Phishing Attacks in the Healthcare Industry
Healthcare Phishing Attacks
Phishing Targets by Industry:
- Financial Phishing
- Government and Military Phishing
- Healthcare Phishing
- Retail Phishing
- Phishing Individuals
Despite how simple they often are, phishing attacks continue to become a bigger and bigger threat to companies across all industries in the digital age. This is especially true for those in the healthcare field and it’s not hard to see why. If information is power, then information about people’s health histories, their personal identification information, and, of course, their financial data, is about as powerful as it gets. Worse yet, this trend isn’t showing any signs of slowing down, much less reversing.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
It’s vital that not just those in the healthcare industry, but everyone—considering any one of us could become victims—understands what this threat entails and what healthcare companies can do to start fighting back.
Why Target Phishing at Healthcare Organizations?
Hackers pick their targets for a few reasons. Sometimes, they’re actually working for a rival government. Currently, espionage probably involves more keystrokes and mouse clicks than secret agents and physical infiltrations.
You’ve probably also read about all the different forms of hacking that have been done by political activists who often hope to expose corruption in governments, politicians or corporations.
The motive for hacking healthcare organizations, though, is one of the simplest and easiest to understand: money. Globally, the entire healthcare industry is worth roughly a trillion dollars. This is when you factor in everything from pharmaceuticals to digital products and more. So it’s not hard to understand why phishing specialists would want to cast all their lines in that particular body of water.
Put another way, as we mentioned at the beginning, phishing is a fairly simple type of cyber-attack. It’s little more than manipulation: you simply trick someone into thinking you’re someone you’re not and, once you do, they’ll basically follow your every command.
Usually, there is no code writing, no need to trick firewalls or leverage hacking software for hours or days at a time until a password breaks. You don’t have to worry that an advanced form of digital security is on patrol to catch your digital footprints.
In this way, phishing in the healthcare industry isn’t any harder than phishing in the pet care industry. It takes the same trick; the difference is just that, when you phish the former, you could end up with hundreds of millions of dollars on your line.
Medical Identity Theft Costs Thousands of Dollars
These attackers aren’t taking money directly out of your accounts. A little later, though, we’ll show you how they often take hundreds of thousands and even millions from big healthcare companies.
However, they can still damage your bank account substantially by stealing your personal information and then using it to spend your money.
A Ponemon study that was done last year reported that victims of this kind of identity theft spend, on average, $13,500 to reimburse their healthcare provider after fraudulent claims have been made, restore their credit and correct inaccuracies that are now in their healthcare records.
In case you think that last problem would be the least of your worries—perhaps just a minor inconvenience—prepare for a very rude awakening: those inaccuracies could actually kill you.
Healthcare Industry Phishing Attacks Can Actually Be Fatal
So, aside from money, keep in mind the information that healthcare companies keep in their databases. A lot of us would flinch at the idea of a complete stranger having access to that private, sensitive information. We may have told our doctors things almost no one else knows.
Fortunately, that’s not really the information these hackers are after.
Unfortunately, it’s actually a lot worse: these attacks could cost people their lives.
For example, a cyber-criminal could use a phishing attack to gain access to a healthcare company’s records, at which point they steal your social security number and health insurance information so that they can get free medical care.
If it’s something serious, like they need surgery, they’ll most likely be asked a number of questions about things like any allergies they have to medication and their blood type. That information can then end up in your permanent file. Because it may differ greatly from your own needs, the next time you require medical attention, you could be in a lot of very serious—even fatal—trouble.
Healthcare Data Is Perfect for Blackmail
As we mentioned earlier, most of us would prefer to keep our healthcare information private. Many of us would even be quite embarrassed if our private data was released. For this reason, some criminals may use phishing attacks to get their hands on information they can then use to blackmail their victims.
Sadly, most targets probably don’t come forward for fear of further exposure. Therefore, it’s impossible to know just how often this happens.
How Are Healthcare Organizations Targeted?
Healthcare organizations can be a targeted a couple of different ways. It all depends on the result the cyber-criminals are hoping for. Two of the most common versions are CEO phishing and using fake websites.
CEO Phishing: The Ultimate Authority Ruse
One very common form of phishing is known as CEO phishing. Remember when we said earlier that phishing schemes involve impersonating an authority figure? Well, CEO phishing may be the best example of this. After all, what greater authority is there in a company than its CEO?
A company called Ameriforge Group Inc. was on the receiving end of a CEO phishing attack back in 2014 that cost them close to half-a-million dollars. To make a long story short, the company’s accountant received an email from someone pretending to be their CEO. They instructed the accountant to work with a lawyer, “Steven Shapiro”, from another company on a highly sensitive matter. Amongst other things, this matter would require the accountant to wire some $480,000 to a bank account in China.
Sure enough, after the CEO’s email, the accountant was phoned and emailed by the alleged attorney. The accountant did as he was told and wired the funds. It was only after a follow-up email asked for another $18 million that the accountant became suspicious.
By then, though, it was too late. The money had been taken; the bank account in China had been zeroed out; the criminals were gone without a trace.
To be sure, this kind of attack takes a bit more work. The accountant was no entry-level employee. He was tricked because the hackers knew the ins and outs of the company. They understood how to talk like a high-powered attorney who knew what he was doing and how to act like a CEO who had a serious business matter that had to be handled.
Magnolia Health Corporation Gets Hit by CEO Phishing
However, far less sophisticated attacks often hit their mark, too, and the results are still incredibly devastating.
Magnolia Health Corporation was an example of this back in February, when an employee received an email that was, again, supposedly from the CEO. It asked for a spreadsheet that was filled out with current employees’ Social Security numbers, addresses, salaries, and other highly-sensitive, personal information.
While there aren’t a ton of details about the attack, it would seem that the malicious party did little more than get their hands on a company email and then mirrored the format and email address used. It seems like such a small thing, but it’s this kind of brazen confidence that short circuits people’s skepticism moments before they become victims.
A Second Attack Three Days Later
An identical attack on St. Joseph's Healthcare System that happened just three days later is why so many experts are calling phishing attacks an epidemic. Again, there aren’t a lot of details at the moment, but it began with another email to an employee that came from a trusted source. It asked the staffer for earnings data on some 5,000 employees’ earnings data for the 2015/2016 financial year.
While the employee is said to have caught their own mistake, the problem is they had already hit “send.” St. Joseph's Healthcare System had to let their employees know about the attack and gave them credit monitoring services for a year.
To ensure that we really drive this point home, let’s take a look at some stunning examples that show how dangerous phishing has become.
Website Phishing
The other common form of phishing we’re seeing in the healthcare industry begins with the scammer starting a website. True to the anatomy of a phishing attack, this website is meant to look authoritative so no one thinks twice about trusting it.
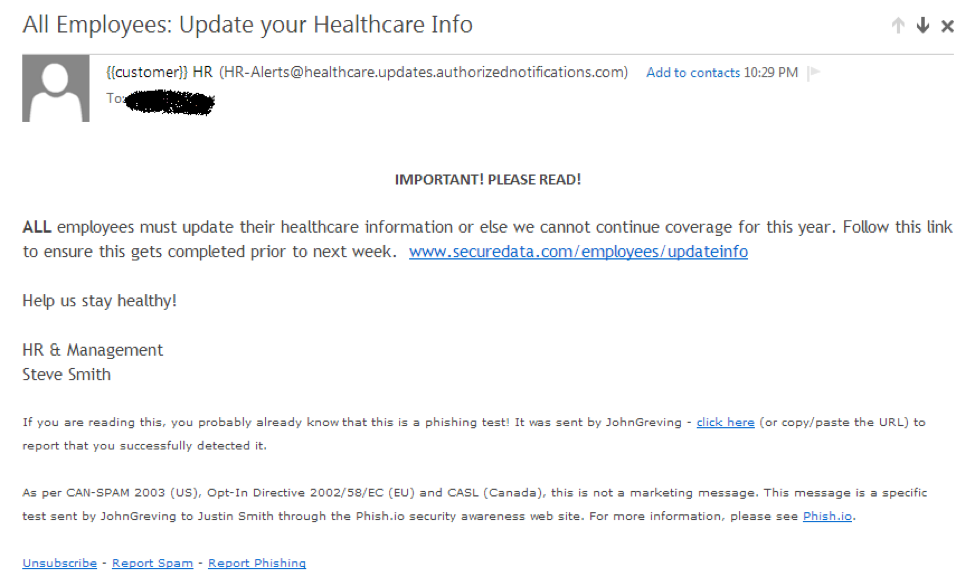
This is what a phishing email may look like. Notice the sense of immediacy and a URL the target is being told to click. It’s even signed by an authority figure.
Dekalb Health Medical Group suffered an attack from this kind of site in March. It began with an attack on a server they were using. Eventually, this attack rewarded the culprits with the records of over 1,300 patients. This included information such as their names, addresses, Social Security numbers, and credit card numbers.
[cta id="1470254826411" post="35736"]
They didn’t stop there, though. Several of the compromised victims were then contacted via email and directed to the scam site. It had been made to look just like the Dekalb Health charity site. The criminals took things a step further, though, and hacked the actual Dekalb Health site so that it would link to the fake charity website instead of the real one.
While this type of phishing attack definitely takes some real technical chops—the criminals needed to go after a server first and build a site—it still worked because the victims went along with what they were being told by a supposed authority.
A Problem That’s Only Getting Worse
Plenty of what we just covered should definitely worry you. As long as they lack a conscience, just about anyone can launch a phishing attack. You’ve seen how easy it can be—there’s generally no real “hacking” involved—and the upshot could easily be hundreds of thousands of dollars.
Well, even scarier is that it’s only going to get worse. In 2013, hackers accessed roughly a million patients’ records. By 2014, that number hit 100 million! While not all of those were phishing attacks, it’s pretty easy to predict that this particular type of method was well represented.
Eight of the 10 largest attacks to have ever hit healthcare companies up to that point happened in 2014 too, which speaks to the fact that this industry is definitely getting a lot of attention from cyber-criminals.
We mentioned that these particular businesses often get hit because they have two very tempting kinds of treasure in large amounts: money and data.
However, experts are starting to think another reason may simply be that employees at these companies already have their hands full. The companies as a whole are focused on juggling so many priorities that even something as important as cyber-security can fall by the wayside. Although these businesses may not have figured out how big their problem is quite yet, cyber-criminals seem to be well aware.
As far back as 2011, criminals were going after healthcare companies. Two of the biggest volleys hit Science Applications International Corporation and IBM. They affected 4.9 million and 1.9 million individuals, respectively.
In 2015, the healthcare industry was the second biggest victim of data breaches in the country. With companies like Boston’s Beth Israel Deaconess reporting that they get hacked every seven seconds, this definitely isn’t a problem that’s slowing down.
Oh and, if you’re curious about what some of those medical records get used for, consider that when Beth Israel Deaconess had 2,000 patient x-rays stolen in 2011, they were most likely sold to Chinese nationals who then use them to pass health exams and gain travel visas.
It should become clear by now that phishing just isn’t going away. The activity is simply too financially rewarding and difficult to root out. All you can do is use common sense and keep a healthy sense of skepticism whenever you’re online.
References
http://www.statista.com/statistics/266161/websites-most-affected-by-phishing/
http://www.pbs.org/newshour/updates/has-health-care-hacking-become-an-epidemic/
http://www.idtheftcenter.org/ITRC-Surveys-Studies/2015databreaches.html
https://info.wombatsecurity.com/blog/the-latest-in-phishing-march-2016
http://www.nbcnews.com/tech/tech-news/bill-gates-says-u-s-needs-limits-covert-email-searches-n558166
http://krebsonsecurity.com/2016/01/firm-sues-cyber-insurer-over-480k-loss/
http://www.ft.com/intl/cms/s/2/f3cbda3e-a027-11e5-8613-08e211ea5317.html#axzz46QNFe6Kf
http://www.nuemd.com/news/2016/03/02/2-us-healthcare-companies-targeted-phishing-scams

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.