Phishing Attacks Using Public Data [Updated 2019]
1. Introduction
According to John McAfee, the developer of the first commercial anti-virus program, hacking a large corporation is "so easy even a grandma could do it". The vast amount of information which large corporations publish is undoubtedly one of the reasons for their significant vulnerability to phishing attacks.
The purpose of this article is to provide a list of publicly available information that is often used by hackers for conducting phishing attacks. Organizations willing to decrease the chance of phishing attacks need to reduce the publications containing such information.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
The list of publicly available information which can be used for conducting phishing attacks consists of six categories, namely, financial information (Section 2), information about software used by an organization (Section 3), information about websites used by an organization (Section 4), information about search engine keywords used by an organization (Section 5), and Whois information (Section 6). At the end of this article, conclusion remarks are given (Section 7).
2. Financial information
Many organizations often publish information about their bank accounts with the aim of allowing their clients and suppliers to make payments. Phishers may add this information to phishing messages. For example, a phisher may send a statement to an organization that there is a problem with organization's bank account. The phisher may use publicly available information from the website of victim's bank in order to create a letter head which looks like a genuine letter head. An example of a real phishing email, disguised as an official email from a real bank, is provided below.

In order to avoid falling victim to spoof bank emails, organizations should never send sensitive information through email. Furthermore, organizations are advised not to provide sensitive information by phone. This is because sometimes phishers invent complex phishing schemes which include not only phishing emails, but also phishing phone calls. For instance, phishers may send an email to a victim requesting the victim to call a phone number (purported to be the phone number of a legitimate bank) in order to confirm a bogus bank transaction. When the victim calls the phone number, the phisher will act as a bank representative and "help" the victim to cancel the transaction. In fact, the phisher will obtain valuable information, such as passwords necessary to enter into victim's online banking system.
Phishers may also use SMiShing, i.e., a phishing practice in which the offenders send out computer-generated SMS (cell phone) text to encourage potential victims to log onto a phishing website or call a phone number operated by a scammer.
A simple rule of thumb for avoiding problems related to spoof bank emails and SMiShing is to provide sensitive information only in person in the bank office.
3. Information about software used by an organization
Many organizations publish information about software used by them. Such information can be, for example, in the form of endorsements of software developers. Phishers can use the information about software used by an organization to send phishing emails purporting to be sent by a software developer. The emails often request the organization to install a software update which, in reality, is a malware collecting information about the victim.
For instance, in 2015, many organizations became victims of malicious emails that offered them an update to Windows 10 for free. The phishing emails look like emails coming from Microsoft. The subject of the emails is "Windows 10 Update for FREE" or "Get Your Windows 10 Update". When a victim installs the fake update, the victim quickly discovers that she/he has installed the ransomware "CTB-Locker" that gives the victim ninety-six hours to pay a ransom. Ransomware is a software that limits the functionality of a computer system without the consent of the user of that system. If the victim does not pay the ransom, victim's data will be permanently deleted. A screenshot of CTB-Locker can be seen below.
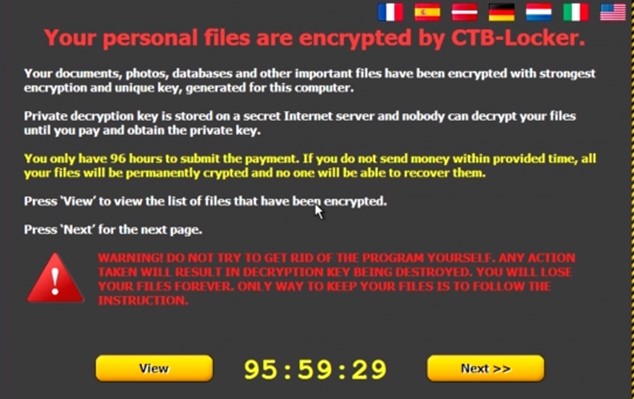
It should be pointed out that only a few anti-virus programs can detect CTB-Locker. According to a report published by Virus Total (a free virus, malware and URL online scanning service), only 5 from 54 anti-virus programs are able to detect the ransomware CTB-Locker.
4. Information about websites used by an organization
If phishers are aware that a potential victim visits certain legitimate websites, phishers may insert malicious content into those websites. The malicious content can install malware on victim's computer, redirect to websites containing malicious content, or redirect data to a phishing server.
In general, malicious content can be inserted into a website via two methods, namely, a cross-site scripting vulnerability and a SQL injection vulnerability. A cross-site scripting vulnerability is a programming flaw allowing the hacker to exploit the permission granted to a content from external sources (e.g., a blog, an auction, and a message in a discussion board). Cross-scripting is one of the most popular information security attacks. According to Symantec, 84% of all security vulnerabilities in 2007 were related to cross-scripting carried out on websites. SQL injection vulnerability refers to executing database commands on a remote server with the aim to cause information leakage.
5. Information about search engine keywords used by an organization
Phishers who know the search engine keywords of interest for an organization may create fake websites containing those keywords. After the search engines index the fake websites, phishers merely wait for potential victims to "discover" the phishing websites.
For example, in 2013, McAfee noted that hackers created a fake website to fool users into downloading a virus instead of a Java update. The victims found the phishing website after typing the keywords "Java Update" in the search engines. The keywords "Java Update" are especially attractive for phishers because Java (computer software developed by Sun Microsystems) is used by millions of users who often search for Java updates in Google and other search engines. Once detected, the fake Java update can be easily removed by uninstalling the update from the infected browsers and computers.
6. Whois information
The Internet Corporation of Assigned Names and Numbers (the organization responsible for domain management) obliges the registrars to publish certain information (also known as Whois information) about the registrants of domain names. Such information includes, for example, name and the address of a domain name owner. Since the Whois information is publicly available, phishers often use it for sending phishing messages to registrants of domain names.
By way of illustration, in 2015, a new phishing campaign targeted domain name owners. Phishers sent phishing emails to email addresses included in Whois information. The phishing emails were in the form of notices of domain name suspension, claiming that victims' domain names were suspended because of complaints regarding those domain names. The phishing emails looked credible because they contained Whois information, such as a valid domain name registration and recipient's full name. Below, one of the phishing emails is provided (in edited form). The phishing email impersonates the Australian registrar Melbourne IT.
Dear Sir/Madam,
The following domain names have been suspended for violation of the Melbourne IT Ltd Abuse Policy:
Domain Name: [Domain Name]
Registrar: Melbourne IT Ltd
Registrant Name [Registrant name as contained in the Whois information]
Multiple warnings were sent by Melbourne IT Ltd Spam and Abuse Department to give you an opportunity to address complaints we have received.
We did not receive a reply from you to these email warnings so we then attempted to contact you via telephone.
We had no choice but to suspend your domain name when you did not respond to our attempts to contact you.
Click here [Link to malicious content] and download a copy of complaints we have received.
Please contact us by email at mail to: abuse@melbourneit.com.au for additional information regarding this notification.
Sincerely,
Melbourne IT Ltd
Spam and Abuse Department
Abuse Department Hotline: 480-124-0101
Organizations can decrease the chance of phishing attacks by using a domain privacy service. This service is provided by a number of domain name registrars. If an organization uses such a service, the Whois information will contain no mention of the organization and its contact details. Instead, the Whois information will contain the name and the address of the company providing domain privacy service.
7. Conclusion
Phishing attacks are the most popular types of information security attacks. Microsoft Computer Safety Index Survey conducted in 2013 found that 15% of the surveyed consumers had been victims of phishing. According to the survey, the average loss which the victims suffer from phishing amounts to USD 158 per consumer. The survey polled 10,000 consumers located in 20 countries. In 2014, phishing numbers continued to be staggering. According to a report issued by Anti-Phishing Working Group (APWG), 128,378 unique phishing sites were reported to APWG in 2014.
This article has shown that the prevention of phishing requires not only the identification of phishing messages, but also a careful selection of the information which an organization intends to publish. Particular attention should be paid to financial information, Whois Information as well as information about the use of software, websites, and keywords.
By avoiding the publication of sensitive information on the Internet, an organization will not provide phishers with the opportunity to prepare a good "Lure". The "Lure" is an important component of a phishing attack which consists of an email message which appears to be from a legitimate institution. Without a good "Lure" the phishers will have a low or no chance to "catch" a victim.
In the near future, we can expect the appearance of a new machine-learning software which will automatically analyze the information published by an organization and will advise the organization on how to reduce phishing-related risks. At present, the use of machine-learning software for prevention of phishing attacks is merely an object of scientific investigations. For example, in 2014, a group of scientists published a scientific study demonstrating that a machine learning algorithm "can be used as an effective and efficient tool in detecting phishing websites and designating them as information security threats."
See Infosec IQ in action
References
- 'Aggressive Phishing Scam Targets Domain Owners', Lavasoft, 29th October 2015. Available at http://www.lavasoft.com/mylavasoft/company/blog/aggressive-phishing-scam-targets-domain-owners .
- Amiri, I.S., Akanbi, O.A., Fazeldehkordi, E., 'A Machine-Learning Approach to Phishing Detection and Defense', Syngress, 2014.
- Blankenship, J., 'Windows 10 Upgrade Spawns Phishing Campaign: Attackers using new Microsoft OS to distribute ransomware', 4th August 2015. Available at https://www.solutionary.com/resource-center/blog/2015/08/windows-10-upgrade-spawns-phishing-campaign/ .
- Chawki, M., Darwish, A., Ayoub Khan, M., Tyagi, S., 'Cybercrime, Digital Forensics and Jurisdiction', Springer.
- Davis, G., 'Malware Disguised as Java Update: Careful What You Download!', McAfee, 22 January, 2013. Available at https://blogs.mcafee.com/consumer/consumer-threat-notices/malware-disguised-as-java-update-careful-what-you-download/ .
- 'Domain name holders hit with personalized, malware-laden suspension notices', Help Net Security, 2015. Available at http://www.net-security.org/malware_news.php?id=3136 .
- Gilbert, D., 'Windows 10 free upgrade scam warning: Cybercriminals spread ransomware with fake Microsoft email', International Business Times, 4th August 2015. Available at http://www.ibtimes.co.uk/windows-10-free-upgrade-scam-warning-cybercriminals-spread-ransomware-fake-microsoft-email-1513971 .
- Hadnagy, C., Fincher, M., 'Phishing Dark Waters: The Offensive and Defensive Sides of Malicious Emails', John Wiley & Sons, 2015.
- Jakobsson, M., and Myers, S., 'Phishing and Countermeasures: Understanding the Increasing Problem of Electronic Identity Theft', Willy 2007.
- 'Scams and Swindles: Phishing, Spoofing, ID Theft, Nigerian Advance Schemes, Investment Frauds, False Sweethearts: How to Recognize and Avoid Financial Rip-offs in the Internet Age', Silver Lake Publishing, 2006.
- 'Symantec Internet Security Threat Report, Trends for July-December 07', Symantec, April 2008. Available at http://eval.symantec.com/mktginfo/enterprise/white_papers/b-whitepaper_exec_summary_internet_security_threat_report_xiii_04-2008.en-us.pdf .
- Sullivan, D., 'The Definitive Guide to Controlling Malware, Spyware, Phishing, and Spam', realtimepublishers.com, 2015.
- Thadani, R., 'Phishing Alert: Beware of Malicious Windows 10 Upgrade Emails', Quick Heal, 5 August 2015. Available at http://blogs.quickheal.com/wp/phishing-alert-beware-of-malicious-windows-10-upgrade-emails/ .
- Virus Total Report published on 3rd of February 2015. Available at https://www.virustotal.com/da/file/05ed142b50033e6b3b129433f6a7b98fa24ecf6e834e070db8567c5e881cc533/analysis/1422984539/ .
- Wacks, R., 'Privacy: A Very Short Introduction', OUP Oxford, 2015.
Co-Author
 Rasa Juzenaite works as a project manager in an IT legal consultancy firm in Belgium. She has a Master's degree in cultural studies with a focus on digital humanities, social media, and digitization. She is interested in the cultural aspects of the current digital environment.
Rasa Juzenaite works as a project manager in an IT legal consultancy firm in Belgium. She has a Master's degree in cultural studies with a focus on digital humanities, social media, and digitization. She is interested in the cultural aspects of the current digital environment.








