GDPR Provides Scammers with a New Golden Opportunity
GDPR latest: Fraudsters posing as banks in data protection emails phishing scam
The EU General Data Protection Regulation (GDPR) has arrived, and crooks are ready to exploit the media attention on the new law to launch cyber-attacks against unaware users.
Several US websites including the one belonging to Los Angeles Times have temporarily been made unavailable in EU counties as a precaution due to the law coming into effect, other websites like the USA Today have published a version for EU users that doesn't include any tracker and advertising element.
Phishing simulations & training
Authorities are warning scammers could use the GDPR as bait to steal personal information from companies and users.
Cyber-criminals are already sending out GDPR-themed phishing messages to trick victims into providing personal information or visit malicious websites set up to steal credentials or to deliver malware.
Recently the customers of the NatWest bank were targeted by the scammers who sent them malicious messages claiming to be from the financial institution.
In the last days, almost any company is informing its customers that its processes comply with the new GDPR, most of the messages share new privacy policies with customers.
Customers are exposed to hacking; it is easy to fall victim to scammers that use similar messages for malicious purposes.
A typical example of a scam is related to the consensus in continuing to receive emails from a company. Many companies are asking customers the permission to continue sending them messages, but crooks are exploiting this process using fake emails telling customers their accounts could be terminated if they do not update their records.
With this kind of social engineering attack, users are tricked into visiting a rogue site specially crafted to steal customers data. Experts observed this attack scheme to steal credentials for victims' bank accounts or credentials for other web services.
Scammers in action months before the GDPR deadline
The activities of scammers begun months before the announced deadline for the General Data Protection Regulation (GDPR), crooks exploited the news about severe penalties for those companies that will be not compliance to demand personal information to netizens and organizations.
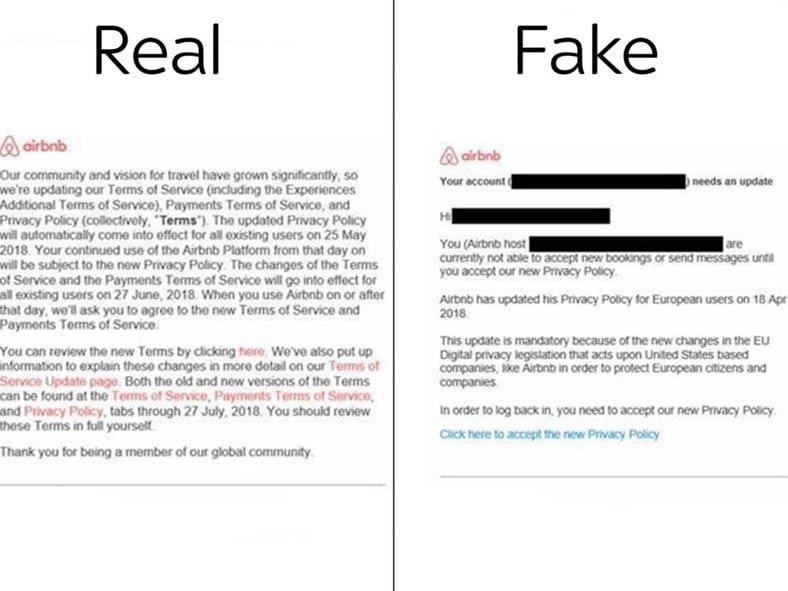
Airbnb users, for example, were among the first hit by GDPR phishing campaigns, the company like many others, is sending emails to inform users of changes in the privacy law according to the upcoming GDPR.
Cybercriminals are targeting Airbnb users demanding personal information and financial data referencing the GDPR.
Experts from Redscan observed a spam campaign targeting Airbnb users with spam messages like the following one:
"This update is mandatory because of the new changes in the EU Digital privacy legislation that acts upon United States-based companies, like Airbnb in order to protect European citizens and companies," reads the spam message according to the Redscan.
Figure 1 - GDPR-themed spam campaign on Airbnb users
The extent of the campaign was not determined at the time of the attack; scammers were targeting businesses' email addresses taken online.
The phishing messages sent to the users pretend to be a GDPR information request sent by Airbnb to the hosts of the service.
"The irony won't be lost on anyone that cybercriminals are exploiting the arrival of new data protection regulations to steal people's data," Skynews cited Redscan Director of Cybersecurity Mark Nicholls Nicholls as saying.
The phishing emails use a simple as effective social engineering trick; the message informs hosts they can't accept new bookings or contact potential guests until they accept their organizations are not compliance to the GDPR.
Malicious email uses a domain that could appear as legitimate, according to Redscan, in this campaign, hackers rather than the legitimate @airbnb.com domain used the @mail.airbnb.work domain.
If the victims click the malicious link embedded in the email, they are redirected to phishing page designed to request victims both personal and financial information.
"Modern phishing campaigns are becoming increasingly difficult to spot, and people need to be extra vigilant when opening emails and clicking links since it's important to ensure they originate from a trusted source," said Mark Nicholls, Redscan's director of cybersecurity.
It is important to highlight, that GDPR notifications sent by companies to its customers don't ask for users' credentials, so be careful and stay vigilant.
"These emails are a brazen attempt at using our trusted brand to try and steal users' details and have nothing to do with Airbnb. We'd encourage anyone who has received a suspicious looking email to report it to our Trust and Safety team on report.phishing@airbnb.com , who will fully investigate. We provide useful information on how to spot a fake email on our help center and work closely with external partners to report and help remove fake Airbnb websites," an Airbnb Spokesperson said to SecurityAffairs.
Crooks impersonate tech giants
Scammers often attempt to exploit the trust in major brands that have a large audience of users that are potential victims of fraudulent activities.
Apple, Google, Microsoft, PayPal, and YouTube are just a few brands that could be exploited by crooks for their campaigns with highly convincing messages. For attackers is quite easy to spoof the email address of the sender in a way to trick victims into opening the messages and follow the instructions it contains.
The emails contain branding and images which are familiar, but all the fraudulent communications ask users personal and financial data with an urgent call to action to avoid problems such as the temporary suspension of their account.
To make the attack more effective and to elude control, an email that apparently is sent by Google could include a link to a weaponized document stored on a Google cloud storage.
GDPR phishing scams recently targeted Apple; the attackers launched several campaigns to steal user account credentials.
A campaign spotted by Trend Micro used email notifying victims that their Apple account has been "limited" due to unusual activity and urged them to update their payment details via a link.
The link, of course, pointed to a fake Apple website that cloned the legitimate one and used to ask victims their data.
"On April 30, we detected a new Apple ID phishing scam using a known social engineering tactic —threatening to suspend service to pressure users into divulging personal details," wrote Trend Micro researchers in a blog post about the scam last week. "Multisite login details, like an Apple ID and corresponding password, are valuable because they can give an attacker access to all the applications linked to that account."
Tips to Spot a GDPR scam
The attacks described in this post are just a few examples of the ways scammers could exploit the new GDPR. More can be expected over the coming days.
Below a few tips to avoid being the victim of GDPR-related scams:
- Carefully review any GDPR-related request and consider them as potentially suspicious.
- Don't forget that banks and other payment services such as PayPal never ask users personal and financial information via email.
- Never provide your password, a pin, or any other sensitive information by email.
- Never click on links embedded in suspicious emails and never open their attachments.
- Instead of opening links included in the suspicious email, visit the website of the sender by typing the correct address directly into the browser.
- If you click a link in the email, check the website address you are directed to.
- Fraudulent messages usually don't address victim by name. Instead, they start with "Dear friend" or "Dear customer."
Unfortunately, the fraudulent messages could be not easy to discover, in some case they contain poor spelling or grammar, in other cases, the grammar is perfect such as the quality design.
References
https://www.thesun.co.uk/tech/6375142/gdpr-email-scams-police-warning/
https://securityaffairs.co/wordpress/72148/cyber-crime/gdpr-phishing.html
https://news.sky.com/story/airbnb-customers-being-scammed-by-criminals-11356730
https://www.spamtitan.com/blog/beware-gdpr-phishing-scams/

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
https://threatpost.com/gdpr-phishing-scam-targets-apple-accounts-financial-data/131915/