Top 10 Anti-Phishing Best Practices
Emails are one of the major modes of communication today. Companies rely heavily on emails when conducting their day-to-day operations. Management sends out directives to their subordinates via emails, and the same goes for company-client communication. This is why they make a good target for phishing attacks, and why it is essential to put in place best practices that can protect your business.
Phishing simulations & training
To help prevent the worst case scenario, here are 10 Anti-Phishing best practices in corporate communication that every company, business owner, and employee should be aware of:
1. Implement and Update Company Procedures
Every company should implement and periodically update its procedures regarding the protection of its users’ confidential data and business-critical systems. For instance, the companies should frequently perform a backup, restoration, and testing procedures for data assets to quickly recover from the ransomware attack. Furthermore, the protection of critical data assets, such as financial transactions, must be ensured by implementing dual-control procedures. In fact, a dual-control procedure has two layers of security, which is a strong defense against phishing attacks.
2. Report Suspicious Activities
If you find any suspicious activity or Email in your company’s account, immediately report it to your digital security department. The faster you inform them, the faster they deal with it.
3. Stay Alert of Suspicious Emails, Links or Attachments
Don’t be curious about the Email content, as the phishers lure you to click on the infected links and Emails to acquire your sensitive information. You should always delete suspicious links and Emails. Even opening these links and Emails can secretly breach your computer security.
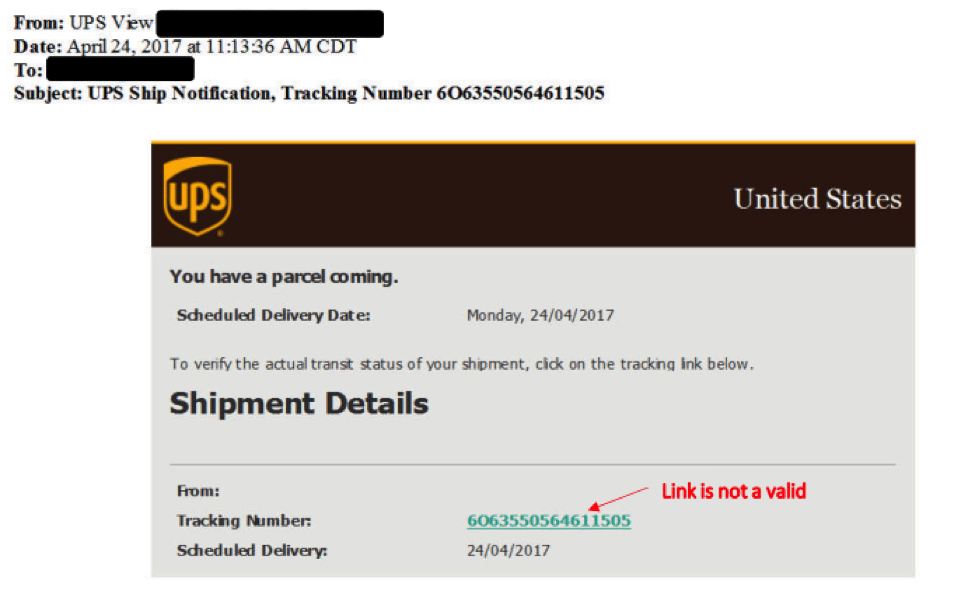
Recently, a fraudulent Email was reported to “fraud@ups.com” that included an invalid link. That suspicious Email is shown in the screenshot below:
Many phishers commonly use Email attachments to sneak a virus program onto the individuals or company’s computers. These viruses can assist the scammer to steal a wealth of information from the infected computer. Once the attack is carried out, your computer acts as a ‘bot’ and can be used for digital crimes. To avert this situation, you must not open unknown attachments.
Also, Digitally Sign Confidential Emails – the digital sign adds another important layer of security to Emails and assists the receiver to make sure that the scammers don’t alter the contents of Email during transit. You can use SSL/TSL certificate to sign Emails and encrypt Email communication.
More importantly, A Sender Policy Framework or SPF is an Email authentication or validation tool designed to detect and block spoofed or forged Emails.
Companies that employ SPF policies provide mail exchangers the capacity to check if an incoming Email from a certain domain is a part of an authorized list of hosts approved by the domain’s administrators.
Through an SPF check, Email providers can look up the domain name that is listed Domain Name System (DNS) to see if the IP address—sending the Email—is a part of the list. If not, then the message has failed the SPF validation.
To acquire the better security benefits, alerts of the validation failure must be acted on. After failing SPF verification, the owner of the network can determine whether to quarantine, block or to tag Email as suspicious.
Why is the Implementation of SPF So Important?
SPF is a widely used and highly ranked technique to mitigate cyber-attacks. The security effectiveness of SPF is rated as excellent as well. Your adversary sends scam Emails to exploit your network and, on the other hand, SPF lowers the chances of malicious contents getting into your network.
How to Implement SPF
SPF can be implemented in two parts: Checking and Publishing.
- SPF Checking helps your company to determine whether the incoming Emails were sent from a legitimate source.
- SPF Publishing assists you in determining which Email Server is authorized to send Emails from your company.
4. Filter Spam
Filtering Spam is another great approach to Email security. Most scammers send unsolicited commercial Emails to the individuals or business communities. You should prevent these spam Emails from reaching your private or company’s mailbox. Presently, many web Email services and applications offer a spam-filtering feature. You need to look at the tutorial guide provided by your Email application to filter scams.
Although it is hard for the spam filter to discriminate between spam and legitimate Emails, it would keep a good deal of spam Emails from getting into your mailbox.
5. Use Common Sense
If the Email gets into your mailbox and promises you big money for no or little effort, or invites you to get unclaimed funds from people you do not know in your country or abroad, then you should take the illegitimacy of this Email into serious consideration.
6. Protect Your PCs
You should not access your confidential information from unprotected machines, like a shared computer at home or in an internet café. In such circumstances, you put your sensitive information at high risk.
Install a Firewall and Keep it Up-to-date: The up-to-date Firewall must be installed on all the PCs and Servers associated with the Company. Though Firewall doesn’t directly prevent spam Emails entering into PCs, it protects the employees from inadvertently executing the virus-bearing attachments or malware. The Firewall also blocks the suspicious network traffic and allows only legitimate contents.
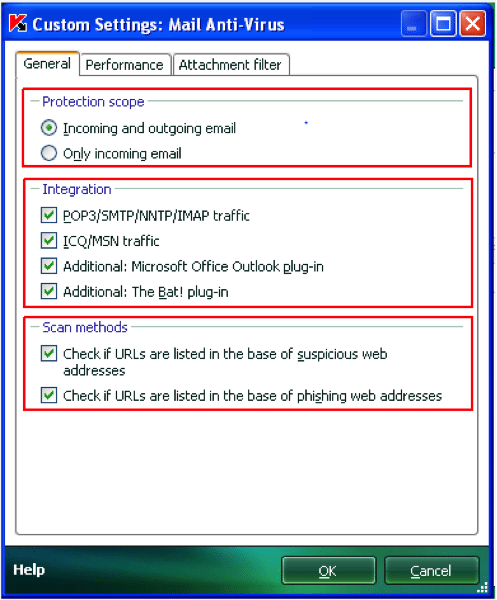
Install Antivirus Program: You must install the antivirus software to prevent viruses from arriving in your company’s computers. It is preferable for those antiviruses to have an Email-scanning feature. For example, Kaspersky Antivirus contains a particular feature: Mail Anti-Virus, showing below.
7. Learn Your Organization’s Email Policies
Most organizations have clear Email policies about how they conduct communication with their employees and customers via Emails. For example, the company would never ask you to submit confidential information (username, password, account number, etc.) in Emails. Therefore, learning your company’s Email policies can save you from an imminent disaster.
8. Select and Configure Your Email Client
The selection of Email Client is significant because you can compare the security features of your Email Client with its rivals. Therefore, you must visit the different Email Client’s websites and choose the best one for you in term of best security features.
Also, configuring Email client can protect you from Email scams. For example, if you configure Email application to view Emails as a “text only,” it would certainly help you to protect from scams that fraudulently use HTML in Emails.
9. Protect Your Password
Don’t store the password on browsers, because it makes easy to log-in to an Email account and may compromise the system if the scammer gains access to the browser.
Also, pick a strong password and replace it regularly, especially with lower and upper-case letters and numbers, and don’t use your birthday, wedding anniversary, and other personal dates.
10. Avoid Using Removable Media
Removable media, such as USB thumb drives, SD cards, and even gadgets like iPods and MP3 players are more prone to the malware attacks, such as malware family Worm.Win32.Radminer. Therefore, try to avoid using removable media for your sensitive information or private data. If the use is inevitable, then it must be properly scanned before and after connectivity.
See Infosec IQ in action
Infosec IQ by Infosec
Do you think your company is vulnerable to Email phishing? Do not wait until it is too late. Infosec offers Security Awareness and Anti-phishing Training from Infosec IQ, a computer-based enterprise training platform that protects your company or organization against phishing attacks today. Start a free account or launch a free Phishing Risk Test to measure your organization's phishing susceptibility today!