Keeping your Security Awareness Training up to Date
The more you perform phishing simulation training your users become more and more security-conscious and thereby more aware of the basic phishing symptoms such as spoofed domains, requests for passwords, and unsolicited requests for financial information. This is without doubt a positive byproduct of active training, but keep mind, the real-world attackers are aware that users are becoming better informed as well. A training routine is definitely a must-have, but a stale training plan is only slightly better than no plan at all.
It is fairly simple to use social media to find which companies people work for as well as their personal email address. If your company allows personal webmail, uses BYOD, or issues take-home laptops; then phish testing, as part of awareness-in-depth is paramount. When attackers target a specific company then you can also bet they are targeting that company’s staff. Initial exploitation does not always mean immediate access to the target network -- compromising even an employee’s personal email would allow the intruder to view calendars, monitor emails, and exfil potentially sensitive information.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
The images below use two training accounts that we own: y.secure (attacker) and tracysimpson372 (victim).
The scenario: Tracy works for ImportantCompany.com, and an attacker has recently begun targeting ImportantCompany.com for whatever reason. The Company has a fairly secure perimeter, and an expensively sophisticated spam filter and sandbox. Through intelligence gathering, the attacker has found personal email addresses for several Important Company users – one of them being tracysimpson372@yahoo.com. The attacker only wants to monitor employees for the time being and not set off any alarms on the corporate side. In a matter of minutes, and just a few steps, the attacker spoofs a Yahoo corporate account and launches the attack.
Attack Account Created
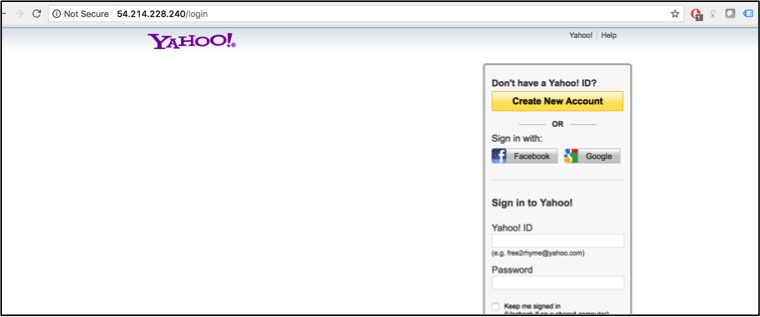
Fake Login Page and Keylogger Created
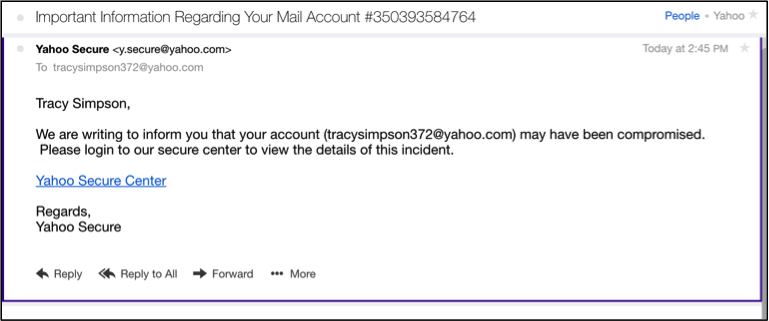
Phishing Message Created
Once Tracy responds to the spoofed email and logs in to the spoofed site, the attacker steals Tracy’s user name and password in clear text. Since Tracy is not using multi-factor authentication, the bad guy can now login to and monitor Tracy’s email, or any other resource that she uses those credentials for.
This same attack could be used against companies that have login pages such as OWA or VPN, but going after individual users is much quieter. If ImportantCompany.com allows webmail in and out of the corporate network, then it is possible that the intruder will find some company related data in Tracy’s personal email.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
To help protect yourself against these attacks there are two keys: 1. Do not allow personal webmail in or out of your network. 2. Do not implement remote access to the corporate environment without multifactor authentication. Furthermore, users should be trained and encouraged to enable multifactor authentication on their personal accounts. Although this cannot be mandated, implementing examples such as this into you awareness-in-depth program could possibly motivate some users to apply multifactor on their own.