Phishing Attacks in the Consulting Industry
Introduction
The consulting industry, a network of professionals that work in an advisory capacity for businesses or individuals, is a tempting target for phishing scams. This is because, if they can get access, they may be able to pose as the consulting firm and attack the companies they work for in a highly convincing fashion. Attacks on the consulting firms are usually carefully targeted, a tactic known as “spear phishing,” which focuses on impersonating specific employees, targeting individuals, or both.
Spear phishing takes a bit more effort, but the rewards are easily worth it. Hackers make the effort to look for social media accounts of employees or executives (such as on LinkedIN) and use information to gain confidence of co-workers. They may then ask for passwords or give co-workers files containing viruses that further their scam.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
Why Target the Consulting Industry?
Consultants come in many varieties, from IT to brand image, and are often employed by successful companies. Generally speaking, a successful consulting firm or individual consultant could have the private emails of top executives from many different companies, including those in the Fortune 500. Gaining access would allow the hacker to appear as a trusted source.
This is part of a larger attack, which the FBI calls business email compromise (BEC); it starts with a spear phishing attack that lets the hackers into a company’s system, including servers and/or email. They may simply observe for a while, gleaning important information like travel schedules or payment processes.
Then, when the thieves know the target is away from the office, posing as the consultant, they may ask the finance department of their clients for fees to be wired to an overseas bank account. According to the FBI, there has been a 1300% increase in BEC scams since 2015, with losses totalling over $3 billion.
How is the Consulting Industry Phished?
The consulting industry, like most industries, first falls victim primarily through email. In fact, it is estimated that some 97% of scams start with a phishing email. This email could appear to be from a client or from IT—it could even appear to be a message from a friend or family member. The main thing is that the message that seems to be legit is actually a scam and the person or persons behind it are out to cause damage.
Consultants may be tricked by hackers who have hijacked companies or applications they use regularly. In May 2017, DocuSign, an electronic signature company, was hacked and a segment of their users was sent a malicious email attachment. (DocuSign insisted that they breached a “non-core” system and that there were no reports of infection.)
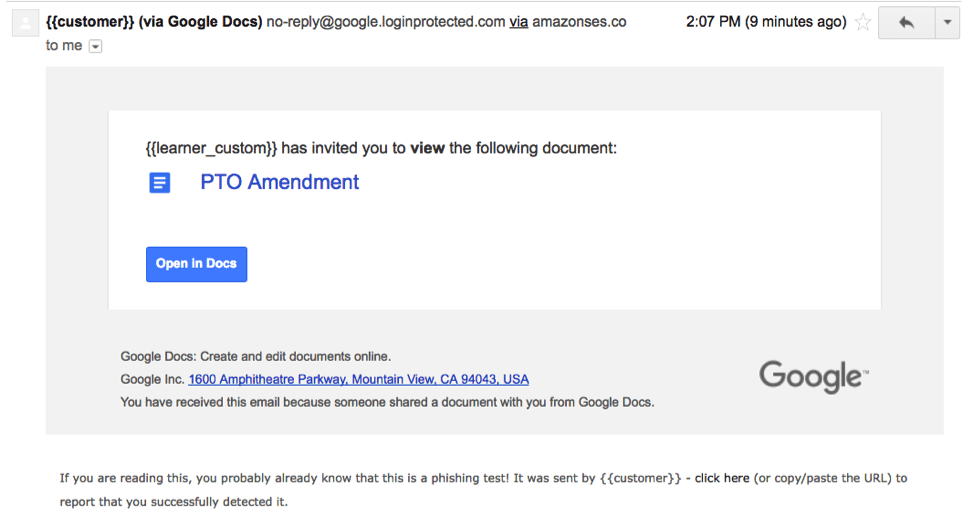
In May 2017, a worm was able to penetrate the Gmail system. The worm sent out emails to people in the user’s contact list along with an attachment that appeared to be a link to a Google Doc. Those that clicked were taken to a real Google page where they were asked to give permission to the pseudo app to manage their account.
This Google Doc template can be fully customized with the name and address of your “target.” Only the disclaimer at the bottom gives away the game. But will they read the fine print?
The ruse was quickly discovered (within 10 minutes) and 0.1 of Google accounts were hacked but that still means one million users were affected.
Deloitte Hit with Massive Breach
In September 2017, it was revealed that one of the biggest consulting firms in the world, Deloitte, was successfully attacked by unknown hackers. The thieves were able to steal confidential email addresses of clients and terabytes of intellectual property.
It turns out that the hackers may have been in there for a full year and were able to access so much data because the company didn’t use two-factor authentication and may have had a single password for their server network.
Even more embarrassing is that Deloitte is also in the cybersecurity consulting business.
Be Prepared – Be Vigilant
How vulnerable are you to phishing scams? Is your staff trained to recognize a phishing email? Have you run any real-world drills?
These crucial questions can be asked (and answered) by joining InfoSec Institute’s SecurityIQ platform. The site consists of two main sections, AwareEd and PhishSIM.
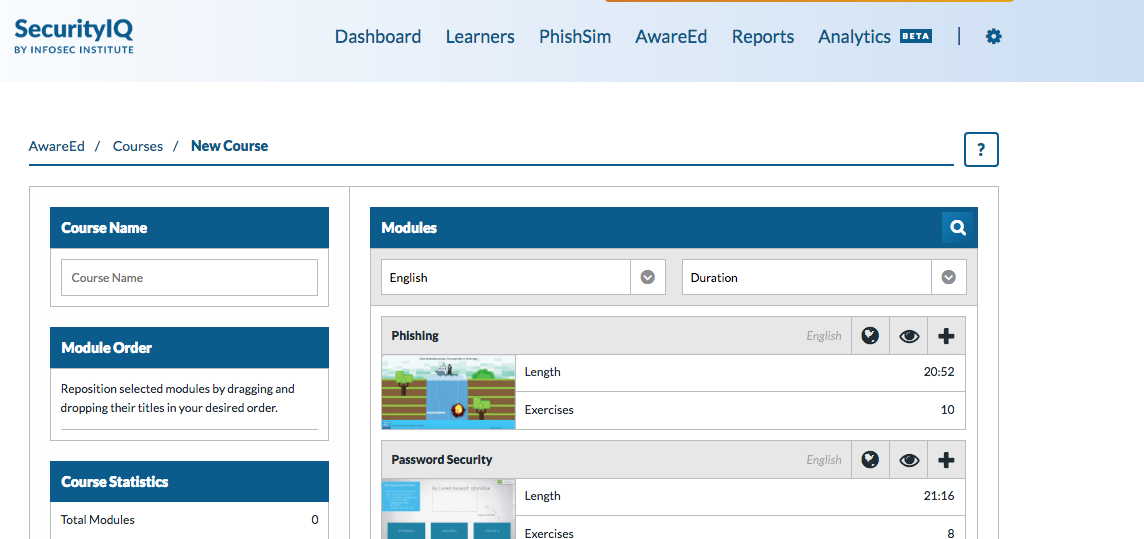
AwareEd focuses on educating users to the dangers of phishing scams and teaches best practices for avoiding them. Administrators can create an educational program called a “course” and fill it with “modules,” which are short lessons that include video and exercises. There is a default course, as well as those tailored for specific departments such as management and IT. They contain modules on topics such as password safety, malware, and mobile security.
Some of the hands-on tutorials available in the AwareEd educational module section
You can use these courses as is or create a new one, even uploading your own materials. Once set up, a campaign email is sent out to all employees that contains a link to the course. The admin can monitor everyone’s progress in the dashboard and select those that do not pass for further training.
PhishSim focuses on testing the vigilance of all personnel by sending out phony phishing emails. The program comes with a variety of templates, including fake corporate communications as well as those designed to look like they are from Google or the U.S. government.
PhishSim also includes fake data entry pages that can be linked to the phishing emails to request usernames and passwords. These mimic web pages like those from Chase Bank or Outlook.
To create a campaign in PhishSim, the administrator selects (or creates) a series of emails and data entry pages and assembles it into a battery; then the admin imports the email addresses people they would like to test. Over a set period of time, the PhishSIM sends the batteries in the campaign and monitors the results.
If an employee clicks the link and/or fills out the data entry form, they are taken to an education page, which will inform them of their error. (This page is completely customizable.) From there, they can be required to take courses in AwareEd.
Another important tool in PhishSim is the quarantine. This allows your staff to flag and isolate real phishing emails that they may find in their inbox. Once quarantined, your incident response team can safely examine it.
Because the nature of threats is constantly evolving, so is SecurityIQ. New modules, templates, and features are continually being added. Right now, InfoSec Institute is offering a free 30-day premium membership, which includes unlimited use of all its features.
Don’t let your firm get phished - join SecurityIQ today!
Resources
https://www.nbcnews.com/tech/security/massive-phishing-attack-targets-millions-gmail-users-n754501
https://www.fbi.gov/news/stories/business-e-mail-compromise-on-the-rise
https://www.linkedin.com/pulse/spear-phishing-when-law-firm-employees-get-targeted-galaad-delval/
Phishing simulations & training
https://www.symantec.com/connect/blogs/scammers-pose-company-execs-wire-transfer-spam-campaign