What Is Spear-Phishing?
When we talk about technology, everyone will agree that it is getting more advanced by the day and information is more easily accessible to us now than it was ten years ago. However, along with the multitude of benefits, it has also brought with it many drawbacks. The easier it is to access information, the harder it becomes to protect it. Malicious users are constantly looking for new ways to intrude into systems and steal valuable information. Even an otherwise secure system can easily fall prey at the hands of these constantly evolving intrusion methods.
In an effort to improve the security of our systems and to keep our critical information safe, we are constantly relying upon technology to do everything for us. But when it comes to cyber security, we cannot ignore the human factor which is still the weakest link that hackers all over the world can easily exploit. This is where the term “phishing” is worth mentioning, which is a means to obtain private information like passwords or credit card details by impersonating a trustworthy source. While general phishing attacks normally fail to achieve the desired results, spear phishing turns out to be comparatively more successful.
Let’s have a look at what exactly spear phishing is, why spear phishing attacks are successful and how we can implement an effective spear phishing defense.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
Spear Phishing Definition
First and foremost, we need to define what spear phishing is. A clear and complete definition will help our readers better understand the concept as they read further on.
“Spear phishing is a phishing method that uses personal information, about an individual, group of individuals, or an organization, to make a phishing e-mail more believable and personalized.”
What is Spear Phishing?
An information security news outlet reported last year that almost 95 percent of spear phishing attacks in 2014 successfully allowed hackers to gain entry into enterprise networks. According to a survey by Cloudmark in January 2016, two-thirds of IT decision makers think of spear phishing as a serious security concern, with 20 percent considering it as the top most concern and 42 percent placing it among the top three security concerns of their organization.
So what exactly is spear phishing? How is it different from simple phishing? Now that spear phishing has been defined, it is important to explain what it is and what the motive behind spear phishing attacks usually is. The content of spear phishing emails is carefully written in such a manner that it seems legitimate and genuine to the reader, thus easily tricking them into sharing their sensitive information such as username, passwords, credit card details, etc. In another type of spear phishing email, users are asked to click a link, which when clicked will deploy spyware in their system and steal their data.
Spear phishing combines phishing tactics such as email personalization, victim segmentation, sender impersonation and techniques for bypassing email filters to trick its target to open an attachment or click a link. Once an attachment is opened or a link is clicked, it allows spear phishers to carry out advanced targeted attacks known also as Advanced Persistent Threat (APT) attacks. Advanced and sophisticated cybercriminals are now able to gain long term access to sensitive networks of organizations with the help of APT attacks.
Typically, the difference between phishing and spear phishing is that phishing attacks are general messages containing little to no personal information whereas spear phishing attacks are targeted at someone specific, usually using a name or other personal information to help give the illusion of legitimacy. Spear phishing emails may appear to come from well-known companies such as EBay, PayPal or Facebook, and may even appear to come from someone in a place of power within the given business.
Why is Spear Phishing Successful?
General phishing attacks are not always successful because with time and experience, people have become more conscious of responding to requests seeking private information unless they trust the source. The success of spear phishing depends upon three things. Firstly, the source should appear to be known and trusted. Secondly, the information in the mail should back its validity. Lastly, the request made by the source should seem logical.
The reason why spear phishing attacks are mostly successful is because of the presence of the above mentioned factors. Few people suspect that an email would be lying about the source’s identity. Even fewer would suspect that an email specifically mentioning their last name could be a hoax. When simple phishing is combined with call to action techniques, such as asking to click a link, it triggers our innate human curiosity and desire to follow through.
Employees who fall prey to spear phishing attacks put their entire organization at risk. Malicious links in these emails can do anything from asking for credentials to allowing the spread of malware in their machines, potentially allowing the attacker to gain access to critical information.
Some Characteristics and Real Life Examples
Here we describe some key characteristics and examples of advanced spear phishing attacks:
Multi-Vector Threat: Uses a combination of zero-day application exploits, email spoofing, dynamic URLs, drive-by download, etc. This allows the hackers to bypass traditional means of spear phishing defense.
Zero-Day Vulnerability Leverage: Advance Spear Phishing Attacks leverage the zero-day vulnerabilities in desktop applications, plugins and browsers and compromise systems. Zero-day vulnerabilities are security holes that are unknown to exist by the vendor and/or entity.
Multi-Staged Attack: In the first stage the system is initially exploited and then further stages involve malware outbound communication, binary download and data exfiltration.
Lack of Spam Characteristics: Personalized messages do not seem suspicious in contrast to high volume spam broadcasted to masses at one time. Reputation filters have a hard time flagging them and this minimizes the likelihood that they will be caught by spam filters.
These characteristics indicate that scammers usually make use of simple as well as advanced phishing techniques to successfully trick people into believing them. The following real life examples show the dangerous consequences a seemingly simple email can have on the victims of spear phishing attacks.
- In January 2009, the CEO and Chairman of Rutberg & Company LLC Mr. Bryan Rutberg became a victim of a spear phishing attack when his Facebook account was hacked. According to him, he had responded to an email from a colleague asking him to click on a link to his Facebook account. Upon clicking, a fake Facebook page opened where he filled his actual username and password. Upon getting the Facebook details of Rutberg, the hacker then took over his account and sent messages to his friends, telling them that he has been robbed and needs them to send money to a branch of Western Union in London. One of Rutberg’s friends actually sent the money and became an indirect victim of the phishing scam.
Spear Phishing Training and Awareness
According to a research by NSS labs, user training and education is the most effective spear phishing defense mechanism. Training and education can be in the form of regular classroom style presentations, reminder emails, office memos, newsletters, or simulated phishing emails. Simulated phishing emails are specifically helpful as they can provide a real life scenario to employees, give soft reminders about best practices and also alert the management about which employees require more training.
How to Protect Yourself from Spear Phishing?
Spam filters are one of the basic controls you can deploy to avoid receiving emails from uncommon sources. Advanced malware detection software also helps identify phishing attachments and links, even it has not dealt with them before. That being said, however, attackers are getting more sophisticated and technology is never a complete solution to keep malicious users away.
To be secure, in terms of technology, IT departments need to keep all systems on their network updated. Outdated systems are often the weak links exploited during an attack. Because the human factor cannot be ignored in phishing attacks, even after all these measures, the most important thing of all is to educate and train employees on spear phishing defense. The best way to do so is to provide real life scenarios and examples with the help of a phishing simulator.
One example of this service would be a product called “SecurityIQ” made by Infosec Institute. They have created several simulated phishing email templates that allow employees to be tested for phishing and teach them how to spot a spear phishing scam when they fail the test.
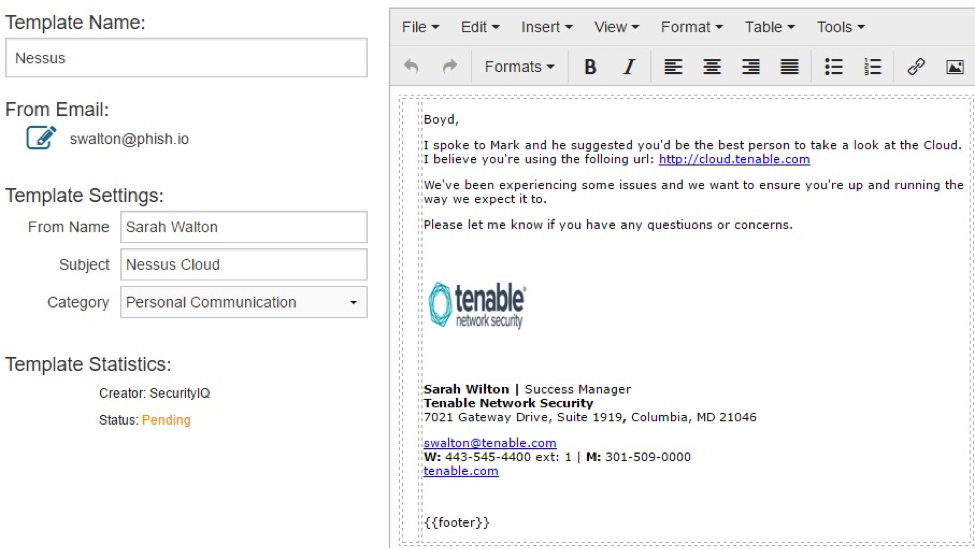
Below is an example of a spear phishing email template from SecurityIQ. These can be used to check employee awareness regarding phishing scams and gauge the need for employee training by testing how many employees actually fall prey to them.
Here, the sender has directly addressed the employee and the email content seems like a routine office communication. In reality, the link sent to the user actually download’s and installs malware into their system.
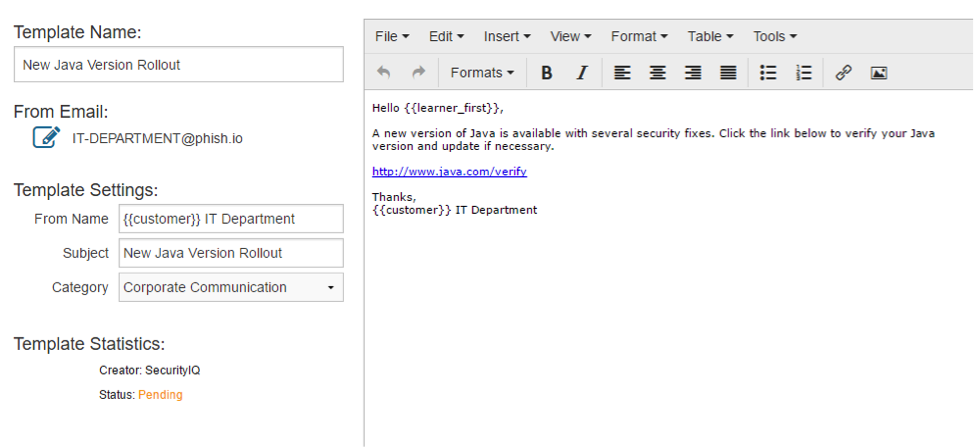
In this Template, the email appears to have been sent by the IT Department, asking all users to update Java on their systems.
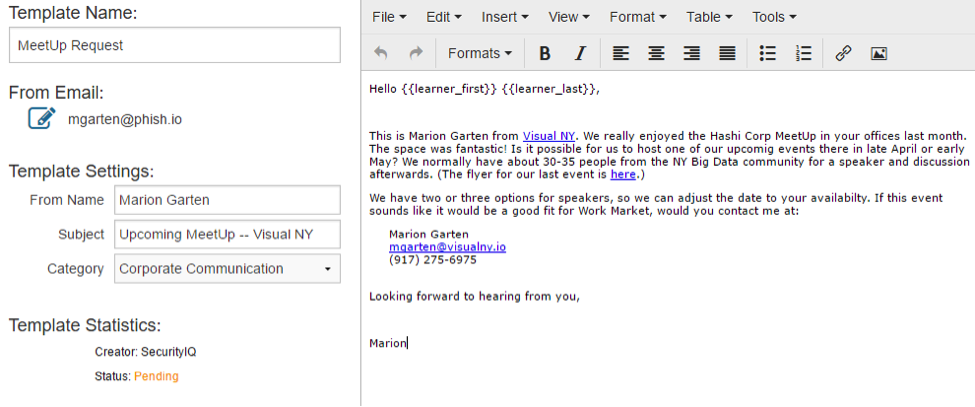
In this email, the sender is referring to a past event that actually took place and addressing the receiver by their name. The request seems legitimate and can easily trick the receiver into clicking the link.
These are only few of the examples of the kind of templates that can be created using an application like SecurityIQ. These simulated emails help organizations and their employees understand the nature and potential level of sophistication of spear phishing emails they might receive in the wild and prepare them for a more “phishing-conscious” approach when reading and responding to electronic messages.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
What are Some of the Best Practices When Responding to Emails?
Here we give you a list of best practices for spear phishing defense to help yourself and your coworkers avoid such attacks:
- Use common email sense. Never trust an email message, even if you think it is from a trusted source. Take out some time to examine its authenticity, especially if the message asks you to provide confidential information or to click a link.
- Be extra vigilant about emails that refer to current events. For example, an email apparently coming from your colleague asking you to open a link to pictures of a recent event that took place in your organization, live broadcasting of a sporting event, or pictures of a recent natural disaster have the potential to be malicious links.
- Do not assume that emails sent by colleagues or friends have secure attachments or links. Information such as email addresses can be easily attained by hackers from the company’s official website or social networking websites. If the contents of the message seem suspicious, a safe approach is to call your friend from whom you have received the mail and verify if they actually sent it or not, especially if you were not expecting a message from them.
- Analyze the URL in case of a web link inside the message to trace its actual origin. Since it is very easy to spoof a hyperlink’s text, take your cursor over the URL without clicking and check the complete address of the link. If it looks unfamiliar or seems to point to something other than what the text implied, do not click it.
- Dig further on emails requesting immediate action. Check the company website by searching the company name in Google and get their contact number. Call them to verify if you have received a valid message or not. Do not call on a number provided in an unfamiliar or seemingly suspicious e-mail message as it could potentially lead to someone other than who you intend to call.
- Do not post too much personal information on social networks. Putting information such as birthdays, names and ages of your spouse or kids and anniversary dates can be used against you by potential phishers and makes it easy to access some specific details about your life.
- Use alternative communication to cross-check and confirm the authenticity of any email that requests for a transaction above a certain amount. For example, if you receive an email from your boss directing you to make a transaction, specifically to send money to an account or to make an international wire transfer, always make a phone call and confirm if the email is valid or not.
- Always be cautious about unexpected messages on through any system, not just e-mail. There are other forms of this attack, a few examples would be Vishing or SMiShing, which may utilize methods such as text messages or phone calls in place of e-mail messages.