Meeting Invite Phishing Attacks- Templates and Examples
It is possible that your organization can be phished by avenues other than email.
Social-engineering attacks are part technical but mostly psychological and the more creative the attacker, the better the probability of a successful the attack.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
A delivery method that isn’t typical but is growing in popularity, as of late is phishing over meeting invites. Even considering how many meeting invites an organization sends and receives on a daily basis, they never really consider the potential for a phishing attack in their calendar. Essentially the attacker only needs host malicious code and then obfuscate the URL to resemble something meeting related then package it up and deliver.
Most email applications these days have a built-in calendar function, but not all organizations use the same application. This works to the benefit of the attacker because the invite can come from an external address and include a link to download a plugin to join the meeting. This attack works best against personal addresses using a ruse such as a job interview, but that’s not to say it cannot be leveraged against an organization.
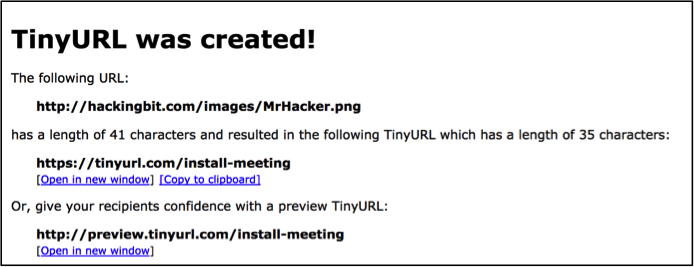
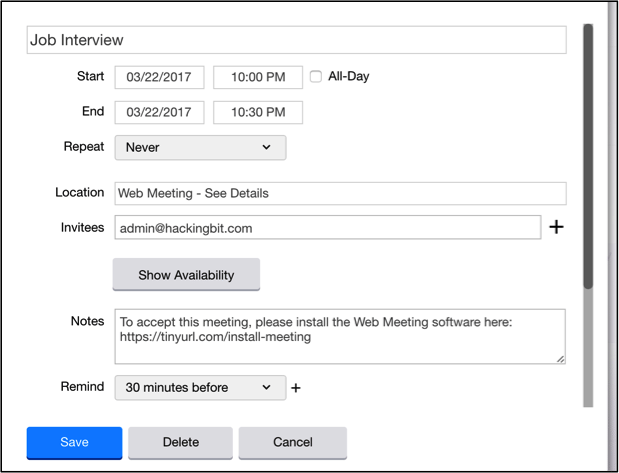
The example below shows how an attacker can disguise their malicious URL to look like something that the recipient needs to install in order to join a meeting and then incorporate it into the meeting invite.
This is another difficult attack to train for. Most users have received meeting invites that require the installation of a meeting plugin, so there is not much of a red flag as far as user awareness goes.
Each organization should conduct a risk analysis when planning on how to defend against this attack. The best option would be to automatically deny meeting invites from outside the organization’s domain, but some organizations deal exclusively with external customers or colleagues, so this control may not be realistic.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
The next best option is to restrict user permissions denying the capability for the average user to be able to execute scripts. This attack depends entirely on downloading and executing code, so any security controls in that attack chain should be locked down as much as operationally possible.