How Phishing Attacks Bypass Spam Filters
A successful phishing campaign has at least three common denominators, which are accurate target information, successful message delivery, and execution of the malicious intent on the client side. Often time’s phishing is thought of as a user exploit only, but the fact of the matter is that phishing exploitation requires the breakdown of several controls including user awareness, administrative controls, and technical controls.
With that said, it is important to understand that targeted attackers are aware of this and continually test these controls to give themselves the highest probability of delivery and execution. More than likely your organization will easily thwart a massive random campaign, but targeted campaigns are designed to bypass popular enterprise security controls. I say this only to remind you that phishing attacks are still the primary ingress point for sophisticated attackers regardless of how many controls are in place.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
All successful cyber attacks also begin with planning and testing. Your adversary expects to encounter spam filters, firewalls, and proxy servers and you can expect that they are testing these controls days or weeks in advance of launching their campaign. Knowing this, it is imperative for your organization’s security team to think, prepare, and test like an attacker.
The following section shows a bit of reverse engineering of standard planning techniques, which will hopefully help improve your pre-attack security posture.
Spam Filters
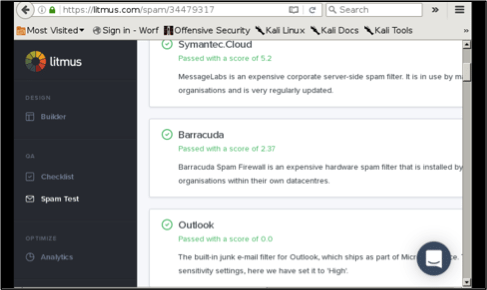
Spam filters are the first line of defense that protects organizations from phishing attacks. These filters can be configured to alert on anything from keywords to untrusted sending domains or IP addresses, depending on your spam-filtering solution. The image below shows an example of how one application can be used to test message delivery across multiple major email providers.
To help counter this attack method, you want to make sure that your organization’s spam filters are configured to be as strict as operationally possible. Whenever feasible you should whitelist trusted domains and sandbox all others for human review. At a minimum, your enterprise email solution should be configured to black hole any untrusted messages which will deny the attacker any bounces that may hint to the security stack that you have in place.
Firewall / Proxy
Web proxy and firewall controls are often similar in their rules, so if an attacker can create an attack that bypasses spam filters, then they are confident that the network is allowing inbound SMTP, so now they just need to test the firewall and proxy.
A common method used for such testing is to host HTML images on the malicious web server, and embed those images into the phishing message. This allows the attacker to view the GET request of the embedded image, which confirms that the firewall and proxy are allowing communication back to the malicious web server.
The Attack
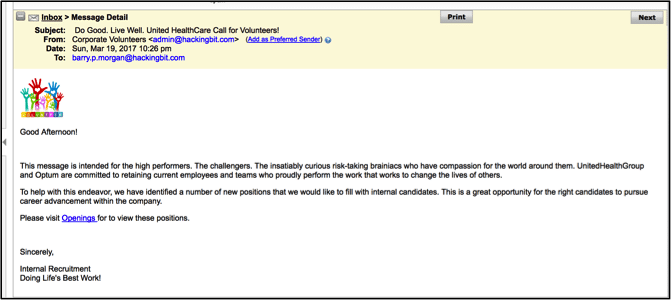
Now the attacker is confident that his messages are bypassing spam filters and the payload is bypassing firewalls and proxies. The image below represents a typical message that has utilized these pre-attack methods.
Notice the image at the top of the message. Not only does the image add to the authenticity of the message, but it is also providing the phisher a confirmation that the message has been rendered in a user’s inbox. With the appropriate attack settings validated, the malicious actor can now develop and deploy a slew of attacks against the organization.
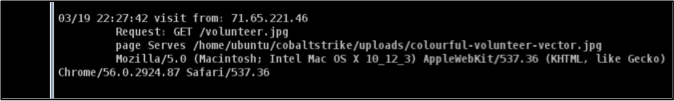
Below is the attacker’s view of his web server logs.
Knowing the level of preparation that hackers are taking, its paramount that security teams perform the same level of preparation and testing.
The best way to combat targeted phishing attacks would be to whitelist all authorized domains; of course this may not be practical for organizations that depend on external customers. At a minimum, security teams should not allow the download images within messages, which will help prevent the attacker from knowing if his malicious message was delivered.
Another option is to set proxy servers to deny requests to domains that have been registered within the last 30 days. Most phishing campaigns rely on categorized domains that have expired and subsequently been purchased and repurposed by the bad guys for their phishing campaigns.
Phishing simulations & training
Risk versus reward. Of course there may be times that un-displayed images and blocked domains may cause a moment of confusion for end-users, but without these controls, there will be many more times that your organization provides attackers with all of the validation they need to view your organization as a viable target.