Phishing Attacks in the Manufacturing Industry
Introduction
In the second quarter of 2017, the manufacturing industry was the most targeted by cyber-attacks, with 24% of attacks globally, according to NNT Security report. According to Dark Reading, the automotive and chemical manufacturing companies were particularly targeted in2016. Despite a huge investment in cybersecurity, manufacturing companies seem to be unsure about how well they are protected against cyber-attack risks, according to Deloitte’s Center for Industry Insights. This is especially alarming, given that 95% of these attacks are successful phishing campaigns in the manufacturing sector, with 13% of the total phishing rate.
See Infosec IQ in action
Why Phish the Manufacturing Industry?
The manufacturing industry has some specifics that make it very attractive to cybercriminals. First, the financial gain is sizeable and frequent, especially now that some cybercriminal groups are becoming organized; many even pay taxes and salaries. Launching large-scale phishing campaigns allows them to collect data, such as bank account information, social security Ids, and credit/debit card information, or just make the victim pay an amount of money that goes to their bank account. In addition, other reasons behind phishing include collecting sensitive data to cause reputational harm to the manufacturer or releasing malicious software that causes the destruction of the company’s material and equipment. Industrial espionage is yet another reason and the most specific to the sector. Indeed, getting manufacturing secrets allows hackers plenty of possibilities, including asking for ransom or selling them to the competition, for instance. The problem with successful phishing is that an undetected breach in the security network can last over time, giving the hacker the freedom to make damages for long periods of time. Furthermore, these attacks may affect the manufacturer’s stakeholders, including suppliers and customers.
How Are Manufacturing Companies Phished?
According to NNT Security report, 58% of malware in the manufacturing industry is spread through web-based downloads, and it varied between Trojans and droppers in the second quarter of 2017. Reconnaissance, which includes methods of collecting vulnerabilities about the victim’s computer once accessed by the hacker, represented 33% of cyber-attacks targeting the sector. This reconnaissance targeted PHP applications (75%), DNS servers (14%), SNMP and ICMP protocols (7%), web servers (2%), WordPress (0.7%), and others.
To illustrate the way phishing attacks are conducted in the manufacturing sector, three different real examples are described below:
Seagate employees’ payroll phishing
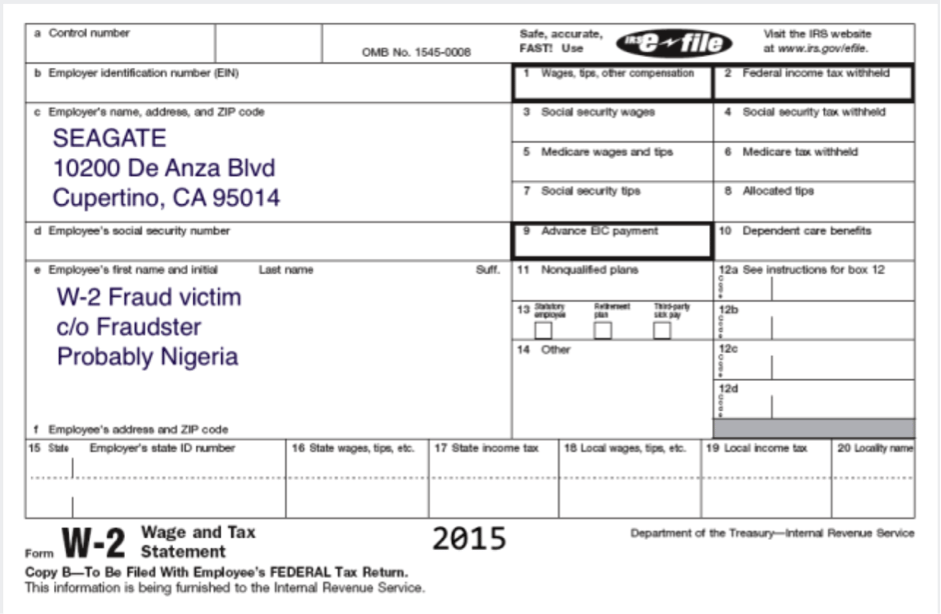
In 2015, an employee receiving a fake email supposedly from the company’s CEO was a victim of phishing and shared the income tax data of the storage device manufacturer’s employees with a third party, putting the U.S.-based employees at risk of tax fraud and identity theft. The employee received an email asking for the 2015 W-2 form of current and previous employees (figure 1). Despite the attempt of the company to protect its employees by offering a two-year credit protection, this was not enough, since it is suspected that the hackers would use the data to make false tax declarations. In this case, the cybercriminals were suspected to be located in Nigeria with a U.S.-based crime partner who cashes checks.
Figure 1. W-2 tax form illustrated by the lure used by the cybercriminals
Gilbane Building Company scam
In this case, the cybercriminal took the identity of Gilbane Building Company and made a reproduction of its website to lure a company that manufactured LED bulbs. The goal of the hacker was to get products delivered to his address without paying for them. He simulated a momentary lack of cash flow in Gilbane Building Company, making the company resort to an open account credit to supposedly pay its order. To be credible as much as possible, he sent the manufacturer the actual information about the company registration number, the data universal number (DUN), the taxpayer identification number (TIN), and other authentic buyer information and asked to apply for the credit from Sinosure Insurance Company. In the end, the trick did not work, as the company’s management discovered from the beginning the fake email address and domain which was www.gilbanecos.com instead of www.gilbaneco.com and the lack of credibility to the manufacturer’s top management (Figures 2 and 3).
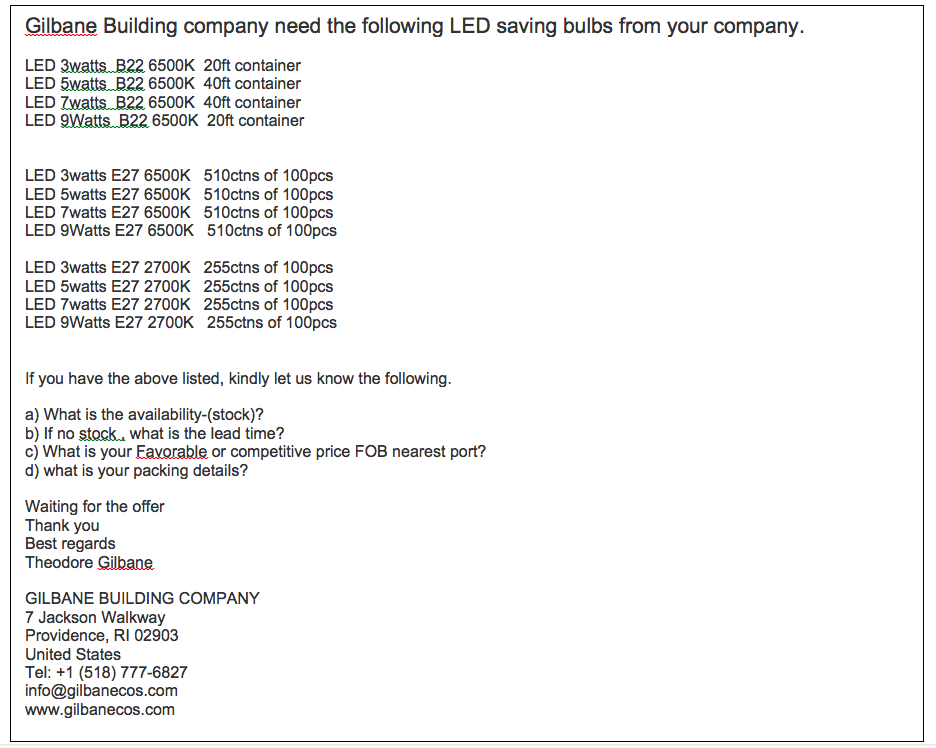 Figure 2. First email sent by the hacker
Figure 2. First email sent by the hacker
 Figure 3. Attempt to convince the manufacturer about the payment via credit
Figure 3. Attempt to convince the manufacturer about the payment via credit
Mattel CEO fraud
This last case is an example of what is known as CEO fraud, in which the CEO’s email address is hacked for identity theft purpose. The toy manufacturer lost $3 million when an employee received a fake email, apparently from his new CEO’s email address, asking him to transfer this amount to a new stakeholder while, in fact, the money went to the hacker’s account.
Strategies for Preventing Phishing in the Manufacturing Industry
When it comes to phishing, communication is the key feature of preventing such attacks.
Several types of communication are involved:
- Education
The InfoSec Institute offers a cost-effective program that allows you to raise awareness among your employees, who are the key role players to arm against phishing because they are the first line of defense. This program is called Infosec IQ, which is composed of two complementary and interchangeable modules. The first module is AwareEd, a tool designed to train your employees while having fun. Through AwareEd, they learn by getting involved in interactive content, such as videos and games. This tool gives you the ability to choose the appropriate material, based on your audience, their skills, and their position in the company, and to track how well the employees are learning. This allows your employees to enjoy learning fast and effectively. The second module is PhishSim, which lets them learn by doing. Indeed, it is a tool with which you can build realistic phishing emails and campaigns and send them to your employees whenever you want to test their awareness. If an employee makes the mistake of opening the link or the attachment embedded in the fake phishing email, he or she is redirected to a link where a video is played to explain his or her mistake and how best one can prevent this to happen again.
In addition to employees’ education, it is important for the company to have an adequate and operational internal reporting procedure in place, which allows fast reporting if a phishing attack is suspected, so that risk is mitigated quickly and effectively.
External reporting relies on communicating phishing attempts to the competent authorities, as a crime is probably involved, and also to the registrar of Internet domains when a link is embedded in the email so that it is consequently blocked and damages limited.
Conclusion
The manufacturing industry is an extremely attractive target for phishing attacks. Therefore, employees should stay aware and should be educated in a sustainable way to be protected against phishing. AwareEd and PhishSim are cost-effective and efficient solutions proposed by the InfoSec Institute to do so.
References
https://digitalguardian.com/blog/2017-data-breach-report-finds-phishing-email-attacks-still-potent
https://certifid.com/business-email-compromise-how-big-is-that-phish/
https://www.manufacturer.lighting/club/31/
https://www.helpnetsecurity.com/2017/08/09/attacks-manufacturing-industry-rise/
http://whatis.techtarget.com/definition/active-reconnaissance
http://iiot-world.com/cybersecurity/how-phishing-is-affecting-manufacturing-and-other-industries/
Phishing simulations & training