Phishing with Data URI
Phishing
Phishing is a method of e-mail fraud that is used to gather personal and financial information from the recipients. According to Wikipedia, phishing is the act of attempting to acquire information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication. Phishing is typically carried out by email spoofing or instant messaging and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one.
Phishing is an example of a social engineering technique used to deceive users; it exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
Data URI
The data URI scheme is a URI (uniform resource identifier) scheme that provides a way to include data in-line in web pages as if they were external resources. It is a form of a file literal or here document. This technique allows normally separate elements such as images and style sheets to be fetched in a single HTTP request rather than multiple HTTP requests, which can be more efficient.
A URI is a string of characters that identifies a resource. The term encompasses the better-known uniform resource locator (URL) and uniform resource name (URN). However, whereas URLs specify the location of a specific network resource and how it should be accessed (i.e., with HTTP, hypertext transfer protocol), URIs are more flexible and can even be used to host the data they "link" to.
Old Method of Phishing
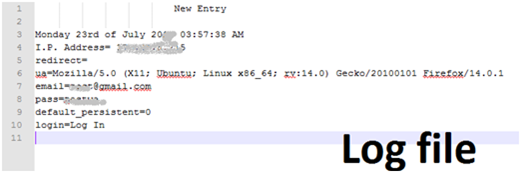
In the old method of phishing, the hacker has two pages; one is a fake page and the other is a PHP file. The fake page looks like the login page of the original website and it has the blocks where the username and password are entered. When a person enters his details, those details are sent to the PHP file. The PHP file is designed in such a way that it creates a new file and stores the username and password in that file, or it can send the username and password to the attacker's email. The two files, i.e., the fake page and the PHP file, need to be uploaded somewhere. When a victim visits the URL and enters his details, the attackers get the username and password from the log file.
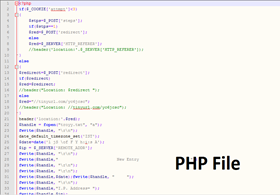
Both the fake page and the PHP file need to be uploaded to our server.
We will get results in this format in our log file.
Phishing with Data URI
Using the data URI scheme, it is possible to present media content in a web browser without hosting the actual data on the internet. Data URIs follow this scheme:
data:[<mediatype>][;base64],<data>
<mediatype> means that you can represent any content type (e.g., image/jpeg,text/html, etc.) from the specification that is supported by the web browser.
It also defeats traditional defenses against phishing attacks, such as web filtering and reputation management, because victims don't need to communicate with an attack server to get phished
In this method, when the victim clicks on the hyperlink, he is redirected to the fake page, but our fake page is not hosted anywhere. It is basically made up of data URI, as we discuss later on. This fake page is linked with the PHP file that can handle the data and send the details via mail to the attacker specified by the attacker. The PHP file has to be hosted somewhere.
How Is the Data URI Formed?
The source code of a website is modified by the attacker in such a way that the details of the victim are sent to the PHP file and the PHP file sends the details to the attackers. The source code of the web page is modified and then converted into base 64 format. Here base 64 is optional.

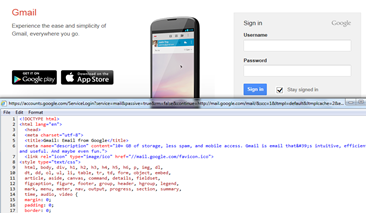
Format of Data URI

How to Perform This Attack
Open the webpage whose phishing page you want to built. Here, as a demonstration, I am using a gmail page. Go to gmail.com, click on view source, then copy all the source code of the page and paste it into notepad or any other editor. Now search for "action" in that code.
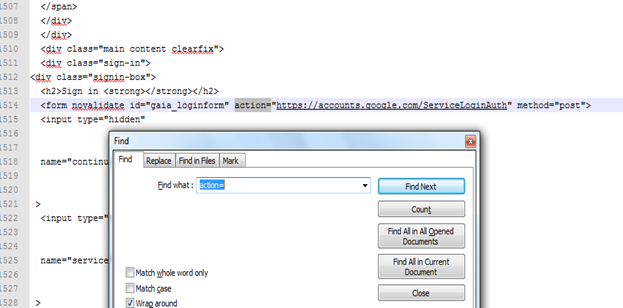
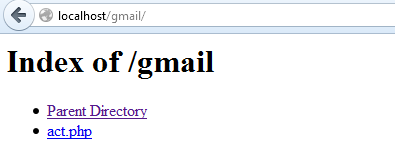
Replace the URL there with our script URL uploaded on server. In my example it is http://localhost/gmail/act.php.
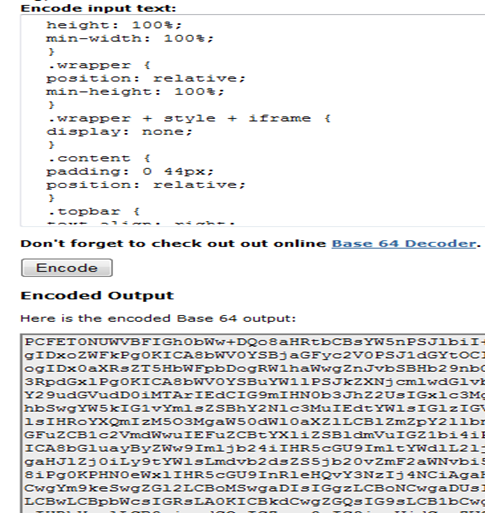
Copy the entire code and convert it into base 64 format. You can convert your code to base 64 by using various online tools like http://www.opinionatedgeek.com/dotnet/tools/base64encode/
Copy all the code and paste it in the data URI format.

To test whether it's working or not, copy the whole code and paste it into your browser. Enter your username and password.
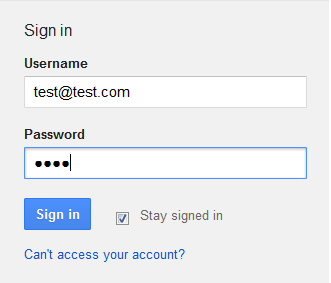
You will see the log file is created on the server and you will get the username and password of the victim as shown below.
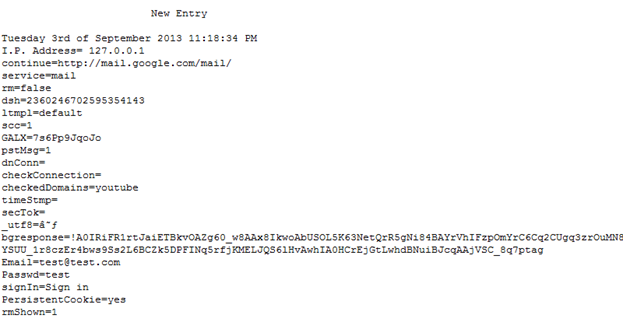
How to Spread or Send It to Victim
To spread or deliver our phishing page to the victim, we have to use the following JavaScript code.
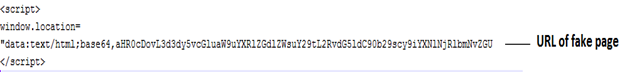
We can use this script by injecting on the web application through the vulnerabilities like XSS or we can create the HTML file by using this script and sending it to the victim.
Phishing simulations & training
Benefits of Data URI
- Phishing web pages may be more elusive as they are passed around the Internet because phishing no longer requires web hosting of the page.
- We can create the phishing pages more easily. A personalized phishing web page can be created automatically, based on gathered information, and transmitted to one victim only. There is reason to believe that the data URI scheme can provide other unknown attack vectors.
-
It also defeats traditional defenses against phishing attacks, such as web filtering and reputation management, because victims don't need to communicate to an attack server to get phished.
Limitation of Data URI
- It is difficult to inject JavaScript in website.
- Internet Explorer doesn't support data URIs.
Conclusion
We learned a new way of presenting phishing web pages using a rather old, seldom used way to present web content. Using this procedure, there is no clear source of the phishing page and its content, which makes it difficult to trace, monitor the movement, or establish the origin of the web page. Also, we conclude that phishing no longer requires web hosting of the page, so phishing web pages may be more elusive passed around the Internet. They have no established anchor point in the Internet.
References
- http://www.klevjers.com/papers/phishing.pdf
- /spearphishing-a-new-weapon-in-cyber-terrorism/
- en.wikipedia.org/wiki/Phishing
- en.wikipedia.org/wiki/Data_URI_scheme.









