Spearphishing: A New Weapon in Cyber Terrorism
Introduction: Spear phishing attacks
Spear phishing and its evolutions like the watering hole attack represent one of the most insidious attack techniques adopted by the majority of threat actors in cyber space.
According to the experts at Trend Micro security firm, spear phishing is the attack method used in some 91 percent of cyber attacks.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
Differently from a common phishing attack, in the spear phishing attack scenario bad actors target a subset of people, usually the employees of an organization, members of an association or visitors of a particular website. The purpose of the attack is to collect personal information and other sensitive data that would be used later in further attacks against the victims.
The attack vector is usually an email message that appears to come from a legitimate entity, that requests an action from the victims. There are numerous variants of spear phishing: some phishing emails include malicious links to websites controlled by attackers, while others include a malicious attachment that infects the victim's system.
In recent attacks operated by several APT groups, the malicious email sent to the victims encouraged users to read Word or PDF documents that were specifically crafted to exploit vulnerabilities in the web browser in order to compromise the host. Analyzing data related to the cyber attacks that occurred in the last five years, it is easy to deduct that spear phishing represents the easiest way for an attacker to compromise enterprises and organizations of any size and is an important area of focus in any security awareness program.
The "Operation Aurora" attack (2010), the hack (2011), the Target breach (2013), and the most recent Sony Entertainment (2014) and the cyber attacks operated by Operation Carbanak and the Syrian Electronic Army are just a few examples of offensives that relied on spear phishing as an infection method.
The key to the success of a spear phishing attack is that it relies on the weakest link of a security chain, humans. Another characteristic of a spear phishing attack is that the content shared with the victims of an attack is usually highly customized to the recipient to increase the chance of exploitation. Social engineering techniques entice users to click on malicious attachments and links by suggesting they may be topics of interest for the victims.
Spear phishing and terrorism
Terrorism is defined as violent conduct or the threat of violent acts conducted with the purpose to create a climate of terror and damage the critical operations of a nation.
We must consider that today's society heavy relies on technologies, the majority of services that we access every day strongly depend on IT systems. This is particularly evident in some industries like defense, energy, telecommunications and banking.
For this reason terrorism is enlarging its spectrum of action and is targeting IT services whose destruction can have the effects of an old style terrorist attack.
Terrorists have several ways to use technology for their operations, and once again, the spear phishing methodology could help them to realize their plans. Let's imagine together some attack scenarios and the way a spear phishing attack could help a terrorist to hit the collective.
Terrorists can directly target the services compromising their operations.
A number of services are based on sophisticated infrastructure managed by humans. By interrupting them, it is possible to create serious damage to the victims and to the population.
Let's imagine a cyber attack against a bank that will cause the interruption of the operations of a financial institution, or a cyber attack against telecommunication systems of a national carrier. Suddenly the users will have no opportunity to withdraw money from their bank accounts, or they will be isolated due to the interruption of the service of the telecommunications carrier; both events would create panic among the population.
Again, let's think to cyber attacks against the transmission of a broadcaster or an energy grid of a state. Also in this case, the impact on the public order could be dramatic. All the systems that could be targeted by the attacks mentioned rely on both an IT system and a human component, and human operators are the element that could be targeted by terrorists using spear phishing attacks that could give them the opportunity to infiltrate the computer systems and move laterally inside the systems of the service provider.
Unfortunately, the attack scenarios described are feasible, and attacks with similar consequences on the final services have already occurred. In those cases, the threat actors were state-sponsored hackers and cyber criminals that mainly operated for cyber espionage and for profit, but in the case of a terrorist attack, the final goal is more dangerous: the destruction itself.
Terrorists can run a spear phishing attack for information gathering
Information gathering through a spear phishing technique is the privileged choice for a terrorist. Cells of terrorists could use this attack method to spread malware and hack into computers and mobile phones of persons of interest with the intent to collect information on their social network and related to the activities they are involved in. Spear phishing could allow terrorists to collect information on a specific target or to access information related to investigation on members of the group.
Let's imagine a spear phishing attack on personnel of a defense subcontractor that could give the terrorist precious information about security measures in place in a specific area that the terrorist cell intends to attack.
Online scams to finance activities of cells
Spear phishing attacks could be used by terrorists to finance small operations. The attacks can be carried out with the intent to conduct online frauds and the proceeds, albeit modest, may also finance the purchase of weapons and false documents in the criminal underground. The terrorists operate online purchases that enable cells to avoid controls exercised by the intelligence agencies in the area.
Terrorists groups become more tech-savvy
Terrorist groups like ISIS and Al Qaeda have become more tech-savvy, and among their members there are also security experts with a deep knowledge of hacking techniques, including social engineering and spear phishing. Spear phishing is the privileged technique to steal sensitive information from corporate or government entities that the terrorists plan to hit.
Unfortunately, the skills necessary to hack SCADA systems of a critical infrastructure are less and less specialized, because on the Internet it is easy to find numerous exploits ready for use. Very often, it is sufficient to know the credentials of a VPN service used to access the SCADA system remotely in order to hack it.
Terrorists are aware of this, and spear phishing attacks against the staff that manages the systems in the critical infrastructure would provide all the necessary information to attack the internal network structure and launch the exploit to hack the SCADA systems.
Resuming, a spear phishing attack could give an attacker the information necessary to damage processes of a nuclear power plant, a water facility systems or a satellite systems.
Another factor that incentivizes the use of spear phishing attacks by terrorists is that this kind of attack for information gathering could be conducted remotely without arousing suspicion.
ISIS operates spear phishing attacks against a Syrian citizen media group
The demonstration that the terrorist group of the Islamic State in Iraq and Syria (ISIS) is using spear phishing techniques against opponents was provided by Citizen's Lab, which published a detailed report on a hacking campaign run by the members of the organization against the Syrian citizen media group known as Raqqah is being Slaughtered Silently (RSS).
The hackers operating for ISIS run the spear phishing campaign to unmask the location of the militants of the RSS with the intent to kill them.
The Syrian group RSS is an organization that in several cases has criticized the abuses made by ISIS members during the occupation of the city of Ar-Raqqah, located in northern Syria.
"A growing number of reports suggest that ISIS is systematically targeting groups that document atrocities, or that communicate with Western media and aid organizations, sometimes under the pretext of finding 'spies'."
ISIS members are persecuting local groups searching for alleged spies of Western governments. The spear phishing campaign run by the terrorists allowed the members of ISIS to serve a malware to infect the computers of the opponents and track them. The experts at Citizen's Lab uncovered the spear phishing campaign managed to target the RSS members.
"Though we are unable to conclusively attribute the attack to ISIS or its supporters, a link to ISIS is plausible," Citizen's Lab noted. "The malware used in the attack differs substantially from campaigns linked to the Syrian regime, and the attack is focused against a group that is an active target of ISIS forces."
The malicious emails contain a link to a decoy file, which is used by attackers to drop a custom spyware on the victim's machine.
"The unsolicited message below was sent to RSS at the end of November 2014 from a Gmail email address. The message was carefully worded, and contained references specific to the work and interests of RSS," states the report. "The custom malware used in this attack infects a user who views the decoy "slideshow," and beacons home with the IP address of the victim's computer and details about his or her system each time the computer restarts."
The researchers at Citizen's Lab have noticed that the malicious code served through the spear phishing campaign is different from the Remote Access Trojans used by the hackers backed by the Syrian Government.
Figure 1 - Slideshow.zip file used by ISIS members in the spear phishing campaign
One of the principal differences is related to the control infrastructure. The members of the ISIS used an email account to gather information from compromised machines.
"Unlike Syrian regime-linked malware, it contains no Remote Access Trojan (RAT) functionality, suggesting it is intended for identifying and locating a target," said CL. "Further, because the malware sends data captured by the malware to an email address, it does not require that the attackers maintain a command-and-control server online. This functionality would be especially useful to an adversary unsure of whether it can maintain uninterrupted Internet connectivity."
Western intelligence collected evidence of the presence of hackers among the members of ISIS. According to some experts, members of ISIS are already working to secure communications between ISIS members and supporting the group to spread propaganda messages avoiding detection.
"In addition, ISIS has reportedly gained the support of at least one individual with some experience with social engineering and hacking: Junaid Hussain (aka TriCk), a former member of teamp0ison hacking team. While Mr. Hussain and associates have reportedly made threats against Western governments, it is possible that he or others working with ISIS have quietly supported an effort to identify the targeted organization, which is a highly visible thorn in the side of ISIS."
ISIS members are targeting many other individuals with spear phishing attacks – for example, it has been documented that it targeted Internet cafés in Syria and Iraq that are used by many hacktivits.
"Reports about ISIS targeting Internet cafés have grown increasingly common, and in some cases reports point to the possible use of keyloggers as well as unspecified IP sniffers to track behavior in Internet cafes," Citizen's Lab reported. Citizen's Lab seems to be confident of the involvement of a non state-actors in the attack, and ISIS is a plausible suspect.
"After considering each possibility, we find strong but inconclusive circumstantial evidence to support a link to ISIS," CL said. "Whether or not ISIS is responsible, this attack is likely the work of a non-regime threat actor who may be just beginning to field a still-rudimentary capability in the Syrian conflict. The entry costs for engaging in malware attacks in a conflict like the Syrian Civil War are low, and made lower by the fact that the rule of law is nonexistent for large parts of the country."
The Energy industry – A privileged target for a terrorist attack
The energy industry is probably the sector more exposed to the risk of terrorist attacks, as energy grids, nuclear plants, and water facilities represent a privileged target for terrorists. Spear phishing attacks could allow terrorists hit systems in the critical infrastructure to destroy the operations or could allow bad actors to gather sensitive information to organize a terrorist attack.
The spear phishing campaign could be run against the personnel of a targeted infrastructure to gather sensitive information on defense mechanisms in place and ways to breach them.
The last report issued by the DHS's Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), the ICS-CERT MONITOR report related to the period September 2014 – February 2015, revealed that the majority of the attacks involved entities in the Energy Sector followed by those in Critical Manufacturing.
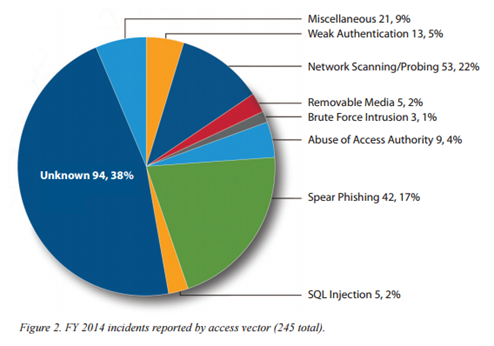
Figure 2 - ICS-CERT MONITOR report related to the period September 2014 – February 2015
Spear phishing attacks appear among the principal attack vectors adopted by threat actors, but it is important to highlight that the report doesn't mention cyber terrorism among possible motivations for the attacks. The fact that spear phishing attacks are effective to compromise the systems in the energy sector should make us reflect on the potential effectiveness of the cyber threat if it is adopted by terrorist groups.
In April 2014, security experts at Symantec discovered a cyber espionage campaign targeting energy companies around the world by infecting them with a new trojan dubbed Laziok. Also in this case, the attack chain starts with a spear phishing attack. The emails used by hackers come from the moneytrans[.]eu domain, which acts as an open relay Simple Mail Transfer Protocol (SMTP) server. The e-mails contain an attachment, typically in the form of an Excel file, that exploits a well-known Microsoft Windows vulnerability patched in 2012 and that was exploited by threat actors behind Red October and CloudAtlas campaigns.
The experts confirmed that the bad actors who used Trojan.Laziok malware to target energy companies haven't adopted a sophisticated hacking technique. The investigation demonstrated that they exploited an old vulnerability by using exploit kits easy to find in the underground market.
This kind of operation could be potentially conducted by groups of terrorists that intend to collect information on the IT infrastructure adopted by an organization to compromise it and cause serious damages to the process of a refinery or a nuclear plant.
Since now security experts have no evidence for the availability of zero-day exploits in the arsenal of terrorists, the spear phishing campaign run by groups linked to the ISIS or Al-Qaida are quite different from the attacks run by APT groups backed by governments.
Unfortunately, it is impossible to exclude that in the future group of terrorists with significant financial resources will have access to the underground market of zero-day exploits and purchase them to conduct targeted campaigns aimed to cause destruction and the lost of human lives.
Conclusion
Spear phishing represents a serious threat for every industry, and the possibility that a group of terrorists will use this technique is concrete.
To prevent spear phishing attacks, it is crucial to raise awareness of the mechanics behind these kind of offensives. By sharing the knowledge of the techniques and tactics of the threat actors, it is possible to reduce in a significant way the likelihood and impact of spear phishing campaigns.
To prevent spear phishing attacks, it is necessary that everyone in an organization has a deep knowledge of the threat and defense mechanisms.
The pillars for an effective defense against the spear phishing attacks are:
- Awareness of the cyber threat
- Implementation of effective email filtering
- Implementation of effective network monitoring
Spear phishing attacks are still a primary choice for cyber criminals and intelligence agencies that intend to steal money and sensitive information, but the technique could be a dangerous weapon to start a cyber terrorism attack.
In order to protect our society we must trigger a collective defense. As explained by many security experts, the government cannot prevent spear-phishing attacks against private firms, but a successful attack against private industrial systems can be used to harm the security of a nation and take innocent lives.
For this reason, it is important to share information on ongoing spear-phishing attacks and track potentially dangerous threat actors, especially cyber terrorists.
Homeland security and national defense need a collective effort!
References
http://securityaffairs.co/wordpress/31325/malware/isis-spear-phishing-attacks-syrian-group.html
/phishing-dangerous-cyber-threat/
http://securityaffairs.co/wordpress/30328/cyber-crime/cyber-attacks-energy-industry.html
http://securityaffairs.co/wordpress/35567/cyber-crime/energy-companies-laziok-trojan.html
http://securityaffairs.co/wordpress/34936/cyber-crime/ics-cert-monitor-report-apt.html
http://techcrunch.com/2015/03/27/spear-phishing-could-enable-cyberterrorism-attacks-against-the-u-s/
https://citizenlab.org/2014/12/malware-attack-targeting-syrian-isis-critics/
Phishing simulations & training










