Phishing: A Very Dangerous Cyber Threat
Introduction
In recent years, phishing attacks have increased exponentially, targeting every sector of society. Despite the simplicity of the schema implemented, they have been successful in a majority of the cases.
RSA's October Online Fraud Report 2012 shows a large increase in phishing attacks, up 19% over the second half of 2011. The total loss for various organizations comes to $2.1 billion over the last 18 months. RSA estimates that there have been nearly 33,000 phishing attacks each month worldwide this year; countries such as Canada have registered an increase of 400 percent in the number of attacks. The firm revealed that it blocked around 200,000 phishing attacks during first half of 2012 and 60% of those attacks originated from U.S. servers. The U.S. is hit by 26% percent of the global volume of phishing attacks followed by U.K. at 46%.
Phishing simulations & training
These figures demonstrate the amplitude of the malicious phenomena and related damage, RSA reveals that the phishing attacks are exploiting new channels, such as social media and mobile platforms, due to their large use by on-line users. It has been estimated that these platforms are used daily by 50% of U.S. citizens, making them a privileged target. Let's consider also that the lack of knowledge about cyber threats and poor awareness about the risks related to an improper use of new media represent critical factors that make possible the spread of malicious contents through social networks and mobile devices. The report notes the link between phishing attacks and the diffusion of social network platforms, "According to a research study by Microsoft, phishing via social networks in early 2010 was only used in 8.3% of all attacks; by the end of 2011 that number stood at 84.5% of attacks delivered through social media." New fraud schemas take advantage of a fundamental aspect of the new social media, the trust. Infecting a node in these complex networks makes it possible to compromise entire groups of individuals, exploiting their mutual trust in contents and links they post.
Statistics
In September, RSA identified 35,440 phishing attacks launched worldwide, marking a 28% decrease from August. U.S. brands continued to be the most targeted by phishing, accounting for 29% of attack volume, followed by the U.K. and Australia.
U.S. is the top hosting country for phishing, with 77% of attacks. Poland, the U.K., Canada, and France combined for hosting just over 10% of attacks in September.
Companies from the United States are the most frequently targeted; eBay, Wells Fargo, PayPal, Bank of America, and J.P. Morgan Chase are the principal targets of cyber attacks. Financial institutions are privileged targets for cybercriminal gangs and state-sponsored attacks.
Similar data are published by McAfee in the "McAfee Threats Report: Third Quarter 2012." The financial sector is the most impacted by phishing activities, followed by "Online Auction."
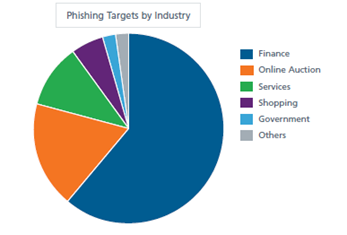
Figure 1 - Phishing Target by Industry (McAfee source)

Figure 2 - Phishing Target by Country (McAfee source)
In this scenario, it is quite difficult to distinguish private cybercriminals from state-sponsored hackers. Both are interested in exploiting private companies and government agencies to acquire sensitive information that will allow them to conduct further cyber attacks.
Consider the following hypothetical scenario: through a phishing attack, a victim gives attackers meaningful information that allows them to compromise the services he uses and to access reserved resources.
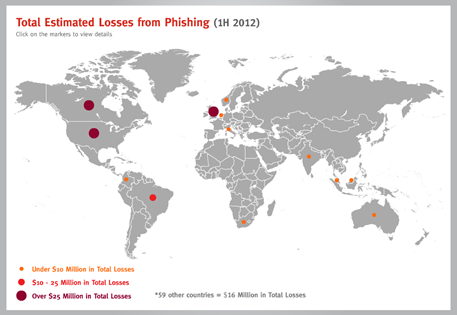
Figure 3 - Total Losses from Phishing in 1H 2012
Attack schemas
Phishing attacks use social engineering techniques mixed with technical tricks to fool the user and steal sensitive information and banking account credentials. Social engineering schemes are typically based on spoofed emails to lead users to visit infected websites designed to appear as legitimate ones. The websites are designed to lead customers to divulge financial data, such as account usernames, credit card numbers, passwords, and social security numbers.
The technical subterfuges are various and usually involve the use of malware specifically designed to steal credentials from victims while hiding evidence of the attack.
Phishing schemas can be more or less complicated. Many variants of the attack are described in the literature. Here are some of the most famous ones:
- User receives deceptive email messages that appear to be sent from a legitimate source, such as a business partner, that contain an explicit request to verify account information with a web service, without which the account will be suspended.
- Users are encouraged to visit fake websites that can be similar in appearance to legitimate sites. When a user visits the compromised website, malicious software can be downloaded automatically to his computer. Typically, the malware installed records the credentials used by the users to access to target services (e.g., banking), sending them to the command and control servers managed by the attackers.
- User receives messages from false charities that request direct donations in cash.
- Users of a social network platform receive messages, apparently from the platform, that contain a link leading them to a compromised website. The compromised website could download a malicious application onto the victim's machine to steal sensible information or it could offer a web form that appears to belong to a legitimate site that request authentication data. This form of phishing is also known as social phishing.
-
Users receive phone calls that claim to originate from legitimate organizations or private businesses and that ask him to dial a phone number because of problems with his bank accounts or other services. When the user calls a phone number that is managed by the attacker, it prompts said user to enter his account numbers and authentication code. Vishing (voice phishing) in many cases uses fake caller ID data to trick the user about the real origin of the call.
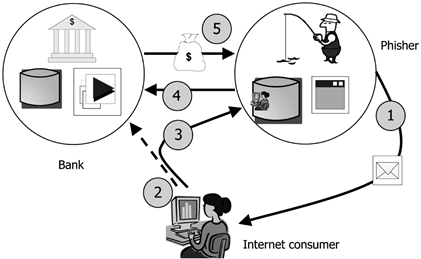
Figure 4 – Typical Phishing Attack Schema
Spear phishing attacks
A variant of the phishing attack against a restricted group of selected targets is called spear phishing. Usually it is an email-spoofing fraud attempt that hits a specific organization or company, seeking unauthorized access to sensitive data. Unlike a generic phishing attack, the spear phishing attack doesn't address a wide audience and is conducted by attackers that are more interested to intellectual property, trade secrets, or military information instead of financial gain. Typically spear phishing attacks are conducted by state-sponsored hackers and by hacktivists that search for reserved information for various reasons. Of course, it is not possible to totally exclude the fact that cybercriminals could be also interested in gaining access to confidential information to resell it to governments and private companies.
Exactly as in an email phishing campaign, phishing messages appear to come from a trusted origin, usually from someone in a position of authority at the victim's own company, a well-known company, business partners, or Web communities with a broad membership base, such as PayPal.
In general, spear phishing attacks are directed against specific targets on which attackers have a deep knowledge of users' internet experience; in fact, they know the websites visited by victims with major frequency and they try to compromise them to propagate the infection within a limited community.
Recent spear phishing attacks followed a consolidated trend observed for ordinary phishing, the exploiting of new communication channels such as social media and social networks.
Spear phishing attacks are conducted with the primary intent of stealing sensitive information, while ordinary phishing is conducted to realize financial frauds. It often causes serious security breaches that could seriously damage the victims.
According a survey conducted at the RSA Conference in 2010, 56% of respondents declared that they believed their organizations had been targeted by this type of attack. Following is a statement from the survey results:
"More than one third (34%) of respondents who reported experiencing a spear phishing attack in the past year (17% of all respondents) believe that such an attack resulted in the compromise of user login credentials (e.g., usernames/passwords) or unauthorized access to corporate IT systems."
The evolution of spear fishing, "watering hole" attacks
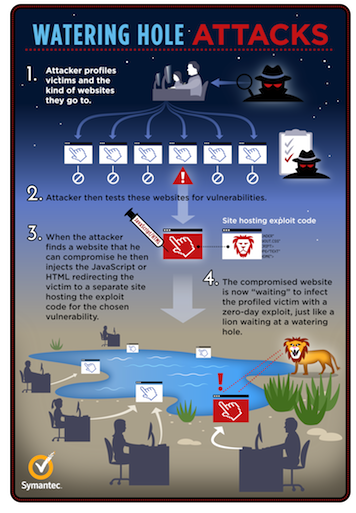
Spear phishing is mainly associated with targeted attacks. Usually users are infected by malware attached to an email or, in many cases, they are led to compromised websites that allow the download of a malicious agent. A new trend in spear phishing is the targeting of whole websites to infect a group on individuals that regularly visit it.
This type of attack is called a "watering hole" attack. The idea is that attackers wait for victims to visit the compromised site instead of inviting them with phishing messages.
Watering hole
In September of 2012, Symantec researchers published an analysis that demonstrates the link between a series of attacks on more than 30 companies and the cyber espionage attacks against Google three years ago in the so-called Operation Aurora.
The attacks are part of the cyber espionage campaign discovered by Symantec that has been named the "Elderwood Project.," These attacks have exploited zero-day vulnerabilities in many large-use software programs, including Internet Explorer and Adobe Flash Player.
The attacks were conducted using an unusual method to infect the victims with malware. This type has been named a "watering hole" attack. It consists of injecting malicious code onto the public Web pages of a site that the targets visit. The method of injection isn't new and it is commonly used by cyber criminals and hackers. The main difference between their use in cybercrime and in watering hole attacks is the choice of websites to compromise and use in the attacks. The attackers haven't indiscriminately compromised any website but they are focused on choosing websites within a particular sector to infect persons of interest who likely work in that same sector and are likely to therefore visit related websites. The Symantec report states:
"Targeting a specific website is much more difficult than merely locating websites that contain a vulnerability. The attacker has to research and probe for a weakness on the chosen website. Indeed, in watering hole attacks, the attackers may compromise a website months before they actually use it in an attack. Once compromised, the attackers periodically connect to the website to ensure that they still have access. This way, the attackers can infect a number of websites in one stroke, thus preserving the value of their zero-day exploit. They are even in a position to inspect the website logs to identify any potential victims of interest. This technique ensures that they obtain the maximum return for their valuable zero-day exploit."
Once a victim visits the compromised site, the software for which the zero-days have been designed will make it possible to infect the machine.
It is a common conviction that this type of attack is related to state-sponsored offensives. The choice of website target, the study of victim habits, and the adoption of an efficient exploit are steps that require meticulous researches and considerable skills on the part of the attackers. In recent months many "watering hole" attacks have been observed; the most famous have hit the Institute for National Security Studies website in Israel, the Nepalese government websites, and the Amnesty International U.K. website.
Figure 5 - Watering Hole Attack Schema (Symantec)
Whaling attack
Whaling is another evolution of phishing attacks that uses sophisticated social engineering techniques to steal confidential information, personal data, access credentials to restricted services/resources, and specifically information with relevant value from an economic and commercial perspective.
What distinguishes this category of phishing from others is the choice of targets: relevant executives of private business and government agencies. The word whaling is used, indicating that the target is a big fish to capture.
Whaling adopts the same methods of spear phishing attacks, but the scam email is designed to masquerade as a critical business email sent from a legitimate authority, typically from relevant executives of important organizations. Typically the content of the message sent is designed for upper management and reports some kind of fake company-wide concern or high confidential information.
Unfortunately relevant executives still continue to be victims of whaling attacks. In a 2008 FBI subpoena, it was reported that around 20,000 corporate CEOs were attacked with this technique. They received email that asked them to download a "special" browser add-on to view the entire subpoena document. The link proposed allowed the download of a key logger that secretly captured passwords. As a result, the compromised companies were victims of further cyber attacks with serious consequences.
Social phishing
A consolidated trend for phishing is the use of social network platforms, such as Facebook, Twitter, LinkedIn, etc., to obtain confidential information and gain access to personal data.
The schema has, like every other phishing technique, its foundation in a message containing a link to an infected site, but it is sent through the social network platforms.
To convince the user to click on the link, various social engineering techniques are used, offering attractive contents to the victim, such as discounts on desirable products or information about the status of their account, and instructions to follow immediately to avoid being blocked.
Clicking on the link, the user is redirected to a website that looks very similar to the legitimate pages that request to victim to enter username and password.
Once the credentials are obtained, the attacker could steal personal information from the victims, taking complete control of user profiles to conduct further attacks against other profiles or to spam phishing message on a larger scale.
Another schema of attack allows the download of malware to the victim's PC when he clicks on a link causing the impairment of the target.
The use of social networks is strategic for a social engineering attack because users usually trust user's profile, messages, and related content without paying the necessary attention. Typically, the messages ask the victims to watch a video, view a photo, or play a new game.
Of course the nature of the attacks could influence the choice of social network platform; platforms such as Facebook or Twitter are ideal for common phishing, while professional communities such as LinkedIn are ideal for spear phishing attacks.
Case Study: The Flame attack against the French government
French weekly news magazine L'Express reported that the offices of France's former president Sarkozy were hit by a cyber espionage campaign back in May 2012. A few days before the second round of the presidential election, which was won by Hollande, the president's office was infected by Flame malware. Among the compromised PCs was the one of Sarkozy's secretary general, Xavier Musca.
The use of Flame in a cyber attack against the French government is a demonstration of a cyber espionage campaign to steal sensitive information from top politicians of the country. Exponents of the French government declared:
"Hackers have not only managed to get to the heart of French political power, but they were able to search the computers of close advisers of Nicolas Sarkozy."
The attack against the president's office was of the spear phishing type that used popular social network Facebook to spread the malware. The attackers shared a link to an infected website that was a replica of the Elysee's intranet and used it to infect the machines and also to gather users' credentials. All the machines in part of the presidential network, including a number of Sarkozy's closest collaborators, were infected by the Flame agent.
Following is the schema of attack:
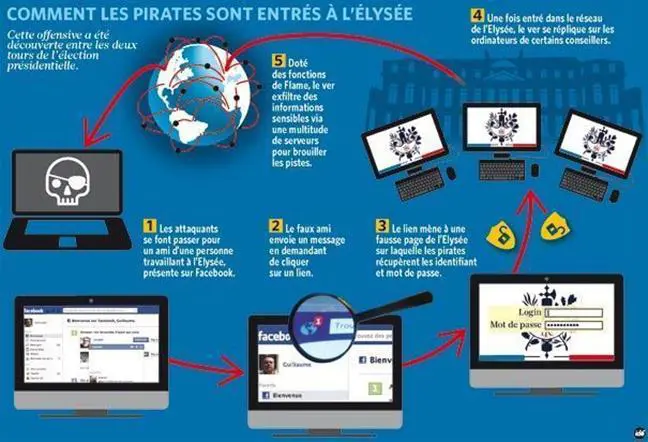
Figure 6 - Social phishing attack
Phishing "in the underground"
On aspect of major concern related to phishing is the simplicity of organizing an attack. On the Internet, it is quite simple to acquire all necessary resources for a phishing campaign.
To give an idea of which services and products are available for purchase and at what price, we can analyze the results of an interesting study published by the security company TrendMicro, "Russian Underground 101," that states:
"This research paper intends to provide a brief summary of the cybercriminal underground and shed light on the basic types of hacker activity in Russia. The bulk of the information in this paper was based on data gathered from online forums and services used by Russian cybercriminals."
In the underground is simple to acquire fake, exact copies of common programs and website packages to steal sensitive information from the victims.
The primary objective of using a fake is to trick a user into entering his user name and password or other kinds of confidential data into a form. Fakes are primary components of phishing attacks; the purpose is to trick users into giving away personal or confidential information. The report recognizes three type of phishing:
- Online
- Hybrid
Online phishing is based on using replicas of official sites hosted on similar-looking domain names or URLs. This technique is known as "site spoofing." When visiting fake sites, users type personal information into forms, believing they are in official sites. Prices for fakes are very cheap as demonstrated from reported, only 50 USD for one year prepaid phishing domain and 20 USD for a copy of a known site.
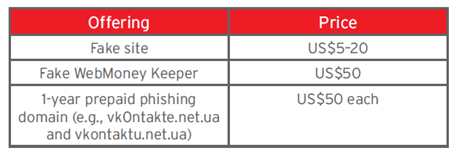
Figure 7 - Fake price list
The underground also offers other fundamental services to organize a phishing campaign such as customized malware, email spam services, and volume of traffic redirected on a fake domain.
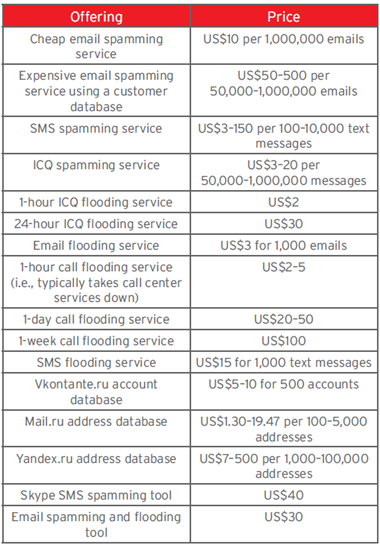
Figure 8 - Spamming and related service prices
This data demonstrates that the underground gives attackers all necessary infrastructures to conduct a phishing campaign. The prices for services and malicious agents are very low and it is simple to acquire them in total anonymity … too easy for cyber criminals.
How to prevent phishing
As illustrated in the article, there are many variants of phishing attacks, many of them are very sophisticated, and it's very hard for internet users to defend against them, such as the case of whaling attacks.
Here are a few basic rules to protect user's digital Identity from these types of attacks:
To help you protect yourself from phishing, we offer the following tips:
-
Be aware of spam and adopt special cautions for email that:
- requests confirmation for personal or financial information with high urgency.
- requests quick action by threatening user with frightening information.
-
is sent by unknown senders.
- Verify online accounts regularly to ensure that no unauthorized transactions have been made.
- Never divulge personal information via phone or on unsecure websites.
- Do not click on links, download files, or open email attachments from unknown senders.
- Be sure to make on-line transaction only on websites that use the https protocol. Look for a sign that indicate that the site is secure (e.g., a padlock on the address bar)
- Beware of phone phishing; never provide personal information over the phone if you receive a call.
- Beware of emails that ask the user to contact a specific phone number to update user's information as well.
- Never divulge personal or financial information via email.
- Beware of links to web forms that request personal information, even if the email appears to come from a legitimate source. Phishing websites are exact replicas of legitimate websites.
- Beware of pop-ups; never enter personal information in a pop-up screen or click on it.
- Adopt proper defense systems such as spam filters, anti-virus software, and a firewall, and keep all systems updated.
- For a social network user, it's fundamental to trust no one and reveal only a limited amount of information. Never post personal information, such as a vacation schedule and home photos. Never click on links and videos from unknown origin and never download uncertificated applications.
These suggestions are small and apparently simple tips that can help to prevent phishing attacks … let's follow them
Conclusions
The phenomenon of phishing is growing and the number of variations of techniques implemented demonstrates the high interest in these types of attacks by cyber crime. The phenomena must be carefully studied. Fundamental is training people in the secure use of computer tools, the cyber threat that is looming, and how the user can recognize threats in order to avoid serious problems.
References
http://www.cccindy.com/credit-counseling-blog/phishing-scams-lead-to-identity-theft/
http://nakedsecurity.sophos.com/2012/12/04/sophos-security-threat-report/
http://docs.apwg.org/reports/apwg_trends_report_q2_2012.pdf
http://www.antiphishing.org/resources/technical-whitepapers/
http://www.mcafee.com/us/resources/reports/rp-quarterly-threat-q2-2012.pdf
Phishing simulations & training