Case Studies of Phishing as an Initial Attack Vector
Phishing, the mass sending of spam emails by a scammer or group in an attempt to “hook” unsuspecting users, is often the first volley in an attack against a person or entity. If it is successful, the initial phish can end up causing much greater damage. In this article, we’ll take a look at a few different phishing attacks to see how they work and what they want.
See Infosec IQ in action
The Setup
According to research done by the Honeynet Project, a nonprofit dedicated to internet security, most phishing scams start with the thieves seeking out a vulnerable server or website they can hack into and exploit. Once they’ve gained access, the phishers will upload bogus web pages that include forms they can use to capture the visitor’s data. These web pages and forms most often mimic bank account logins or sites like eBay or Paypal.
Next, the spamming begins. These criminals will send tens of thousands (if not millions) of emails to users anywhere and everywhere. Many times, the content of the email will implore the recipient to click the included link to either update passwords or confirm accounts, otherwise they risk being locked out. When the person clicks the link, they are connected to the web form hosted on the hacked server, which will then gather all the personal information it can. Later, it will be used against them.
Case One: Dan and Nancy Boyle Get Phished
Although phishing scams go back to the 1990s (the term was coined in 1996) it didn’t really become a massive problem until around 2004; the Anti-Phishing Working Group reported that in the first six months of that year the number of reported of attacks went from 176 to 1,422, an increase of 800 percent.
One of the earliest reported victims were Dan and Nancy Boyle, who ran a small window treatment company out of their home in Racine, Wisconsin. According to a 2004 article in the Washington Post, Mrs. Boyle received an email from what she thought was her bank, Bank One, which informed her that her account would be suspended unless she updated her information.
Dutifully, she clicked the link, entering her account information on the provided form. She then received a second email, purportedly from EBay, also asking her to verify her info. The combination of these two emails allowed scammers to later steal $1,800 from her bank as well as to charge $800 in escort fees to the couple’s credit card.
Case Two: The South Korean Media/Bank Attacks
And while it is understandable that a mom-and-pop organization might be vulnerable to a phishing attack, the truth is that it can affect even the largest of organizations. In 2013 it was reported that three banks and three media companies in South Korea were compromised due to a malware dropper attachment on a phishing email. TV stations KBS, MBC and YTN and the Jeju, NongHyup, and Shinhan banks were all attacked at the same time.
While the content of the specific email wasn’t released, security researchers stated that it was a message posing as a bank. When the recipient clicked on the link, it began downloading nine different files to the user’s computer in the background. These were programmed to begin wiping computer hard drives at a specific date and time, an attack what is often referred to as a logic bomb.
In addition, this particular phishing attack was able to replicate and spread to more than 32,000 computers by stealing passwords and redistributing itself over the network as a software update. Although the identity of the attackers has not yet been found (the North Koreans were initially blamed), it was clear that whoever was behind it wanted to create maximum damage.
Case Three: Anthem HealthCare Breach
A very popular target for phishing scams are hospitals and other healthcare facilities or providers. Because of requirements of the Affordable Care Act, much more patient data is online. Unfortunately, this means that thieves can also exploit this information, which often includes Social Security numbers, birthdates, and medical identification numbers, to buy prescription drugs, submit false medical claims, open credit card accounts, and more.
The largest hack to date occurred in December of 2014, when criminals gained access to the personal data of Anthem HealthCare’s 80 million customers. While the company’s official statement was coy about how it had occurred – they called it a “sophisticated attack” – other reports stated it was due to an email phishing scam that persuaded at least five employees to divulge their credentials. The hackers got access and laid low for a while, as the data breach wasn’t discovered until at least six weeks later. Anthem insisted that no bank account information was compromised and offered their customers free identity protection from AllClear ID for two years.
(Hospitals are also increasingly targets for ransomware, where data is held and decrypted for a fee, which we discuss in our Case Study of Hollywood Presbyterian [insert link].)
Methods of Prevention
As we’ve attempted to show with these cases, phishing is a problem that cannot necessarily be prevented by the IT department alone. It takes diligence on the part of every employee to know when an email just doesn’t seem right.
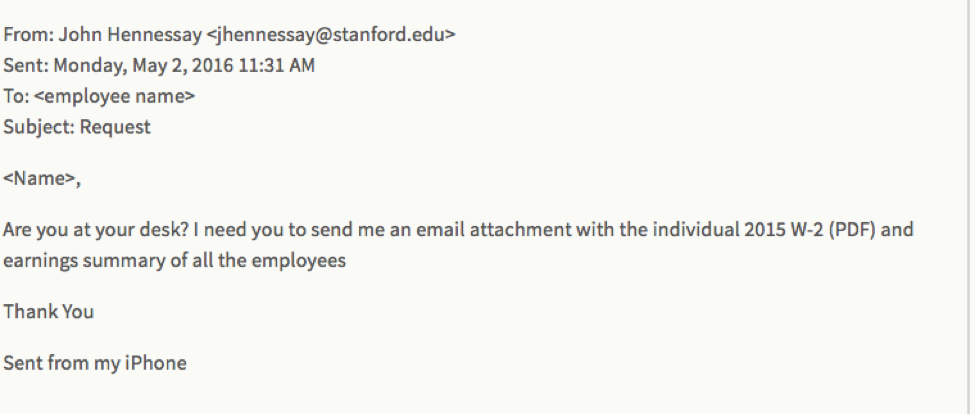
To help educate their staff, many organizations have created safety bulletins or web pages listing the details of the latest phishing emails that have attempted to breach their systems. For example, Stanford University’s IT department regularly posts flagged emails. One dated from May 6, 2016 appeared to be from the university’s president asking for the 2015 earnings summaries of all employees.
Photo: Stanford.edu
The university noted in the bulletin that President Hennesey’s name was spelled incorrectly. MIT has a similar page listing examples of phishing emails supposedly sent by their administrators. They also include important things to look out for (bad grammar, spelling mistakes, request for a password, etc.)
Other sites serve as both repositories and disseminators of phishing scam alerts. One such service is MillersMiles.co.uk, which offers daily reports to users and websites around the world via RSS. MillersMiles encourages anyone who has received a phishing email to forward it to them so they can add it to their database and track its usage.
InfoSec’s PhishSIM and AwareED
But simple awareness is not enough. In order for companies to maintain the highest level of vigilance against the never-ending assault from phishing emails, it’s crucial that you continually make sure every single employee is on board and on guard.
That’s where InfoSec comes in, with its suite of products called Infosec IQ, designed to train and, perhaps most important, drill employees. The two main offerings are PhishSIM and AwareED, which allow you to deploy simulations and run educational campaigns effortlessly and automatically.
AwareED is our package of lessons and courses designed to teach your staff about the importance of protecting the network, including videos and exercises about how to create secure passwords, browse safely, and avoid being phished.
Once you sign up for a free account, as an administrator you can make up a course, add learners, and select learning modules. Everything else is automated, as AwareED will send out enrollment instructions and reminders as well as administer the course. All activity, including those who pass and fail can be viewed in a generated report.
But as we’ve said before, education is only half of the battle. The true test is in a real-world situation, where the user is not expecting a phishing email. To help with this is PhishSIM, a phishing simulator, where you can create and send emails to staff. But instead of compromising their computer or stealing their info, clicking on the link sends employees to the Infosec IQ website where a short video plays.
PhishSIM has a variety of pre-made templates that can be customized to your needs. They represent some of the more common phishing tactics, like those in the case studies above. You can send phony emails from banks, system administrators, or even ones that offer “Free Pizza.” Or, you can design one from scratch, perhaps based on the latest threats as listed by MillersMiles, SpamHaus, etc.
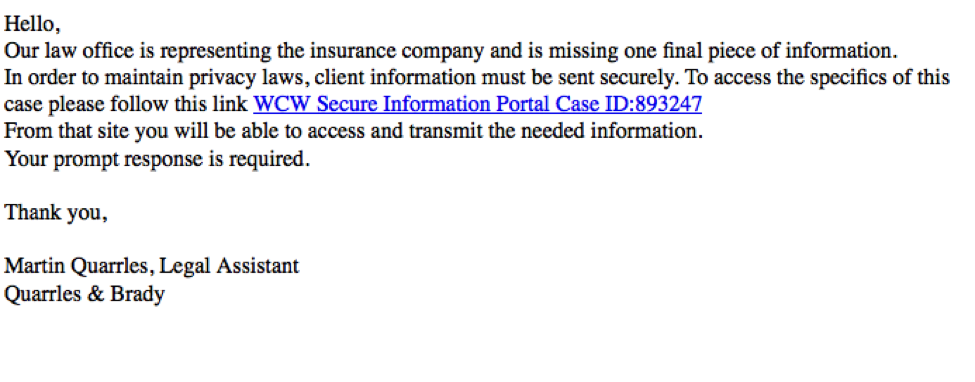
Below is an example from the library:
A good way to start using Infosec IQ is with PhishSIM. You can surreptitiously send a phishing email and see who gets “caught” (a list of users who clicked is available in the dashboard); those that do can be required to take an AwareED course.
But sending just one email may not be enough to let you know who is not paying attention to protocol. That’s why an administrator can make a battery, which is a series of email templates that can be configured and scheduled for release over a period of hours, days, weeks, or months. As with AwareED, all of this is automated, and the results of the campaign can be viewed in the dashboard or in a report.
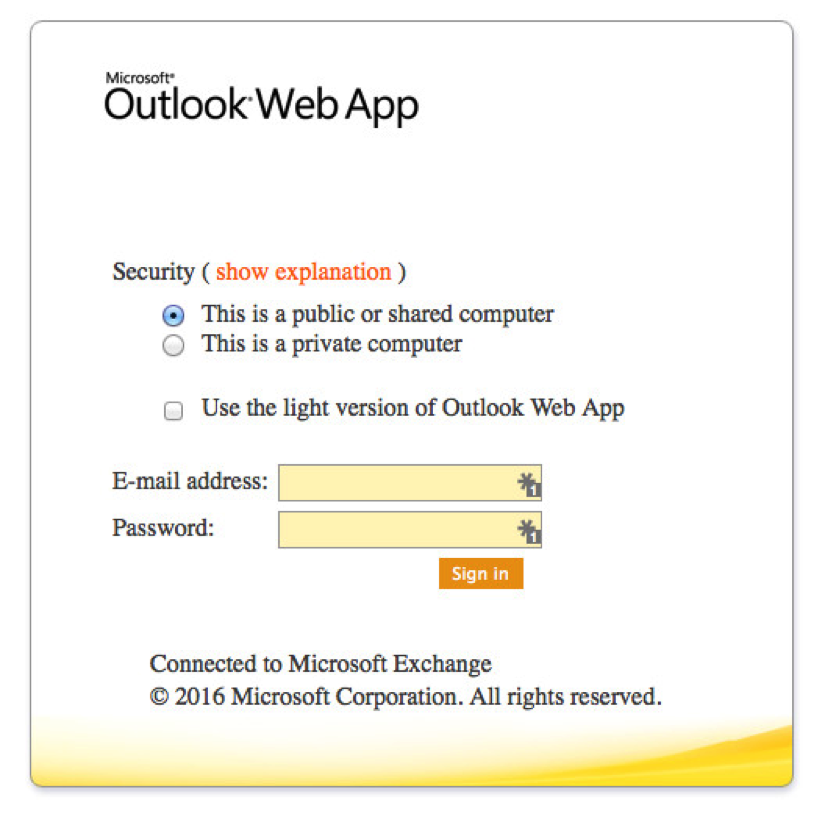
As the case of Dan and Nancy Boyle illustrated, many phishing attacks are used in combination with rogue websites that mimic banks or other types of important websites. Because of this, PhishSIM has recently added a "data entry site section," which contains templates emulating Outlook or Salesforce. You can add the link to the page in the email campaign. Again, everyone who clicks is redirected to a short video and their activity is reported to you.
A realistic Outlook template included in the PhishSIM library
See Infosec IQ in action
Most experts agree that the last line of protection against phishing is the recipient. You can have all the filters and blacklisters in place but, if one bad email gets through, all it takes is one click to lose it all.
Infosec IQ is free to register and gives new users 100 sends, 5 campaigns, and 30 learners. This will allow you to see how it works and perhaps show you how vulnerable to phishing your company really is.