Phishing Attacks in the Hospitality Industry
Introduction
The hospitality industry has been consistently hit with cyberattacks year after year. Fast food chains, large retailers, and every major hotel chain have been victims. As with most industries, the hospitality industry has also seen major changes in their processes. Over the past five years, they have veered towards a completely digital way of operating. This increases efficiency, which is the backbone of the hospitality industry. There have been increases in online travel companies, online ordering, online delivery services, etc. They are expected to provide their customers with quick and efficient service. We expect it. But, this, of course, increases the landscape of potential attacks. In 2016, over 1000 Wendy’s restaurants were hit with a scam that resulted in massive credit card theft. In 2017, every major hotel chain was hit with a cyber-attack. These examples prove the hospitality industry needs protection from phishing attempts as well.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
Why Phish the Hospitality Industry?
Businesses in the hospitality industry process lots of credit card information as well as consumer data. Restaurants, retail stores, and entertainment are all areas where consumerism is enjoyed by everyone. Patrons in this industry have varying levels of economic value, so gaining access to their information is desired by cybercriminals. The best way to gain access to this information is by attacking consumer-oriented businesses. Having an employee of one of these places fall for a phishing attempt opens the door to this access.
How the Hospitality Industry Is Phished
Members of the hospitality industry use social media to advertise and market their business. It has been shown that online advertisement is the way to advertise now. With many commercial-less options and streaming music services, the modern consumer may never see a television or hear a radio ad Phishing attempts against this industry could use social media as a way to trick employees into clicking malicious links.
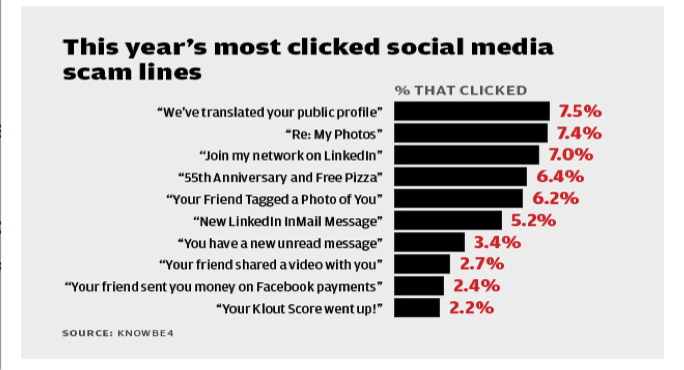
According to CSO online and KnowBE4, the following were the most used social media based phishing attempts in 2016:
Employees in this industry may not receive as much cybersecurity training. In hospitality, time is money, and many of the owners of these companies want their employees working, not sitting through a phishing class. Scammers may also use spam emails that are centered on company benefits.
Hotel employees are focused minute to minute on immediate emergencies, and may not feel they have time to read the fine print of every email that comes their way. Infosec IQ will help them remember
Steps for Preventing Hospitality Industry Phishing
Preventing phishing attempts requires similar steps in every industry. What makes preventing phishing the hospitality industry so important is their access to so much consumer information. The best way to protect against phishing attempts is through education, testing, and reporting.
Education and Training
Many of companies in the hospitality industry do not want their employees sitting through a phishing tutorial given by the IT team. Hackers have gained a lot of momentum and maturity over the years and this trend in cyber-crime is only expected to continue to grow as a threat. With the increased use of social media tools and people volunteering to post details about their personal information, hackers can compile information to better form phishing emails. There are also tools available on the dark web that make creating a phishing email easy, even for a novice user.
With such a large potential for attacks, educating employees, or any system users, is important to maintaining the integrity of an organizations digital assets and network.
It is important that organizations educate their employees on the types of emails they will send. Since hackers use things like open enrollment and potential account issues to try and lure victims, employees should be shown what these types of emails actually look like, or whether they are ever sent at all.
InfoSec Institute offers a myriad of self-paced tutorials and other training tools, all of which are available to InfoSec account holders, including those with free membership plans. The training provides overviews of phishing email attempts to help learners recognize suspicious emails, and to discover what to do when a questionable email is received. You can view InfoSec’s tutorials and sign up for an account here.
Testing and Evaluation
Infosec’s Infosec IQ is an ideal mechanism for performing just such an assessment.
With the PhishSim tools, emails similar to those that may be used by these criminals can be created and sent to anyone who interacts within a network. This helps to determine how they might respond to a real threat.
With an extensive collection of existing templates, cloning and then modifying an existing one is probably the quickest and easiest way for a user to start a phish testing campaign. Email templates may be edited as needed.
Whether you create a fake phishing e-mail of your own or adapt one of the templates, you can send these simulated emails directly from PhishSim. Email addresses of those being tested may be directly imported from all your employee e-mails, and different campaigns with various false-phishing emails and recipient lists can be managed completely within PhishSim with the Campaigns Manager. Once your employee has fallen for the fake-phishing attack, they will be redirected to our AwareEd service, where they will be asked to watch one or more short, interactive videos that will help them understand what to watch for in a phishing attack, and how to work safer.
AwareEd’s interactive videos are short, interactive, and entertaining, allowing users to learn the rudiments of security awareness without taking much time out of their busy day
Reporting
Organizations should provide their employees with a method to report phishing attempts. Many firms in the hospitality industry do provide an email address for that purpose. All members of the organization should be apprised of the email address and the procedures for sending the suspicious email.
It should be stressed to employees how important reporting is. This is the information used to create signatures for security devices and tools. Homeland Security, the FBI, Interpol, and other federal and state agencies maintain databases containing all of the information relating to these different attempts including suspects’ names, metadata, affiliate organizations and other relevant information. This information is often shared with other law enforcement agencies and some private organizations to help prevent and prosecute cyber-crime.
Conclusion
Phishing attempts show no signs of slowing. IT security professionals must remain vigilant in monitoring, training, testing, and reporting these attacks and novice employees need to take cybersecurity-related training they receive serious. Failure to thwart phishing activities could cost an IT worker his or her job, jeopardize a firm’s reputation and financial standing, or even lead to the demise of an organization.
InfoSec can assist with training staff to counter phishing and other cyberthreats. InfoSec’s PhishSim tool, tutorials, and advanced training provide a system for combating the threat of phishing. Click here to create your account and get started in helping to fight against phishing.
References

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
http://blog.morphisec.com/hospitality-industry-needs-shelter-from-cyber-threats