to other Russian exploits, uses encryption and targets western governments. It has Russian paw prints all over it," said Jim Lewis, a former U.S. foreign service officer.
The SNAKE campaign adopted sophisticated techniques to infect Windows systems. Bypassing security defenses, it has the ability to hide in the victim's web traffic.
"Hiding a few DNS/HTTP requests among busy network traffic allows the Snake rootkit to stay unnoticed."
The presence of a reconnaissance component in the Snake framework suggests the existence of an arsenal of infiltration tools.
"As demonstrated, the backdoor commands allow Snake to provide remote attackers with full remote access to the compromised system. Its ability to hibernate, staying fully inactive for a number of days, makes its detection during that time very difficult."
Last summer the Russian government announced the creation of a dedicated branch for the information warfare. Belonging to the Russian Armed Forces, its purpose is to improve cyber capabilities of the country, exactly has many other governments are doing. Official military fonts revealed that the agency's budget for 2013 was 2.3 billion rubles ($70 million).
"Cyber space is becoming our priority…the decision to create a cyber-security command and a new branch of the armed forces has already been made … We are working on the overall concept of the program to be developed in this area … We have reviewed 700 innovative projects so far," declared Andrei Grigoryev, the head of the recently created Foundation for Advanced Military Research, in an interview with Echo Moskvy radio.
Andrei Grigoryev, head of the Foundation for Advanced Military Research, announced that the new unit will be composed of three main areas of military: R&D, futuristic weaponry and soldier gear, and Cyber warfare.
A Look to the Past, to Understand the Present and Predict the Future
The offensives occurred in these days have many similarities with the attacks that anticipated the invasion of Georgia in 2008. Also in that case, Russian militias engaged in information warfare against the enemies to prepare for a kinetic attack.
Georgia and security experts accused Russian state-sponsored hackers of breaking into Georgian government and principal commercial websites as part of an information warfare campaign to supplement Russia's military operations in South Ossetia. The principal government websites were hacked and shut down, including Georgian President Mikheil Saakashvili's official website, as well as the websites of the Ministry of Foreign Affairs, the Ministry of Defence, the central government site, and various commercial sites, which have all been forced offline over the past week.
The hackers of the group of "South Ossetia Hack Crew" defaced The Georgian Parliament website with images comparing Saakashvili to Adolf Hitler. The cyber expert Jart Armin, the most skilled researcher on the story of a group of Russian cyber criminals, linked the attacks on the Georgian government to the operation of the Russian Business Network (RBN), demonstrating a link with Russian authorities.
Armin discovered that Georgian Internet servers were controlled by foreign attackers and Internet traffic was totally hijacked to servers in Moscow. Security experts claim Georgia's websites suffered powerful "denial-of-service" attacks, which knock targets offline.
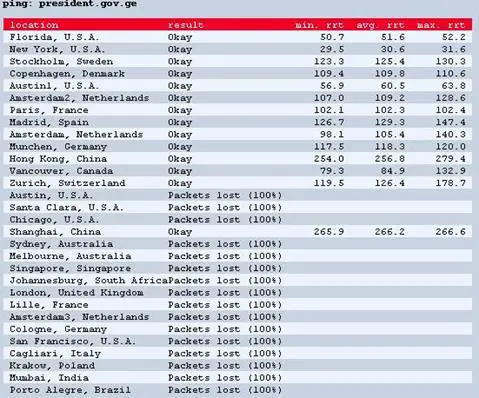
Figure 5 - DDoS against the Georgian President's website
The attacks not only hit government websites. The Russian strategy also targeted any communication channel, even the principal Georgian hacking forum, avoiding the fact that Georgian hackers were able to organize a structured reply. One of Georgia's most popular hacking forums was down for over 24 hours and was under a permanent DDoS attack.
Another singularity of the attacks against Georgia was the availability within the principal Russian hacking forum of a public list of email addresses belonging to Georgian politicians. The hackers arranged a massive spamming campaign and abused the list to conduct spear phishing attacks against the politicians. Security experts and military strategists believe that the list was spread by the Russian military to incite hackers to coordinate a series of attacks against the government.

Figure 6 - List of email addresses of Georgian politicians
The Rule of Hacktivis
Crimea is the battlefield between Ukraine and Russia, but as usual it happens that the dispute also has repercussions in cyber space where the governments are increasing their covert operations. The disputes in cyberspace may involve also third-party actors like hacktivists or cyber mercenaries, or in the worst scenario, other governments interested in fomenting the conflict. We cannot ignore also the possibility to conduct PSYOPs by foreign governments interested in destabilizing the area or the global diplomatic scenario. Foreign actors could spread propaganda messages over the principal forums and social networks, influencing the strategy of group of hacktivists and the sentiment of the population.
Many Russian and Ukrainian URLs have already been attacked as part of the #OpUkraine and #OpRussia campaigns, launched as usual on principal social networks like VK, Odnoklassniki and Facebook.
Ukrainian activists are starting a hacking campaign against Russian websites. The Ukranian site Bimba, which calls itself the "cyber weapon of the Maidan revolution," is sustaining an online recruiting campaign for cyber volunteers wishing to participate in attacks against Russia.
Figure 7 - Bimba website used for recruiting for hacking campaigns
"The VK group #опПокращення // #OpUkraine, identified with Anonymous, uploaded a paste to the pastebin.com site, containing an anti-Russian message and a link to a download of an internal SQL data from Crownservice.ru (publishes tenders for governmental jobs), in a file called Putin Smack Down Saturday," states an interesting post published on SenseCy blog.
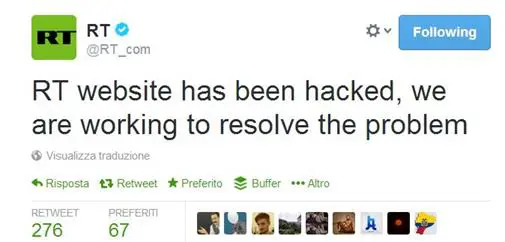
If we analyze the hacktivism phenomena, we can clearly distinguish that almost all operations are conducted to sustain the Ukrainian population. Groups like Anonymous have chooses the side to support, and a series of clamorous attacks hit Russian entities. Russia Today, Russian principal news channel website (RT.com) has been hacked and defaced by an unknown group of hackers.
The media agency confirmed the attack with a Tweet from its official account:
"RT website has been hacked, we are working to resolve the problem"
Figure 8 -RT Tweet
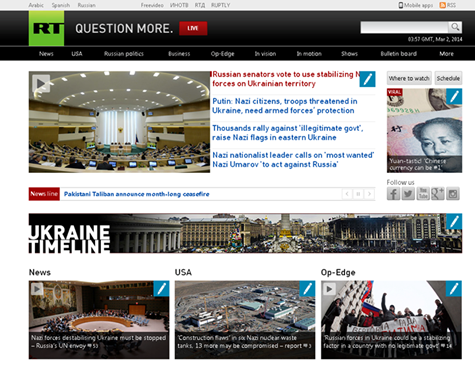
The hackers have replaced the words "Russia" and "Russians" with "Nazi" or "Nazis". The defacement is visible in the following image.
Figure 9 - Defaced RT home page
The modifications to the Russia Today website were visible for nearly 30 minutes. One of the changed headlines stated:
"Nazi nationalist leader call on 'most wanted'"
Though it is still unclear who is behind the attackes, recently the popular collective Anonymous invited its followers to join in the hacking operation dubbed #OpRussia in support of the Ukrainian protesters. Under the #OpRussia campaign the group of hacktivists has hacked hundreds of Russian websites. The attack on the pro-Kremlin news organization is successive to the approval for the use of military force in Ukraine's Crimea by Russian parliament.
Another important attack was conducted by a group of hackers called the Russian Cyber Command, which leaked around 1,000 documents allegedly stolen from Russian Defense Export Company Rosoboronexport.The hacktivists expressed their dissent to Putin's strategy with a message next to a link pointing to the leaked files:
"Taken into consideration recent Russian Government delusional attempts to start WWIII, we – Free from Putin – people of Russian Federation - Free computer renegades and outlaws from IT Security – have decided to initiate a true domestic CyberWar on Russian Military Enterprises and eventually we shall deliver critical infrastructure companies on which Russian Putin's Empire stands on."
The hackers have stolen the files from the systems of India's embassy in Moscow. Once inside the embassy's networks, they sent a spear phishing mail to the CEO of Rosoboronexport.

Figure 10 - Leaked documents
According the hackers' message, it is just the first of a long series data breach against Russian companies.
"Same way we have infected SUKHOI, OBORONPROM, GAZFLOT, RUSAL and VELES CAPITAL and many others, but we shall deliver them right after this very first leak," the hackers said.
At the time of this writing, a group of Ukrainian hacktivists known as Cyber-Berkut published a list of 40 websites that it had hacked, and it includes the state-funded broadcaster Russia Today.
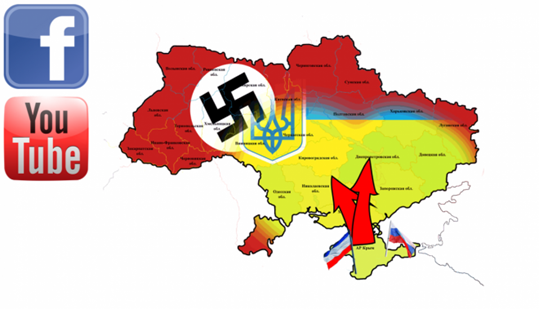
Figure 11 - Cyber-Berkut post on social media
A post on the page of the group on a popular social network reports the following message:
"Today, the "KiberBerkut" countdown begins. Traitors of Ukraine who have transgressed the laws of our homeland, you have nine days to voluntarily surrender to the prosecuting authorities or the Kharkov Simferopol."
The post remarks that Russian "imposters" "have no right" to control Ukraine and must surrender to Ukraine.
Conclusions
What to expect in the future? It's difficult to say. While diplomacy will continue to work, deep in cyber space the attacks will increase. It is premature to define the tensions in cyber space as a cyber war between Russia and Ukraine. On one side hackers who are pro-Ukraine will intensify their activities against Russian entities, while Russian cyber units and patriotic hackers will increase their offensives against Ukrainian opposites. I made a rapid tour on principal social media, andf I noted that on both sides there has started a misinformation campaign. On the one hand, Putin's supporters are publishing disconcerting stories and images about atrocities committed by Ukrainian forces in Crimea, and on the other side of Putin it is possible to read everything.
I desire to close this article by evaluating the position of the Chinese Government on the Crimean crisis. To do so, I contacted a professional that I consider the greatest expert of Chinese Cyber Warfare, Lieutenant Colonel – US Marine Corps Retired & Chairman Cyber Defence and Network Security, Bill Hagestad II.
Pierluigi: Bill Based on your experience which is the position of China on the events? Is China interested in the dispute and why (supremacy, energy, weapons)?
Bill Hagestad II:Yes! Of course! The People's Republic of China is very interested in what is happening in both the Ukraine, geo-strategic energy issues and Crimea, geo-political focused attention.
Pierluigi:Do you think that Chinese cyber units could interfere with actual cyber conflict between Ukraine and Russia? If yes, how and why?
Bill Hagestad II: No, the Chinese will not 'interfere' unless asked to aid the Russians in terms of providing a Mandarin-based rootkit or other form of malware which the Ukrainian info-security technical appliances and teams will not be able to detect using Cyrillic language based IDS & IPS solution - essentially the ultimate Zero Day exploit.
With the escalation of tensions in Crimea, the number of cyber attacks will sensibly increase, and there is the concrete risk that other critical infrastructure in the country will be impacted.
References
http://securityaffairs.co/wordpress/22716/cyber-crime/russia-today-hacked.html
http://securityaffairs.co/wordpress/22875/intelligence/snake-cyber-espionage-campaign.html
http://www.reuters.com/article/2014/03/08/us-ukraine-cricis-cyberattack-idUSBREA270FU20140308
http://www.foreignpolicy.com/articles/2014/03/03/hack_attack
http://www.reuters.com/article/2014/03/04/ukraine-crisis-cybersecurity-idUSL6N0M12CF20140304
http://en.wikipedia.org/wiki/2014_Crimean_crisis
http://www.ibtimes.co.uk/ukraine-crisis-cyber-war-russia-heating-1438890
http://www.technologyreview.com/news/525336/watching-for-a-crimean-cyberwar-crisis/
http://blog.sensecy.com/2014/03/03/ukraine-versus-russia-in-a-cyber-duel/
http://www.zdnet.com/blog/security/coordinated-russia-vs-georgia-cyber-attack-in-progress/1670
http://www.smh.com.au/news/technology/georgian-websites-forced-offline/2008/08/12/1218306848654.html
http://www.reuters.com/article/2014/03/04/us-ukraine-crisis-telecoms-idUSBREA230Q920140304
Hands-on threat intel training
http://www.zdnet.com/blog/security/coordinated-russia-vs-georgia-cyber-attack-in-progress/1670